Found a clever honey pot contract
At a glance it looks vulnerable: an admin provides a string that is used as a key. Anyone that calls a function w/ 1 ETH and the string takes away 30 ETH.
So just find the admin's transaction and copy the string, right?
etherscan.io/address/0xb58c…
At a glance it looks vulnerable: an admin provides a string that is used as a key. Anyone that calls a function w/ 1 ETH and the string takes away 30 ETH.
So just find the admin's transaction and copy the string, right?
etherscan.io/address/0xb58c…
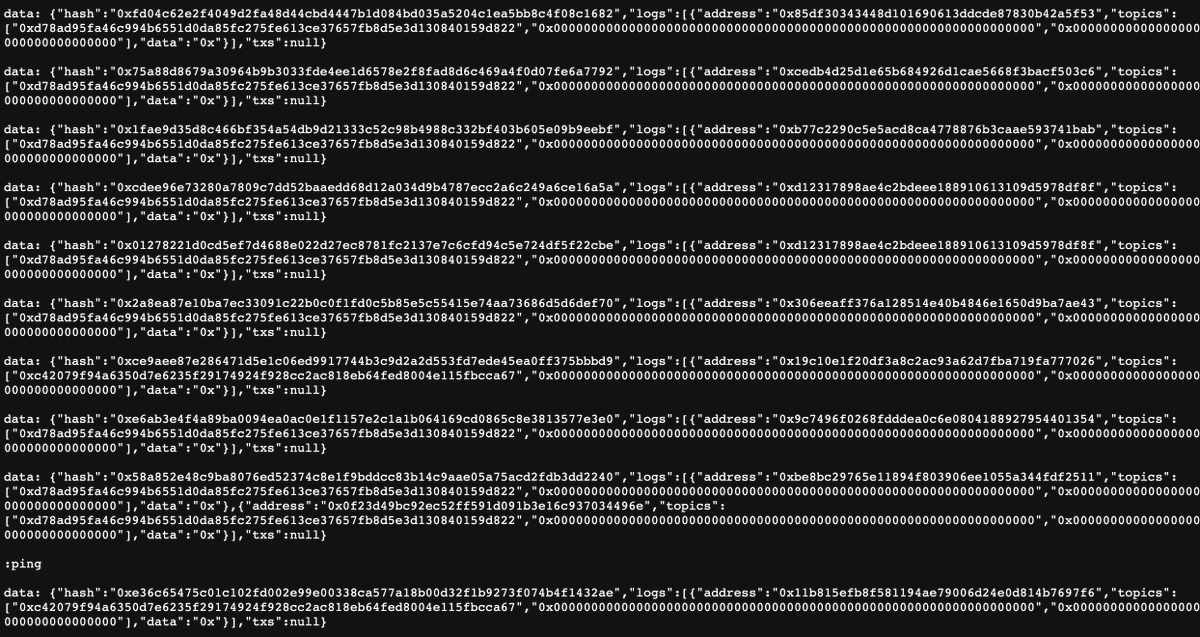
Wrong. Hidden away in Etherscan is an internal call that updates the string. You can't see the update on Etherscan, but plugging this into ethtx.info makes it clear the correct string has been updated.
ethtx.info/mainnet/0x1ce4…


ethtx.info/mainnet/0x1ce4…
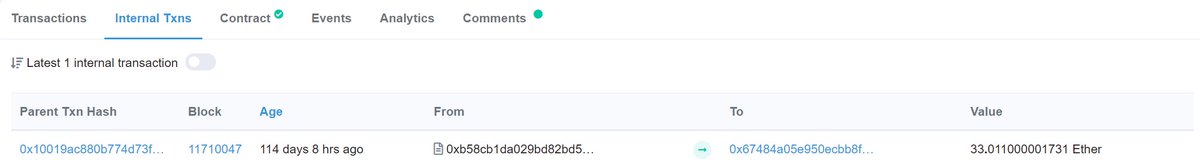
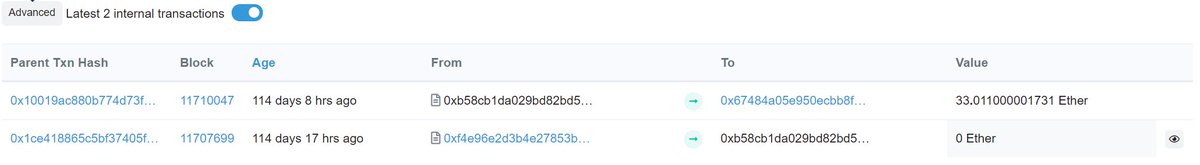
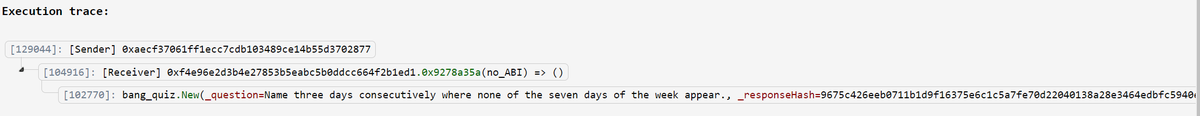
Interestingly within hours of deployment a few people tried to exploit this honey pot. Looks like 3 ETH was trapped, and the creator made away with that and their initial 30 ETH. 

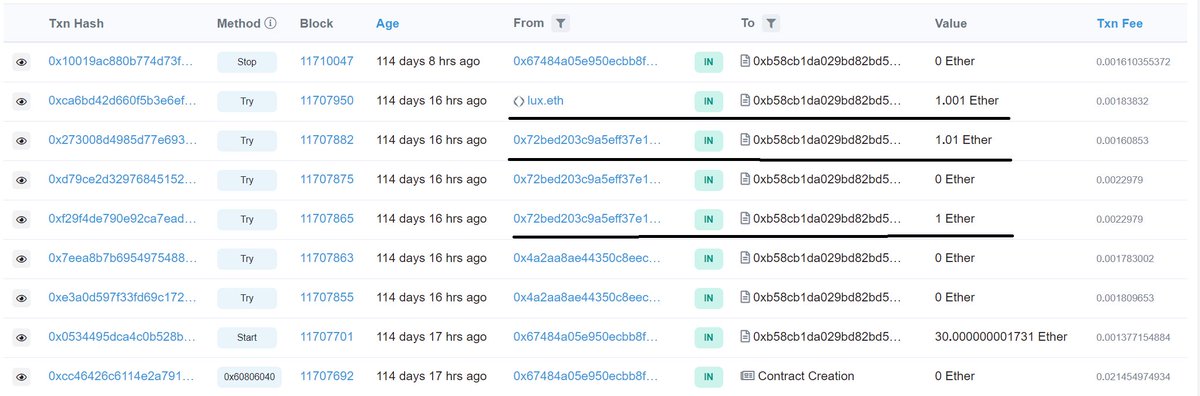
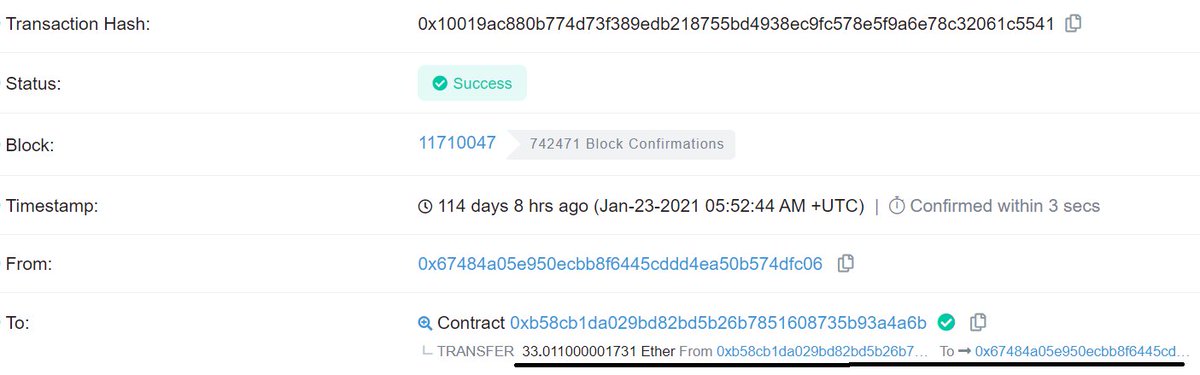
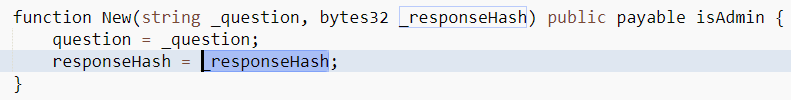
Should have explained this before, but this is what I meant by find the admin's transaction and plug in the string.
At first glance it must have looked like you just stumbled on a 30 ETH jackpot that someone sloppy deployed!
At first glance it must have looked like you just stumbled on a 30 ETH jackpot that someone sloppy deployed!
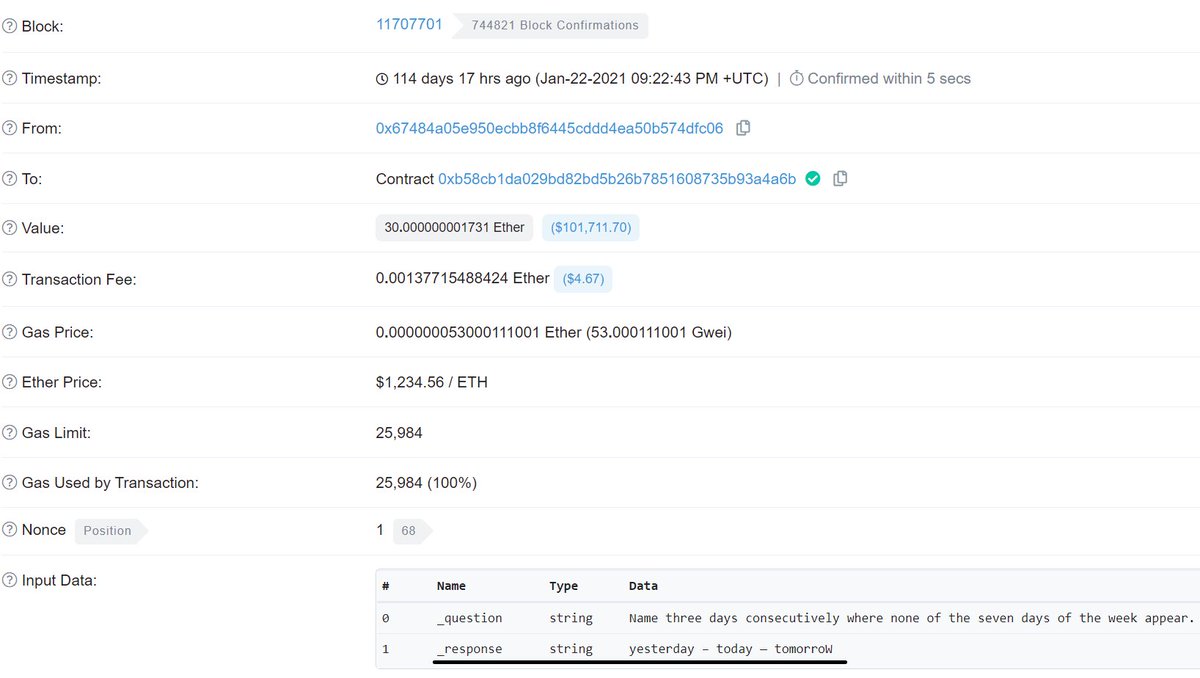
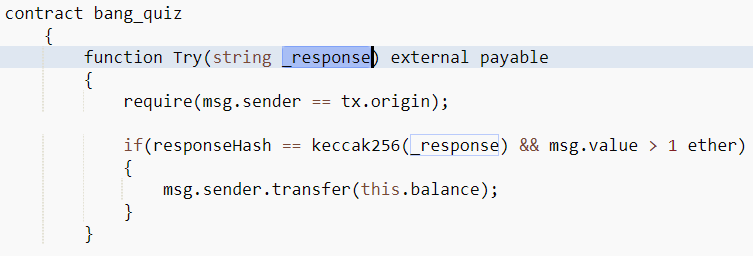
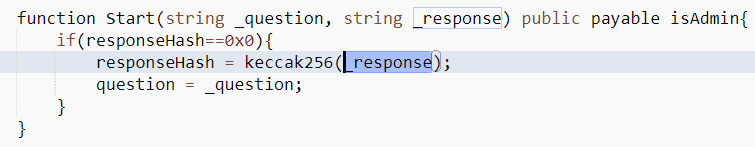
That string looks like the string that would "solve" the quiz and transfer you the 30 ETH...
Unless it is replaced with a sneaky internal call to new(), which is what happened in the transaction that was hidden away in the contract's internal transactions


Unless it is replaced with a sneaky internal call to new(), which is what happened in the transaction that was hidden away in the contract's internal transactions
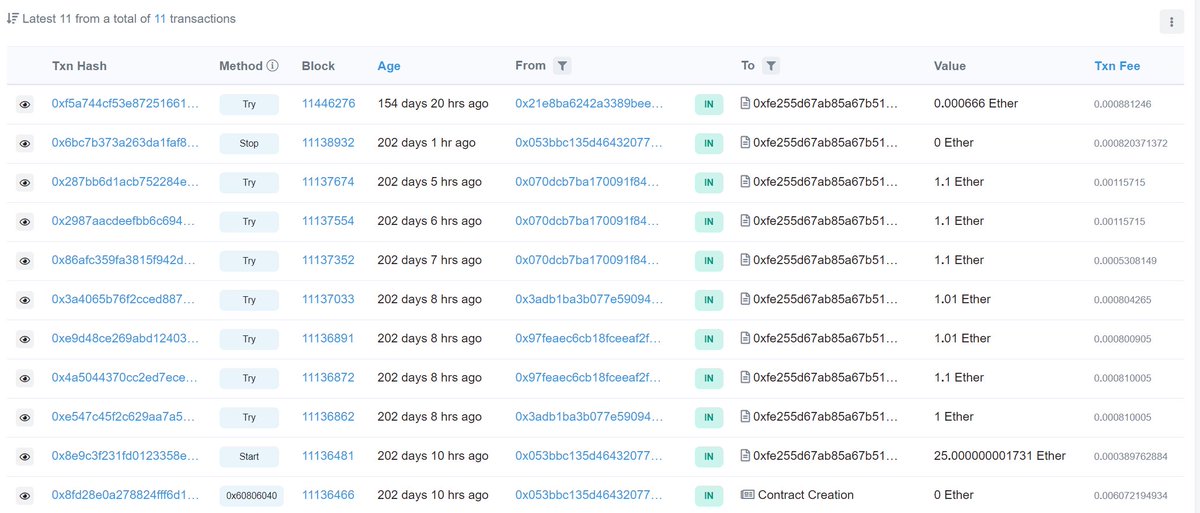
Went down a rabbit hole trying to figure out how long this fellow has been doing this honey pot. They've deployed this dozens of times and made way more ETH than I thought.
F in the chat for the people who lost 7 ETH on this one alone!
etherscan.io/address/0xfe25…
F in the chat for the people who lost 7 ETH on this one alone!
etherscan.io/address/0xfe25…
• • •
Missing some Tweet in this thread? You can try to
force a refresh