
1/ Today we shared our IO Threat Report, an analytical paper that dives into the 150+ CIB takedowns across 50+ countries that FB’s Threat Intel team discovered over the past 3 years. The report IDs adversary TTPs, trends, and provides recs for tackling IO: about.fb.com/wp-content/upl…
2/ We also released a summary dataset of all of our takedowns since 2017 alongside the report itself. Check that out here (at the end of the report) about.fb.com/wp-content/upl…
3/ We’ve reported on every CIB takedown since the advent of the CIB policy in 2017, but those reports tend to focus on the individual operations’ behavior and attribution. We felt it was important to also provide a strategic look at the ecosystem of IO uncovered between 2017-2020
4/ Some key statistics during that period:
- 150+ CIB takedowns from 2017-2020
- 50+ countries
- 30+ languages
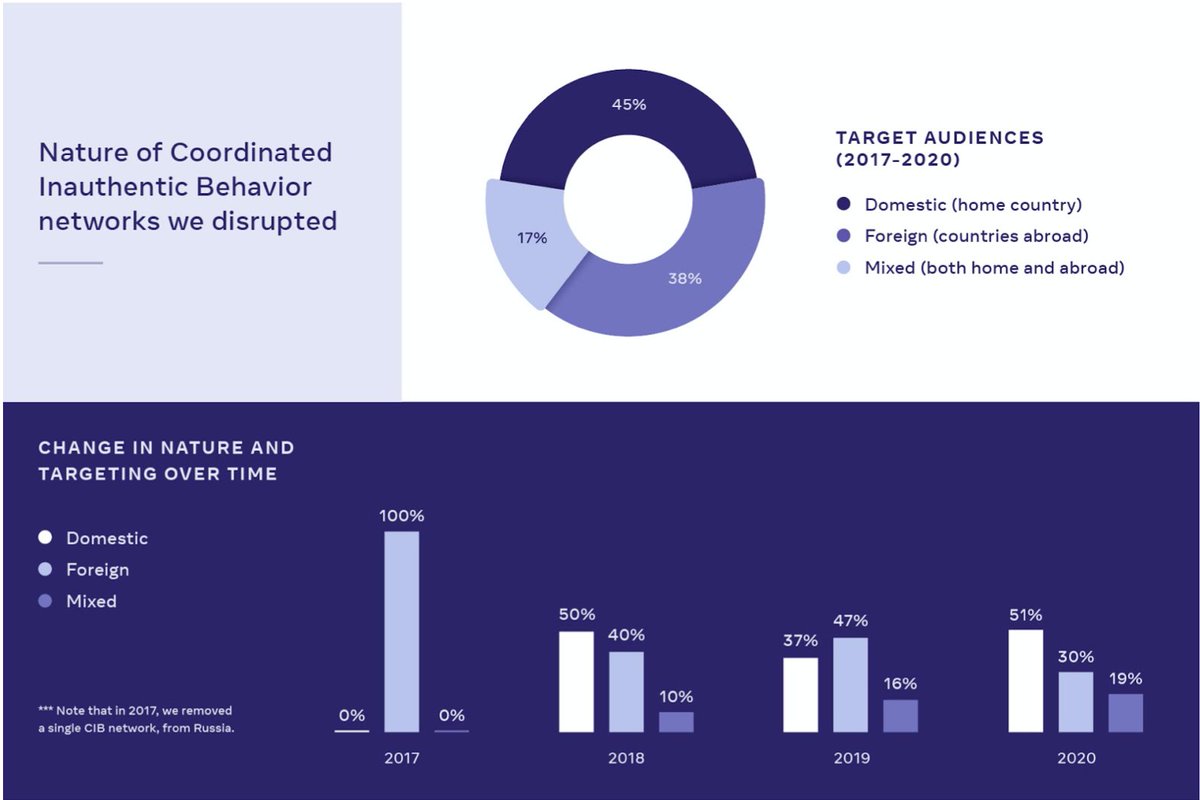
- 45% domestic-targeted
- 38% foreign-targeted
- 17% mixed targeting
- 150+ CIB takedowns from 2017-2020
- 50+ countries
- 30+ languages
- 45% domestic-targeted
- 38% foreign-targeted
- 17% mixed targeting
5/ Where did those operations come from?
Russia (27): mainly IRA/Prigozhin or Russian intel
Iran (23): gov-linked broadcasters and media
Myanmar (9): primarily linked to the Burmese military
USA (9): mix of fringe political groups and PR agencies
Ukraine (8): PR agencies and pols
Russia (27): mainly IRA/Prigozhin or Russian intel
Iran (23): gov-linked broadcasters and media
Myanmar (9): primarily linked to the Burmese military
USA (9): mix of fringe political groups and PR agencies
Ukraine (8): PR agencies and pols

6/ Key trends we observed over those 3 years:
1: Shift to IO actors targeting smaller communities
2: Blurring of authentic and inauthentic activity
3: Perception hacking
4: IO-for-hire
5: Increased operational security
6: Platform diversification
1: Shift to IO actors targeting smaller communities
2: Blurring of authentic and inauthentic activity
3: Perception hacking
4: IO-for-hire
5: Increased operational security
6: Platform diversification
7/ So how did these trends play out in the 2020 US elections? We saw more than a dozen ops targeting public debate in the US around the election, including 5 ops from Russia, 5 from Iran, and 5 from the US. We didn’t see much CIB from China focused on the US ahead of the election 

8/ Russia’s campaigns targeting the US in 2020 were largely ineffective. We saw ops from the GRU + IRA, which focused on the US and other countries. These ops often used unwitting authentic intermediaries, incl journos + activists, to write their content. theguardian.com/technology/202…
9/ Iran’s activity was more varied, employing tactics we’d previously seen from Iran in ops linked to the IRIB while also deploying “perception hacking” tactics off-social-media by posing as the Proud Boys to threaten voters in the US reuters.com/article/us-usa…
10/ Domestic operations targeting the US election were as common as those from Russia or Iran - an important data point in the seriousness of domestic IO. These networks were mainly run by conspiracy or fringe political groups, PR agencies/consulting firms, and media websites. 

11/ So what’s next? We expect IO actors to move into grayer spaces, blending foreign and domestic and authentic and inauthentic voices. The growth of non-state actors in the IO arena further complicates this.
12/ Financially-motivated ops (IO-for-hire) will continue to adopt the TTPs of sophisticated IO. It's even important to avoid overstating the influence and impact of state actors because it plays directly into the hands of those seeking to erode trust in democratic institutions.
13/ And we’ll continue to see IO actors weaponize moments of uncertainty, like we saw with critical elections, and key civic moments. Countering those efforts will require collaboration btwn platforms, governments, industry, media, and civil society.
14/ In the past few years an incredible community grew to detect, disrupt, and deter these ops. Investigative journos, academics, gov analysts, and TI teams in industry fight tooth and nail to counter IO, We hope this report can help inform that community and inspire new research
15/ The fight is not over - but in these last few years the defenders have improved considerably and the playing field is turning. And for everyone out there researching, investigating, disrupting, and innovating - thank you for fighting to make the information ecosystem safer.
And from my colleague @benimmo -
https://twitter.com/benimmo/status/1397524596333682691?s=20
• • •
Missing some Tweet in this thread? You can try to
force a refresh




