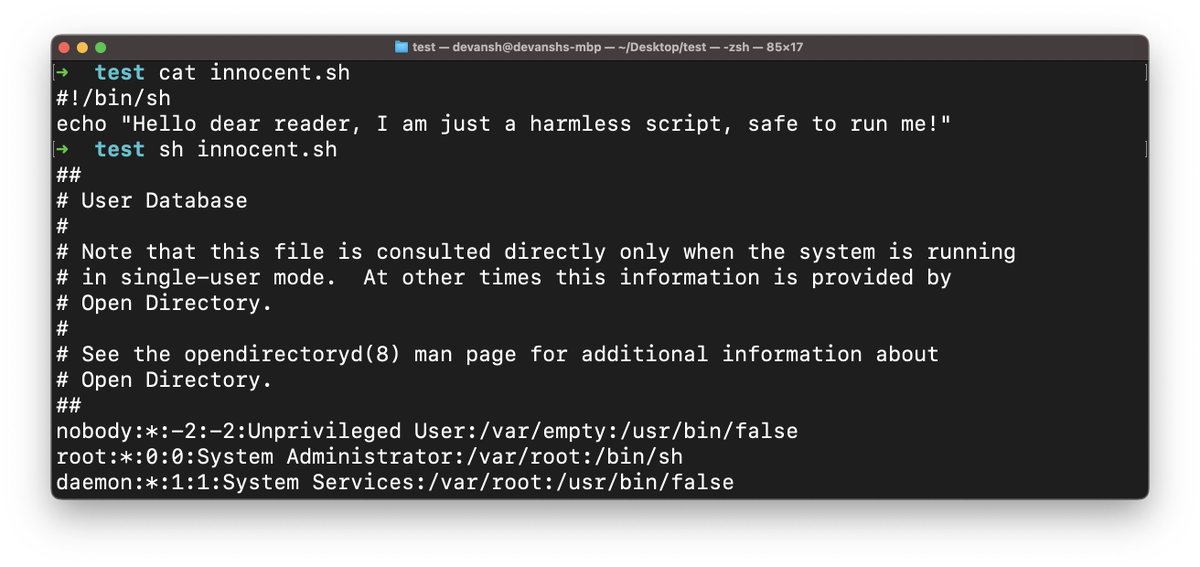
My notes (actually a checklist ✅) for getting into Blockchain Security, a thread 🧵
I have a detailed article (Genesis 0x001) coming v soon, the content will never be monetized, but if you wanna show some support I have a buy me a coffee page (or just buy some biscuits for street dogs, that will make me happy as well).
buymeacoffee.com/Asm0d3us
buymeacoffee.com/Asm0d3us
• • •
Missing some Tweet in this thread? You can try to
force a refresh