
Freenode admins hijacked the #grapheneos and #grapheneos-offtopic channels due to us migrating to Matrix rooms:
gist.github.com/thestinger/eb9…
They removed our channel moderation privileges, changed the topic and set the channel to invite-only preventing users from joining/rejoining.
gist.github.com/thestinger/eb9…
They removed our channel moderation privileges, changed the topic and set the channel to invite-only preventing users from joining/rejoining.
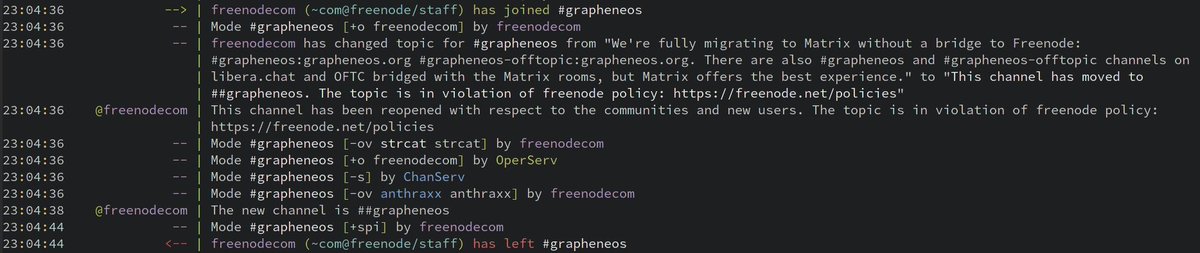
It justifies our urgent migration away from freenode.
Be careful what you say in private messages on freenode because the new admins can easily read them and may retaliate if you speak badly about them.
See arstechnica.com/gadgets/2021/0… and vice.com/en/article/m7e… for more details.
Be careful what you say in private messages on freenode because the new admins can easily read them and may retaliate if you speak badly about them.
See arstechnica.com/gadgets/2021/0… and vice.com/en/article/m7e… for more details.
Please join #grapheneos:grapheneos.org and #grapheneos-offtopic:https://t.co/f02rVtJa8a via Matrix. Links to join via the Element web client:
app.element.io/#/room/#graphe…
app.element.io/#/room/#graphe…
Element (web, desktop or mobile) with matrix.org is one option.
app.element.io/#/room/#graphe…
app.element.io/#/room/#graphe…
Element (web, desktop or mobile) with matrix.org is one option.
Very unfortunate we can't redirect users anymore.
IRC users may prefer weechat-matrix as a client. It works well for public rooms like our official chat rooms but lacks decent end-to-end encryption (E2EE) support for use with private rooms. Element has the best support for E2EE.
IRC users may prefer weechat-matrix as a client. It works well for public rooms like our official chat rooms but lacks decent end-to-end encryption (E2EE) support for use with private rooms. Element has the best support for E2EE.
Our Matrix rooms are bridged to the Telegram groups t.me/grapheneos and t.me/grapheneosofft… along with #grapheneos and #grapheneos-offtopic on both libera.chat and OFTC.
Matrix offers the best experience and most of our community is using Matrix directly.
Matrix offers the best experience and most of our community is using Matrix directly.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



