
— A THREAD —
[1/n] We’re monitoring developments on a new piece of proof-of-concept #ransomware called #Chaos. It’s purportedly a .NET version of #Ryuk, but our analysis shows that its routines are different from Ryuk’s.
[1/n] We’re monitoring developments on a new piece of proof-of-concept #ransomware called #Chaos. It’s purportedly a .NET version of #Ryuk, but our analysis shows that its routines are different from Ryuk’s.

[2/n] Earlier versions of #Chaos were actually destructive #trojans that overwrote rather than encrypted files, which meant that victims had no way of restoring their files to their original state. 

[3/n] The third version of #Chaos was traditional #ransomware, having the ability to encrypt files via RSA/AES and also providing a decrypter. With this version, the creator asked for donations to support the ongoing development of Chaos. 
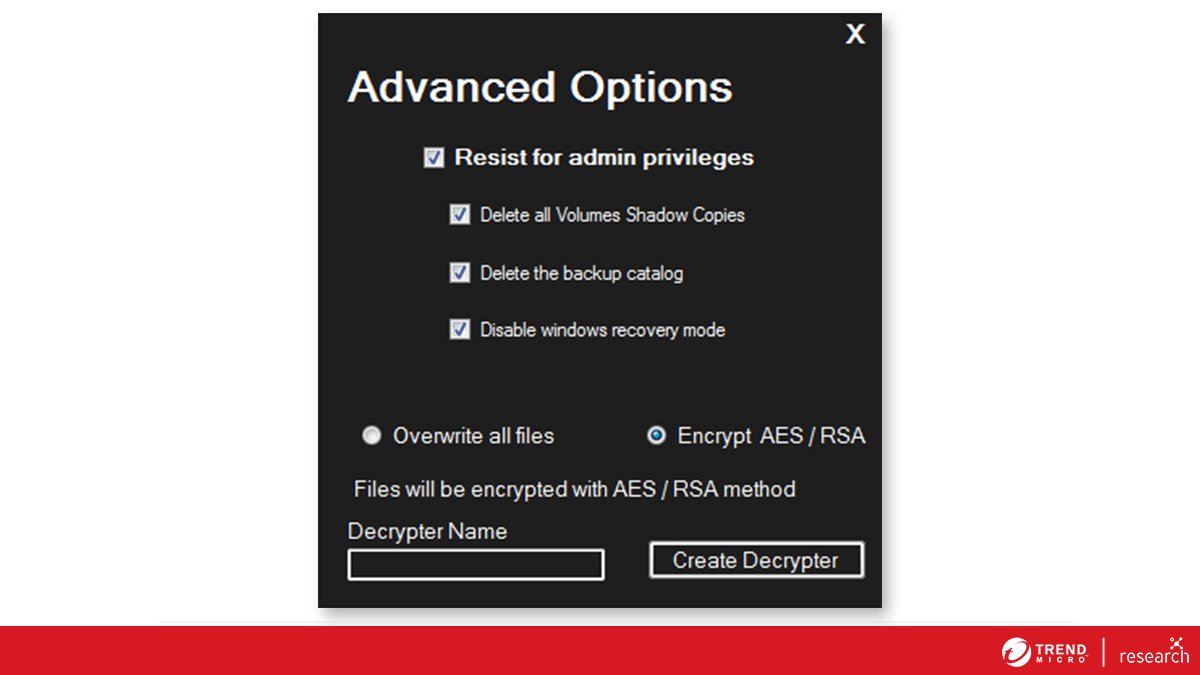
[4/n] The fourth version of #Chaos was recently released on an underground forum. It gained support for custom file extensions, the ability to change an infected machine’s desktop wallpaper, and an increase in the size limit of encrypted files to 2 MB. 

[5/n] While we have not yet detected an active infection or victim of the #Chaos #ransomware, we believe that the ransomware builder still poses a threat in the hands of malicious actors who have access to malware distribution and deployment.
[6/n] It appears that the #Chaos #ransomware is still undergoing evolution, since it lacks some features that many modern ransomware families have, such as the collection of data from victims that could be used for blackmailing if the ransom is not paid.
[7/n] The development of new #ransomware families and variants will always be a matter of concern. In our research, we provide recommendations that will help organizations prevent and mitigate the effects of modern ransomware attacks: research.trendmicro.com/3xqVtKH
• • •
Missing some Tweet in this thread? You can try to
force a refresh




