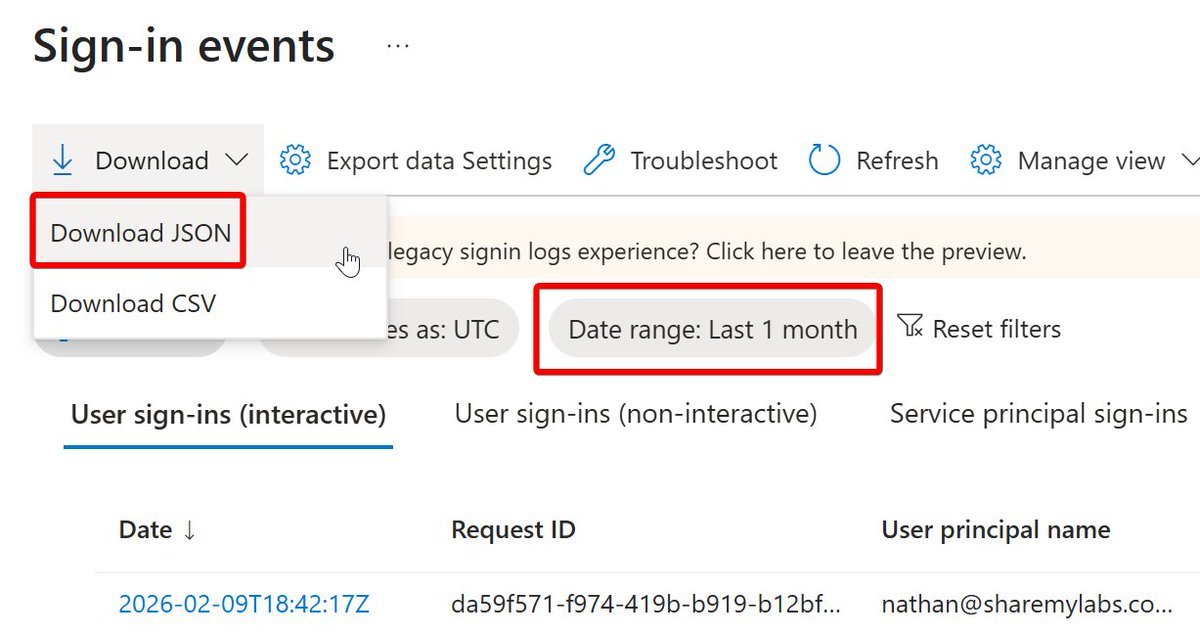
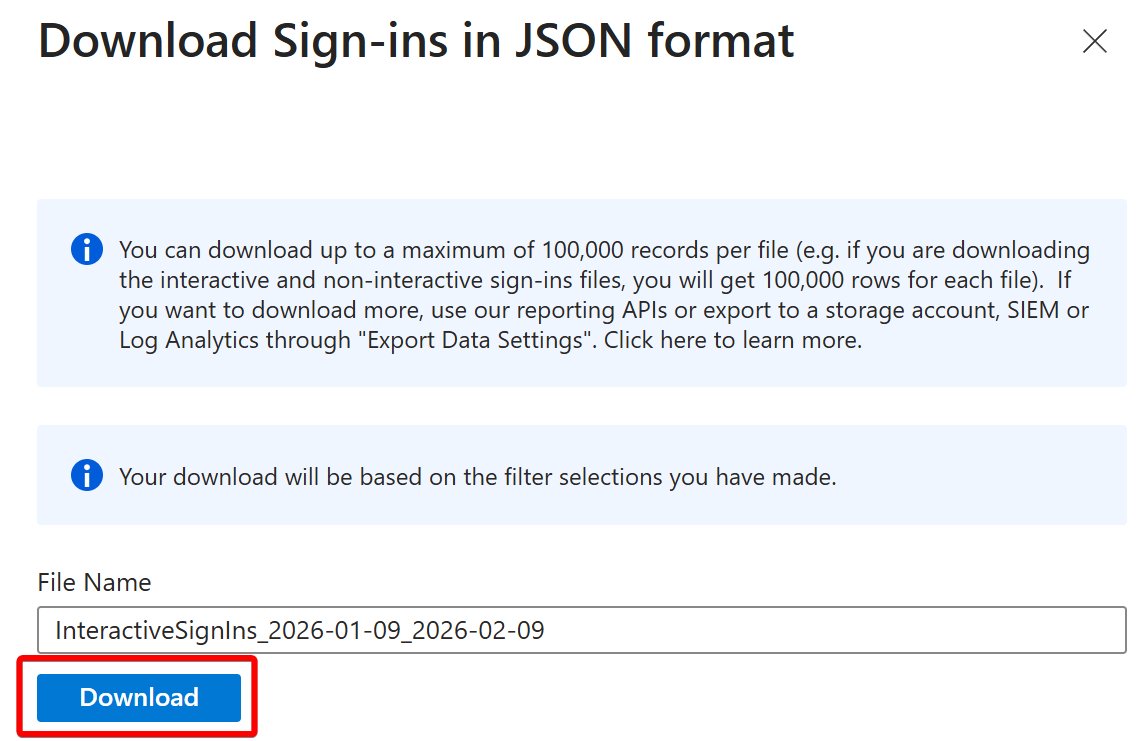
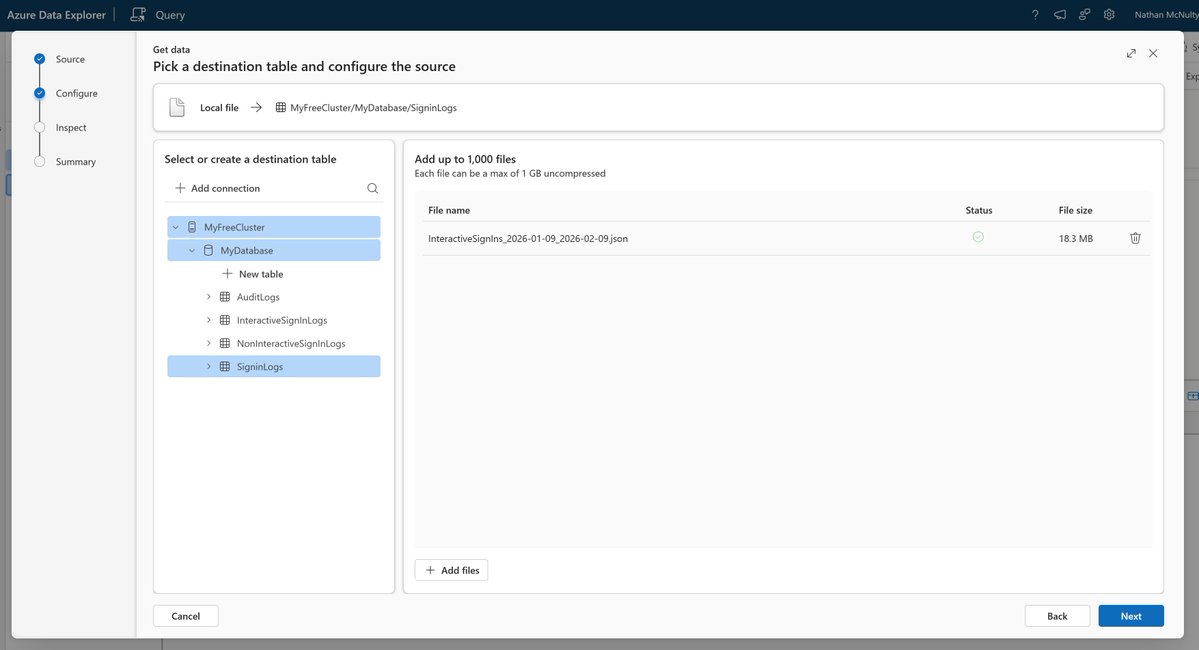
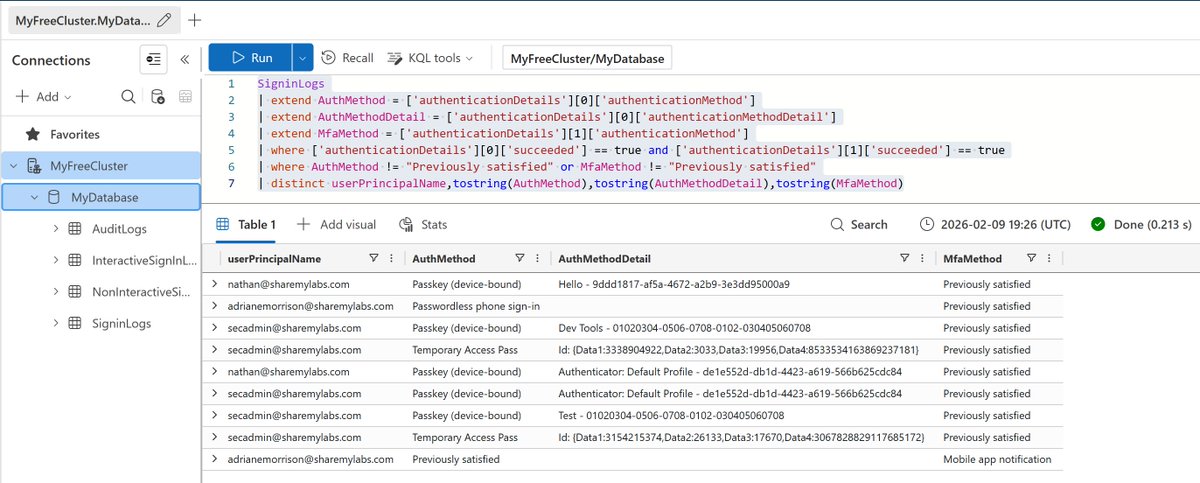
It's finally time to learn about Groups in Azure AD :)
Groups are foundational components for granting access to resources, email delivery, and even assigning licenses within Azure AD.
But first, you need users, so if you haven't yet, go create some :)
Groups are foundational components for granting access to resources, email delivery, and even assigning licenses within Azure AD.
But first, you need users, so if you haven't yet, go create some :)
https://twitter.com/NathanMcNulty/status/1397041008374734849
In Azure AD, we have a few different types of groups
The main group types are security and Microsoft 365 groups, but in Exchange we also have distribution lists which are mail enabled groups with no security context
Each group also has an assigned and dynamic membership type
The main group types are security and Microsoft 365 groups, but in Exchange we also have distribution lists which are mail enabled groups with no security context
Each group also has an assigned and dynamic membership type
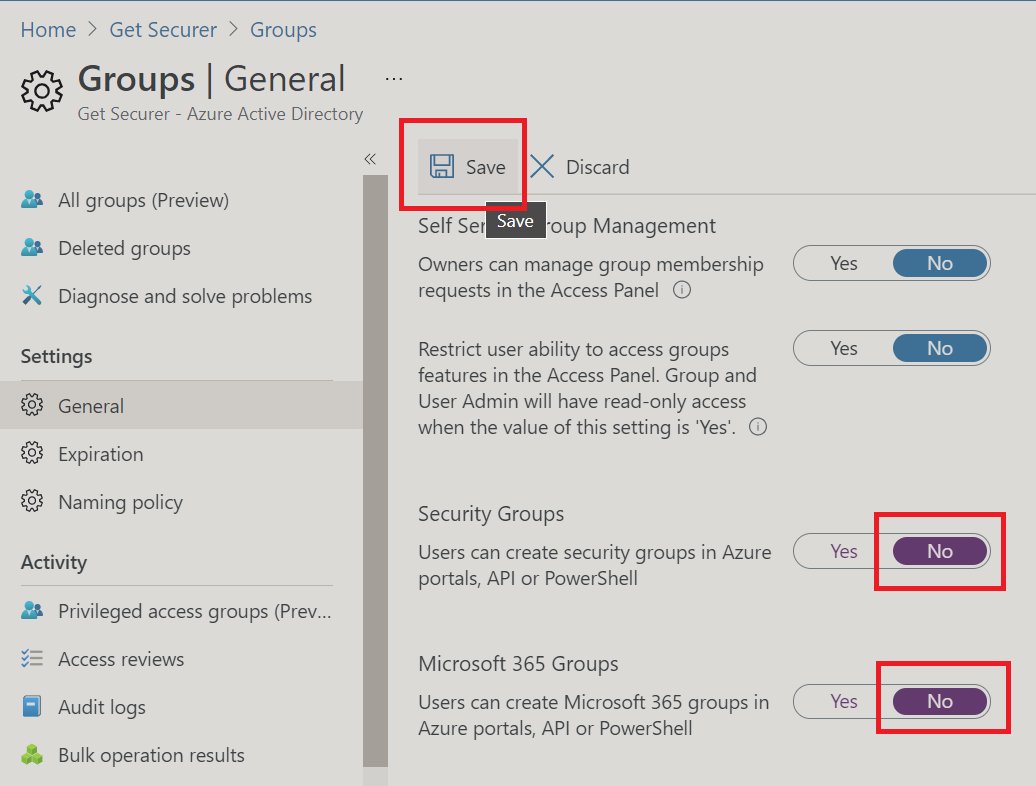
Now, before we start creating groups, I need to warn you that Microsoft stupidly believes any user should be able to create groups, both security and M365 types
What you should know is that they can select any email address they want 😱
Let's start here: portal.azure.com/#blade/Microso…
What you should know is that they can select any email address they want 😱
Let's start here: portal.azure.com/#blade/Microso…
You have 2 options:
1) Prevent users from creating groups - IT wants to be the bottleneck ;)
2) Create a naming policy, and optionally pester group owners to "renew" groups. If they don't, groups are automatically cleaned up.
docs.microsoft.com/en-us/microsof…
docs.microsoft.com/en-us/microsof…


1) Prevent users from creating groups - IT wants to be the bottleneck ;)
2) Create a naming policy, and optionally pester group owners to "renew" groups. If they don't, groups are automatically cleaned up.
docs.microsoft.com/en-us/microsof…
docs.microsoft.com/en-us/microsof…


With that out of the way, let's create some groups!
portal.azure.com/#blade/Microso…
Click "New group" and start with the simplest form - security groups using assigned membership
This is the traditional method you'd see in on-prem AD and will be most common/familiar to AD based ogs
portal.azure.com/#blade/Microso…
Click "New group" and start with the simplest form - security groups using assigned membership
This is the traditional method you'd see in on-prem AD and will be most common/familiar to AD based ogs

Groups with "assigned" membership can now be granted a role in Azure AD, so I'm going to do that too
This also lets us use PIM to add users to the group allowing us to have different settings/approval workflows for different groups.
Very cool stuff:
docs.microsoft.com/en-us/azure/ac…


This also lets us use PIM to add users to the group allowing us to have different settings/approval workflows for different groups.
Very cool stuff:
docs.microsoft.com/en-us/azure/ac…



Next, security groups with dynamic membership
You'll quickly see how important it is to populate user attributes as that is the key to building these groups
While Azure AD doesn't come close to the flexibility of an IAM, this could be totally sufficient for many orgs

You'll quickly see how important it is to populate user attributes as that is the key to building these groups
While Azure AD doesn't come close to the flexibility of an IAM, this could be totally sufficient for many orgs


Microsoft 365 Groups are a weird beast
They create a ton of backend resources and are heavily used by Yammer and Teams
Overview
docs.microsoft.com/en-us/microsof…
These have an email address, so ensure your naming convention prevents abuse
You can recover them if an owner fails to renew

They create a ton of backend resources and are heavily used by Yammer and Teams
Overview
docs.microsoft.com/en-us/microsof…
These have an email address, so ensure your naming convention prevents abuse
You can recover them if an owner fails to renew


If you want, create an M365 group with dynamic membership for practice :)
Before we move to Powershell modules, let's look at Audit logs and group based licensing
Audit logs:
portal.azure.com/#blade/Microso…
Group based licensing takes planning but worth it:
docs.microsoft.com/en-us/azure/ac…

Before we move to Powershell modules, let's look at Audit logs and group based licensing
Audit logs:
portal.azure.com/#blade/Microso…
Group based licensing takes planning but worth it:
docs.microsoft.com/en-us/azure/ac…


Ran out of time tonight, but on the plus side, got to snuggle a baby for an hour.
I'll finish this up tomorrow, but I did just push some of the Powershell code for creating groups.
Will push Get, Modify, and Delete tomorrow once I comment it all :)
github.com/nathanmcnulty/…
I'll finish this up tomorrow, but I did just push some of the Powershell code for creating groups.
Will push Get, Modify, and Delete tomorrow once I comment it all :)
github.com/nathanmcnulty/…
Time for some Powershell :)
If you haven't installed the modules, check out this repo and section of my previous thread:
Also a reminder, I love questions and try to respond to everyone I can. Please ask away :D
If you haven't installed the modules, check out this repo and section of my previous thread:
https://twitter.com/NathanMcNulty/status/1397053828097220609
Also a reminder, I love questions and try to respond to everyone I can. Please ask away :D
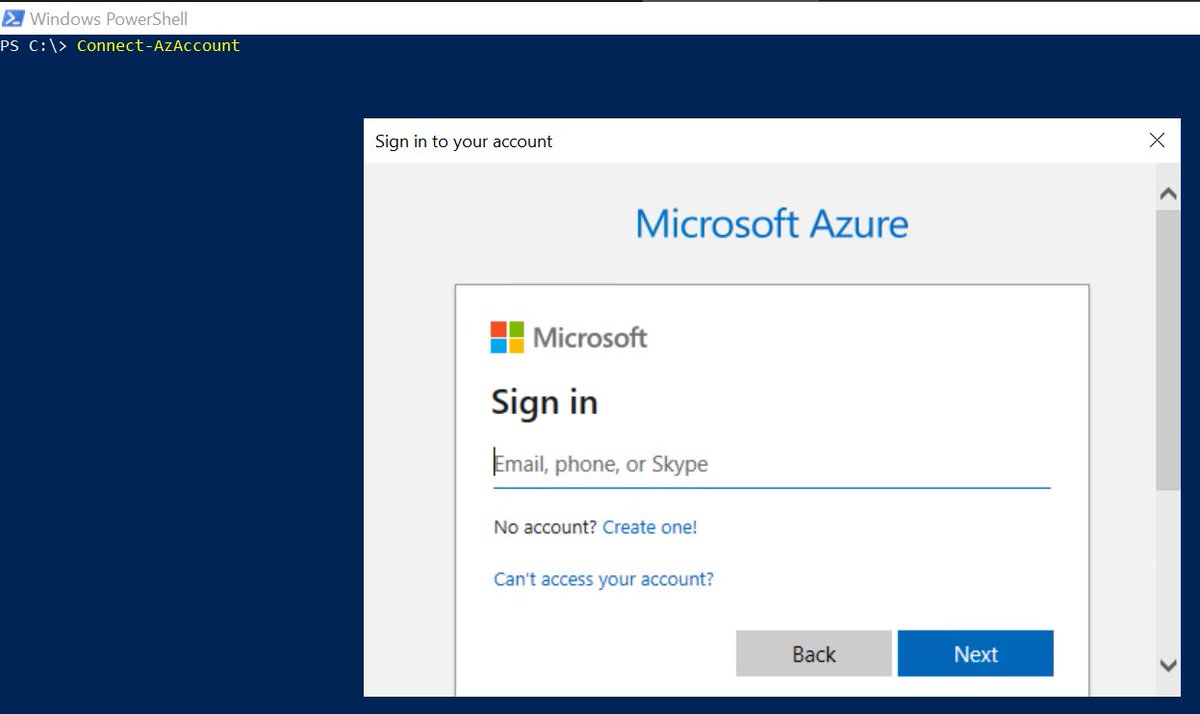
Let's create a group with the Az module
Authenticate:
Connect-AzAccount
Then create:
New-AzADGroup -DisplayName "Test Group 1" -MailNickname "TestGroup1"
There aren't many properties available when creating a group with these modules. Let's look at the others :)

Authenticate:
Connect-AzAccount
Then create:
New-AzADGroup -DisplayName "Test Group 1" -MailNickname "TestGroup1"
There aren't many properties available when creating a group with these modules. Let's look at the others :)

Next, let's create a group with the AzureADPreview module
Authenticate:
Connect-AzureAD
Create:
New-AzureADGroup -DisplayName "Test Group 2" -MailEnabled $false -MailNickname "TestGroup2" -SecurityEnabled $true
-MailEnabled $true doesn't work yet, still not many options here

Authenticate:
Connect-AzureAD
Create:
New-AzureADGroup -DisplayName "Test Group 2" -MailEnabled $false -MailNickname "TestGroup2" -SecurityEnabled $true
-MailEnabled $true doesn't work yet, still not many options here


Finally, let's do the MSOnline module
Authenticate:
Connect-MsolService
Create:
New-MsolGroup -DisplayName "Test Group 3" -Description "Test Group 3"
So none had very many property options :-/
Let's see if we can change membership and properties with a Set/Update

Authenticate:
Connect-MsolService
Create:
New-MsolGroup -DisplayName "Test Group 3" -Description "Test Group 3"
So none had very many property options :-/
Let's see if we can change membership and properties with a Set/Update


The Az module does not appear to have a Set/Update cmdlet.. :(
At least it does have an add group member option:
Add-AzADGroupMember -MemberUserPrincipalName "tuser1@getsecurer.onmicrosoft.com" -TargetGroupDisplayName "Test Group 1" -Verbose
No output on this without -Verbsose

At least it does have an add group member option:
Add-AzADGroupMember -MemberUserPrincipalName "tuser1@getsecurer.onmicrosoft.com" -TargetGroupDisplayName "Test Group 1" -Verbose
No output on this without -Verbsose


Hurray! The Azure AD module has cmdlets to deal with group membership, ownership, and attributes for both assigned and even dynamic groups!
Commands are too long for Twitter, so be sure to check the repo here:
github.com/nathanmcnulty/…



Commands are too long for Twitter, so be sure to check the repo here:
github.com/nathanmcnulty/…




The MSOnline modules are disappointing (as usual)
Note that some of these cmdlets require ObjectId, so we have to do (Get-Group).ObjectId to get it.
Set-MsolGroup -ObjectId (Get-MsolGroup -SearchString "Test Group 3").ObjectId -DisplayName "Test Group 3 - Modified" -Verbose
Note that some of these cmdlets require ObjectId, so we have to do (Get-Group).ObjectId to get it.
Set-MsolGroup -ObjectId (Get-MsolGroup -SearchString "Test Group 3").ObjectId -DisplayName "Test Group 3 - Modified" -Verbose

OK, so let's use the "Get-" cmdlets to see if our changes went through :)
One of the neat discoveries I had going through this was the -AzureADMSGroup cmdlets can work with dynamic group properties
It's been around a while, but the documentation isn't really even there :P



One of the neat discoveries I had going through this was the -AzureADMSGroup cmdlets can work with dynamic group properties
It's been around a while, but the documentation isn't really even there :P




And finally, we'll delete all the test groups with the "Delete-" cmdlets
Rather than type them all out here, you can check them out in the repo:
github.com/nathanmcnulty/…
Hopefully this gives you some ideas on how to build automation around groups in Azure AD :D


Rather than type them all out here, you can check them out in the repo:
github.com/nathanmcnulty/…
Hopefully this gives you some ideas on how to build automation around groups in Azure AD :D



No Exchange yet, so no lists for now
Already have content for adding a custom domain to AAD, setting up the mail records, and for installing Azure AD Connect in Express mode
Plan to do properly delegated AAD Connect with ADFS, then migrate to PHS
Other suggestions welcome! :)
Already have content for adding a custom domain to AAD, setting up the mail records, and for installing Azure AD Connect in Express mode
Plan to do properly delegated AAD Connect with ADFS, then migrate to PHS
Other suggestions welcome! :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh