A thread on what caught my eye from the @WhiteHouse's Fact Sheet on 'Ongoing Public U.S. Efforts to Counter #Ransomware'.
#InThaCybers #CyberDiplomacy
#InThaCybers #CyberDiplomacy
The second paras describe the national security threat posed by ransomware and the global nature of that threat. No surprises here. 

Counter-ransomware policy = Multi-stakeholder by design.
The state must work with industry and other states because of inherent technological and economic realities.
Plus, it takes a network to take down a network like a transnational ransomware gang.
The state must work with industry and other states because of inherent technological and economic realities.
Plus, it takes a network to take down a network like a transnational ransomware gang.

Onto the four pillars of USA counter-ransomware policy.
Pillar 1, including #ReleaseTheHounds
Timely in light of DIRNSA's recent remarks:
Pillar 1, including #ReleaseTheHounds
Timely in light of DIRNSA's recent remarks:
https://twitter.com/ravirockks/status/1445713355834941449?s=20

Pillar 2.
Firstly, I am thrilled that the word, 'Resilience', is used in the headline here.
More holistic than 'Security'.
In addition to the need to enact law and instruments is that to send the right signals via other policy levers.
Firstly, I am thrilled that the word, 'Resilience', is used in the headline here.
More holistic than 'Security'.
In addition to the need to enact law and instruments is that to send the right signals via other policy levers.

Pillar 3.
I have written on the need to hit the money eg my Hons and the following article (anujolt.org/post/1101-rans…).
I am glad to see the acknowledgement here that the USA already has AMLCTF laws in place re virtual assets and needs to enforce those _existing_ laws,
I have written on the need to hit the money eg my Hons and the following article (anujolt.org/post/1101-rans…).
I am glad to see the acknowledgement here that the USA already has AMLCTF laws in place re virtual assets and needs to enforce those _existing_ laws,

Pillar 4: #CyberDiplomacy
Working with states to keep their noses clean in the cybers. Including joint offensive ops like against ISIS?
Also, what does 'imposing consequences and holding accountable' mean? OCOs? Financial countermeasures?
Working with states to keep their noses clean in the cybers. Including joint offensive ops like against ISIS?
Also, what does 'imposing consequences and holding accountable' mean? OCOs? Financial countermeasures?

Onto some of the actions taken by the USA under the above pillars.
Eg the updated OFAC advisory = sanctions law as a lever for incident and payment reporting?
Eg the updated OFAC advisory = sanctions law as a lever for incident and payment reporting?

Eg #ReleaseTheHounds = SIGINTing --> Starting the symphony.
Also, SIGINTing which can inform financial countermeasures, by the looks of the final bit there?
Also, SIGINTing which can inform financial countermeasures, by the looks of the final bit there?

A concrete achievement there.
One of the highest stakes ICS/OT security games to be played is in the electricity generation/distribution context.
Good stuff.
One of the highest stakes ICS/OT security games to be played is in the electricity generation/distribution context.
Good stuff.

Note that the FATF Recommendations were amended to cover virtual assets and VASPs during the US Presidency of @FATFNews in 2018 (a few days before I submitted by Hons thesis on the AML regulation of virtual assets, funnily enough).
Good to keep up said efforts.
#CyberDiplomacy
Good to keep up said efforts.
#CyberDiplomacy

#CyberDiplomacy writ large here.
Add the Ransomware Annex to the G7 Finance Ministers and Central Bank Governors’ Statement on Digital Payments (October 2020), FVEY Ministerial Statement on ransomware (April 2021) and the UN GGE final report (July 2021).
Add the Ransomware Annex to the G7 Finance Ministers and Central Bank Governors’ Statement on Digital Payments (October 2020), FVEY Ministerial Statement on ransomware (April 2021) and the UN GGE final report (July 2021).

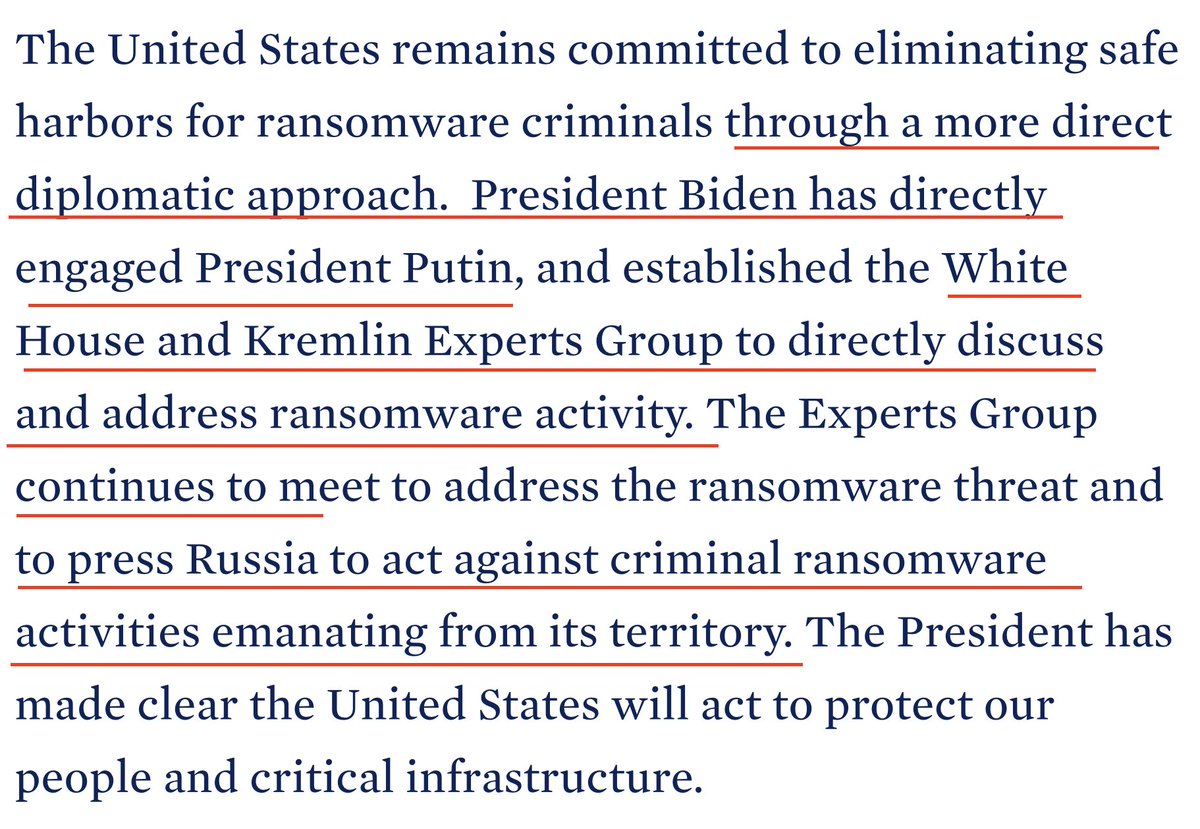
Question: what has the diplomacy with Russia actually achieved?
Ransomware activity targeting the USA and her allies hasn't exactly calmed down, has it?
Especially such activity which is originating from Russia, as admitted by @CISAgov's Director.

Ransomware activity targeting the USA and her allies hasn't exactly calmed down, has it?
Especially such activity which is originating from Russia, as admitted by @CISAgov's Director.
https://twitter.com/ravirockks/status/1446703694968344578?s=20
I recently looked at the issue of ransomware attacks against American critical infrastructure even after policymaking such as that mentioned above.
https://twitter.com/TechLegalUpdate/status/1441296972543979523?s=20
So said direct diplomacy with Russia did not even achieve enough to justify inviting _Russia_ to the counter-ransomware summit?
reuters.com/article/us-usa…
reuters.com/article/us-usa…
And in synch with what:
1) we Aussies said just yesterday;
1) we Aussies said just yesterday;
https://twitter.com/ravirockks/status/1448185818690965507?s=20
• • •
Missing some Tweet in this thread? You can try to
force a refresh















