Did you know that you can get a free M365 E5 subscription with 25 user licenses to learn, create automation, and develop applications?
I know most folks never get the chance to admin this stuff, so sign up now, and let's walk through this together :)
developer.microsoft.com/en-us/microsof…
I know most folks never get the chance to admin this stuff, so sign up now, and let's walk through this together :)
developer.microsoft.com/en-us/microsof…
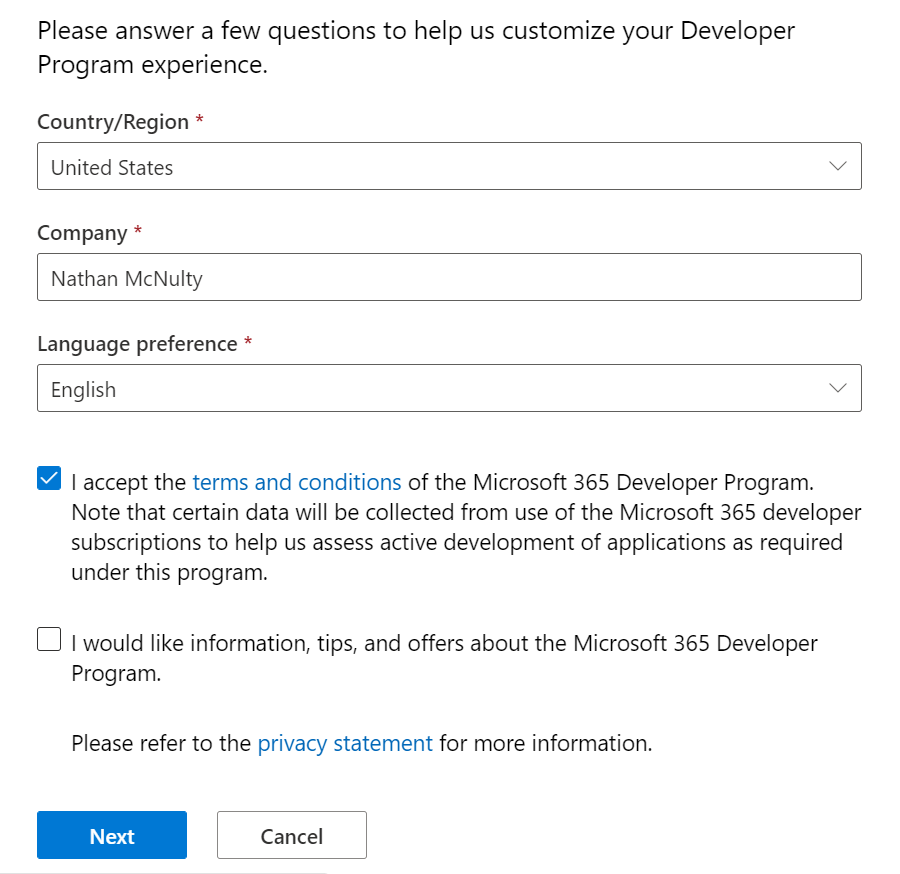
Upon visiting the Microsoft 365 Dev Center, it will ask you to sign in with your Microsoft account.
This will be the Microsoft account that your developer tenant will be associated with, but not the one you use to log into it.
You should see something like this 👇
This will be the Microsoft account that your developer tenant will be associated with, but not the one you use to log into it.
You should see something like this 👇

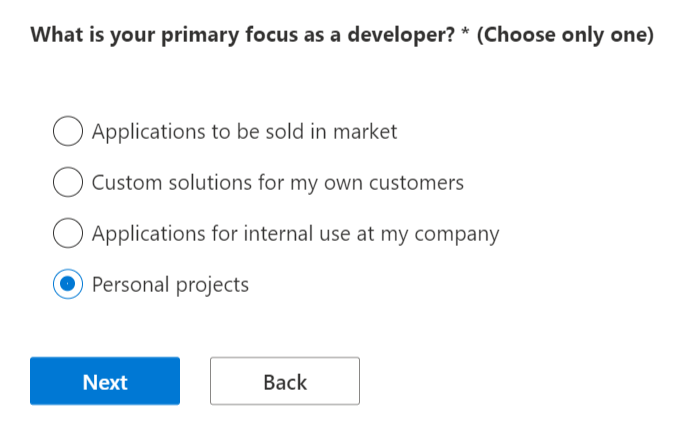
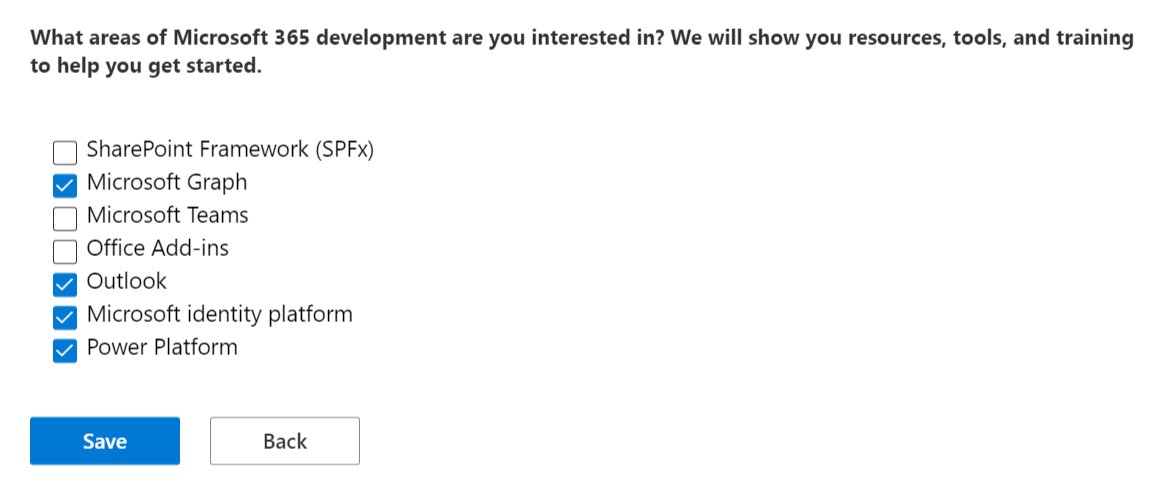
So we simply fill out a few forms that let Microsoft know what we intend to do.
Please do not abuse this or use it for business purposes.
I build automation scripts, test SSO like SAML/OIDC with various apps, and build documentation for sharing with others for learning.


Please do not abuse this or use it for business purposes.
I build automation scripts, test SSO like SAML/OIDC with various apps, and build documentation for sharing with others for learning.
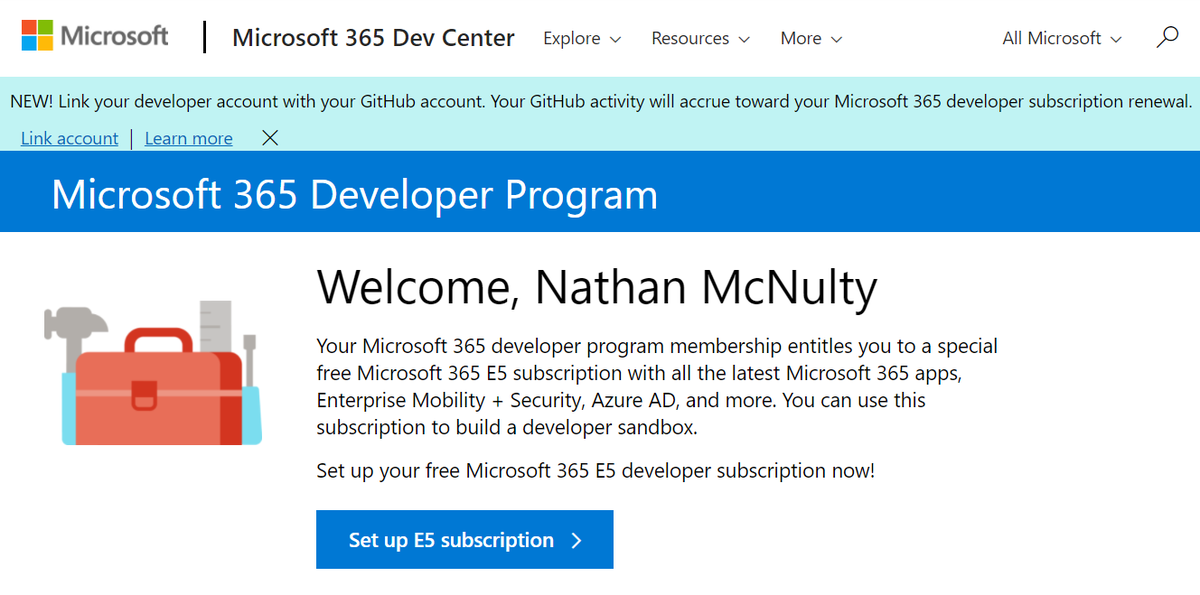
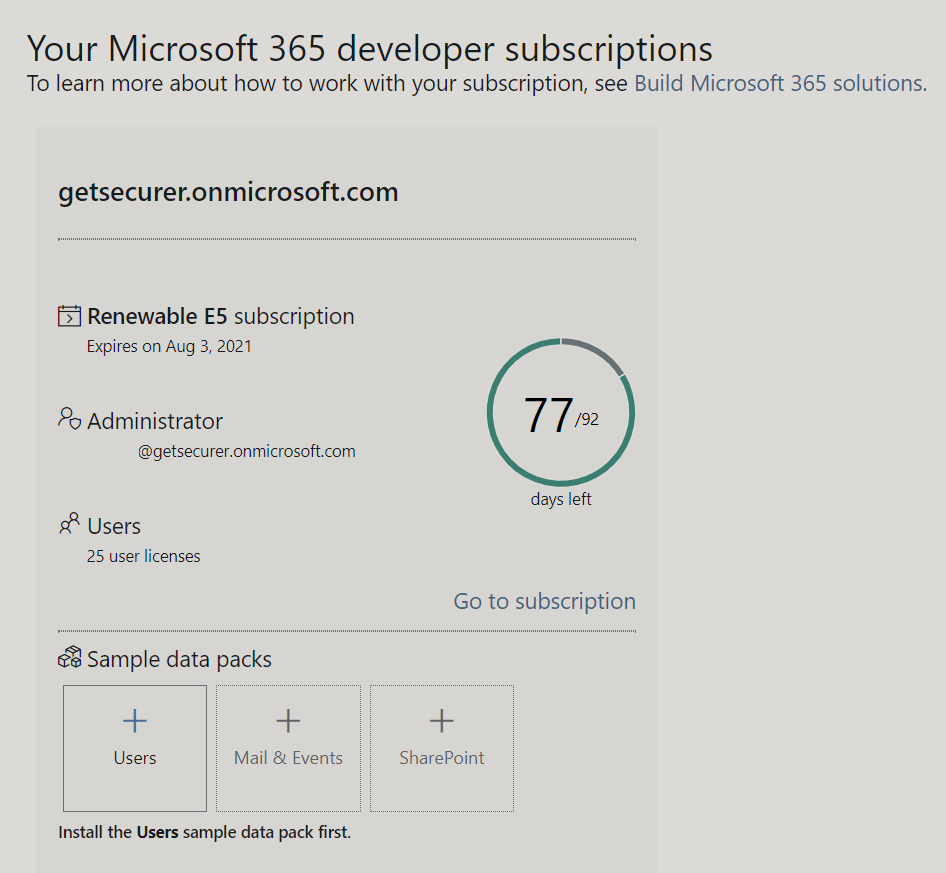
And just like that, we now have our own M365 Developer account where we can set up our E5 subscription! 
So the next step is to click the big blue "Set up E5 subscription" button and follow the wizard.
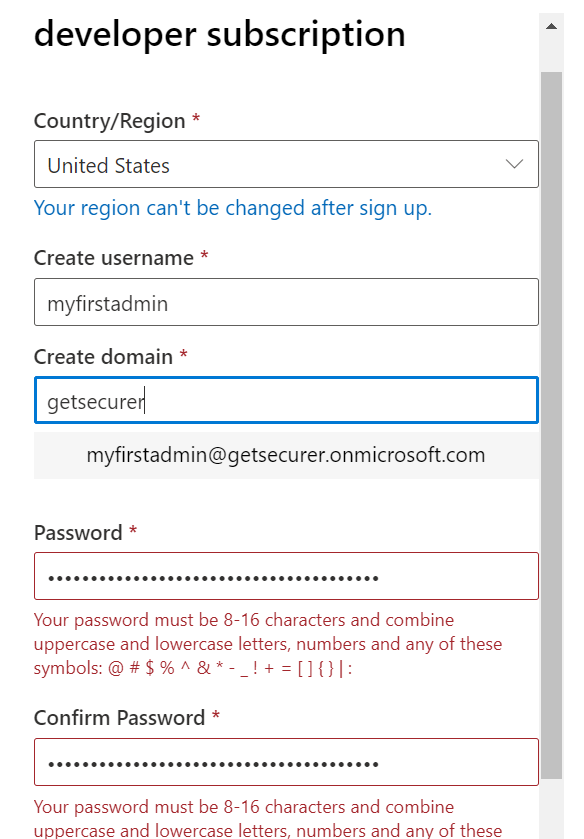
Note: Microsoft has a really bad password limitation on sign up, so use a crappy one and change it once you've logged in
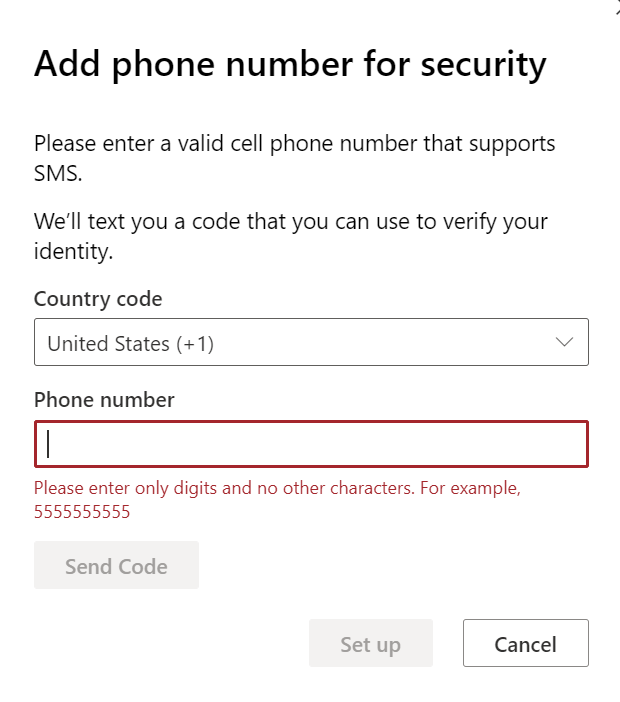
2nd note: Kudos to MS on requiring MFA, even if it is SMS :)


Note: Microsoft has a really bad password limitation on sign up, so use a crappy one and change it once you've logged in
2nd note: Kudos to MS on requiring MFA, even if it is SMS :)
You should now see 92 days or so (I did this a bit ago) remaining on the subscription, and you can renew this over and over as long as you are using it appropriately.
While you are here, you can definitely add their sample data packs which might be helpful to learn with :)
While you are here, you can definitely add their sample data packs which might be helpful to learn with :)
Next thing we can do is log into the Azure Portal by going to portal.azure.com
Click the hamburger menu icon (that's what we're calling it, right?), and click Azure Active Directory.
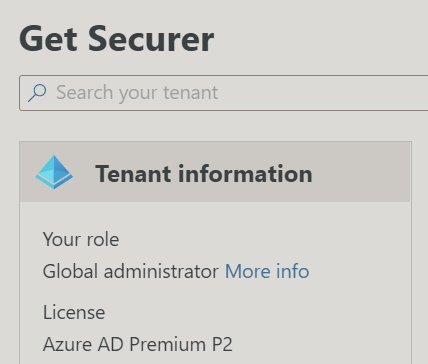
You should now see that you are a Global Admin with Azure AD Premium P2
Feel the power!

Click the hamburger menu icon (that's what we're calling it, right?), and click Azure Active Directory.
You should now see that you are a Global Admin with Azure AD Premium P2
Feel the power!
So you now have a dev tenant that you can just look around and play in.
Check out Azure AD, poke around, create users, groups, etc.
I have an AD lab that I will be connecting to this, and I'll be creating threads in the near future on setting up everything we can in M365.
Check out Azure AD, poke around, create users, groups, etc.
I have an AD lab that I will be connecting to this, and I'll be creating threads in the near future on setting up everything we can in M365.
If you have specific things you want to see, let me know
Plan is Azure AD first (Roles/PIM, Apps/SP's/SSO, Conditional Access, Users, Groups, AUs, etc), then Exchange/SharePoint/ConfigMgr migration stuff, and finally set up the full Defender/MCAS suite
Bedtime for now though :)
Plan is Azure AD first (Roles/PIM, Apps/SP's/SSO, Conditional Access, Users, Groups, AUs, etc), then Exchange/SharePoint/ConfigMgr migration stuff, and finally set up the full Defender/MCAS suite
Bedtime for now though :)
Many people asked about renewals, so I'm tossing a little update on here
I've logged into this tenant about 40 times in the last 90 days and played around with various settings, and I added my GitHub to my dev account with a few dozen commits.
That was all it needed to renew 👇
I've logged into this tenant about 40 times in the last 90 days and played around with various settings, and I added my GitHub to my dev account with a few dozen commits.
That was all it needed to renew 👇

• • •
Missing some Tweet in this thread? You can try to
force a refresh