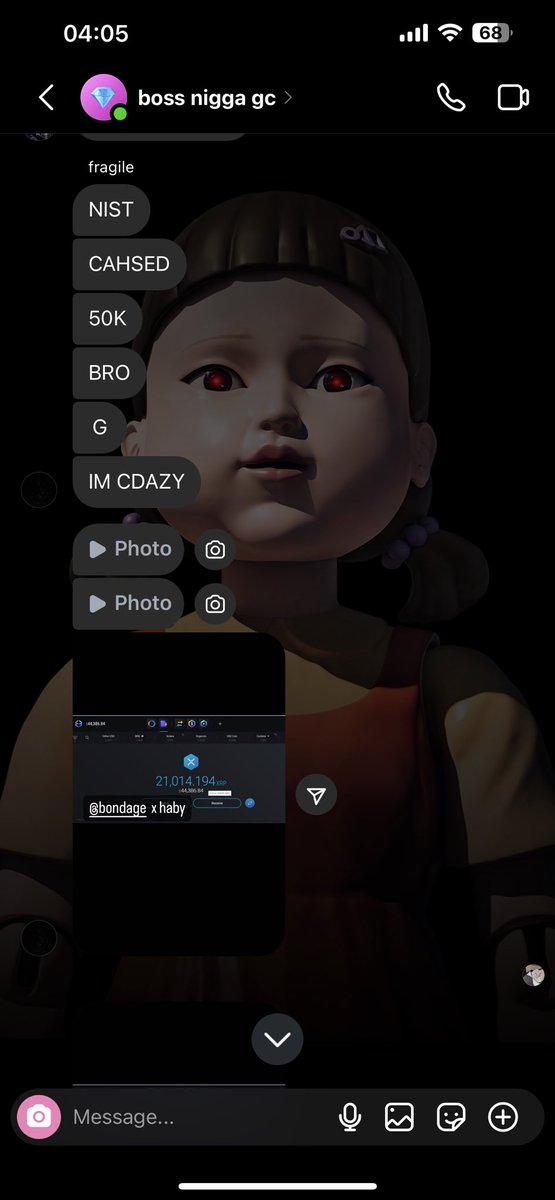
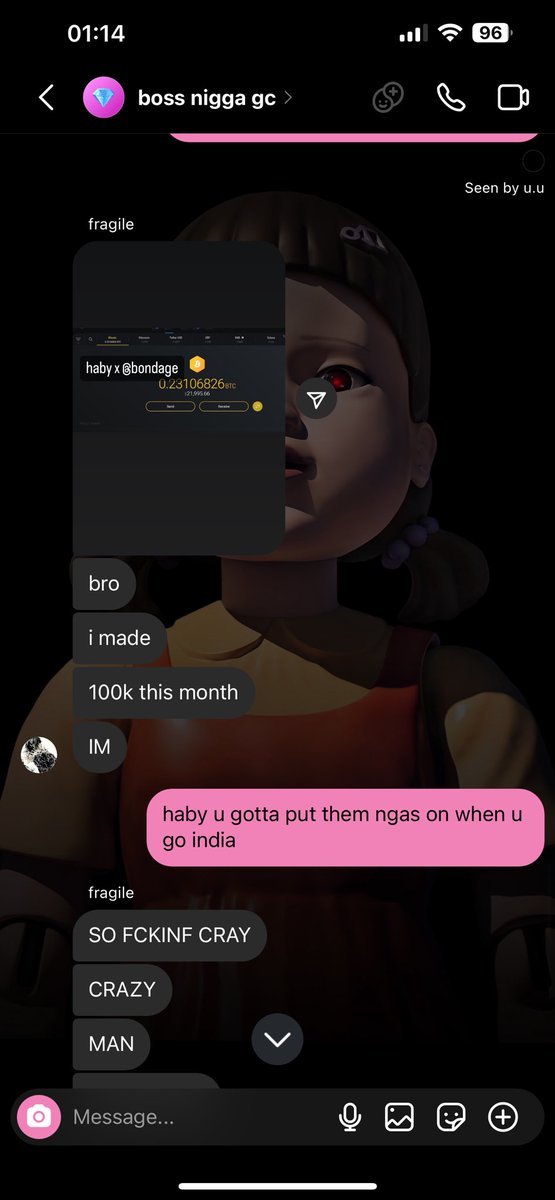
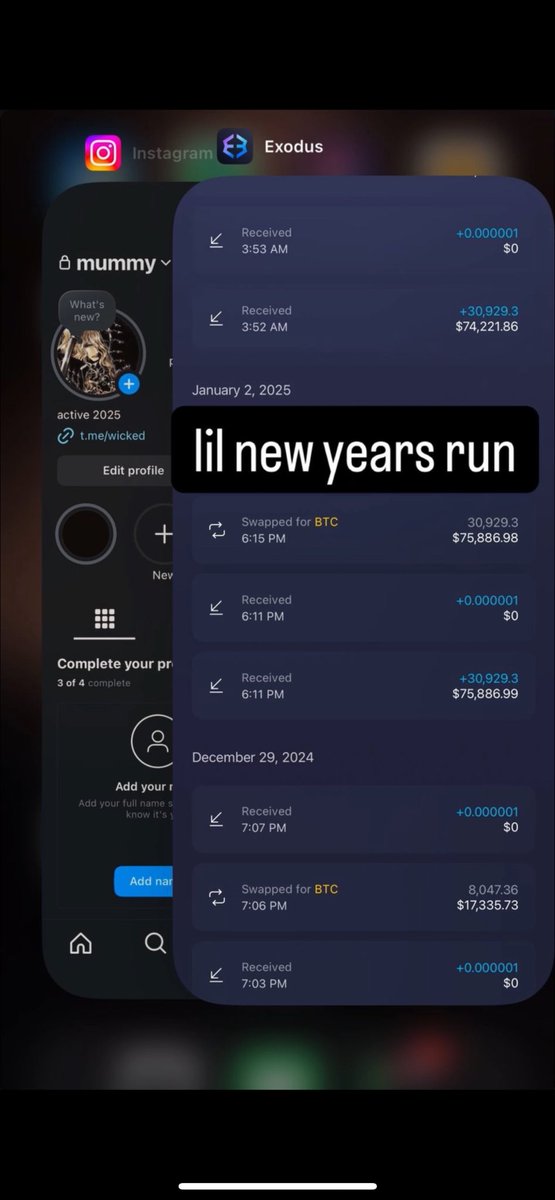
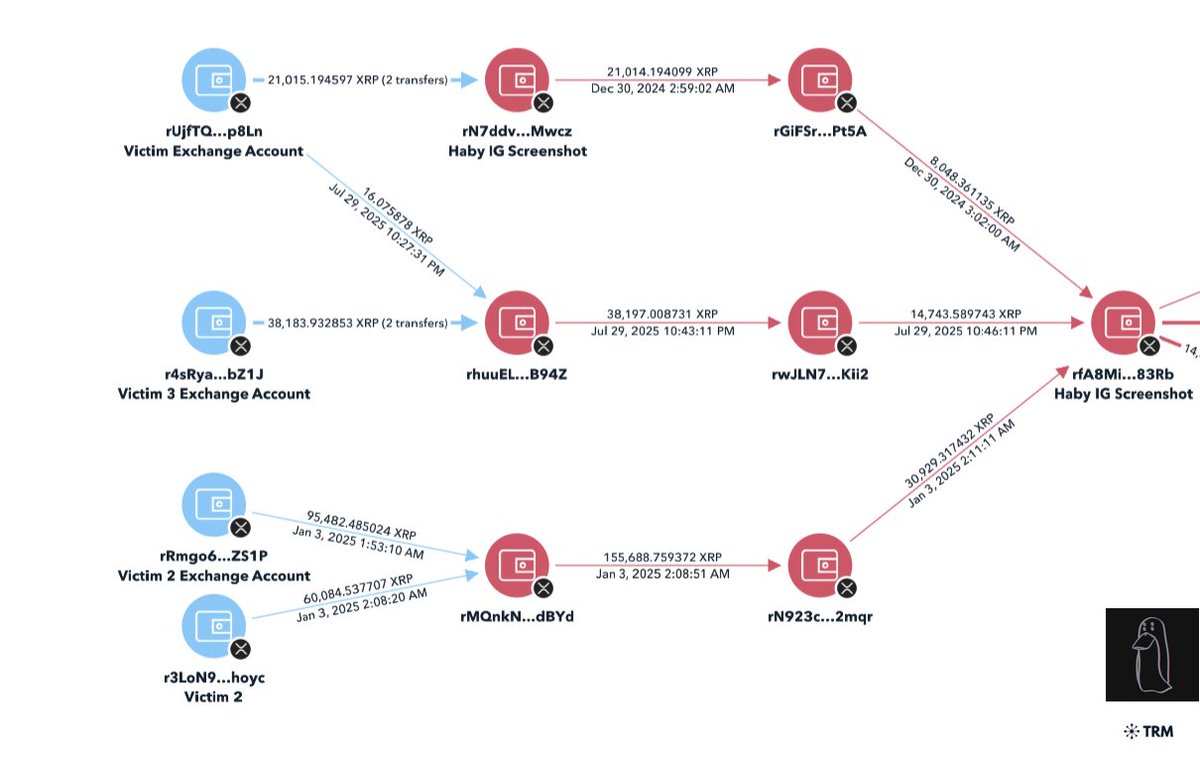
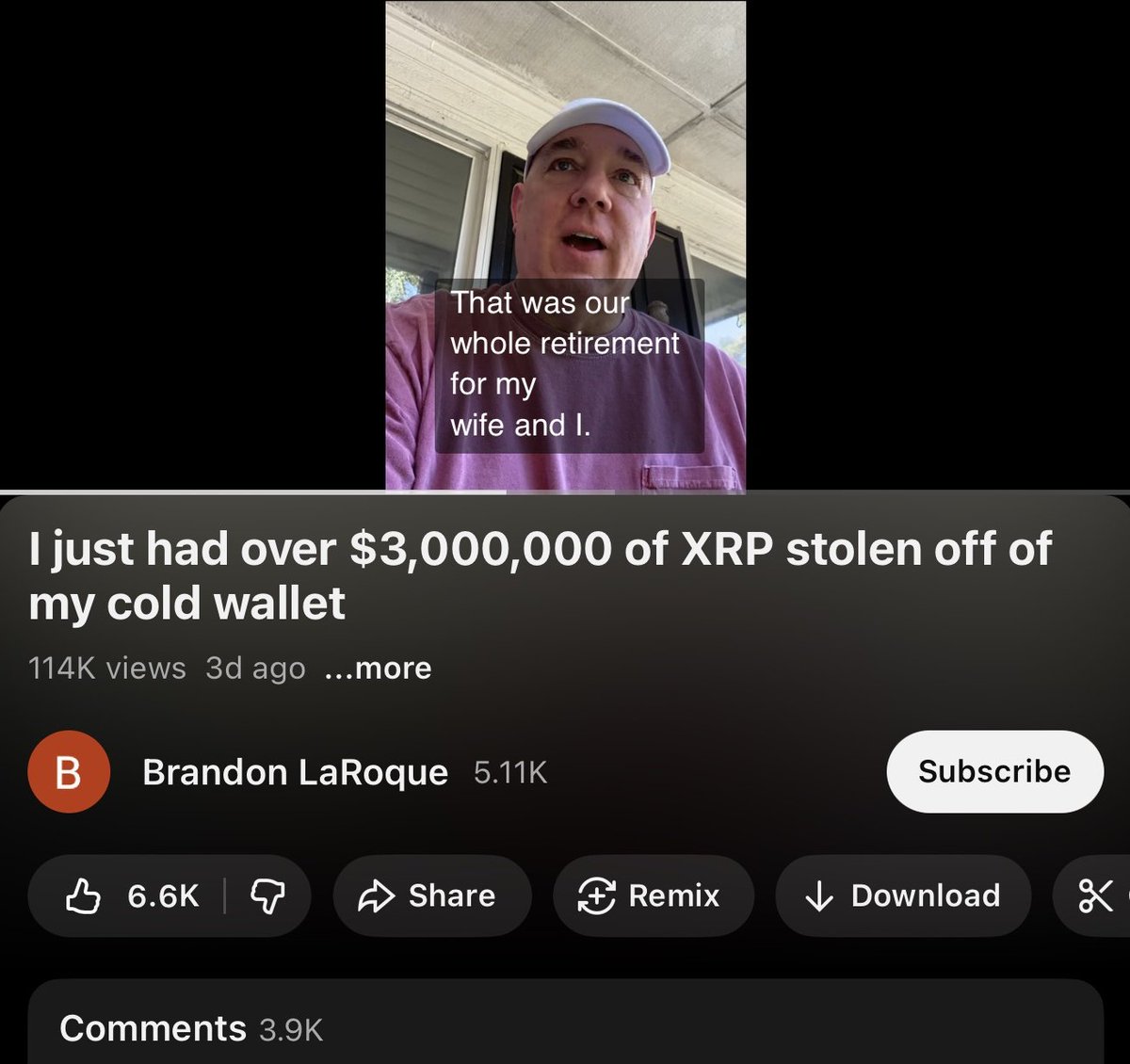
1/ Welcome to the bull run of 2020/2021. It’s up only (was), valuations are at ATH, and your favorite influencer can be a VC.
New funds pop up on a weekly basis yet at the same time invest/incubate a billion projects at once. How are they so efficient you might ask?
👇👇👇
New funds pop up on a weekly basis yet at the same time invest/incubate a billion projects at once. How are they so efficient you might ask?
👇👇👇
2/ Let me introduce you to Moonrock Capital.
In 2018 Johnathon Habicht & Simon Dedic founded Blockfyre; a blockchain advisory firm based in Germany. In 2020 this was acquired by Tixl. In between that period in 2019 Moonrock Capital was formed by them.

In 2018 Johnathon Habicht & Simon Dedic founded Blockfyre; a blockchain advisory firm based in Germany. In 2020 this was acquired by Tixl. In between that period in 2019 Moonrock Capital was formed by them.


3/ After the Scott Melker incident someone close to the team at Moonrock & Blockfyre messaged me about the firm and all that went on.
Let’s dive into two of the projects ($POLK & $PMON) incubated by Moon Rock Capital a bit deeper to see if they did set the “standard”.
Let’s dive into two of the projects ($POLK & $PMON) incubated by Moon Rock Capital a bit deeper to see if they did set the “standard”.

4/ Polkamon ($PMON)
As one of the largest marketing failures this bull run the chart exemplified suspicious activity.
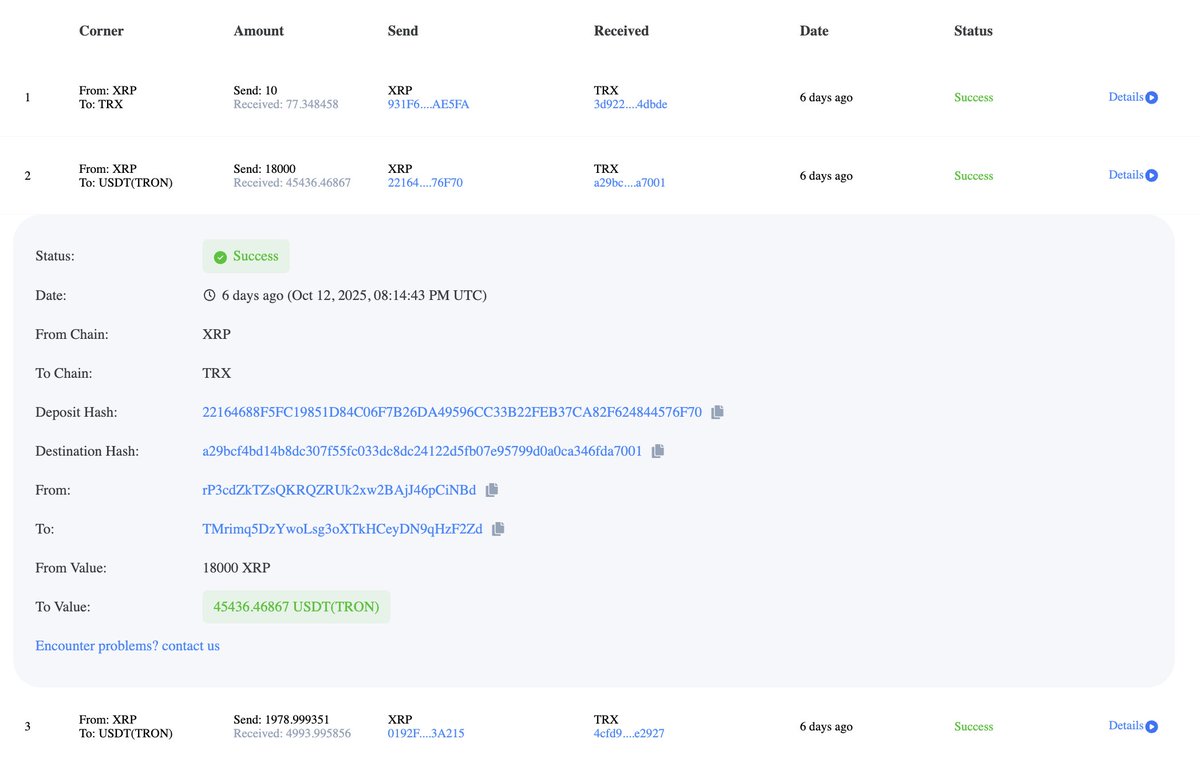
In doing so I reviewed the entire transaction history from launch to June. Below is a brief summary of my findings.
As one of the largest marketing failures this bull run the chart exemplified suspicious activity.
In doing so I reviewed the entire transaction history from launch to June. Below is a brief summary of my findings.

5/ It’s clear the only thing that MoonRock helped them succeed with was pump investors/insiders funds and dump on retail.
Below is the typical lifecycle of the “Moon Rock incubation standard”.
Below is the typical lifecycle of the “Moon Rock incubation standard”.

6/ Polkamarkets ($POLK)
As another incubation you might think $PMON was a one time event.
Below is a graph with all of the largest (cumulative) sells in the first 4 weeks. Many of the wallets received tokens from other IDO’s as well.

As another incubation you might think $PMON was a one time event.
Below is a graph with all of the largest (cumulative) sells in the first 4 weeks. Many of the wallets received tokens from other IDO’s as well.


7/ Now you’re starting to see the pattern? If you’re still not convinced here are some other projects that they invested in.
I’ve included the investment announcement date, token launch date, and ATH date in the chart.
($KYL, $DAFI, $LKR, $CGG)



I’ve included the investment announcement date, token launch date, and ATH date in the chart.
($KYL, $DAFI, $LKR, $CGG)




8/ All your favorite CT influencers work with the VC’s and Marketing firms for a collective shilling campaign. Many do not disclose they were compensated in some capacity. They are placed into groupchats organized by people like Danny Les (for $PMON & $POLK) 





9/
Perhaps you think that the teams at $PMON & $POLK were taken advantage of. A couple of the founders on the $POLK & $PMON team worked at Tixl which Blockfyre was acquired by. All of who Moon Rock worked closely with previously.


Perhaps you think that the teams at $PMON & $POLK were taken advantage of. A couple of the founders on the $POLK & $PMON team worked at Tixl which Blockfyre was acquired by. All of who Moon Rock worked closely with previously.



10/ Other VC’s have sprung up and do the exact same thing.
The larping VC model includes: little to no vesting period, shilling campaign, use noob friendly buzzwords, ponzi tokenomics designed to benefit VC’s at launch.
The larping VC model includes: little to no vesting period, shilling campaign, use noob friendly buzzwords, ponzi tokenomics designed to benefit VC’s at launch.
11/ Here are possible solutions that hopefully more VC’s should follow.
⁃Dont share the cap table with larping VC’s that dump instantly
⁃Make transparency status quo
⁃Regulation
This will help wash out the bad actors that give the crypto space a bad name.
⁃Dont share the cap table with larping VC’s that dump instantly
⁃Make transparency status quo
⁃Regulation
This will help wash out the bad actors that give the crypto space a bad name.
13/
A huge thanks to the team at @LedgerQL for providing me with the entire history of DEX trades for $POLK & $PMON. Can’t wait for the fully functioning site to be live.
Also a thanks to @mathieu_ouioui for helping give me a second eye by reviewing my analysis .
A huge thanks to the team at @LedgerQL for providing me with the entire history of DEX trades for $POLK & $PMON. Can’t wait for the fully functioning site to be live.
Also a thanks to @mathieu_ouioui for helping give me a second eye by reviewing my analysis .
14/ Sources:
Refer to the files below for data dumps for Polychain Monster (Polkamon) & Polkamarkets.
drive.google.com/file/d/1MfinJ9…
drive.google.com/file/d/1tB8GTr…
Refer to the files below for data dumps for Polychain Monster (Polkamon) & Polkamarkets.
drive.google.com/file/d/1MfinJ9…
drive.google.com/file/d/1tB8GTr…
• • •
Missing some Tweet in this thread? You can try to
force a refresh