There’s a lot to unpack in @MsftSecIntel’s latest blog on the CVE-2021-40444 vulnerability. Here’s a thread of some of the details that I think are notable
https://twitter.com/MsftSecIntel/status/1438291542142246920
The volume of initial exploitation was limited. Most security orgs I talked to didn’t observe it directly in their telemetry
“In August…MSTIC identified a small number of attacks (less than 10) that attempted to exploit a remote code execution vulnerability in MSHTML”
“In August…MSTIC identified a small number of attacks (less than 10) that attempted to exploit a remote code execution vulnerability in MSHTML”
The attribution behind the various components involved in the campaigns is a little more complicated than I typically see (we’ll unpack that more shortly).
But the end motivation was human-operated ransomware by cyber criminals
But the end motivation was human-operated ransomware by cyber criminals

Attack surface reduction rules (ASR) mitigated the specific attack vector we observed in the wild.
I feel like ASR rules are an overlooked defensive capability by many enterprises. Seriously - go read up on ASR and implement as many as you can
docs.microsoft.com/en-us/microsof…
I feel like ASR rules are an overlooked defensive capability by many enterprises. Seriously - go read up on ASR and implement as many as you can
docs.microsoft.com/en-us/microsof…

The exploit chain involved a series of steps that when combined sort of resembles a “cyber Rube Goldberg machine”
These “features” will play into future detection opportunities for defenders due to the processes and arguments that need to be spawned
These “features” will play into future detection opportunities for defenders due to the processes and arguments that need to be spawned

Every cyber security company tracks threat actors in a unique way based on their telemetry and insights. At @MsftSecIntel - we track threat actors initially as DEV-### clusters that may get collapsed into other clusters (based on new analysis) or “promoted” to a proper name 

Now this is where attribution gets challenging. It’s clear that large set of C2 infrastructure registered by a distinct set of operators
But the same infrastructure has been used by multiple different ransomware actors
Hypothesis: Cobalt Strike C2-as-a-service (aka CS-C2aaS)😜
But the same infrastructure has been used by multiple different ransomware actors
Hypothesis: Cobalt Strike C2-as-a-service (aka CS-C2aaS)😜

I feel like (possibly new) as-a-service model can really throw intel attribution curve ball (I know we had internal convos trying to make heads or tails of the disparate activity we were/are seeing)
We saw same CS-C2aaS delivering Trickbot/Bazaloader payloads w/o CVE-2021-40444
We saw same CS-C2aaS delivering Trickbot/Bazaloader payloads w/o CVE-2021-40444

One explanation of the sophistication of the lure document (or lack thereof) vs. use of an unpatched exploit - could indicate that the group deploying the exploit didn’t develop the exploit
Cc: @HackingLZ
Cc: @HackingLZ

It probably doesn’t take a rocket 🚀scientist to figure out - I’m no expert in oleObject relationships and what is normal vs. anomalous. Fortunately I work with folks on the #MSTIC team who are gifted at spotting nuanced anomalies in maldocs - and dig deeper to get to the truth 
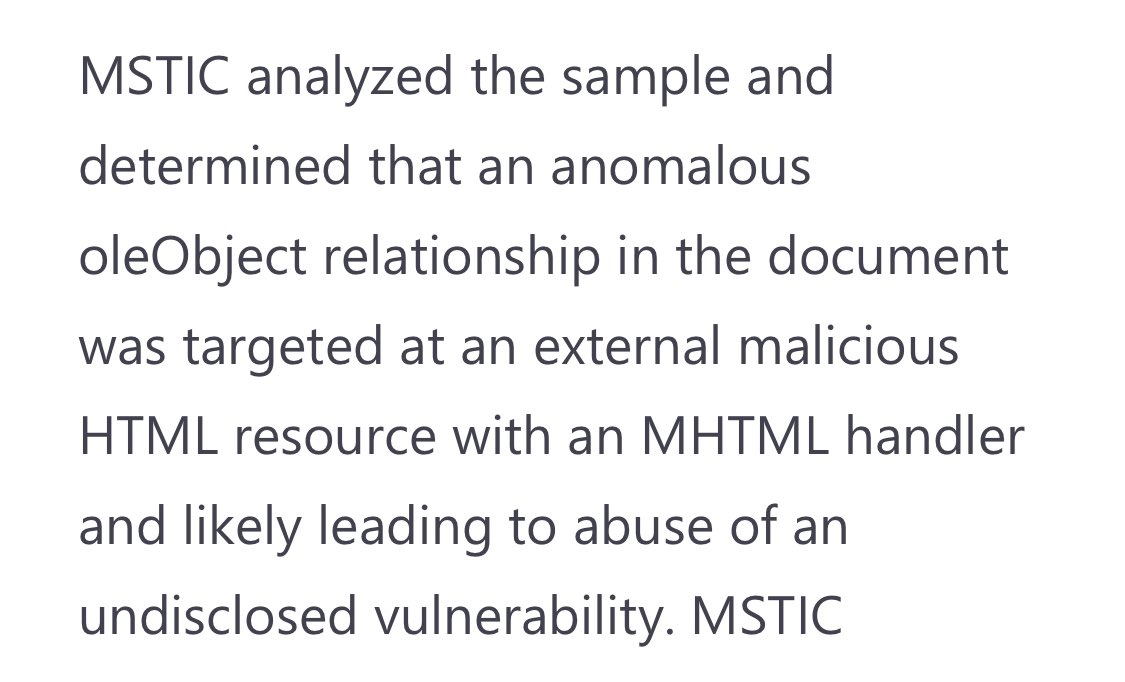
Getting back to “cyber Rube Goldberg” machine
Due to the nature of exploit requiring path traversal & URL protocol handlers - makes for more durable hunting signal that is difficult for attackers to evade
Note: this may pick up activity that may not be related to CVE-2021-40444
Due to the nature of exploit requiring path traversal & URL protocol handlers - makes for more durable hunting signal that is difficult for attackers to evade
Note: this may pick up activity that may not be related to CVE-2021-40444

If you want to learn more about the infrastructure that is related to the possible Cobalt Strike C2-as-a-Service (CSC2aaS) (aka DEV-0365) - check out @RiskIQ’s companion blog
riskiq.com/blog/external-…
riskiq.com/blog/external-…
• • •
Missing some Tweet in this thread? You can try to
force a refresh