
Analogies comparing "economics" and "cybersecurity" usually understand neither.
That's demonstrated in the item below using economics concept "market for lemons".
That's demonstrated in the item below using economics concept "market for lemons".
https://twitter.com/ciaranmartinoxf/status/1406878901230571521
The report this article refers to is below, as is the Wikipedia article on economics principle.
debatesecurity.com/downloads/Cybe…
en.wikipedia.org/wiki/The_Marke…
debatesecurity.com/downloads/Cybe…
en.wikipedia.org/wiki/The_Marke…
"Information asymmetry", the fact the sellers know more than buyers, but it's an issue for ALL buyers/sellers.
The "market for lemons" describes one case of this overall issue, with specific criteria.
The "market for lemons" describes one case of this overall issue, with specific criteria.
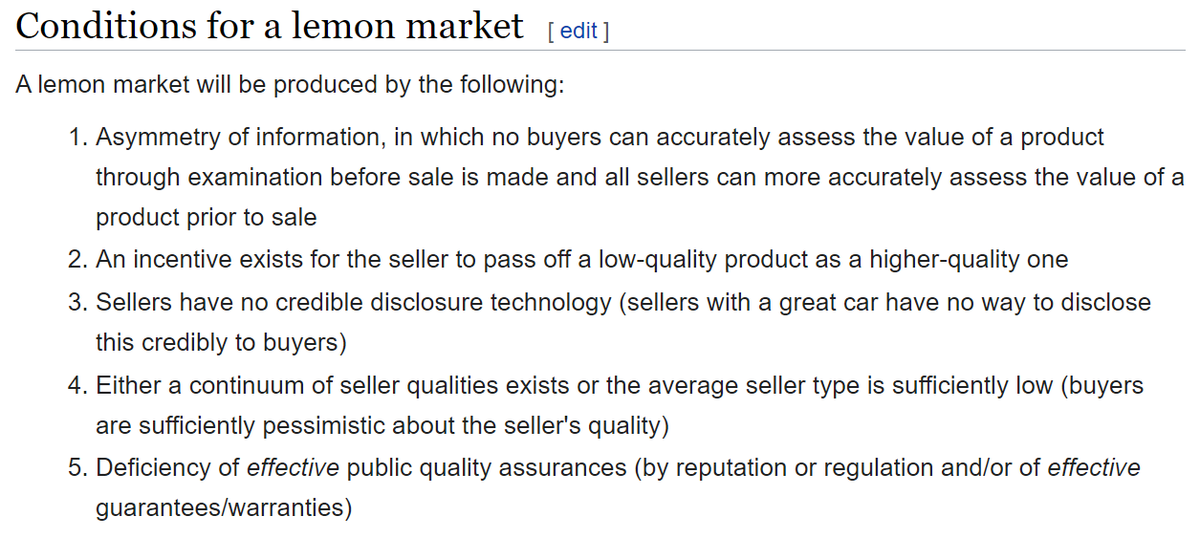
None of these criteria are met in the market for cybersecurity products. Sure, many customers struggle to assess the value of products, but that's absolutely different than the criteria "no customers" can do so. The other items don't match, either.
This is typical example of economics analogies in cybersecurity. People cherry pick something that superficially seems to support their point without any deep understanding of the underlying issue.
The above report understands cybersecurity products even less than it understands economics.
The majority of cybersecurity products are like exercise equipment. Their efficacy depends upon the user rather than the product itself.
The majority of cybersecurity products are like exercise equipment. Their efficacy depends upon the user rather than the product itself.
Cybersecurity is about tradeoffs that no product can help you with. Securing your network is first and foremost about which tradeoffs you've chosen. If you choose bad tradeoffs, no product can help you.
Sure, vendors try to claim a secret sauce, but the majority of their functionality is knowable and predictable. An EDR product seems magical, but customers can demand vendors explain exactly what their products actually do in direct terms.
Big customers also test them. They simply run the same sorts of attacks that hackers do against the EDR in order to learn what value the products provide. These things aren't unknowable black boxes.
...unless you are CISO.
The above report was written by non-technical writers interviewing non-technical CISOs for a non-technical audience.
If you are non-technical, then all of cybersecurity unknowable magic.
The above report was written by non-technical writers interviewing non-technical CISOs for a non-technical audience.
If you are non-technical, then all of cybersecurity unknowable magic.
The "market for lemons" happens because even skilled mechanics evaluating a used car cannot know it's history, and hence, likelihood of future problems.
But in cybersecurity, skilled techies can understand these things. QED: the analogy is flawed.
But in cybersecurity, skilled techies can understand these things. QED: the analogy is flawed.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



