
Corporate Vice President, Security Fellow, Microsoft Security Research, johnla(AT)https://t.co/3dGtq71Nby
How to get URL link on X (Twitter) App




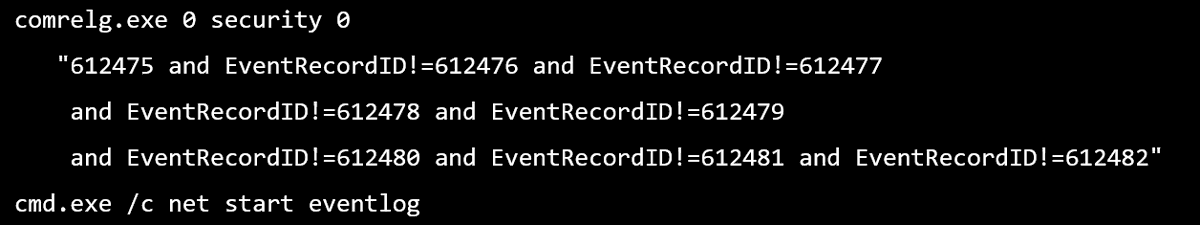
 It certainly seems to be mucking with the event log, given the security parameter, it seems clear it's interested in the Windows security event log.
It certainly seems to be mucking with the event log, given the security parameter, it seems clear it's interested in the Windows security event log. 
https://twitter.com/JohnLaTwC/status/682351102688284672



https://twitter.com/moo_hax/status/1314429486335549440



 This XLL decodes a Base64 string using CryptStringToBinary and uses the Nt APIs to jump to it.
This XLL decodes a Base64 string using CryptStringToBinary and uses the Nt APIs to jump to it.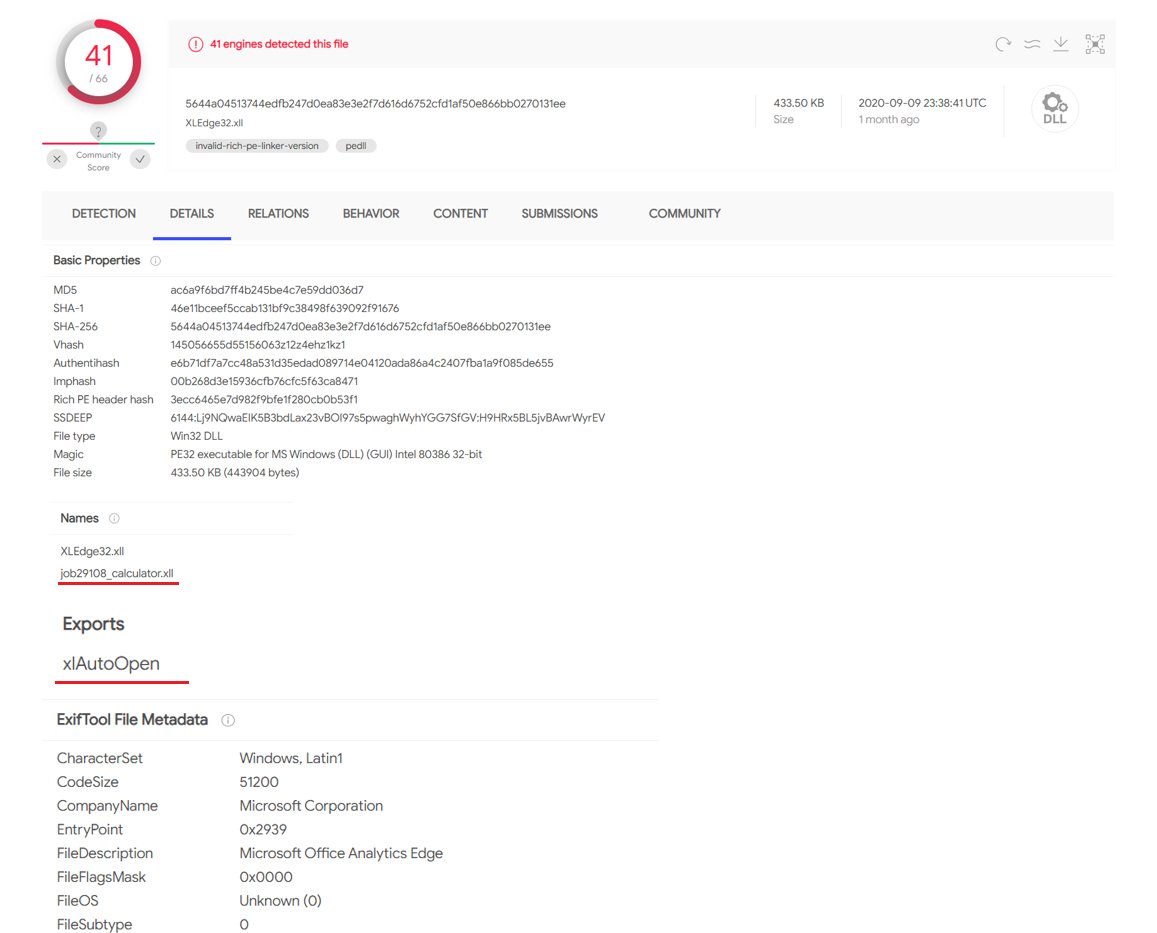


https://twitter.com/_saadk/status/1288529007714107392"There is no love, there are only proofs of love"
https://twitter.com/JohnLaTwC/status/682350922710659073
https://twitter.com/ryanaraine/status/12885193313793720322⃣
https://twitter.com/JohnLaTwC/status/682351102688284672

 In 2007 there was a massive avalanche on the right side. The force was so strong it carried across Gold Creek and up the left side of the valley causing the trees to fall UPHILL.
In 2007 there was a massive avalanche on the right side. The force was so strong it carried across Gold Creek and up the left side of the valley causing the trees to fall UPHILL. 

https://twitter.com/DidierStevens/status/1243943478557577216This started with a pentest Excel4 macro file by @spamv noticed by @malwrhunterteam:
https://twitter.com/JohnLaTwC/status/1242546135169785856



 Maldocs that launch code via CreateShortcut and SendKeys
Maldocs that launch code via CreateShortcut and SendKeys

 and
and