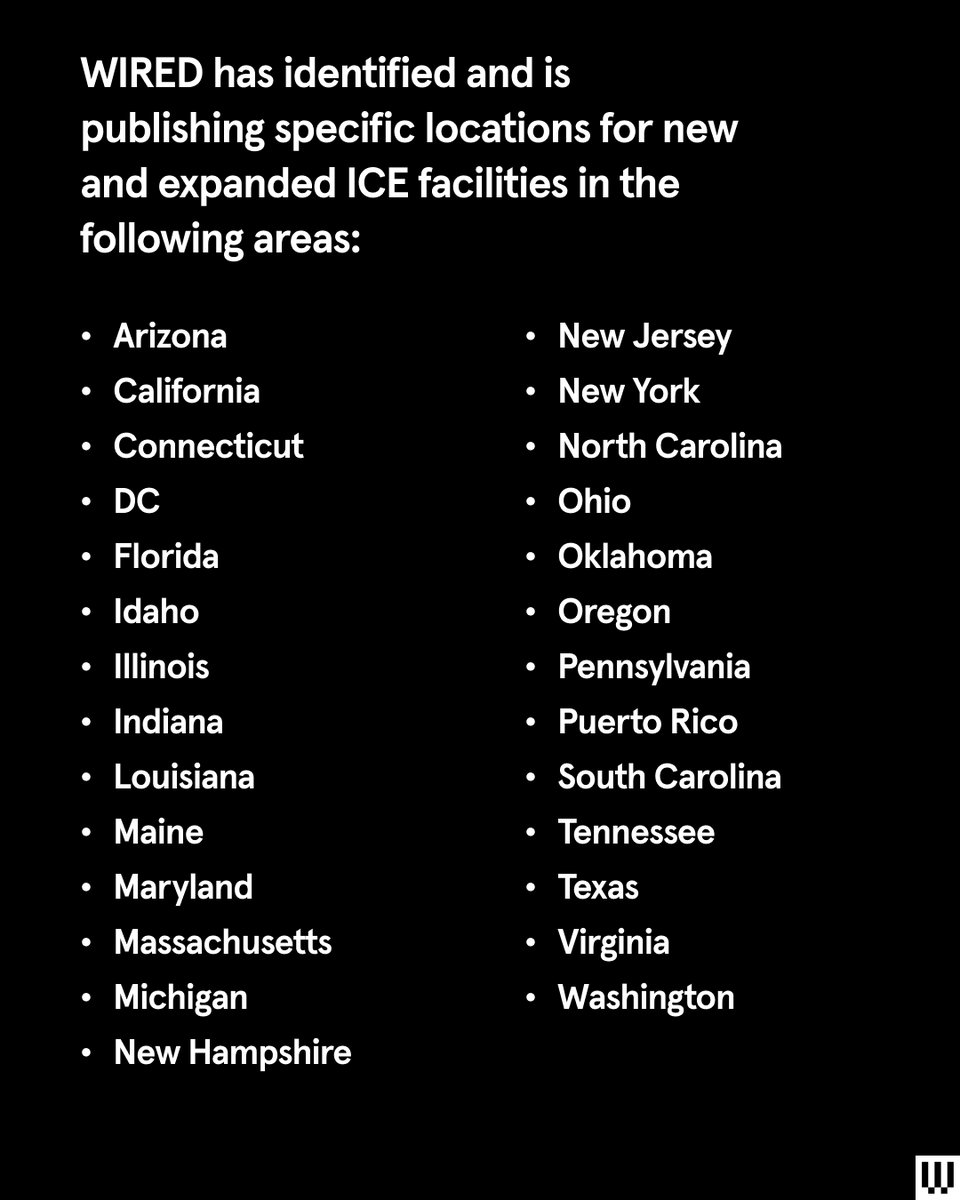
Browser extensions are extremely useful and generally just make life on the web more convenient, but they have the potential to be a serious security risk. wired.trib.al/Mmn3yZd 1/
But don’t let that discourage you from using your favorite extensions. To help you make sure your browser extensions are safe, here's how to run an effective audit. 2/
Always do your research before installing an add-on—check the reviews from other users and reviews on the web. See when the extension was last updated and be sure to look for indications that the add-on has changed hands recently. 3/
To see the extensions you have installed in Chrome, click the three dots (top right), then choose More Tools and Extensions. For Details, click next to any extension to reveal more information about it. Extensions can be temporarily disabled or removed completely. 4/ 

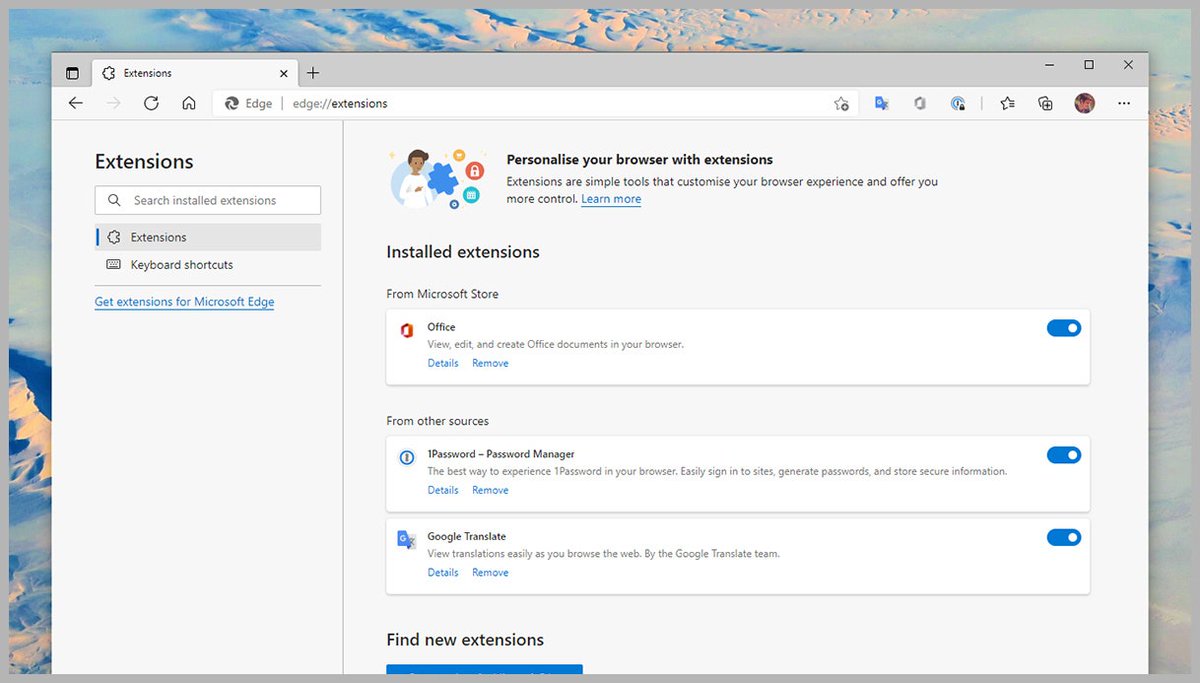
Microsoft Edge is based on the same code as Google Chrome, so the process will look about the same. You’ll click on Details to see the permissions granted to an extension, which sites it has access to, and whether or not an extension can run in Edge's InPrivate mode. 5/ 
For Firefox, simply click the menu button (three horizontal lines, top right), then tap Add-ons and Themes and Extensions to get to your extensions. Click on any extension toggle switch to disable or enable it. 6/ 

In Safari on macOS, open the Safari menu and select Preferences, then switch to the Extensions tab. This is where all of your installed add-ons are, the currently active ones will have a blue tick next to them. Change as desired. 7/ 

In addition to these tips, be sure to keep your computer and its applications up to date. Run regular malware scans. That'll go a long way toward minimizing the risk posed by potentially dodgy extensions. Happy browsing. wired.trib.al/Mmn3yZd 8/
Fourth of July Sale! Subscribe to WIRED today for just $5 & get unlimited access to all the stories on WIRED.com. wired.trib.al/f3r0g6N
End of thread
End of thread
• • •
Missing some Tweet in this thread? You can try to
force a refresh