
A comprehensive thread on OWASP!
What is OWASP Top 10?
2013 vs 2017 vs 2021 ?
How OWASP is useful for pentesters and bug bounty hunters?
My Views on OWASP 2021 Update?
cc - @shifacyclewala @Hacktifycs
What is OWASP Top 10?
2013 vs 2017 vs 2021 ?
How OWASP is useful for pentesters and bug bounty hunters?
My Views on OWASP 2021 Update?
cc - @shifacyclewala @Hacktifycs
Who is Owasp?
→ Open Web Application Security Project
→ its a non-profit foundation dedicated to improving the security of software. @owasp operates as open community model, where anyone can participate in & contribute to projects, events, online chats, and more.
{1/17}
→ Open Web Application Security Project
→ its a non-profit foundation dedicated to improving the security of software. @owasp operates as open community model, where anyone can participate in & contribute to projects, events, online chats, and more.
{1/17}
What is Owasp?
→ OWASP Top 10 is an online document on OWASP’s website that provides ranking of and remediation guidance for the top 10 most critical web application security risks
{2/17}
→ OWASP Top 10 is an online document on OWASP’s website that provides ranking of and remediation guidance for the top 10 most critical web application security risks
{2/17}
Why Owasp it important?
→ OWASP maintains the Top 10 list and has done so since 2003. The list is updated in accordance with advancements and changes in the AppSec Industry every few years.
{3/17}
→ OWASP maintains the Top 10 list and has done so since 2003. The list is updated in accordance with advancements and changes in the AppSec Industry every few years.
{3/17}
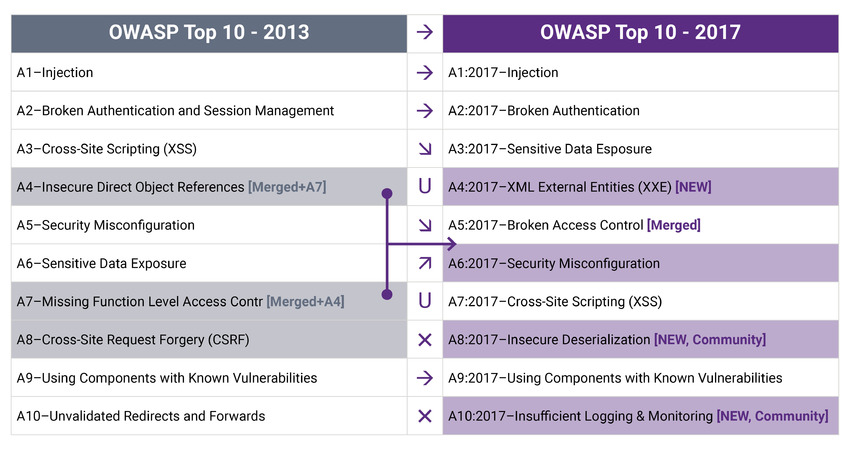
OWASP 2013 vs 2017 ?
Key Differences:
NEW added: ↓
→ XXE
→ Insecure Deserialization
→ Insufficient Logging & Monitoring
Merged :↓
→IDOR + MFLAC = BAC
{4/17}
Key Differences:
NEW added: ↓
→ XXE
→ Insecure Deserialization
→ Insufficient Logging & Monitoring
Merged :↓
→IDOR + MFLAC = BAC
{4/17}
Injection :
→ Injection occurs when an attacker exploits insecure code to inject their own code into a program/website/DB.
→ Examples - SQLi, LDAP Injection, Python Injection, Command Injection, Remote Code Execution
Fix: Source code review, SAST & DAST.
{5/17}
→ Injection occurs when an attacker exploits insecure code to inject their own code into a program/website/DB.
→ Examples - SQLi, LDAP Injection, Python Injection, Command Injection, Remote Code Execution
Fix: Source code review, SAST & DAST.
{5/17}
Broken Authentication:
→ Improper authentication mechanism where attacker is able to bypass the login mechanism like Email/Pass, OTP, Captcha etc.
→ Session Related issues like session mismanagement, lack of expiration etc.
Fix: MFA System, Strong Session Management
{6/17}
→ Improper authentication mechanism where attacker is able to bypass the login mechanism like Email/Pass, OTP, Captcha etc.
→ Session Related issues like session mismanagement, lack of expiration etc.
Fix: MFA System, Strong Session Management
{6/17}
Sensitive Data Exposure:
→ Any sensitive data including source code,api,passwords etc been disclosed
→ Directory listing, Github leaks, EXIF Data
Fix: Data encryption, tokenization, proper key management, disabling response caching, Restricted access control
{7/17}
→ Any sensitive data including source code,api,passwords etc been disclosed
→ Directory listing, Github leaks, EXIF Data
Fix: Data encryption, tokenization, proper key management, disabling response caching, Restricted access control
{7/17}
XML External Entities:
→ Attacker is able to include hostile XML content due to insecure code, integrations, or dependencies in applications
→ Can lead to file disclosure, DOS, SSRF
Fix: Disabling External DTDs, Whitelisting, Server side input validation
{8/17}
→ Attacker is able to include hostile XML content due to insecure code, integrations, or dependencies in applications
→ Can lead to file disclosure, DOS, SSRF
Fix: Disabling External DTDs, Whitelisting, Server side input validation
{8/17}
Broken Access Control:
→ The attacker is able to operate as the user or as an administrator in the system. He is able to elevate privileges on the app
→ Privilege Escalation - Horizontal (Same access) & Vertical (higher access)
Fix: Patch unintended access-controls
{9/17}
→ The attacker is able to operate as the user or as an administrator in the system. He is able to elevate privileges on the app
→ Privilege Escalation - Horizontal (Same access) & Vertical (higher access)
Fix: Patch unintended access-controls
{9/17}
Security Misconfiguration:
→ Occurs when design or configuration weaknesses result from a configuration error
→ App running on default configuration, poorly secured systems
Fix: Updating/Patching the systems, Updating Default / secure configs.
{10/17}
→ Occurs when design or configuration weaknesses result from a configuration error
→ App running on default configuration, poorly secured systems
Fix: Updating/Patching the systems, Updating Default / secure configs.
{10/17}
Cross-Site Scripting (XSS):
→ Attacker is able to load & execute arbitrary supplied javascript code in the application
→ 3 Types - Reflected, Stored, DOM
Fix: Input Sanitization, HTML Encoding
{11/17}
→ Attacker is able to load & execute arbitrary supplied javascript code in the application
→ 3 Types - Reflected, Stored, DOM
Fix: Input Sanitization, HTML Encoding
{11/17}
Insecure Deserialization:
→ In app like PHP, Ruby where deserialization flaws allow an attacker to remotely execute code in the system
→ It deserializes hostile objects that were supplied by an attacker.
Fix: do not accept serialized objects from untrusted sources
{12/17}
→ In app like PHP, Ruby where deserialization flaws allow an attacker to remotely execute code in the system
→ It deserializes hostile objects that were supplied by an attacker.
Fix: do not accept serialized objects from untrusted sources
{12/17}
Insufficient Logging And Monitoring:
→ Timely Logging to be done for the application to be aware of ongoing or upcoming risks
→ Failure to log & monitor a site leaves it vulnerable to more severe compromising activities
Fix: All Activities to be logged on the server
{13/17}
→ Timely Logging to be done for the application to be aware of ongoing or upcoming risks
→ Failure to log & monitor a site leaves it vulnerable to more severe compromising activities
Fix: All Activities to be logged on the server
{13/17}
2017 vs 2021 :
Key Differences:
NEW added: ↓
→ Insecure Design
→ Software & Data Integrity failures (SDIF)
→ SSRF
Merged :↓
→ XSS = Injection
→ XXE = Security Misconfiguration
→ Insecure Deserialization = SDIF
→ SDE = Cryptographic Failures
{14/17}
Key Differences:
NEW added: ↓
→ Insecure Design
→ Software & Data Integrity failures (SDIF)
→ SSRF
Merged :↓
→ XSS = Injection
→ XXE = Security Misconfiguration
→ Insecure Deserialization = SDIF
→ SDE = Cryptographic Failures
{14/17}

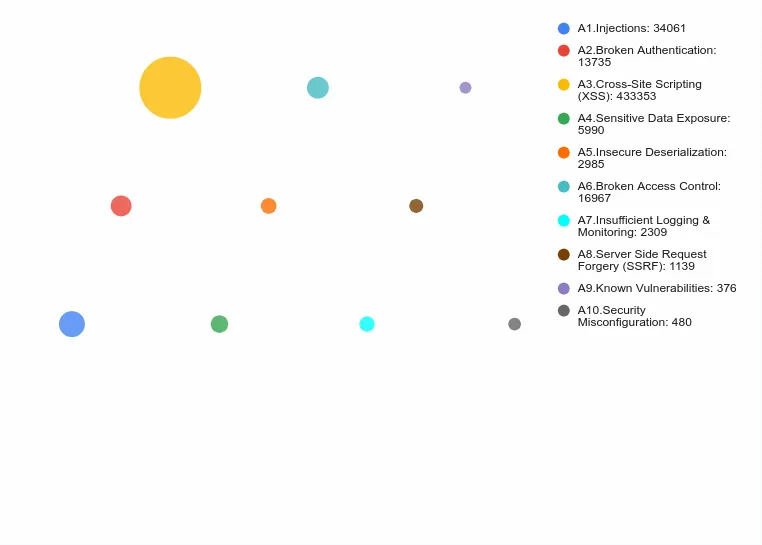
Interesting distribution of these categories by amount of security reports, mean bulletins, bug bounties, exploits etc. ( XSS is the champ) src: lab.wallarm.com/owasp-top-10-2…
{15/17}
{15/17}
How OWASP is useful for pentesters and bug bounty hunters?
→ OWASP is a standard document to categorise the most common issues in the general appsec space
→ The top 10 list will provide sufficient help to understand the current trends/shift for vulnerabilities
{16/17}
→ OWASP is a standard document to categorise the most common issues in the general appsec space
→ The top 10 list will provide sufficient help to understand the current trends/shift for vulnerabilities
{16/17}
My Views on OWASP Top 10 2021
→ The shift is more towards secure design and architecture issues
→ With XXE, ID & SSRF could be merged into Security Misconfiguration
→ Broader Visualization of Business Logic & supply chain attacks in issues in Insecure Design
{17/17}
→ The shift is more towards secure design and architecture issues
→ With XXE, ID & SSRF could be merged into Security Misconfiguration
→ Broader Visualization of Business Logic & supply chain attacks in issues in Insecure Design
{17/17}
• • •
Missing some Tweet in this thread? You can try to
force a refresh



