Loves Jesus, loves others | Husband, father of 4, security solutions architect, love to learn and teach | Microsoft MVP | @TribeOfHackers | 🦋@nathanmcnulty.com
3 subscribers
How to get URL link on X (Twitter) App

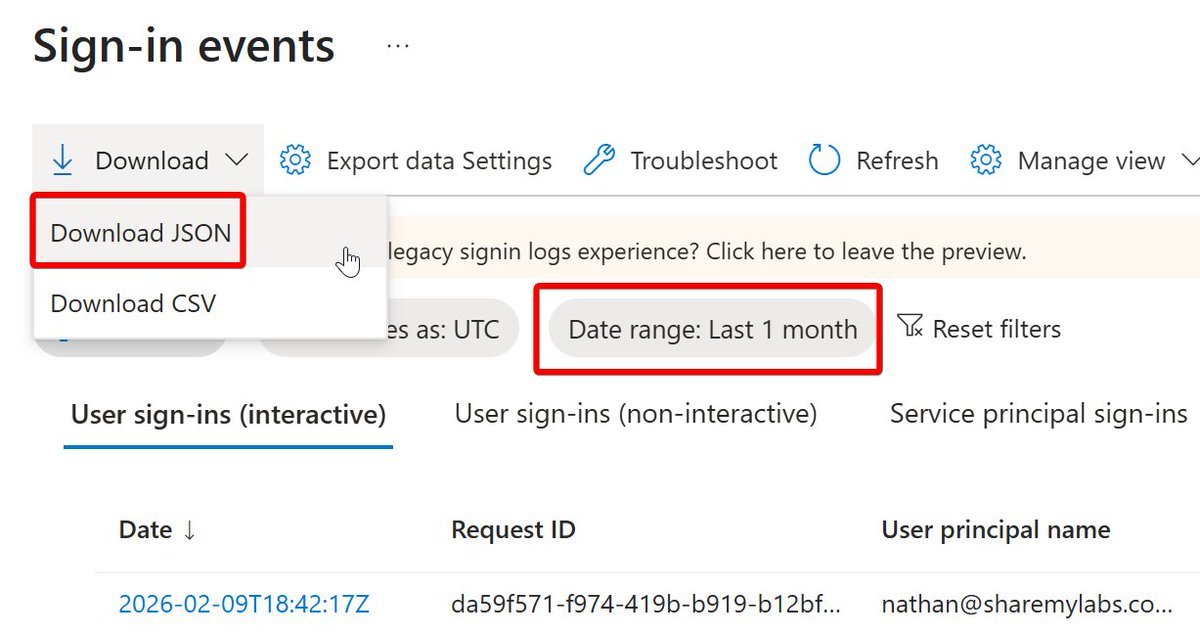

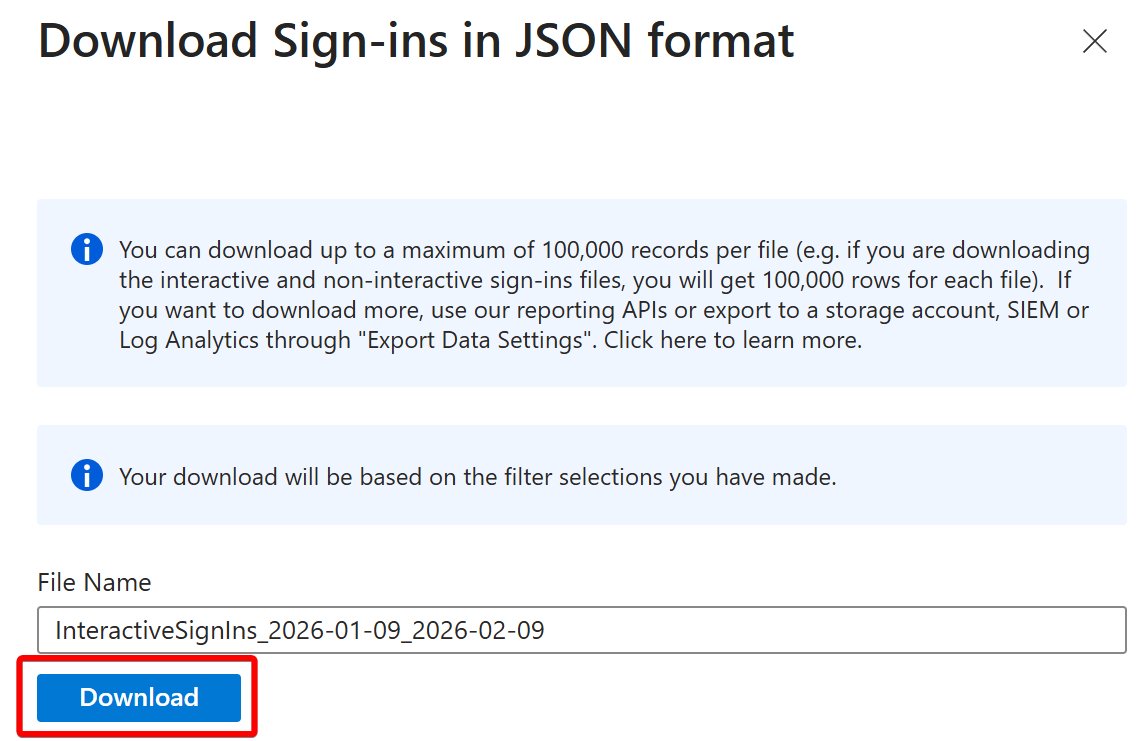 Now go to and set up your free cluster if you've never done that before. Once you have created the cluster and database, right click on the database, select Get data, select Local file, create a table for SigninLogs, select it, add your JSON, and import. dataexplorer.azure.com
Now go to and set up your free cluster if you've never done that before. Once you have created the cluster and database, right click on the database, select Get data, select Local file, create a table for SigninLogs, select it, add your JSON, and import. dataexplorer.azure.com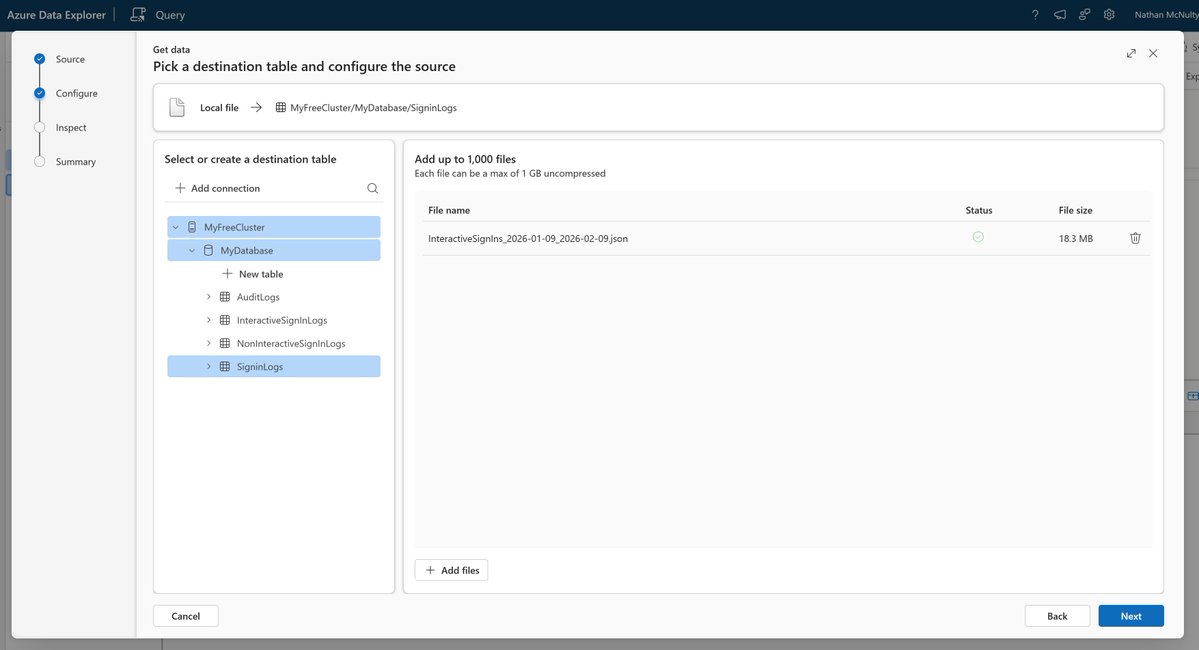

https://twitter.com/Xenoulis1/status/1985286647840481374
 To understand authorization controls (Conditional Access), we need to understand the authentication tokens it evaluates
To understand authorization controls (Conditional Access), we need to understand the authentication tokens it evaluates

https://twitter.com/magnus133/status/1883097307463483657Before I share how easy it is now, I want to share why people still hate Hello because its history was way more complicated

 This policy only applies to users with the Microsoft 365 Advanced Audit SKU assigned, audit records are retained for 1 year. Audit records for users without this SKU are retained for 180 days (thanks CISA for the bump up from 90 days!)
This policy only applies to users with the Microsoft 365 Advanced Audit SKU assigned, audit records are retained for 1 year. Audit records for users without this SKU are retained for 180 days (thanks CISA for the bump up from 90 days!)
https://twitter.com/NathanMcNulty/status/1831864788789686540First, if the built-in phishing resistant auth strength works for you, use it

https://twitter.com/_wald0/status/1820951605333950947@Alex_T_Weinert For those with PIM, these two scopes will help us get what we need (remove the /'s):

https://twitter.com/merill/status/1818119365646290948So we create a security group named "Salesforce Admins" and add our admins to the group

https://twitter.com/ChadWst/status/1801631429559730423
 That doc is a long but valuable read, especially since CAE affects things you probably don't realize
That doc is a long but valuable read, especially since CAE affects things you probably don't realize
https://twitter.com/paulbendall/status/1798725316841783374Group Policy - well known, easy to evaluate against benchmarks

https://twitter.com/reprise_99/status/1792877678649069814
 First, if auditing isn't enabled, you aren't getting anything...
First, if auditing isn't enabled, you aren't getting anything...
https://twitter.com/reprise_99/status/1778325781103743315
 Before we being, it's very important to call out that the Preview requires we set "Enforce attestation" to No, and for this reason, we NEED to restrict use to specific keys
Before we being, it's very important to call out that the Preview requires we set "Enforce attestation" to No, and for this reason, we NEED to restrict use to specific keys

 After changing "Let users install and use available apps by default" to Off, we'll see Assignments change from Everyone to Not Assigned
After changing "Let users install and use available apps by default" to Off, we'll see Assignments change from Everyone to Not Assigned 

https://twitter.com/EricaZelic/status/17321194943807367249 years ago (!), Microsoft released a feature called Administrative Units


https://twitter.com/arekfurt/status/1720781454110552454First, it's important to note that CA (authorization) comes AFTER authentication

https://twitter.com/neutroncore/status/1717093663078289677Filter for apps was introduced late last year that allows us to leverage custom security attributes within Conditional Access policies
https://twitter.com/SantasaloJoosua/status/1710163010528981132Ideally, we want to move to phishing resistant authentication

 Reusable settings can be used in multiple firewall policies, and updates to these settings apply across all policies automatically
Reusable settings can be used in multiple firewall policies, and updates to these settings apply across all policies automatically
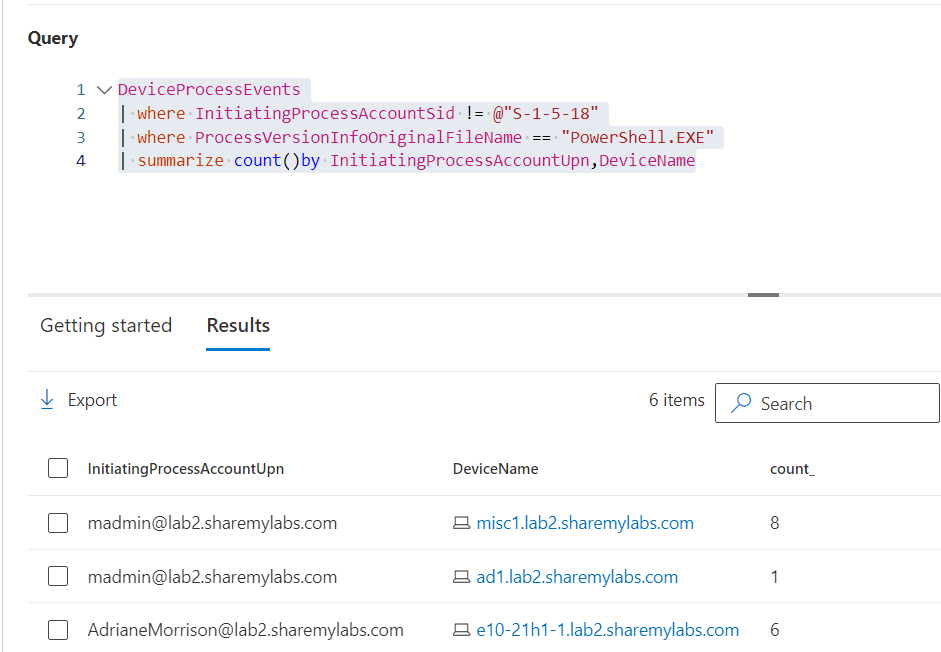
https://twitter.com/NathanMcNulty/status/1649480551777312769// PowerShell execution (including renamed binaries) excluding SYSTEM, UPN per device

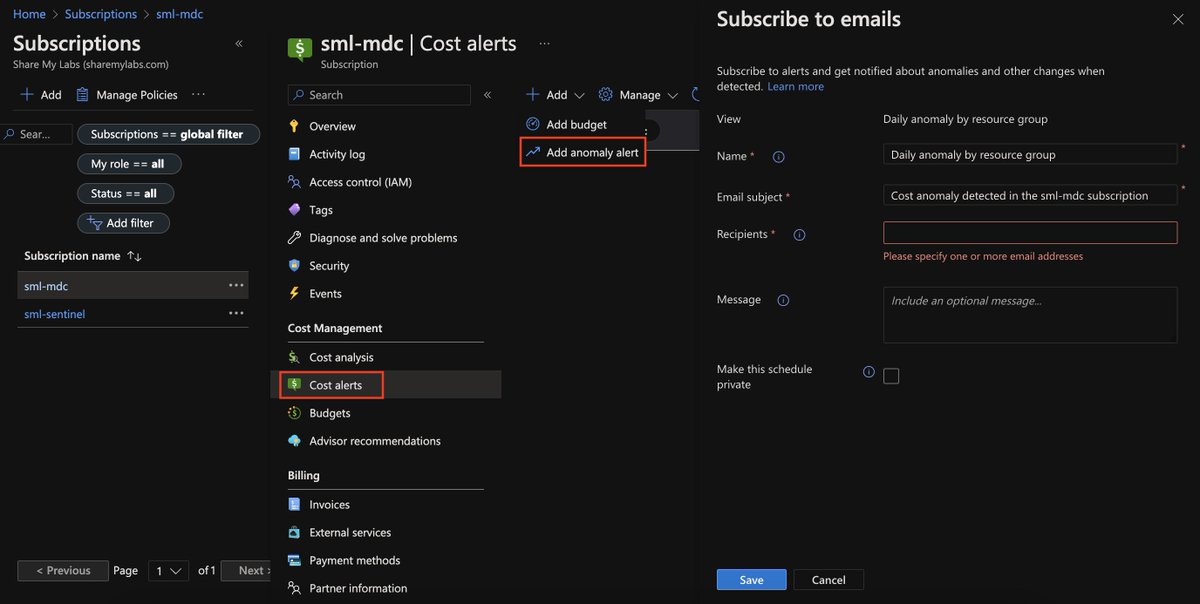
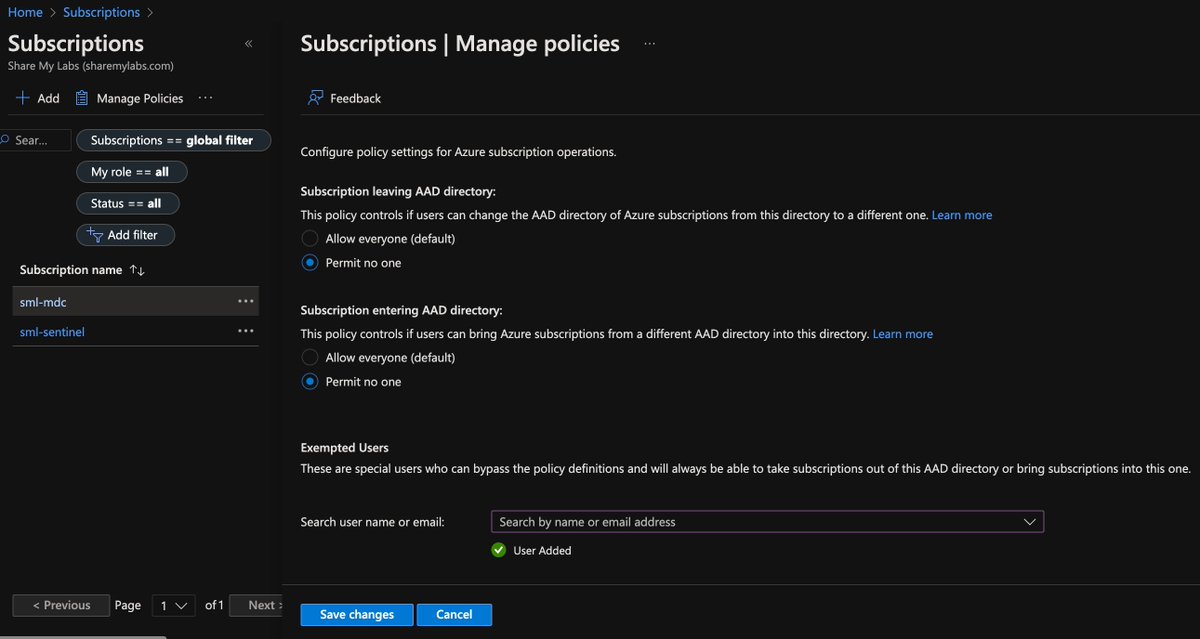
 While I'm at it, I always double check to se who can transfer subscriptions in and out of my tenant
While I'm at it, I always double check to se who can transfer subscriptions in and out of my tenant