#HuntingTipOfTheDay
If you're in a SOC or IR role and don't use @GitHub because "you're not a developer", read on! It can be powerful when paired with #VirusTotal.
Came across this interesting command. What is it doing? 🤔
If you're in a SOC or IR role and don't use @GitHub because "you're not a developer", read on! It can be powerful when paired with #VirusTotal.
Came across this interesting command. What is it doing? 🤔
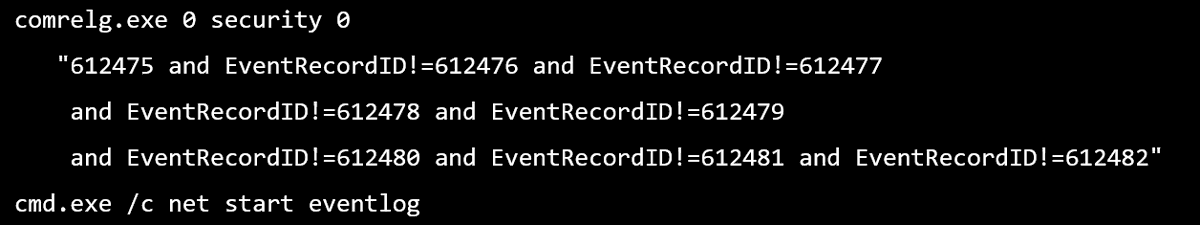
It certainly seems to be mucking with the event log, given the security parameter, it seems clear it's interested in the Windows security event log.
The most obvious explanation is that it is deleting records--the ones that correspond to the EventRecordIDs listed.
The most obvious explanation is that it is deleting records--the ones that correspond to the EventRecordIDs listed.

How can we find out more about this tool? The tool name (comrelg.exe) is faked🤥 and the hash didn't lead anywhere and I didn't have a copy of the sample. (set aside pivoting on imphash etc for now🧠)
I searched #VirusTotal for the command to start the event log and bounded the file size to match the sample.
This led to some interesting hits. Looking at the samples string content on VT, it showed definite event log manipulation and many more relevant strings.

This led to some interesting hits. Looking at the samples string content on VT, it showed definite event log manipulation and many more relevant strings.


Since many security tools are on @GitHub, let's search for those strings. Only a small number of projects! 😃💪 

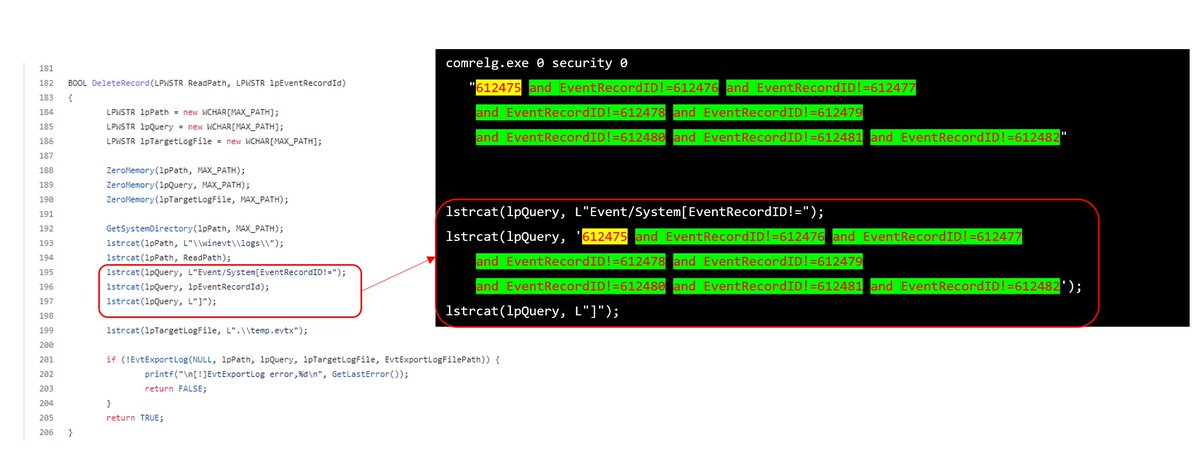
✅This one seems a definite match based on strings.
✅If we look closer at the command line params, we can see how they are substituted into an XPath query.
✅And we see the tool invoke the command to restart the eventlog after it's been modified.
🏁github.com/3gstudent/Even…

✅If we look closer at the command line params, we can see how they are substituted into an XPath query.
✅And we see the tool invoke the command to restart the eventlog after it's been modified.
🏁github.com/3gstudent/Even…

Hope you found it helpful how #VirusTotal content search and @GitHub code search can enhance your SOC investigations! #DFIR #infosec
Also, rather than surgically edit the event log, many export a copy EXCEPT for the events to remove. Then replace it. That's the reason for the != (EventRecordID!=612476 ...)
📎github.com/3gstudent/Even…
📎github.com/agnusha/EventL…
📎github.com/QAX-A-Team/Eve…
📎docs.microsoft.com/en-us/windows/…
📎github.com/3gstudent/Even…
📎github.com/agnusha/EventL…
📎github.com/QAX-A-Team/Eve…
📎docs.microsoft.com/en-us/windows/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh











