
Microsoft Threat Intelligence Center - Former Incident Responder & Chief Security Architect @Mandiant
How to get URL link on X (Twitter) App


https://twitter.com/george_kurtz/status/1814235001745027317
 We discussed how DEV-0537/LAPSUS$ used this technique to gain initial access to a low privileged identity at targeted orgs in our ransomware ecosystem compendium
We discussed how DEV-0537/LAPSUS$ used this technique to gain initial access to a low privileged identity at targeted orgs in our ransomware ecosystem compendium



https://twitter.com/MsftSecIntel/status/1438291542142246920The volume of initial exploitation was limited. Most security orgs I talked to didn’t observe it directly in their telemetry



 First up is @HoldSecurity discussing how to harvest information from botnets
First up is @HoldSecurity discussing how to harvest information from botnets
https://twitter.com/josephmenn/status/1105599568765378562The reality is the large defense contractors have enormous supply chains of sub contractors and suppliers - many of which are small(er) businesses that don’t have the size/resources/security maturity to adequately protect the data - that the bigger defense contractors have

 APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim
APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim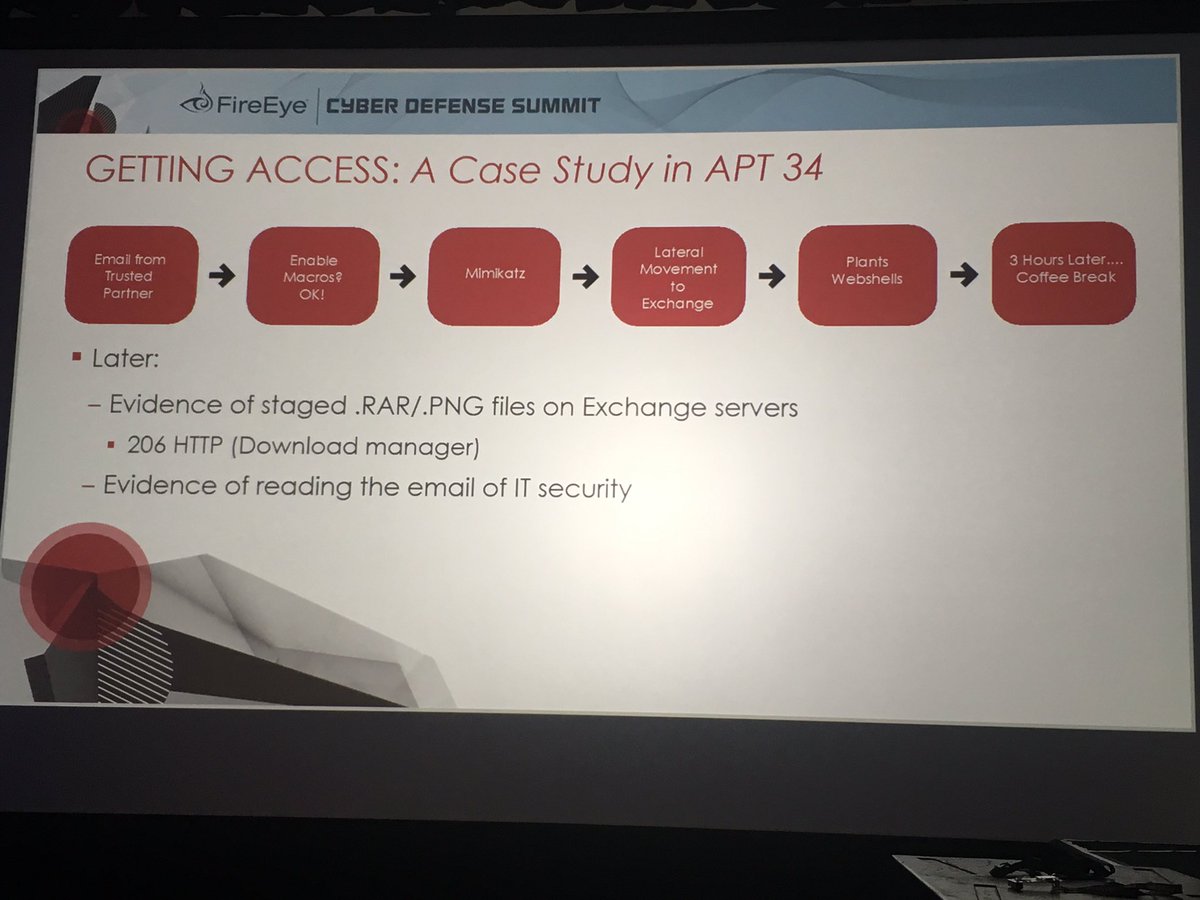

 APT38 targeted banks (SWIFT messaging initiated wire transfers you've read about in the news) and crypto currency exchanges (among other orgs)
APT38 targeted banks (SWIFT messaging initiated wire transfers you've read about in the news) and crypto currency exchanges (among other orgs)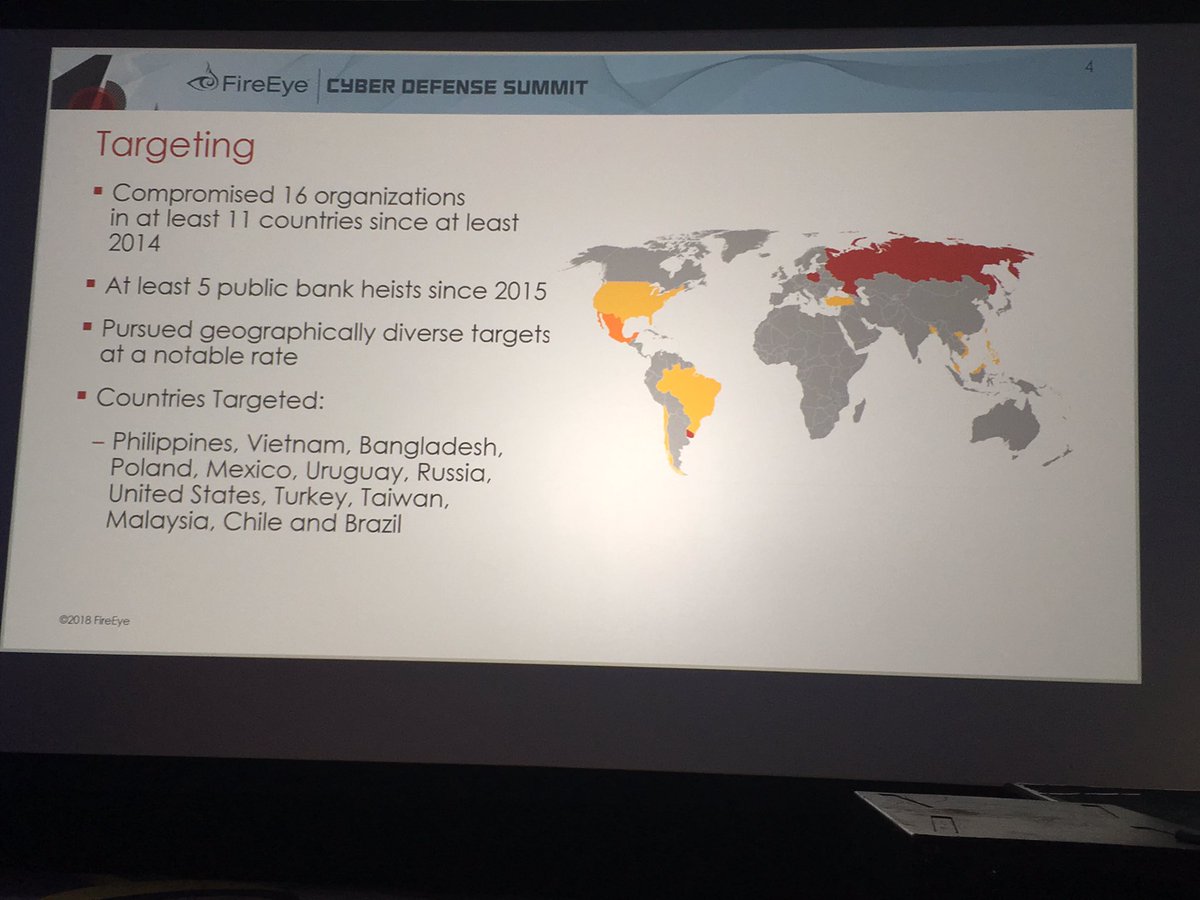

 It's not often that you see ACI Shims used for persistence
It's not often that you see ACI Shims used for persistence 
https://twitter.com/realDonaldTrump/status/1018072081676865536