How to get URL link on X (Twitter) App
https://x.com/zachxbt/status/2014685263327351116

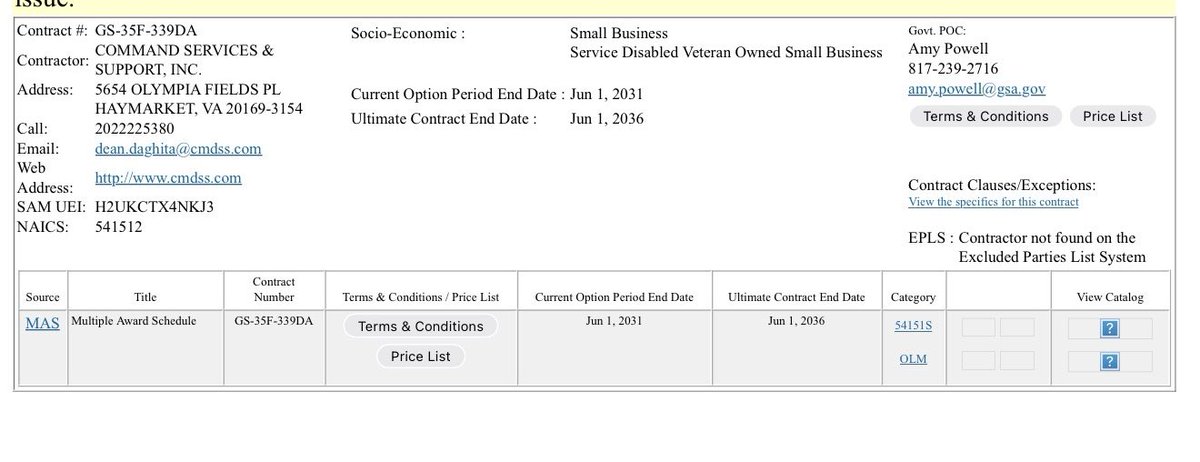
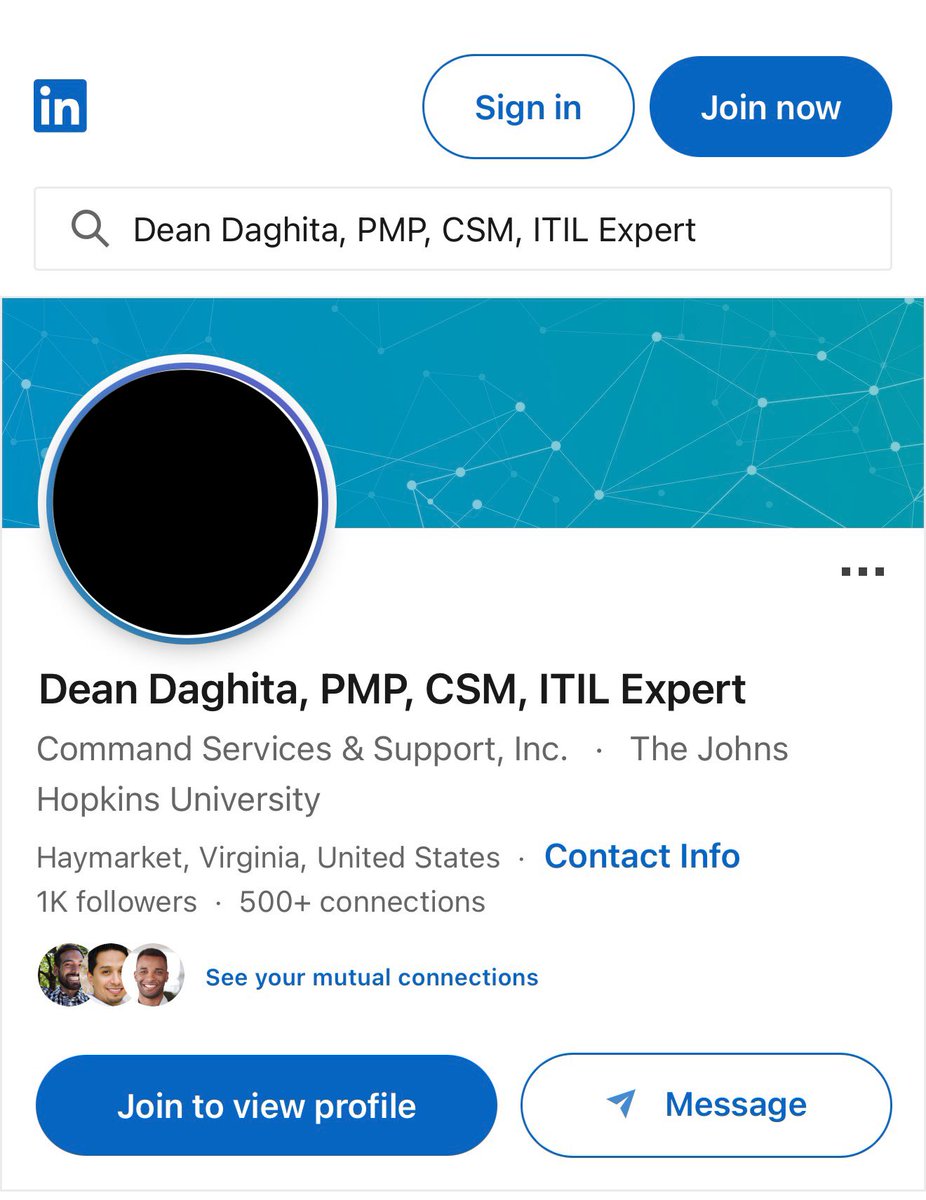
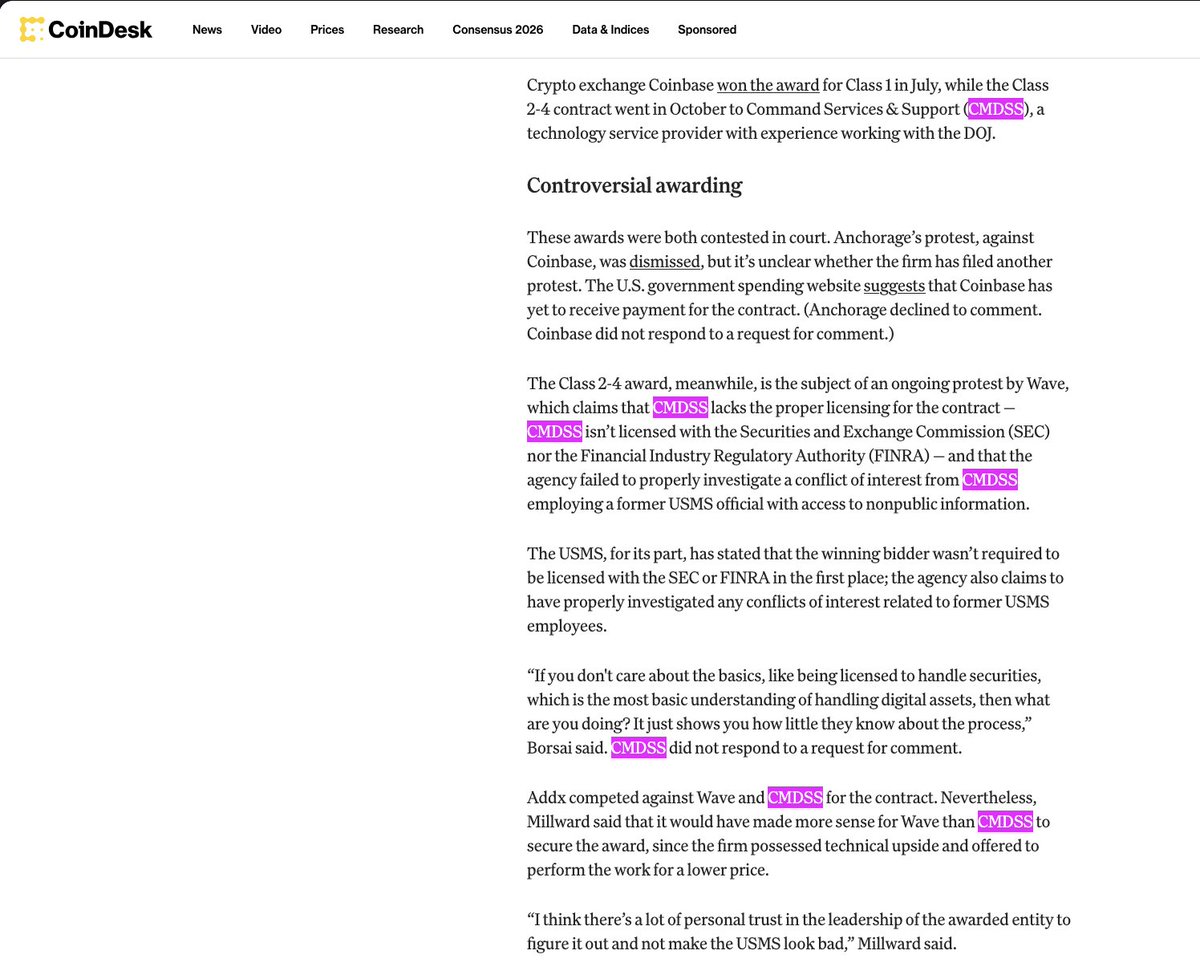 Update: The CMDSS company X account, website, & LinkedIn were all just deactivated
Update: The CMDSS company X account, website, & LinkedIn were all just deactivated 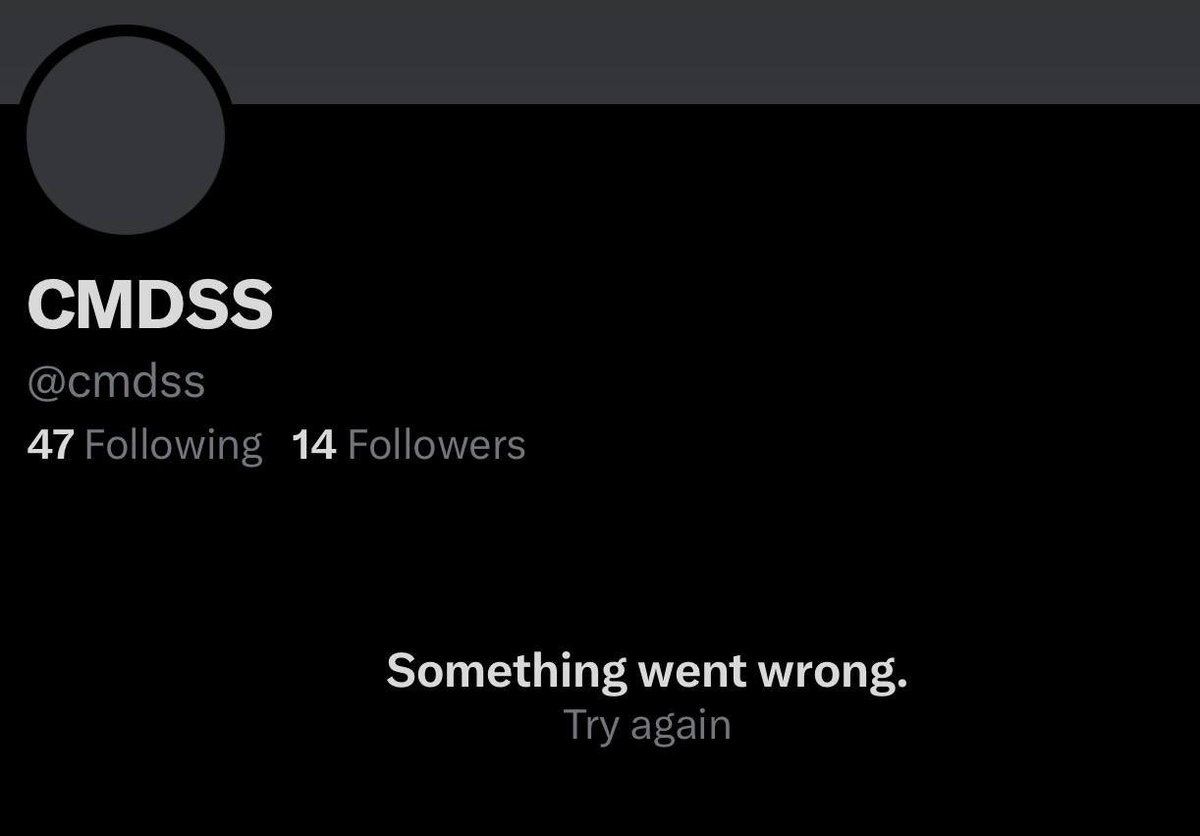
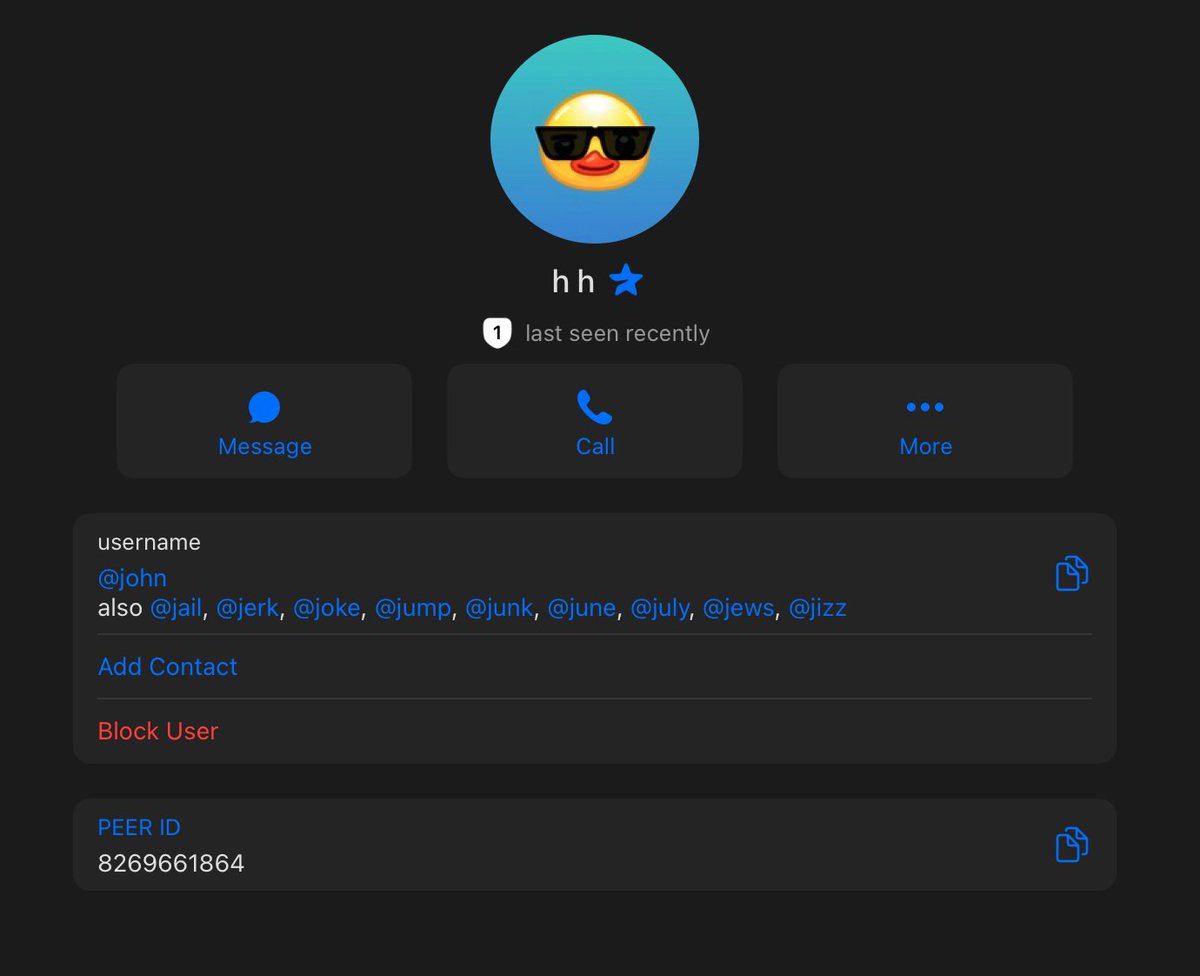

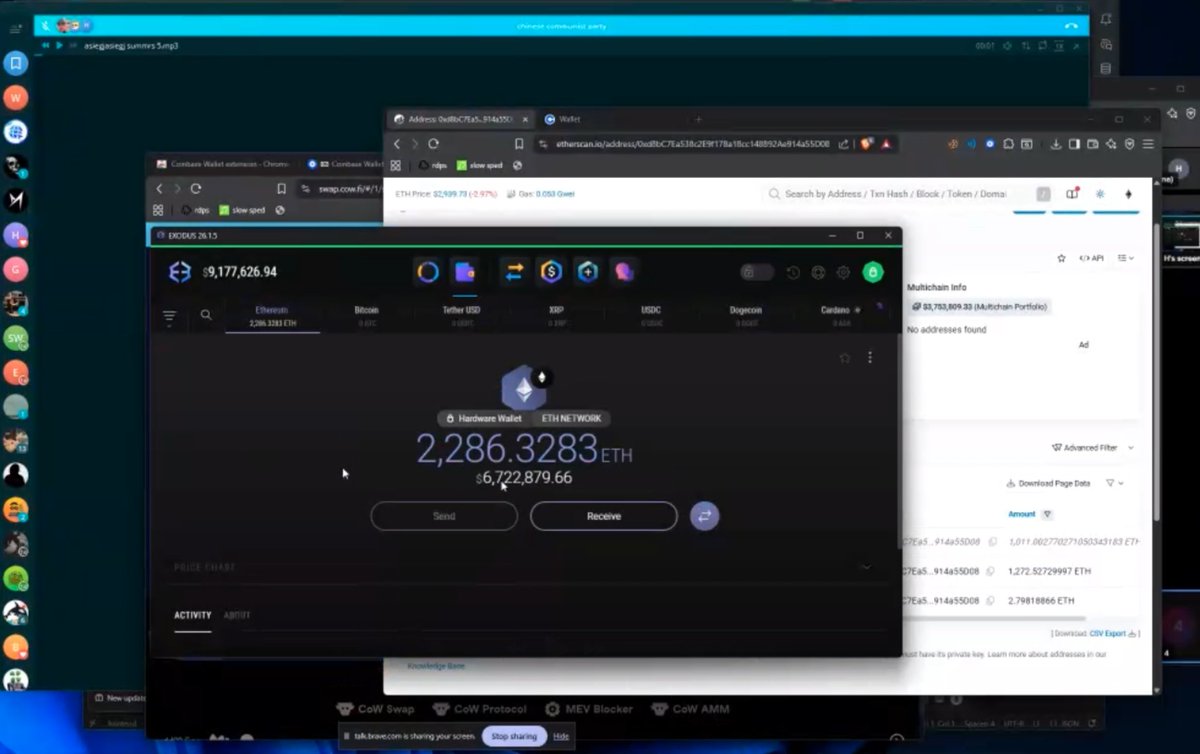
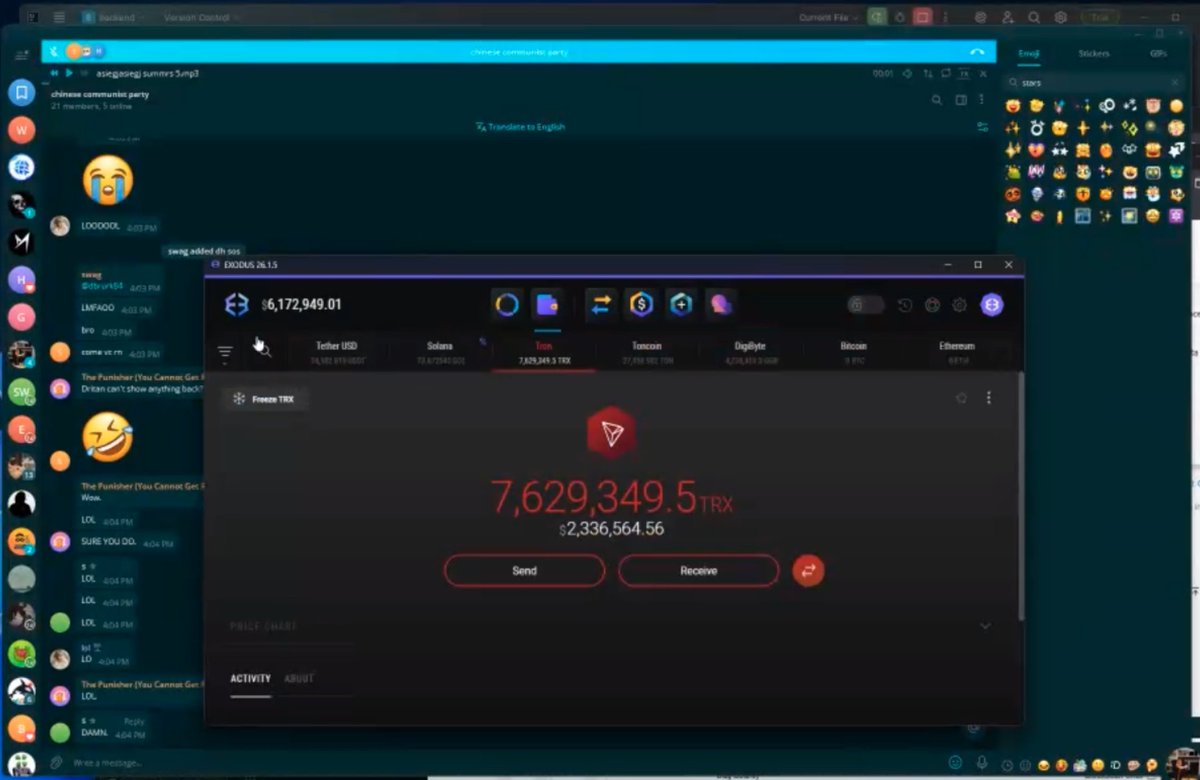 2/ Earlier today John got into a heated argument with another threat actor known as Dritan Kapplani Jr. in a group chat to see who had more funds in crypto wallets.
2/ Earlier today John got into a heated argument with another threat actor known as Dritan Kapplani Jr. in a group chat to see who had more funds in crypto wallets.https://x.com/zachxbt/status/1931216174903398723
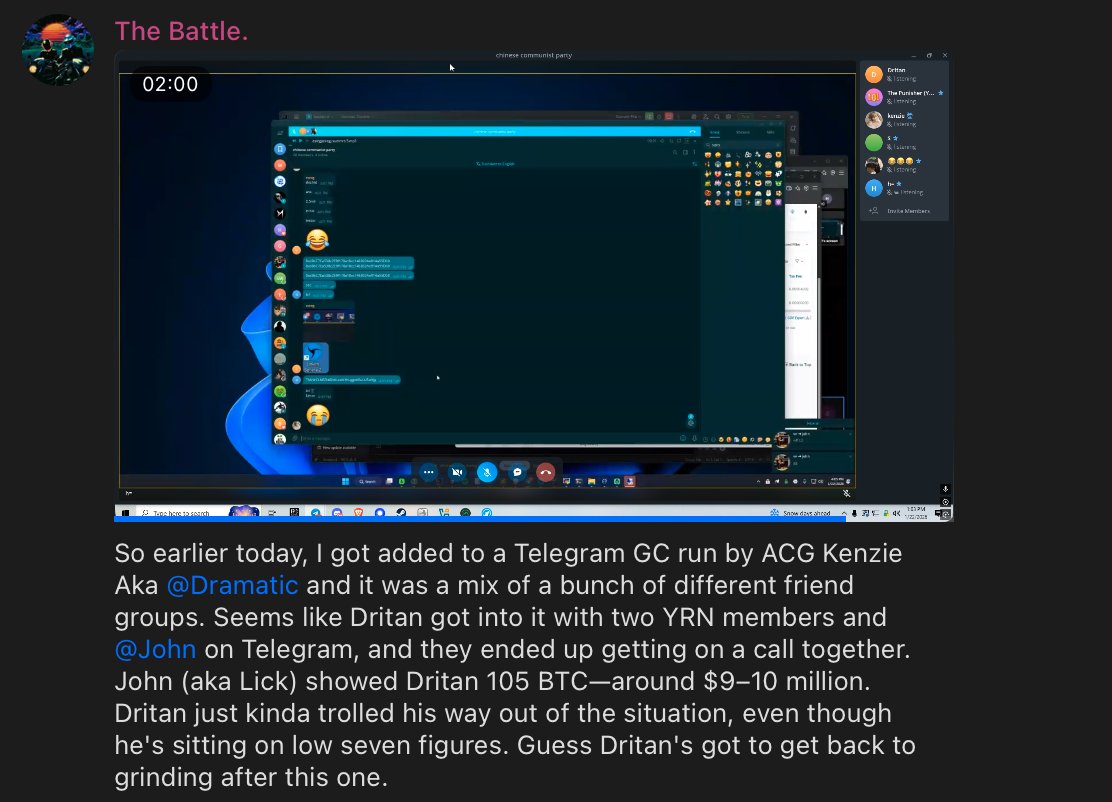

 2/ On Dec 30, 2024 Haby posted a screenshot in a group chat showing off a 21K XRP ($44K) theft from a Coinbase user.
2/ On Dec 30, 2024 Haby posted a screenshot in a group chat showing off a 21K XRP ($44K) theft from a Coinbase user.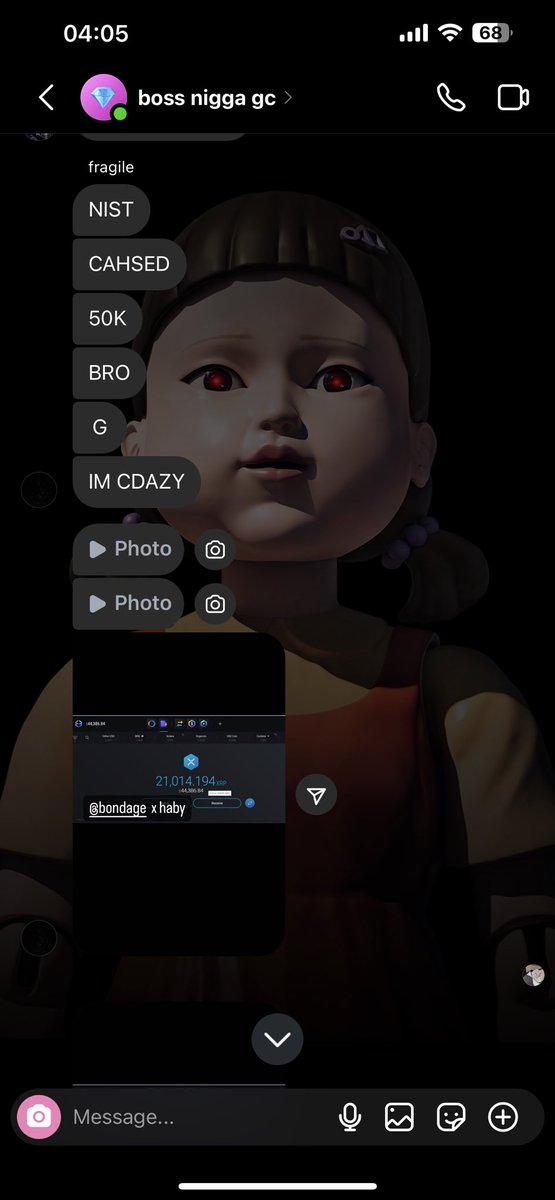
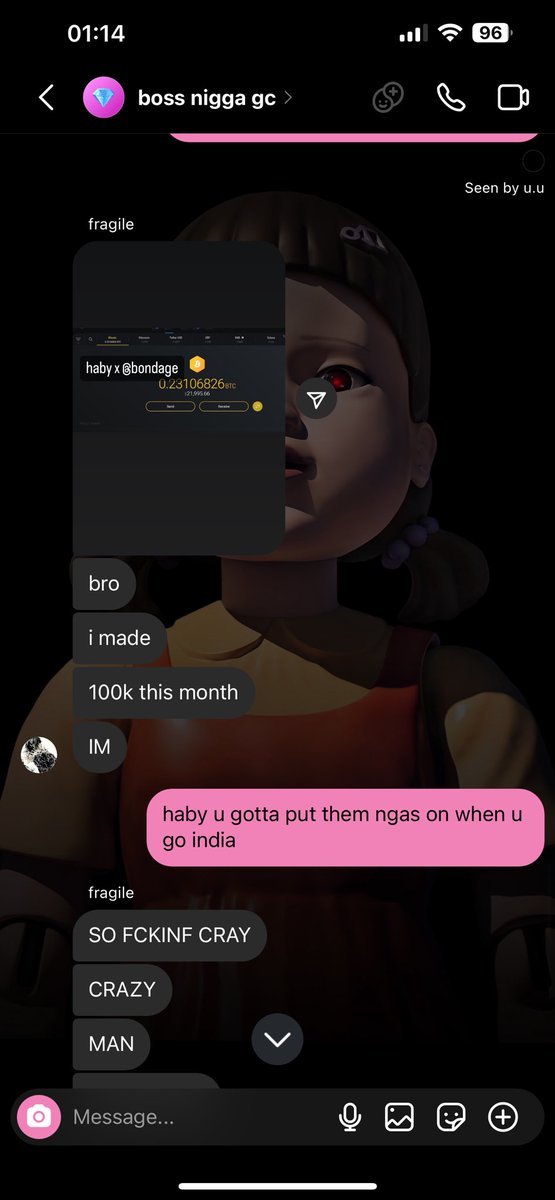
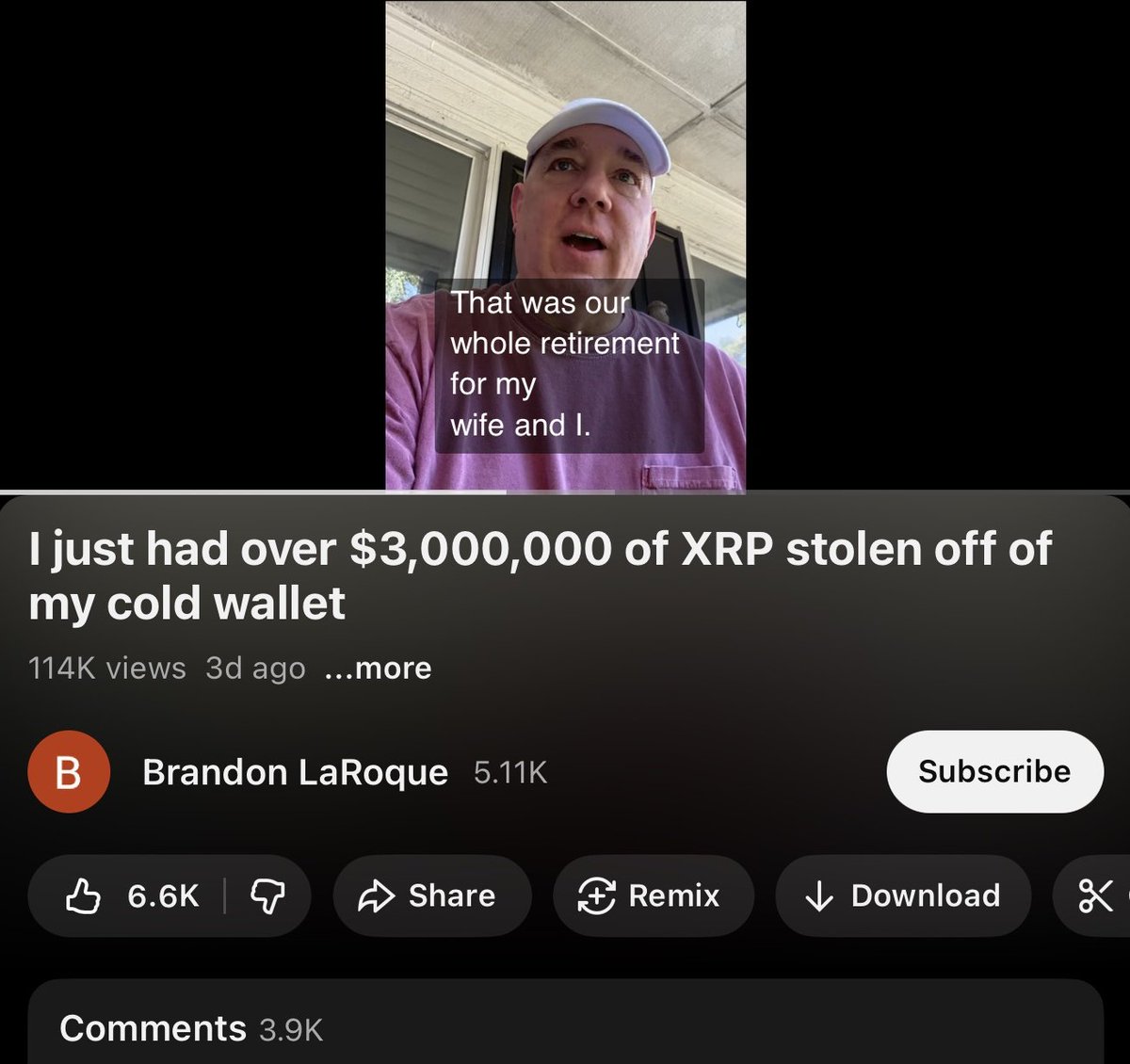
 2/ Although the victim did not directly share the theft address after watching the video I found it by reviewing the date and amount.
2/ Although the victim did not directly share the theft address after watching the video I found it by reviewing the date and amount. 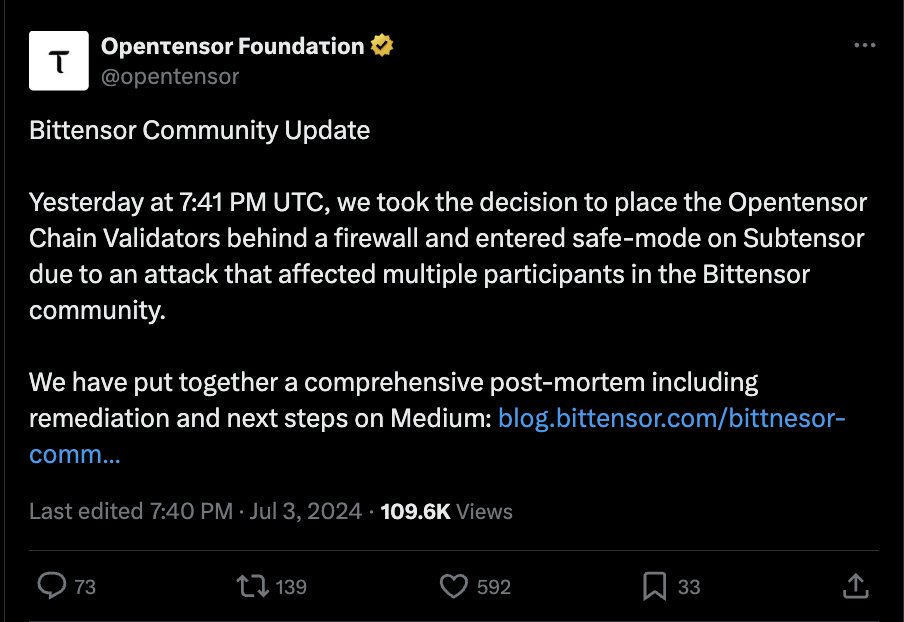

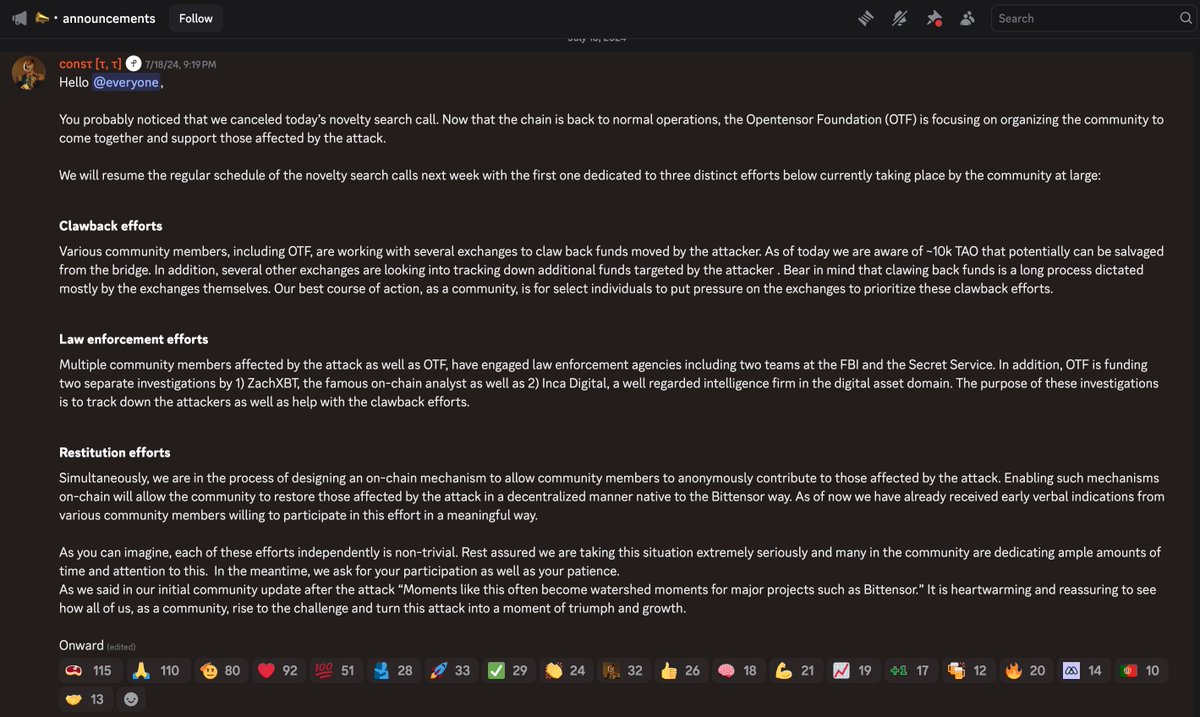 2/ 32 $TAO holders experienced unauthorized transfers in excess of $28M from May to July 2024 and the Bittensor network was temporarily halted on July 2, 2024.
2/ 32 $TAO holders experienced unauthorized transfers in excess of $28M from May to July 2024 and the Bittensor network was temporarily halted on July 2, 2024.


 2/ An export of their Google Drive, Chrome profiles, and screenshots from their devices was obtained.
2/ An export of their Google Drive, Chrome profiles, and screenshots from their devices was obtained. 

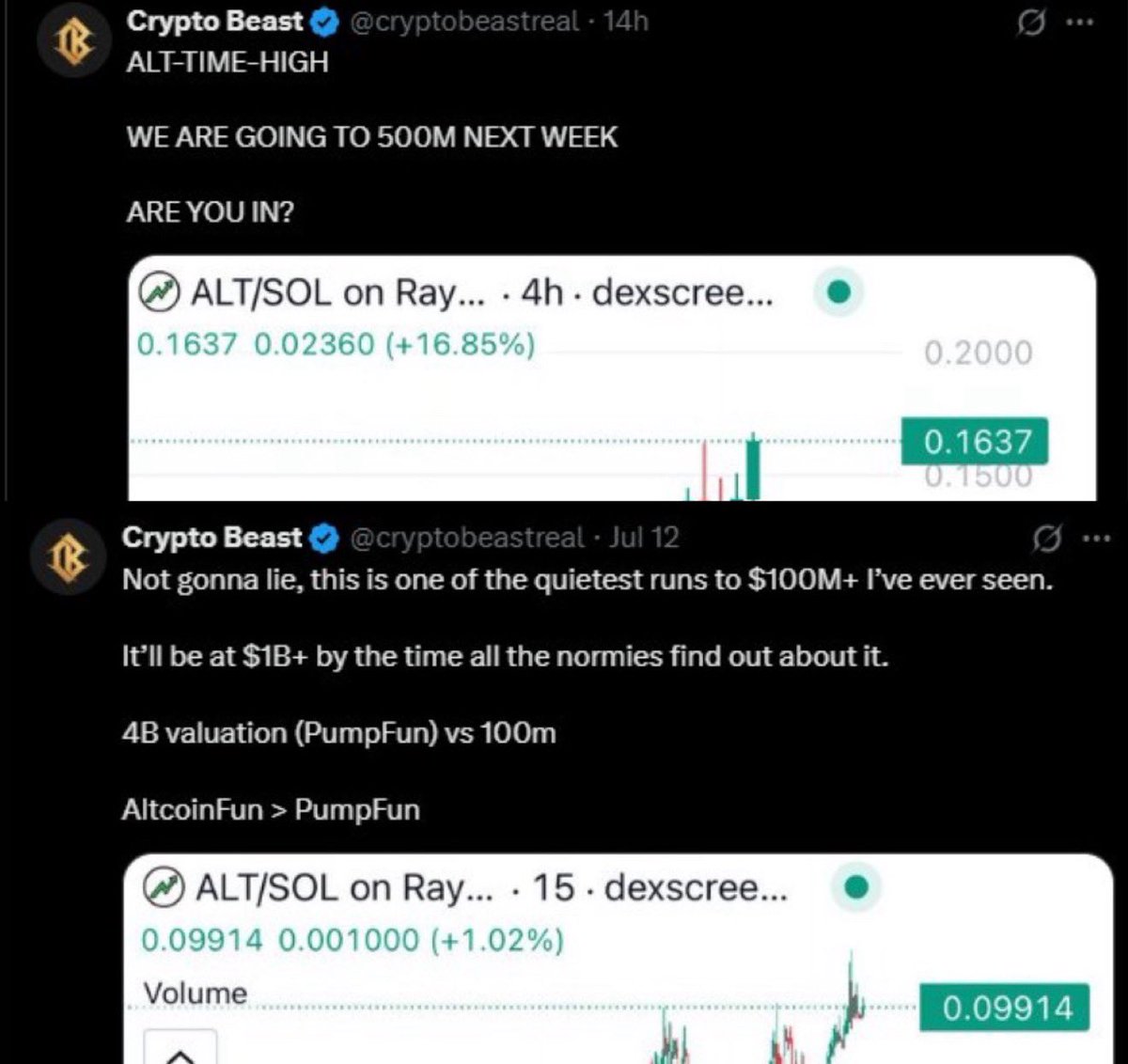
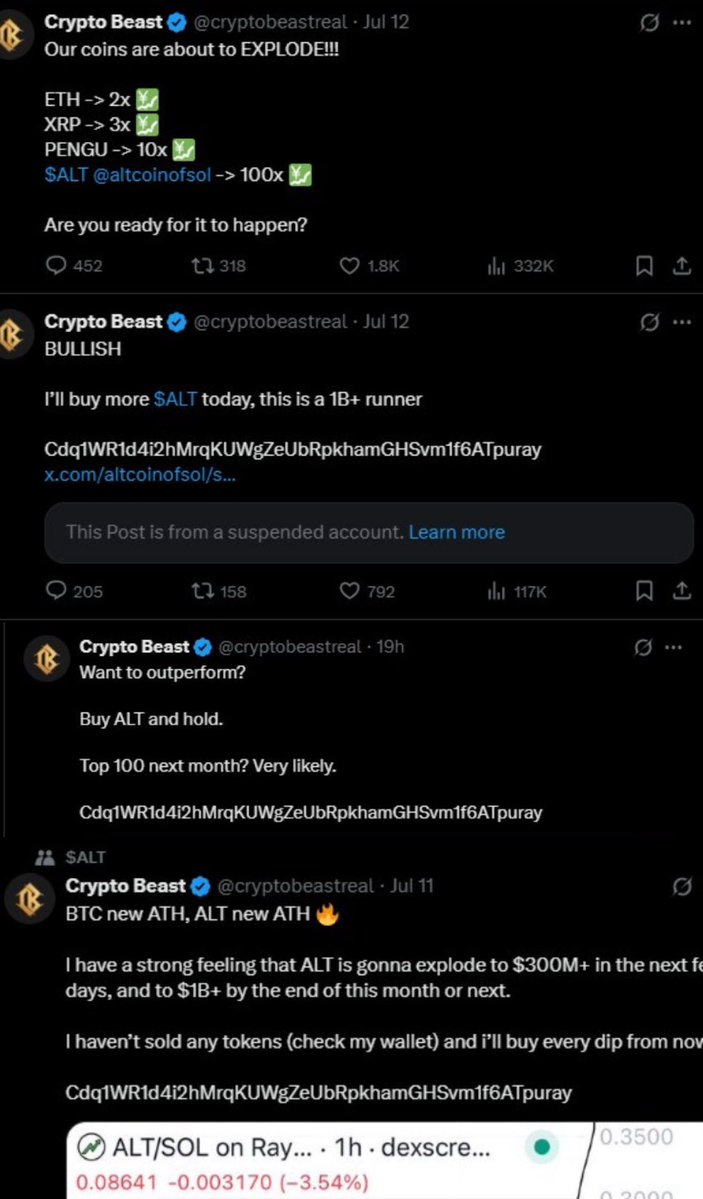
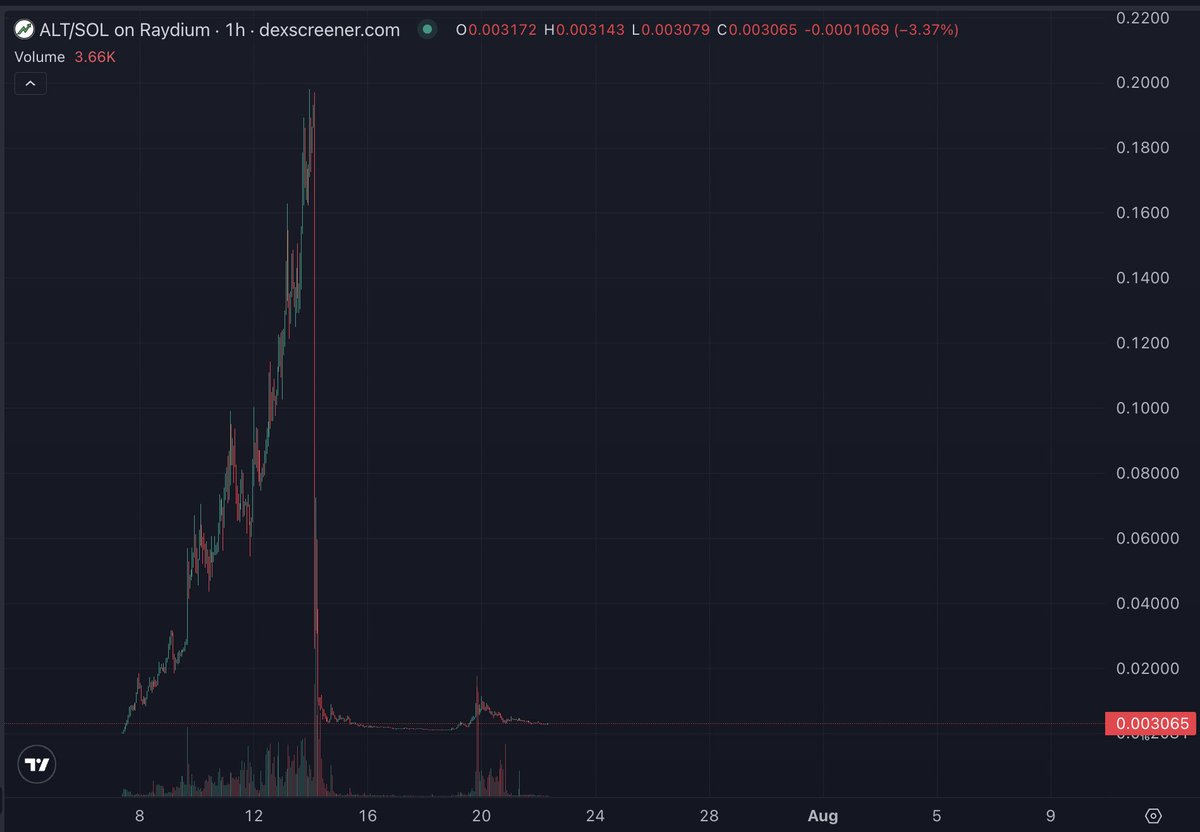
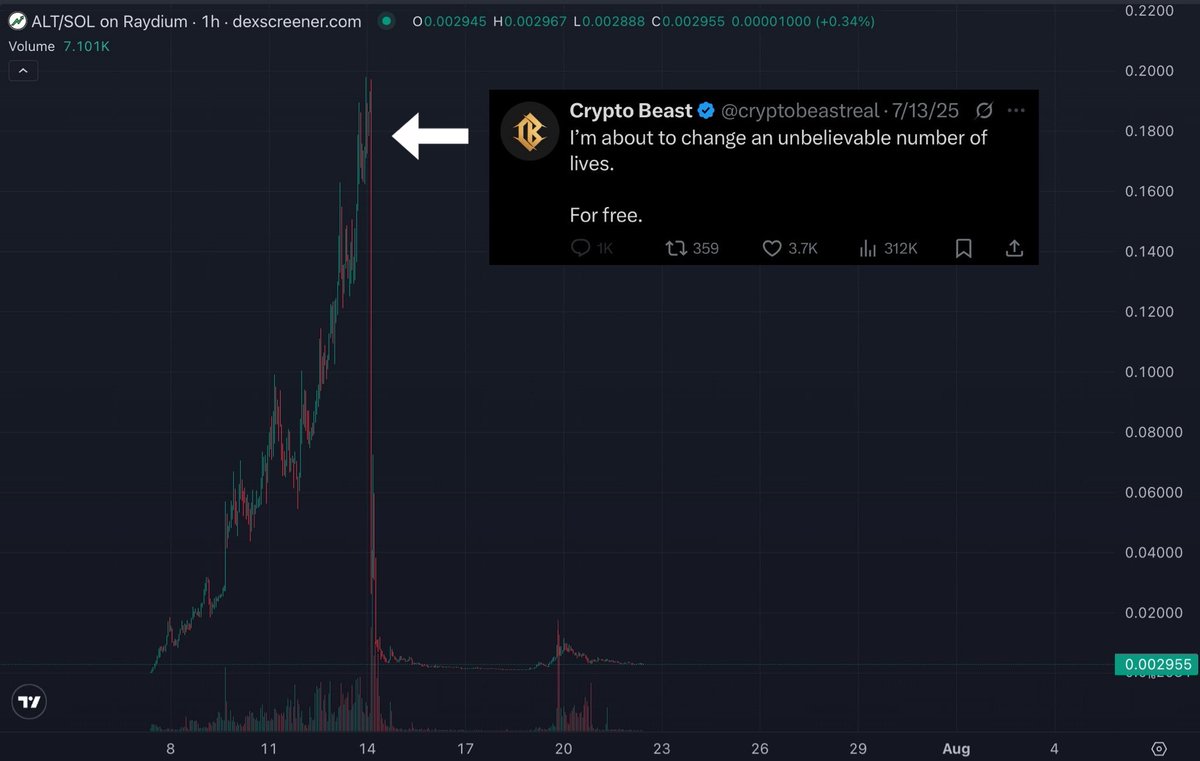 2/ Earlier this month Crypto Beast began aggressively promoting $ALT on X and TG.
2/ Earlier this month Crypto Beast began aggressively promoting $ALT on X and TG.


 2/ Here’s a look into one of the six clusters I have been monitoring and was able to attribute 8 different DPRK ITWs that obtained roles at 12+ projects.
2/ Here’s a look into one of the six clusters I have been monitoring and was able to attribute 8 different DPRK ITWs that obtained roles at 12+ projects. 


 2/ On Jun 18, 2025 at 4:25 am UTC ownership for ‘Replicandy’ from Matt Furie & ChainSaw was transferred to a new EOA 0x9Fca.
2/ On Jun 18, 2025 at 4:25 am UTC ownership for ‘Replicandy’ from Matt Furie & ChainSaw was transferred to a new EOA 0x9Fca.





 2/ Daytwo operates a small call centre group and also works as a caller.
2/ Daytwo operates a small call centre group and also works as a caller. https://twitter.com/bestvideosofct/status/1937120536846532672



 2/ In Dec 2022, a victim had 14 X BAYC NFTs phished in a social engineering scheme where purchased X accounts were used to convince the victim they wanted to license the IP rights for a film.
2/ In Dec 2022, a victim had 14 X BAYC NFTs phished in a social engineering scheme where purchased X accounts were used to convince the victim they wanted to license the IP rights for a film. 





 2/ A trader opened multiple highly leveraged positions on Hyperliquid and GMX from Jan - Mar 2025.
2/ A trader opened multiple highly leveraged positions on Hyperliquid and GMX from Jan - Mar 2025. 




 2/ Myself and @tanuki42_ spent time reviewing Coinbase withdrawals and gathering data from my DMs for high confidence thefts on various chains.
2/ Myself and @tanuki42_ spent time reviewing Coinbase withdrawals and gathering data from my DMs for high confidence thefts on various chains. 

https://twitter.com/zachxbt/status/1861450263925559399


 2/ Serpent (SerpentAU) is a former pro Fortnite player from Australia who was released from the esports organization ‘Overtime’ after being caught allegedly cheating in June 2020.
2/ Serpent (SerpentAU) is a former pro Fortnite player from Australia who was released from the esports organization ‘Overtime’ after being caught allegedly cheating in June 2020.


 2/ On Aug 21, 2024 the McDonald’s IG became compromised and a post was made promoting the bundled meme coin GRIMACE and the hacker began trolling after.
2/ On Aug 21, 2024 the McDonald’s IG became compromised and a post was made promoting the bundled meme coin GRIMACE and the hacker began trolling after. 





 2/ A US based victim sent me a DM on Oct 7, 2024 after receiving a call from a spoofed number impersonating Coinbase support where they were coerced in to using a phishing site.
2/ A US based victim sent me a DM on Oct 7, 2024 after receiving a call from a spoofed number impersonating Coinbase support where they were coerced in to using a phishing site. 


 2/ While paying others to be the face of OPSEC behind the scenes he was involved with key decisions as the owner in private Telegram chats.
2/ While paying others to be the face of OPSEC behind the scenes he was involved with key decisions as the owner in private Telegram chats. 






 2/ A follower reached out to me a few months ago after having their exchange account frozen after completing a P2P transaction with Yicong Wang an OTC who has used pseudonyms like Seawang, Greatdtrader, & BestRhea977
2/ A follower reached out to me a few months ago after having their exchange account frozen after completing a P2P transaction with Yicong Wang an OTC who has used pseudonyms like Seawang, Greatdtrader, & BestRhea977 

 2/ A project reached out to Jaypeg who agreed to promote a meme coin for 2% of the supply.
2/ A project reached out to Jaypeg who agreed to promote a meme coin for 2% of the supply.




 2/ On June 18th a victim posted to X post he had been victim of a robbery earlier that day forcing him to send $4.3M to two addresses.
2/ On June 18th a victim posted to X post he had been victim of a robbery earlier that day forcing him to send $4.3M to two addresses. 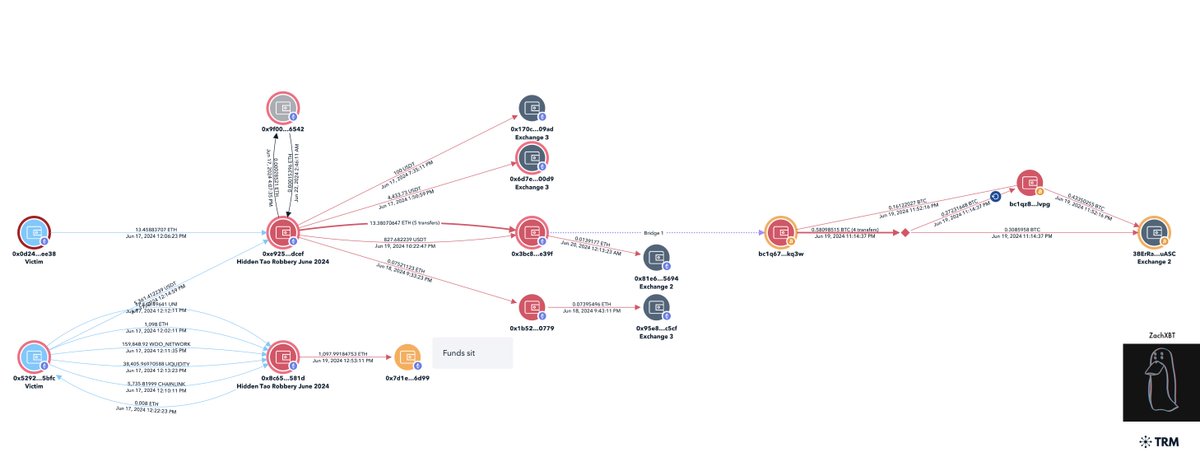


 2/ Incident Summary: On August 19, 2024 the threat actors targeted a single Genesis creditor by:
2/ Incident Summary: On August 19, 2024 the threat actors targeted a single Genesis creditor by:


