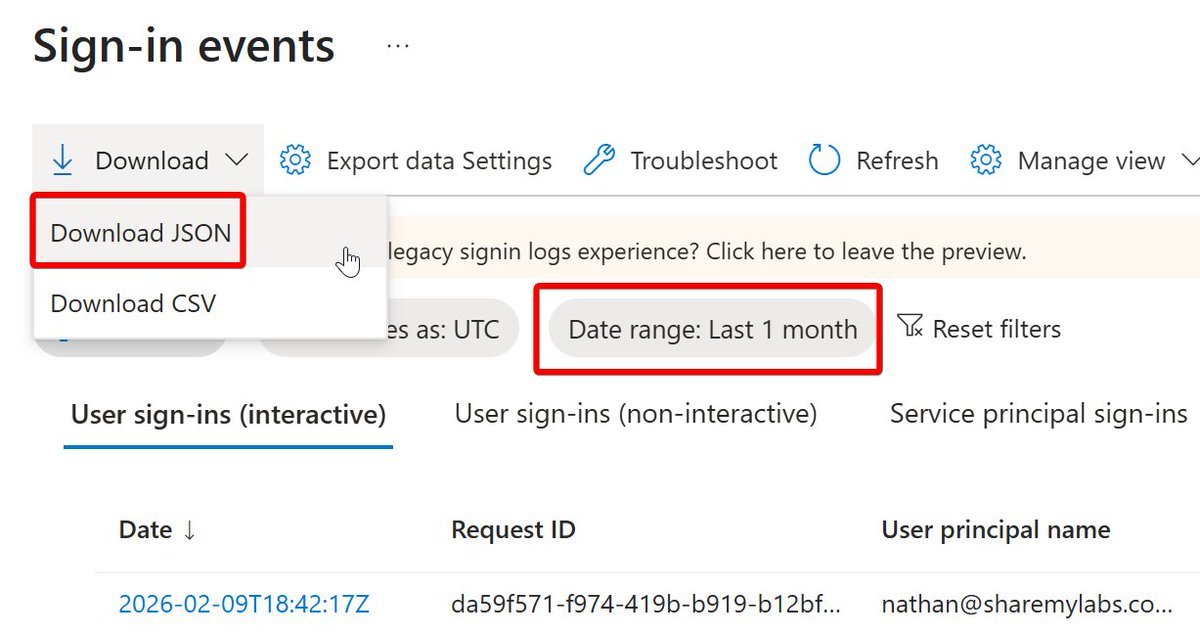
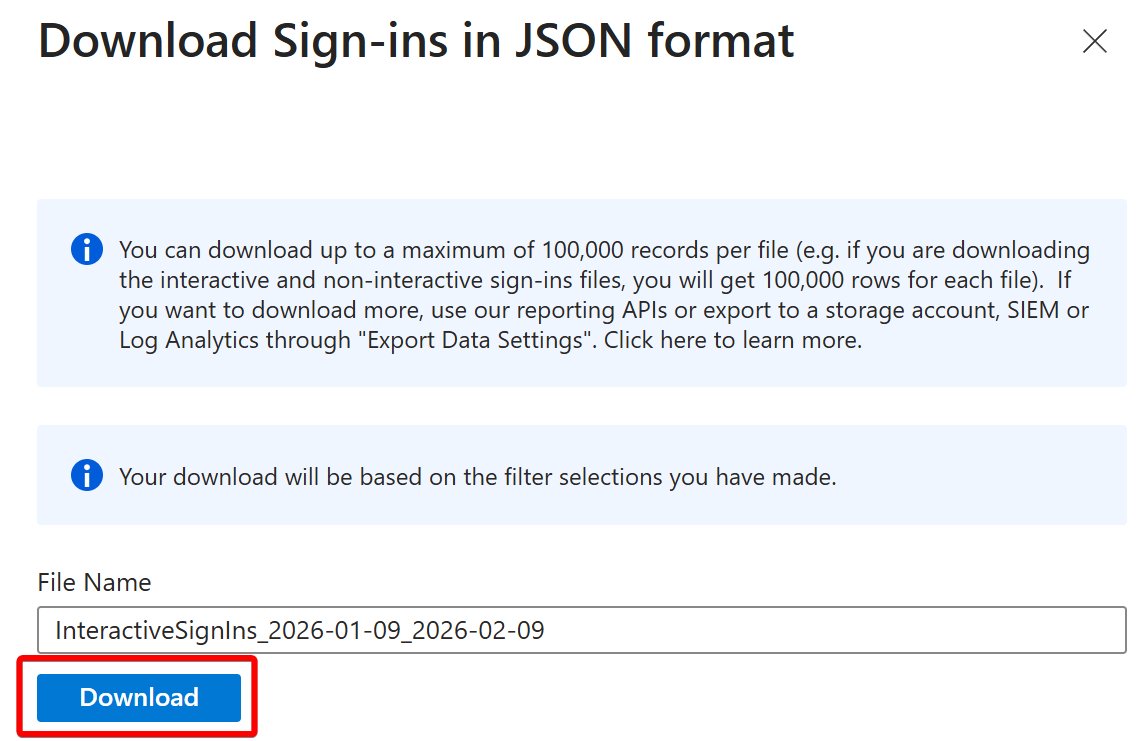
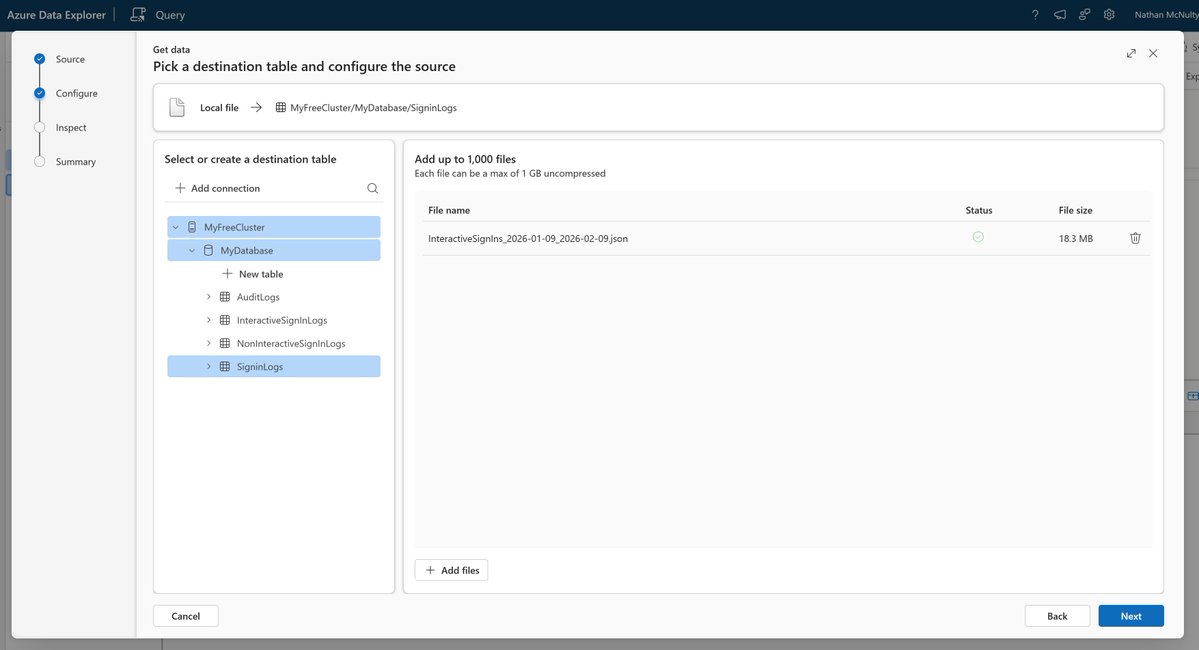
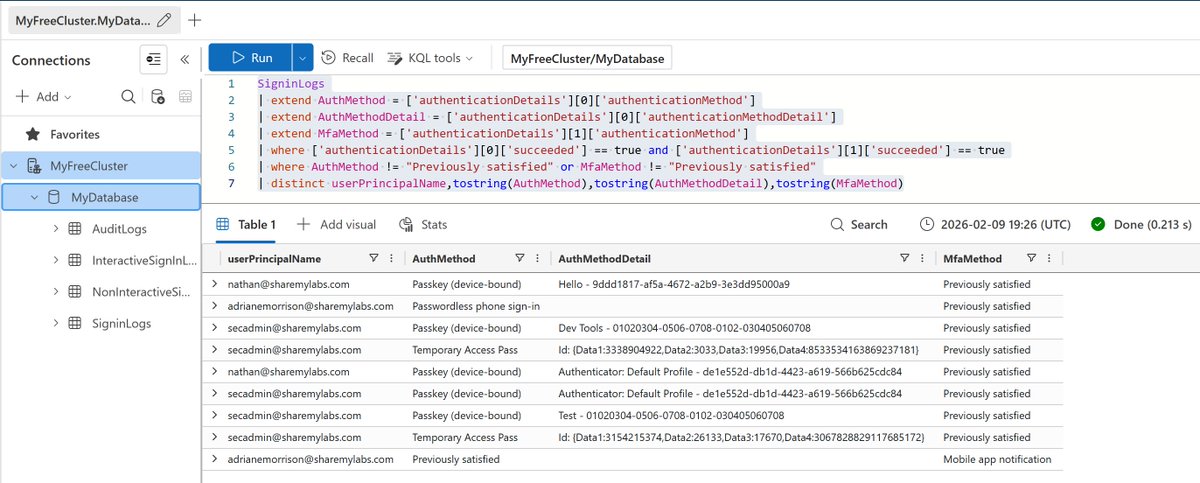
Let's learn about Users in Azure AD :)
In this thread, I'm covering the Azure Portal and Powershell modules. We'll look at Graph API later (setup required).
If you haven't already signed up for a M365 dev account, check the thread below and follow along!
In this thread, I'm covering the Azure Portal and Powershell modules. We'll look at Graph API later (setup required).
If you haven't already signed up for a M365 dev account, check the thread below and follow along!
https://twitter.com/NathanMcNulty/status/1394904334438002690
whoami
I've been managing AAD/O365 for almost a decade, and I absolutely can (and will) be wrong
Please correct me, nerd snipe, whatever your style is, if you see something wrong or have suggestions
I want value here for beginners and veterans alike, but we start with basics
I've been managing AAD/O365 for almost a decade, and I absolutely can (and will) be wrong
Please correct me, nerd snipe, whatever your style is, if you see something wrong or have suggestions
I want value here for beginners and veterans alike, but we start with basics
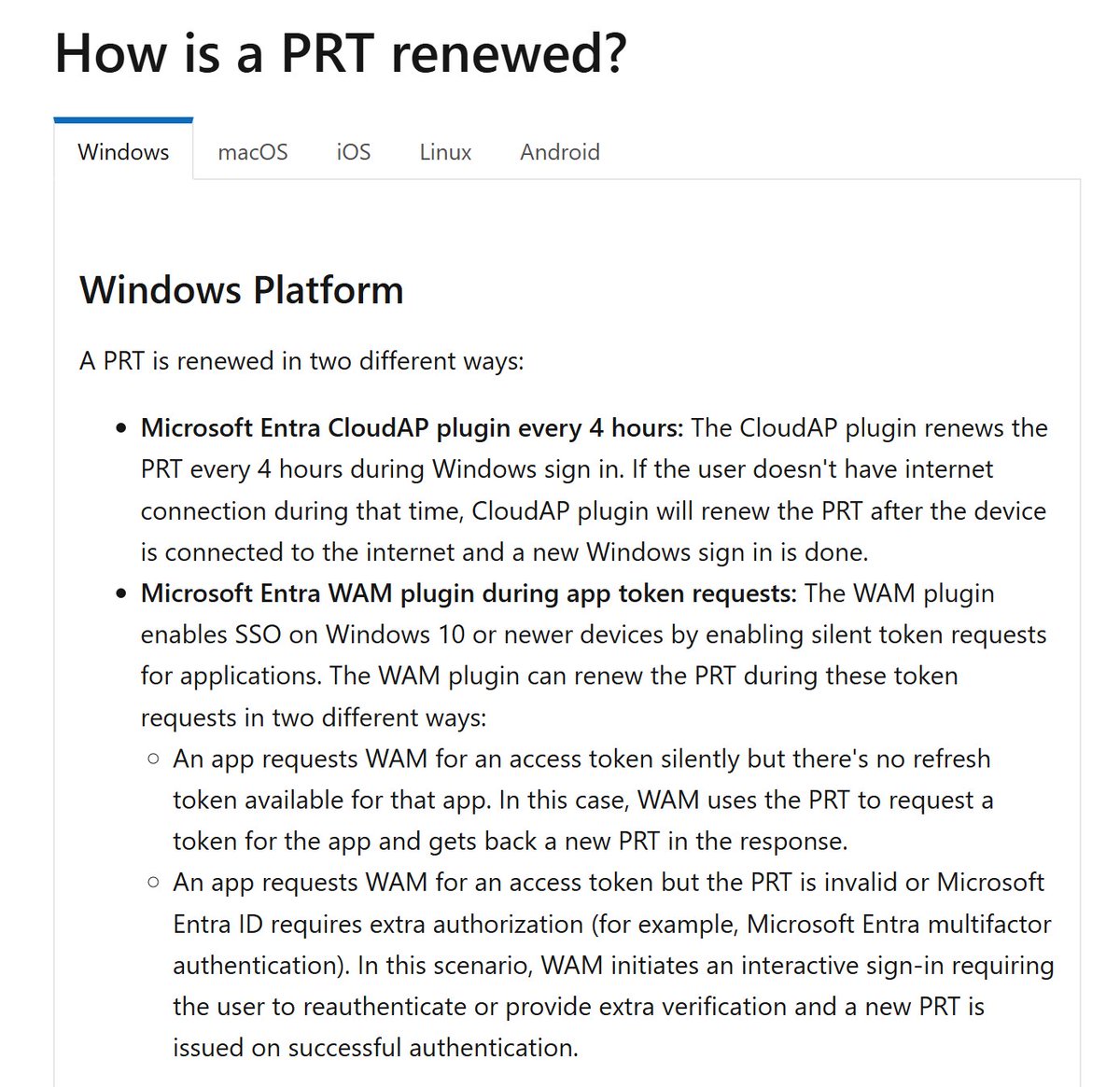
So, let's get started by logging into portal.azure.com with the Global Admin (GA) account for our developer tenant
In the middle of the dashbord, you'll see a link to View Azure Active Directory. Go ahead and click on that ;)
On the left, click Users, then click New User


In the middle of the dashbord, you'll see a link to View Azure Active Directory. Go ahead and click on that ;)
On the left, click Users, then click New User


Something that will make these threads a little more unique is that I will cover less known topics, like break glass accounts
Use the Create user option to create 2 break glass accounts giving them GA (see pictures)
Best practices (learn for prod):
docs.microsoft.com/en-us/azure/ac…



Use the Create user option to create 2 break glass accounts giving them GA (see pictures)
Best practices (learn for prod):
docs.microsoft.com/en-us/azure/ac…




I will cover Conditional Access/MFA in a different thread, but if this were prod, we'd be all over those policies right now :p
In a prod environment, you will want to spend time designing good CA policies for these accounts. Emergency access vs security is a tricky balance.
In a prod environment, you will want to spend time designing good CA policies for these accounts. Emergency access vs security is a tricky balance.
Next, let's look at Bulk operations.
And by look at, I mean I'll mention it's there but good luck getting it to work.
This has always been a pain and doesn't really scale you. Honestly, just skip this and use Powershell.
Import-Csv is your friend:
docs.microsoft.com/en-us/powershe…

And by look at, I mean I'll mention it's there but good luck getting it to work.
This has always been a pain and doesn't really scale you. Honestly, just skip this and use Powershell.
Import-Csv is your friend:
docs.microsoft.com/en-us/powershe…


In the Portal, if you click on a User, you can view the details about them.
This view can be extremely helpful for help desk/support staff, and it is much nicer than AD Users and Computers.
You'll notice the ability to edit, reset password, kill sessions, and delete at the top.

This view can be extremely helpful for help desk/support staff, and it is much nicer than AD Users and Computers.
You'll notice the ability to edit, reset password, kill sessions, and delete at the top.


I created a GitHub repo for these M365 threads, and I will continue to add to it as I go.
The install commands seen in the images can be found there, and I've also included links to the Docs for each module.
Commands and scripts (later) will go here too
github.com/nathanmcnulty/…
The install commands seen in the images can be found there, and I've also included links to the Docs for each module.
Commands and scripts (later) will go here too
github.com/nathanmcnulty/…
To get up and running quickly, here's what I did. For best security, you should totally check the docs if you aren't sure if this is safe ;)
Install-Module -Name Az -Scope CurrentUser -Repository PSGallery -Force
Install-Module AzureADPreview
Install-Module MSOnline


Install-Module -Name Az -Scope CurrentUser -Repository PSGallery -Force
Install-Module AzureADPreview
Install-Module MSOnline



It will not hurt anything to have all three of these modules installed alongside one another.
Having managed over 45K users in Google Workspace, I can definitively say Microsoft is the only large productivity suite provider that cares about IT admins by providing good tooling ;)
Having managed over 45K users in Google Workspace, I can definitively say Microsoft is the only large productivity suite provider that cares about IT admins by providing good tooling ;)
Let's create a user with the Azure Az Powershell module.
First, we need to connect:
Connect-AzAccount
Then we can create:
New-AzADUser -DisplayName "Test User 1" -UserPrincipalName "tuser1@domain.onmicrosoft.com" -Password (Read-Host -AsSecureString) -MailNickname "tuser1"

First, we need to connect:
Connect-AzAccount
Then we can create:
New-AzADUser -DisplayName "Test User 1" -UserPrincipalName "tuser1@domain.onmicrosoft.com" -Password (Read-Host -AsSecureString) -MailNickname "tuser1"


Now, let's create a user with the Azure AD module
Connect:
Connect-AzureAD
Create a password profile:
$PasswordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile
$PasswordProfile.Password = "Haha, nice try!"
What what? Oh yeah, hang on.
Connect:
Connect-AzureAD
Create a password profile:
$PasswordProfile = New-Object -TypeName Microsoft.Open.AzureAD.Model.PasswordProfile
$PasswordProfile.Password = "Haha, nice try!"
What what? Oh yeah, hang on.

New-AzureADUser cmdlet requires an object be passed into the -PasswordProfile paramter, so we have to create that first.
It's in the docs :p
docs.microsoft.com/en-us/powershe…
The rest of the command is too big for Twitter, so check my repo here:
github.com/nathanmcnulty/…
It's in the docs :p
docs.microsoft.com/en-us/powershe…
The rest of the command is too big for Twitter, so check my repo here:
github.com/nathanmcnulty/…

Last, let's create a user with the MSOnline module :)
Connect:
Connect-MsolService
Create:
New-MsolUser -UserPrincipalName "tuser3@domain.onmicrosoft.com" -DisplayName "Test User 3" -FirstName "Test" -LastName "User 3" -UsageLocation "US" -Password (Read-Host -AsSecureString)

Connect:
Connect-MsolService
Create:
New-MsolUser -UserPrincipalName "tuser3@domain.onmicrosoft.com" -DisplayName "Test User 3" -FirstName "Test" -LastName "User 3" -UsageLocation "US" -Password (Read-Host -AsSecureString)


Now lets look at how to get user details in each module.
My primary 3 uses for Get commands are to view user details (usually troubleshooting), search users and filter (Get-* | Where-Object...), and get an object to pipe into another command (Get-* | Where-Object {...} | Set-*).
My primary 3 uses for Get commands are to view user details (usually troubleshooting), search users and filter (Get-* | Where-Object...), and get an object to pipe into another command (Get-* | Where-Object {...} | Set-*).
Az Azure module:
Get-AzADUser -UserPrincipalName tuser1@domain.onmicrosoft.com
AzureAD module:
Get-AzureADUser -SearchString "tuser2"
MSOnline module:
Get-MsolUser -SearchString "tuser3"
More details can be found in the repo:
github.com/nathanmcnulty/…


Get-AzADUser -UserPrincipalName tuser1@domain.onmicrosoft.com
AzureAD module:
Get-AzureADUser -SearchString "tuser2"
MSOnline module:
Get-MsolUser -SearchString "tuser3"
More details can be found in the repo:
github.com/nathanmcnulty/…



Now let's talk about modifying users. This is where you'll spend a lot of time if you develop automation scripts.
Each module is a little different, so check the docs for the list of attributes.
If you are syncing from on-prem, many attributes cannot be modified in the cloud :(
Each module is a little different, so check the docs for the list of attributes.
If you are syncing from on-prem, many attributes cannot be modified in the cloud :(
To save some time, I've put all of the Set-* commands in the repo:
github.com/nathanmcnulty/…
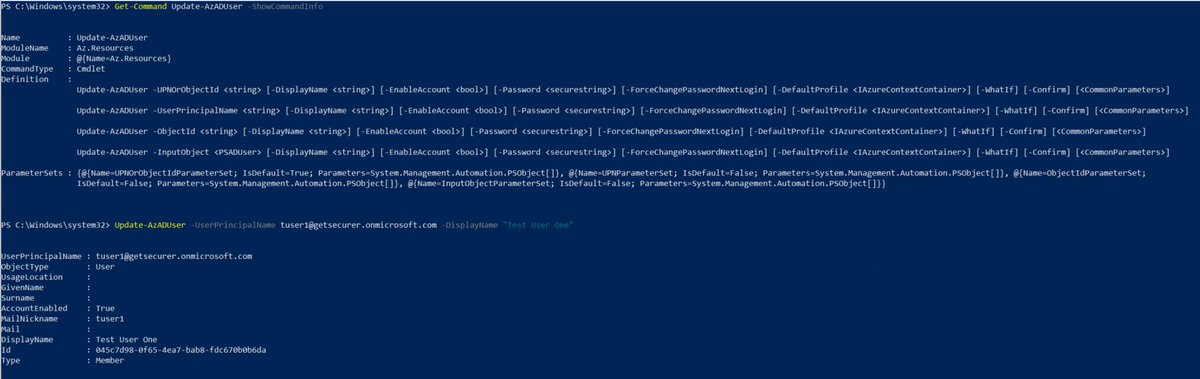
Update-AzADUser is limited compared to the other two. That's why I'd suggest comparing all three and seeing which is the right tool for the job.
Keep an eye on Az modules - changes fast


github.com/nathanmcnulty/…
Update-AzADUser is limited compared to the other two. That's why I'd suggest comparing all three and seeing which is the right tool for the job.
Keep an eye on Az modules - changes fast


Not sure if anyone will notice, but as I was playing with the modules, I tabbed through the options for UserType and discovered something I've never seen before.
Anyone know what a "viral" user type is?
Whatever it is, it doesn't sounds good, and I changed Test User Three to it
Anyone know what a "viral" user type is?
Whatever it is, it doesn't sounds good, and I changed Test User Three to it

The last main function that I'll cover is deleting users.
Again, the commands are too long for Twitter, but you can find them all over on the repo:
github.com/nathanmcnulty/…
These 4 building blocks (New, Get, Set, and Remove) can help us automate user lifecycle in Azure AD.


Again, the commands are too long for Twitter, but you can find them all over on the repo:
github.com/nathanmcnulty/…
These 4 building blocks (New, Get, Set, and Remove) can help us automate user lifecycle in Azure AD.



Now that we have a handle on users, the next thread will be building groups. With that, we can do licensing, apps, and other fun stuff.
Hopefully you can see how you might be able to write scripts to build a lightweight IAM, and later, we'll talk AAD Connect and MS Graph :)
Hopefully you can see how you might be able to write scripts to build a lightweight IAM, and later, we'll talk AAD Connect and MS Graph :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh