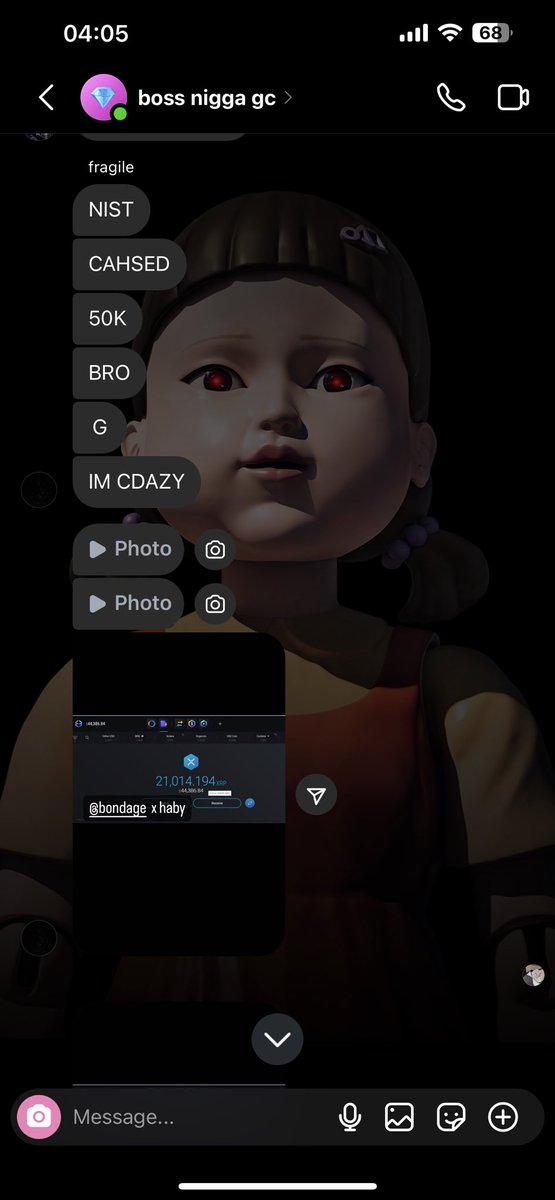
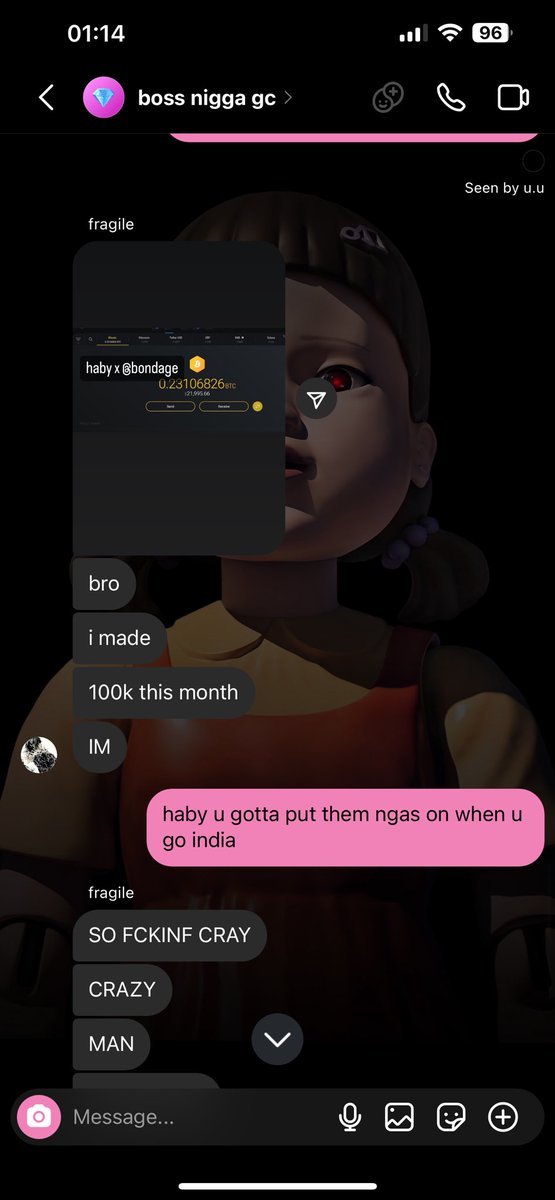
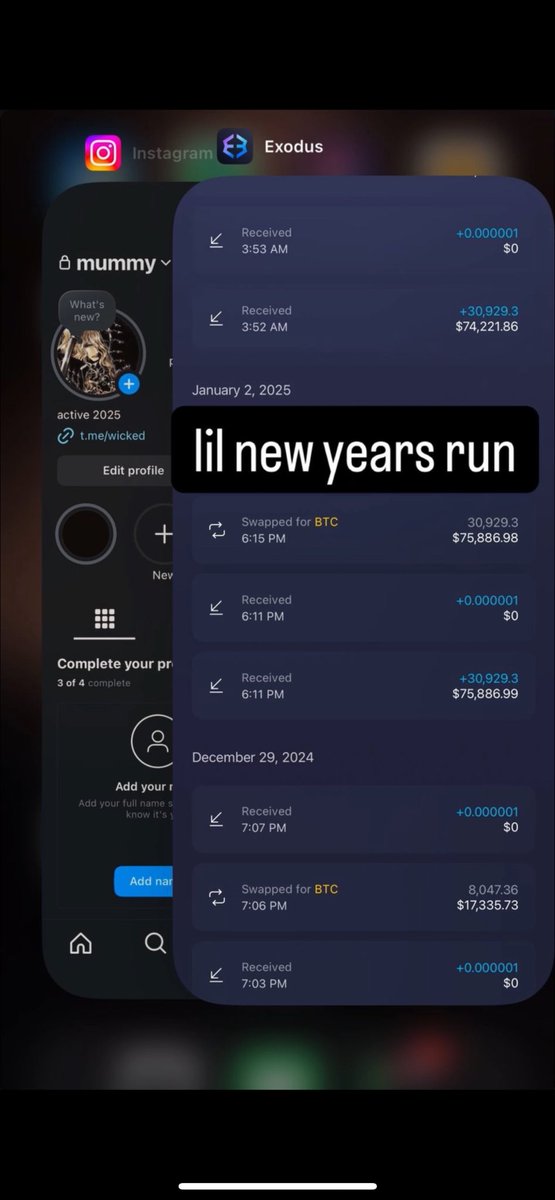
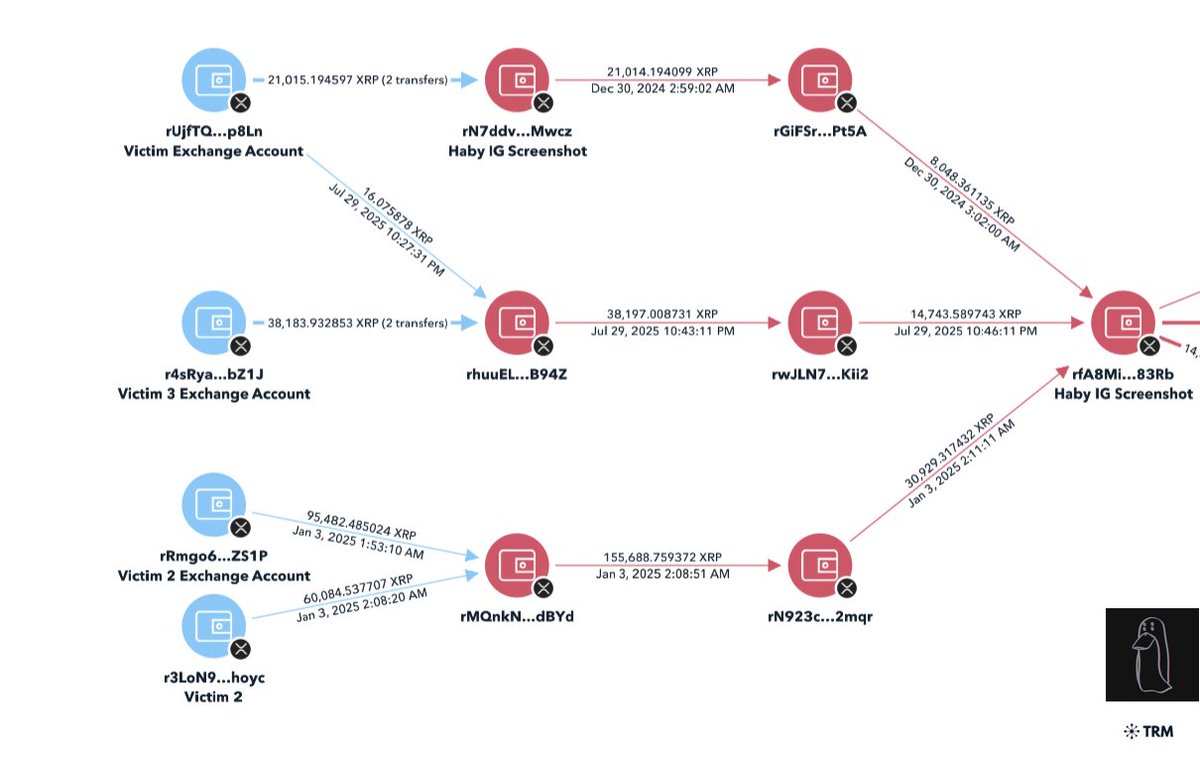
1/ Welcome to the next episode of marketers shilling IDOs that you should avoid.
This time featuring the team at Yellowblock:
TeddyCleps
The Crypto Monk
Crypto Birb
CryptoRangutang
This time featuring the team at Yellowblock:
TeddyCleps
The Crypto Monk
Crypto Birb
CryptoRangutang
2/ Want to live a extravagant lifestyle and flex on your audience?
See how you can as well below!
*perfectly sells the top*



See how you can as well below!
*perfectly sells the top*




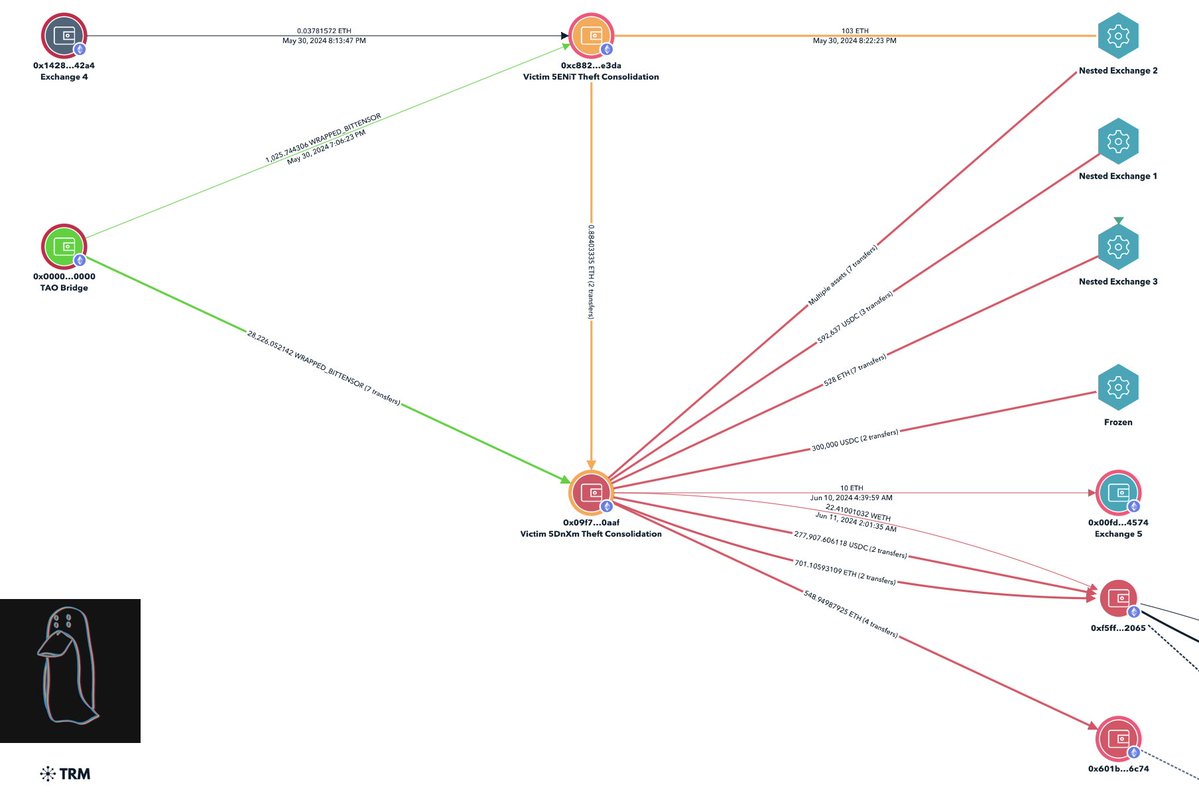
3/ Case 1: $POLK In my other threads we already know Moonrock & friends sell instantly.
Let’s see who actually pushes this out on Twitter.



Let’s see who actually pushes this out on Twitter.




6/ Case 4: $MATTER
This project suddenly changed it’s vesting schedule because of private sale investors repeatedly dumping . Guess who was quick to claim their tokens after the change?



This project suddenly changed it’s vesting schedule because of private sale investors repeatedly dumping . Guess who was quick to claim their tokens after the change?


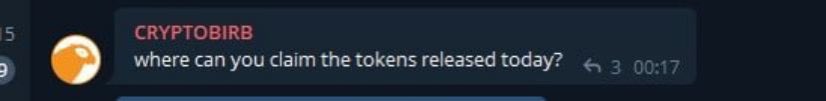

7/ No tweets from them about $MATTER or any other of these projects in months even though they were so “bullish” on them.
You’d think as private sale investors they’d aim to support the project longterm.



You’d think as private sale investors they’d aim to support the project longterm.




10/ This is another classic example of marketers pretending to trade who will shill anything available to them.
We all remember the engagement on Twitter during the first couple months of 2021. Imagine being a newbie seeing the tweets.
None of these tweets gave any disclosure.
We all remember the engagement on Twitter during the first couple months of 2021. Imagine being a newbie seeing the tweets.
None of these tweets gave any disclosure.
Follow for more threads in the future!
If you’re new and unfamiliar with Moonrock make sure to read this.
https://twitter.com/ZachXBT/status/1412600271260246016
• • •
Missing some Tweet in this thread? You can try to
force a refresh