
How to get URL link on X (Twitter) App


 There are at least 3 ways to achieve code execution on an Azure App Service Web App ("Azure Web App" from here on) instance:
There are at least 3 ways to achieve code execution on an Azure App Service Web App ("Azure Web App" from here on) instance:


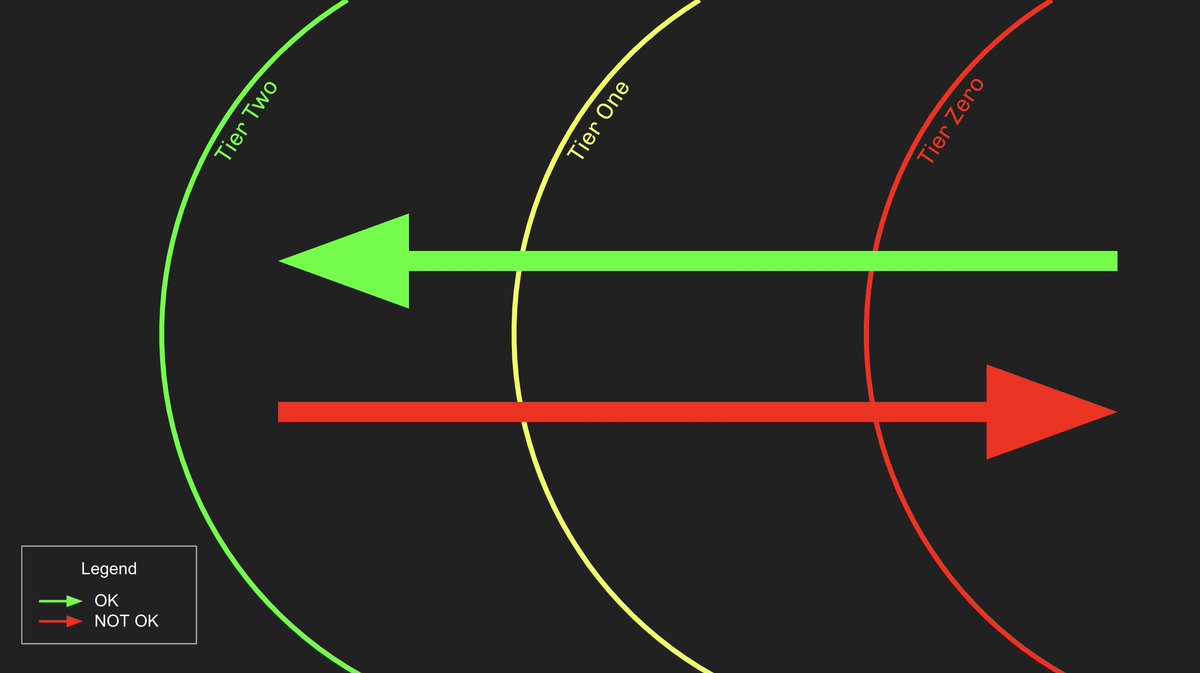
 First, understand the problem we are trying to solve with Tiered Administration:
First, understand the problem we are trying to solve with Tiered Administration: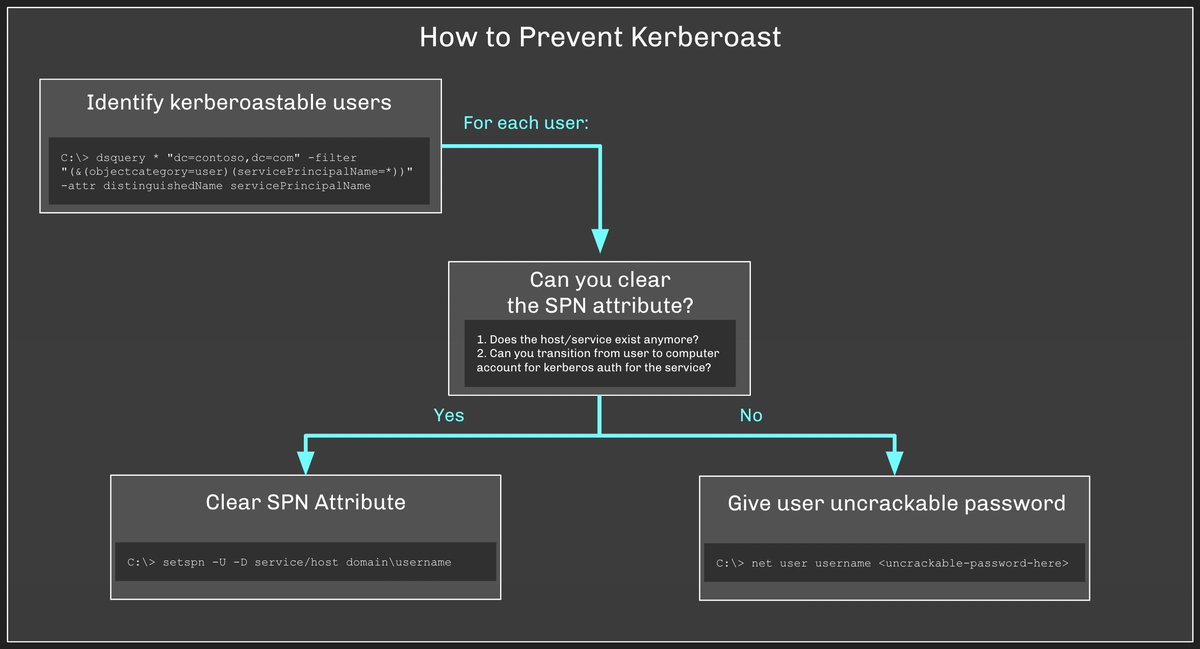
 First we need to identify Active Directory users that are "kerberoastable" - possible targets for the attacker to choose to Kerberoast.
First we need to identify Active Directory users that are "kerberoastable" - possible targets for the attacker to choose to Kerberoast.










 In its default state, an Azure tenant enforces a trust boundary around itself. The Azure Security Token Service (STS) for this tenant will only authenticate principals within this tenant. In other words: only users in your tenant can access anything in your tenant.
In its default state, an Azure tenant enforces a trust boundary around itself. The Azure Security Token Service (STS) for this tenant will only authenticate principals within this tenant. In other words: only users in your tenant can access anything in your tenant.

https://twitter.com/_wald0/status/1493263809074503682
https://twitter.com/_wald0/status/1502475482004041730There are 3 major reasons I see why we should not be blaming the people behind these dangerous configurations:



 In "Azure", the story is very, very different. There are multiple forms of access control, and multiple services responsible for making access decisions.
In "Azure", the story is very, very different. There are multiple forms of access control, and multiple services responsible for making access decisions.

