Fatal flaws in a bot, a sort of on-chain virus, a trojan horse token, and arbitrage gone wrong
Join me in looking at the latest MEV bot exploit in this thread 👇🏻
Join me in looking at the latest MEV bot exploit in this thread 👇🏻
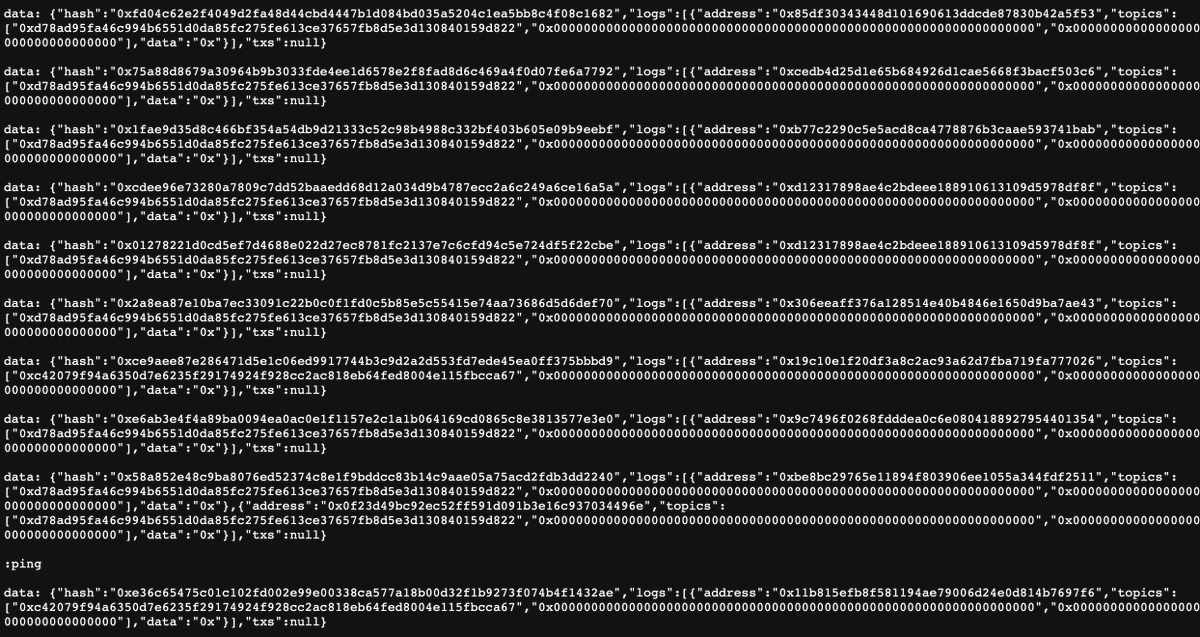
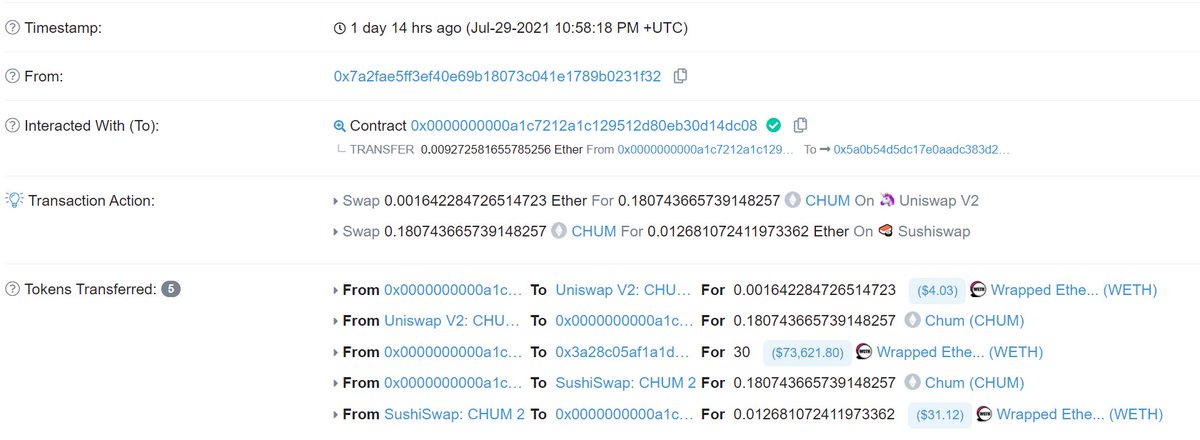
The victim today tried to arbitrage the CHUM token (!) for ~0.01 ETH in profit, but in the process had 30 WETH transferred out of their wallet.
They only interacted with Uniswap v2 pools, how did this happen!?
They only interacted with Uniswap v2 pools, how did this happen!?
Searchers optimize their contracts to the extreme to do very specific things very efficiently.
However, occasionally they have a need to do random things & add in functions that can be used for to execute basically any arbitrary transaction in a contract
However, occasionally they have a need to do random things & add in functions that can be used for to execute basically any arbitrary transaction in a contract
https://twitter.com/mevintern/status/1416858843649171456
The Flashbots simple arb example has one of these! It can execute arbitrary transactions on behalf of the owner, and only the owner.
This is validated by checking who is calling this function with msg.sender, which is important to this story.
github.com/flashbots/simp…

This is validated by checking who is calling this function with msg.sender, which is important to this story.
github.com/flashbots/simp…
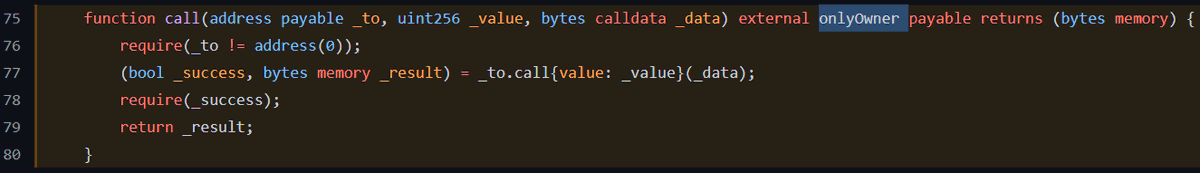
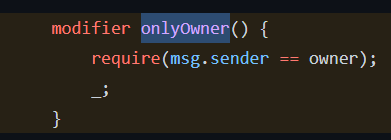
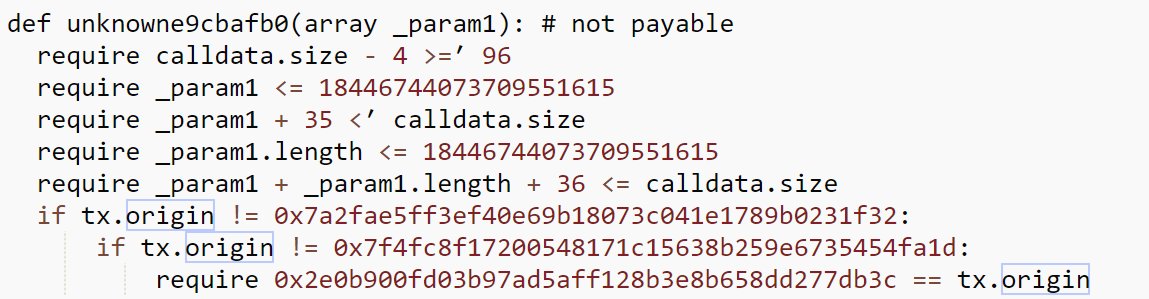
Decompiling their contract, the victim uses tx.origin to ensure that transactions calling some functions originated with their account.
Including a function that made arbitrary calls.
As with the THORChain saga this is very dangerous.

Including a function that made arbitrary calls.
As with the THORChain saga this is very dangerous.
https://twitter.com/bantg/status/1418586485725532165
Still, for almost any interaction on-chain it was fine.
To make an arbitrary call with this victim's contract you would need them to originate the transaction somehow and inject your desired transaction in their's, like a virus!
How might you bait them into doing so?
To make an arbitrary call with this victim's contract you would need them to originate the transaction somehow and inject your desired transaction in their's, like a virus!
How might you bait them into doing so?
Well, the victim was an arbitrage bot! The answer was to bait them by deploying a new token and creating a fake arb to get them to interact with that token.
Thus the CHUM token and two Uniswap v2 pools were borne.
Thus the CHUM token and two Uniswap v2 pools were borne.
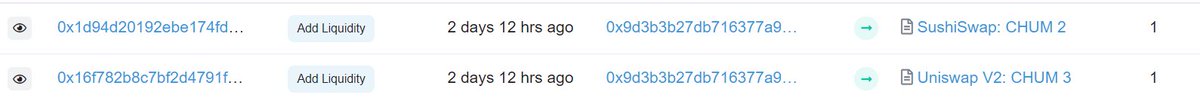
But how does CHUM work? Let's go through it end to end.
First, the victim tried to swap on the Uniswap v2 pool
Then, the Uniswap v2 pool transferred CHUM back to the victim, in doing so triggering some special logic
First, the victim tried to swap on the Uniswap v2 pool
Then, the Uniswap v2 pool transferred CHUM back to the victim, in doing so triggering some special logic
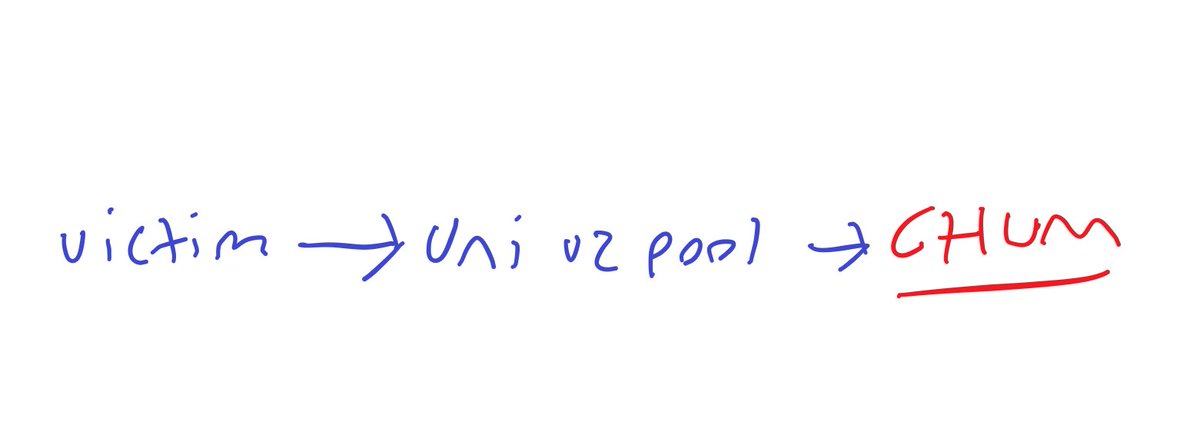
What happens now?
This was hard to piece together but I think I got it with 3 clues.
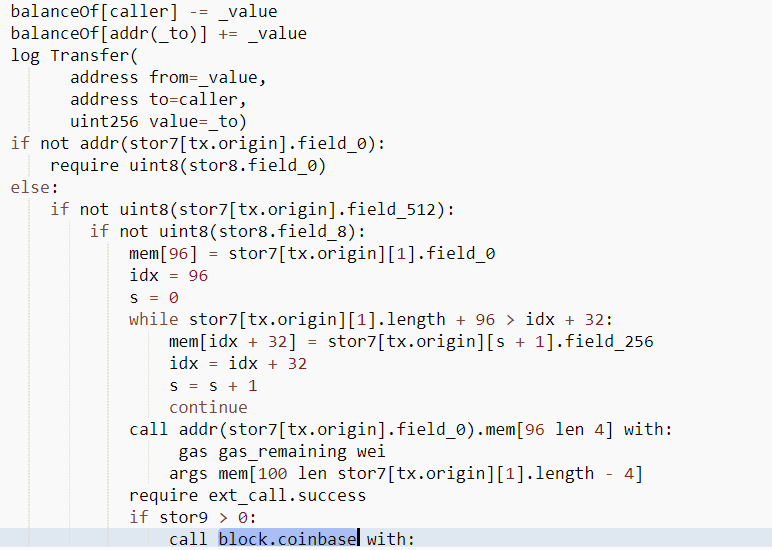
1st, you can see in CHUM decompiled that it checks for certain addresses as well as using block.coinbase and making calls.
This is CHUM targeting the victim & maybe avoiding simulation.
This was hard to piece together but I think I got it with 3 clues.
1st, you can see in CHUM decompiled that it checks for certain addresses as well as using block.coinbase and making calls.
This is CHUM targeting the victim & maybe avoiding simulation.
Second, looking @ CHUM's transactions we can see transactions with input data that contains the address for WETH, as well as the attacker's address (3a28...), and what looks to be numbers.
Looks to me like a custom payload that transfers WETH to the attacker, a sort of virus.
Looks to me like a custom payload that transfers WETH to the attacker, a sort of virus.
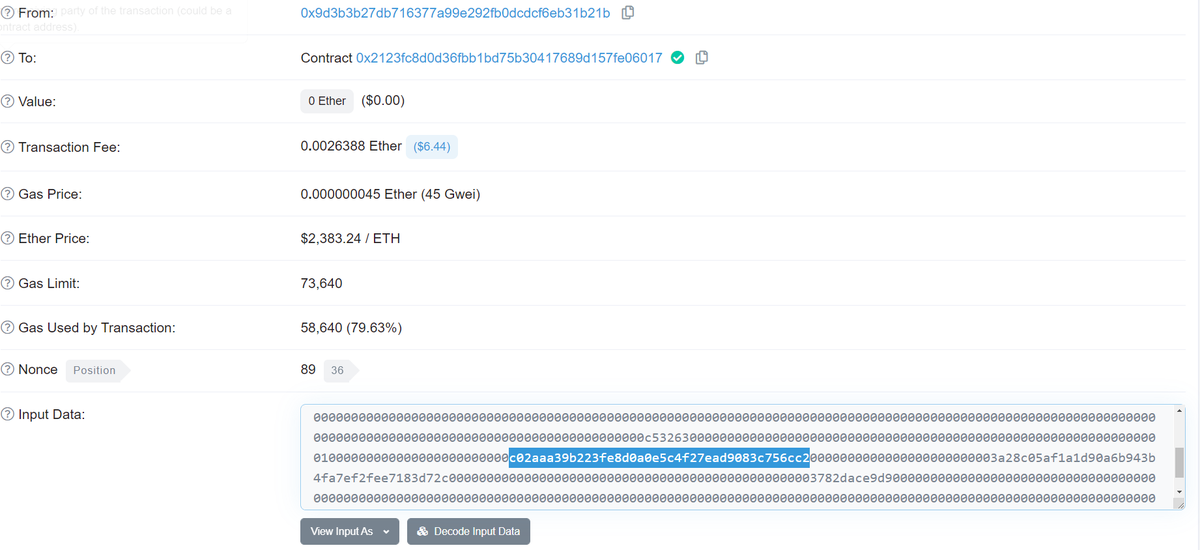
Lastly, we can also see in a trace of the execution that CHUM is calling another contract (!) "0x33..." that is hard to spot on Etherscan.
With these I think we can construct what happened.
With these I think we can construct what happened.

The attacker first injects the on-chain virus designed to transfer WETH out of the victim into CHUM
Victim arbs CHUM and the Uniswap pool calls transfer on CHUM as part of the swap
CHUM calls then contract 0x33 with the WETH transfer virus
Victim arbs CHUM and the Uniswap pool calls transfer on CHUM as part of the swap
CHUM calls then contract 0x33 with the WETH transfer virus
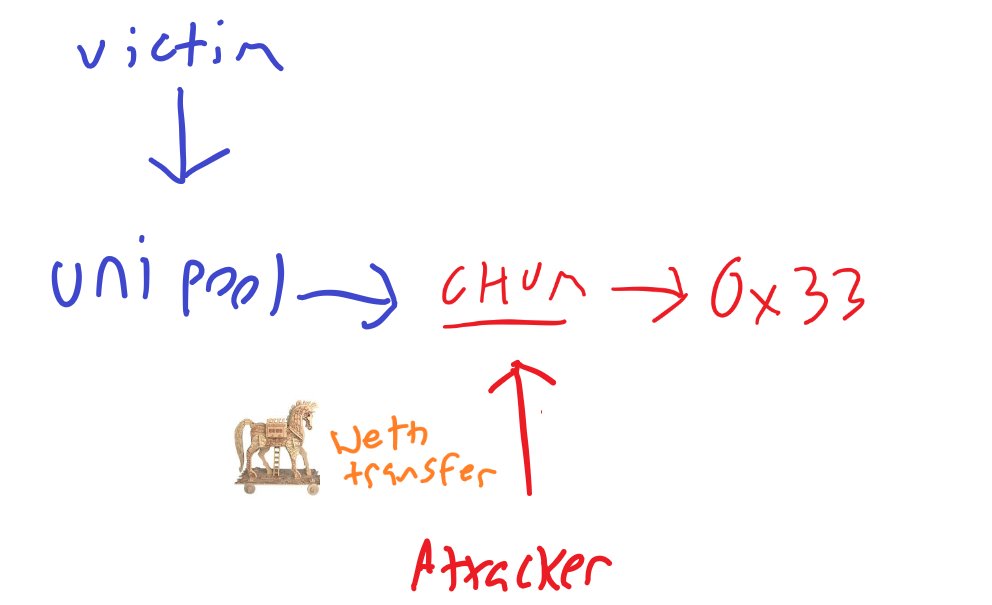
0x33 then calls the victim's contract with the WETH transfer virus, attempting to execute it
The victim's contract checks to see that the victim started the transaction and this condition passes.
The victim's contract executes the virus.
The attacker is sent 30 WETH.
The victim's contract checks to see that the victim started the transaction and this condition passes.
The victim's contract executes the virus.
The attacker is sent 30 WETH.
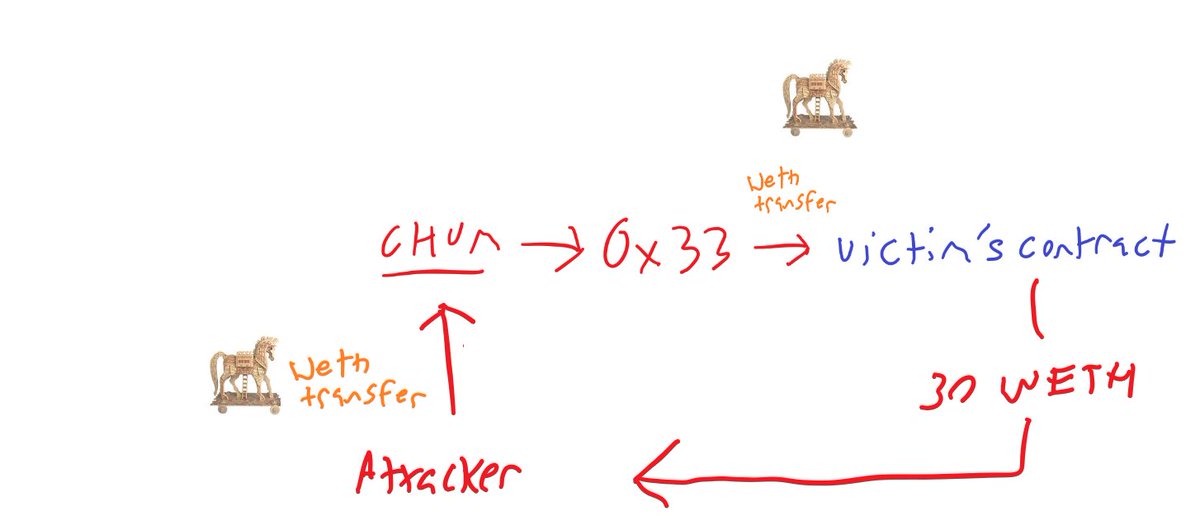
The attacker then IMMEDIATELY updated their WETH transfer virus and repeated this twice more for 35 WETH in total.
They were watching closely.
They were watching closely.
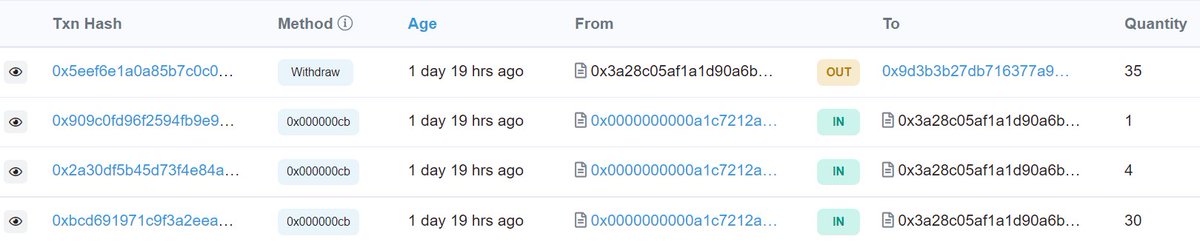
This was a highly targeted attack pointed at a specific bot's contract. It would only work for bots with a specific function AND if the bot used tx.origin as a safety check.
I have to wonder how they even found that vulnerability amongst hundreds of other bots.
I have to wonder how they even found that vulnerability amongst hundreds of other bots.
Still, it was relatively easy to defend against. First, you shouldn't use tx.origin as a safety check.
Second, you should check that your transaction has made a project before paying the miner!
Second, you should check that your transaction has made a project before paying the miner!
That is it for today everyone.
Check out our Github to learn more and get involved if you're interested in mitigating MEV's negative externalities:
github.com/flashbots/pm
Check out our Github to learn more and get involved if you're interested in mitigating MEV's negative externalities:
github.com/flashbots/pm
Huge shout to the Flashbots team who I am eternally grateful to for their tireless and excellent work
@phildaian @tzhen @epheph @ObadiaAlex @thegostep @jparyani @fiiiu_ @tkstanczak
@taarushv @LukeYoungblood @sui414
@phildaian @tzhen @epheph @ObadiaAlex @thegostep @jparyani @fiiiu_ @tkstanczak
@taarushv @LukeYoungblood @sui414
Profit***
• • •
Missing some Tweet in this thread? You can try to
force a refresh