Come join me (the "monster" 😂) as we dive deep into the #WiFi Code inside #RISCV #BL602 (the "wifi chip" 😂)
lupyuen.github.io/articles/pinec…
lupyuen.github.io/articles/pinec…

Many thanks to this hilarious (but truthful) comment on #BL602 😂
https://twitter.com/MisterTechBlog/status/1407339654689476612?s=19
Here's the #BL602 #WiFi Firmware ... Let's find out how it connects to a WiFi Access Point
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

#BL602 #WiFi Manager runs as a Background Task ... Here's how we send requests to WiFi Manager
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

#BL602 #WiFi Manager runs a State Machine ... That connects to the WiFi Access Point in the Background Task
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

To connect to a #WiFi Access Point, #BL602 WiFi Manager sends a request to the Lower MAC Firmware
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

#BL602 #WiFi Manager sends Connect Request to LMAC Firmware thru another Message Queue
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

#BL602 #WiFi Manager talks to LMAC Firmware via Message Queue ... Let's find out how it works
ceva-dsp.com/product/rivier…
ceva-dsp.com/product/rivier…

#BL602 #WiFi Driver talks to LMAC Firmware ... By writing to a Message Buffer and triggering an Interrupt
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

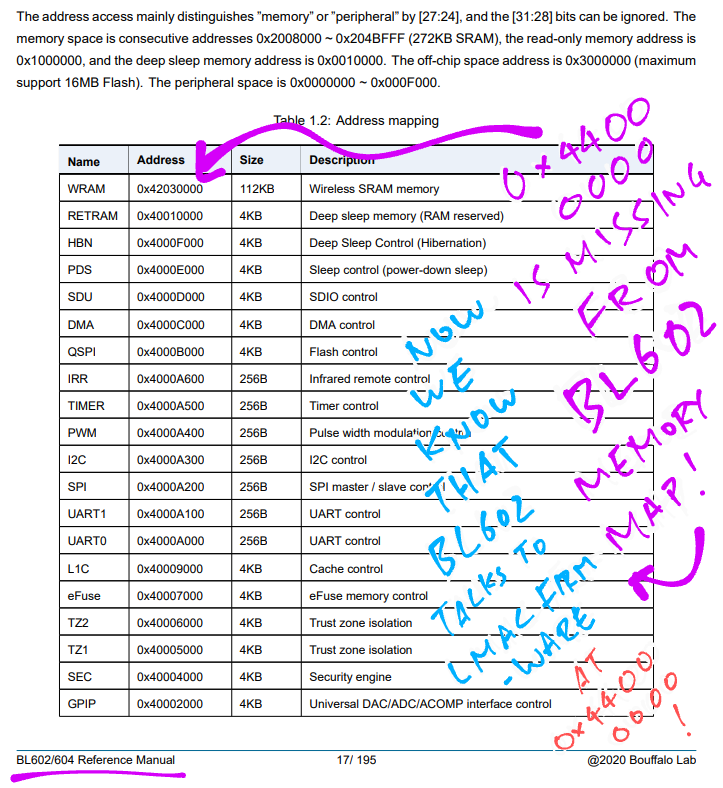
#BL602 WiFi Driver triggers LMAC Interrupt ... By writing to Address 0x4400 0000 ... Let's see what's at 0x4400 0000
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

But 0x4400 0000 is NOT documented in #BL602 Reference Manual! 😲 Now we know a secret ... BL602 talks to LMAC Firmware at Address 0x4400 0000 🤫
github.com/bouffalolab/bl…
github.com/bouffalolab/bl…
Moving away from LMAC Firmware (since we got no code) ... Let's study the mysterious #BL602 #WiFi Library "libwifi" ... Which has been decompiled into C by BraveHeartFLOSSDev
github.com/BraveHeartFLOS…
github.com/BraveHeartFLOS…

#BL602 Firmware starts the #WiFi Stack ... By creating a Background Task that runs wifi_main ... Let's hunt for wifi_main
github.com/lupyuen/bl_iot…
github.com/lupyuen/bl_iot…

"wifi_main" lives in the mysterious #BL602 #WiFi Library "libwifi" ... Let's study the decompiled C code (thanks to BraveHeartFLOSSDev and Ghidra)
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

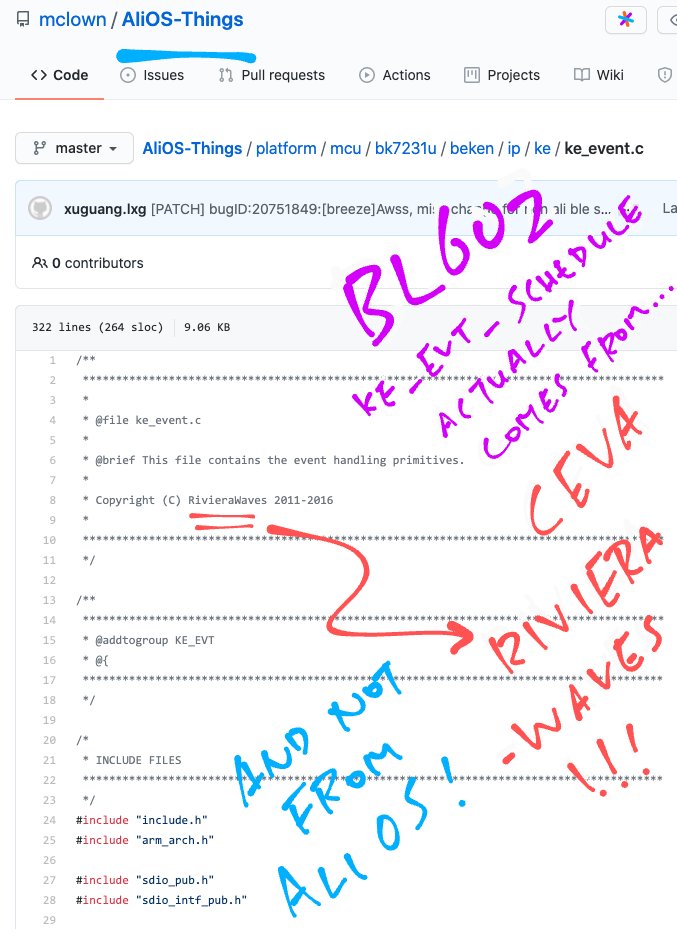
#BL602 "wifi_main" calls "ke_evt_schedule" to do #WiFi Tasks ... GitHub Search shows that "ke_evt_schedule" is also defined in ... AliOS! 😲
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

But does "ke_evt_schedule" really come from AliOS? Not quite ... "ke_evt_schedule" actually comes from ... CEVA RivieraWaves! 😲
github.com/mclown/AliOS-T…
github.com/mclown/AliOS-T…
Now the #BL602 #WiFi Stack gets clearer ... We're actually reading the WiFi Driver Code by CEVA RivieraWaves! 💡
ceva-dsp.com/product/rivier…
ceva-dsp.com/product/rivier…

Lesson Learnt: GitHub Search is our very good friend for Reverse Engineering! 👍
github.com/search?l=C&o=a…
github.com/search?l=C&o=a…

The AliOS / RivieraWaves code we saw earlier was for Beken BK7231U WiFi + BLE SoC ... Is it related to #BL602? 🤔
bekencorp.com/en/goods/detai…
bekencorp.com/en/goods/detai…

AliOS for Beken BK7231U WiFi SoC contains LMAC Firmware Code ... Is this the same LMAC Firmware that runs on #BL602's #WiFi Radio? 🤔 Super Exciting!
github.com/lupyuen/AliOS-…
github.com/lupyuen/AliOS-…

From Now On: We shall read and understand the AliOS / RivieraWaves Source Code ... While comparing it with the Decompiled Code for #BL602 libwifi ... Just to be sure that they are the same 🤝
github.com/lupyuen/AliOS-…
github.com/lupyuen/AliOS-…

Back to ke_evt_schedule, the function in #BL602 #WiFi Driver Kernel that handles every WiFi Event ... Let's hunt for ke_evt_hdlr and discover the WiFi Events
github.com/lupyuen/AliOS-…
github.com/lupyuen/AliOS-…
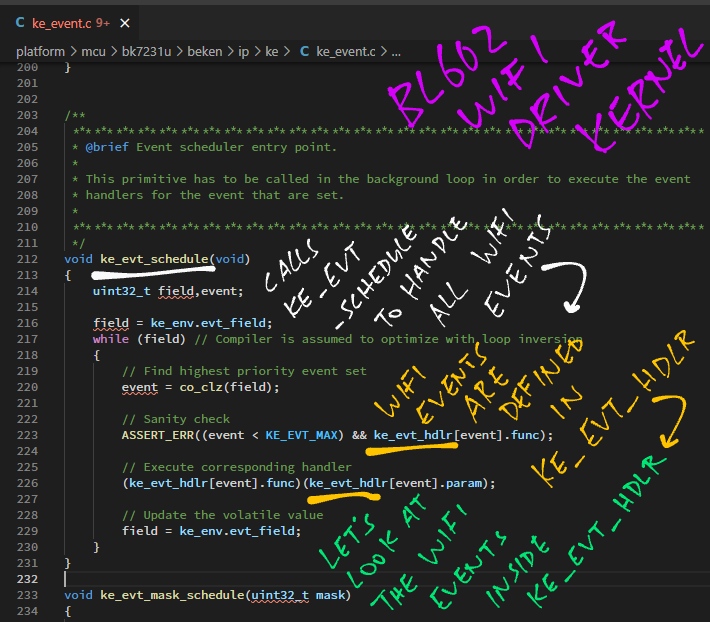
Here are the #WiFi Event Handlers for #BL602 WiFi Kernel ... txl_payload_handle looks interesting ... Let's hunt for it
github.com/lupyuen/AliOS-…
github.com/lupyuen/AliOS-…

txl_payload_handle handles #BL602 #WiFi Payloads by doing ... nothing! But txl_payload_handle_backup seems to be the right function that handles WiFi Payloads 🤔
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

#BL602 #WiFi Payload Handler calls rxu, txl and txu functions ... Fortunately these are defined in the AliOS / RivieraWaves Source Code we saw earlier
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

Here's the Decompiled #BL602 #WiFi Supplicant that handles WiFi Authentication ... Decompiled code looks readable
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

Thankfully #BL602 #WiFi Library libwifi was compiled with Assertions Enabled ... Makes Reverse Engineering simpler 👍
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

Let's do Quantitative Analysis of the Decompiled #BL602 #WiFi Demo Firmware ... How many lines of code do we actually need to Reverse Engineer ... Now that we've found some matching source files?
github.com/lupyuen/bl602n…
github.com/lupyuen/bl602n…

Load the Decompiled #BL602 #WiFi Functions into a spreadsheet ... For easier crunching
Google Sheets: docs.google.com/spreadsheets/d…
Google Sheets: docs.google.com/spreadsheets/d…

Matching the Decompiled #BL602 #WiFi Functions with AliOS / RivieraWave Source Code ... And identifying the differences
Google Sheets: docs.google.com/spreadsheets/d…
Google Sheets: docs.google.com/spreadsheets/d…

Work In Progress: What's inside the #BL602 #WiFi Demo Firmware ... And how many lines of code need to be Reverse Engineered
Google Sheets: docs.google.com/spreadsheets/d…
Google Sheets: docs.google.com/spreadsheets/d…

• • •
Missing some Tweet in this thread? You can try to
force a refresh