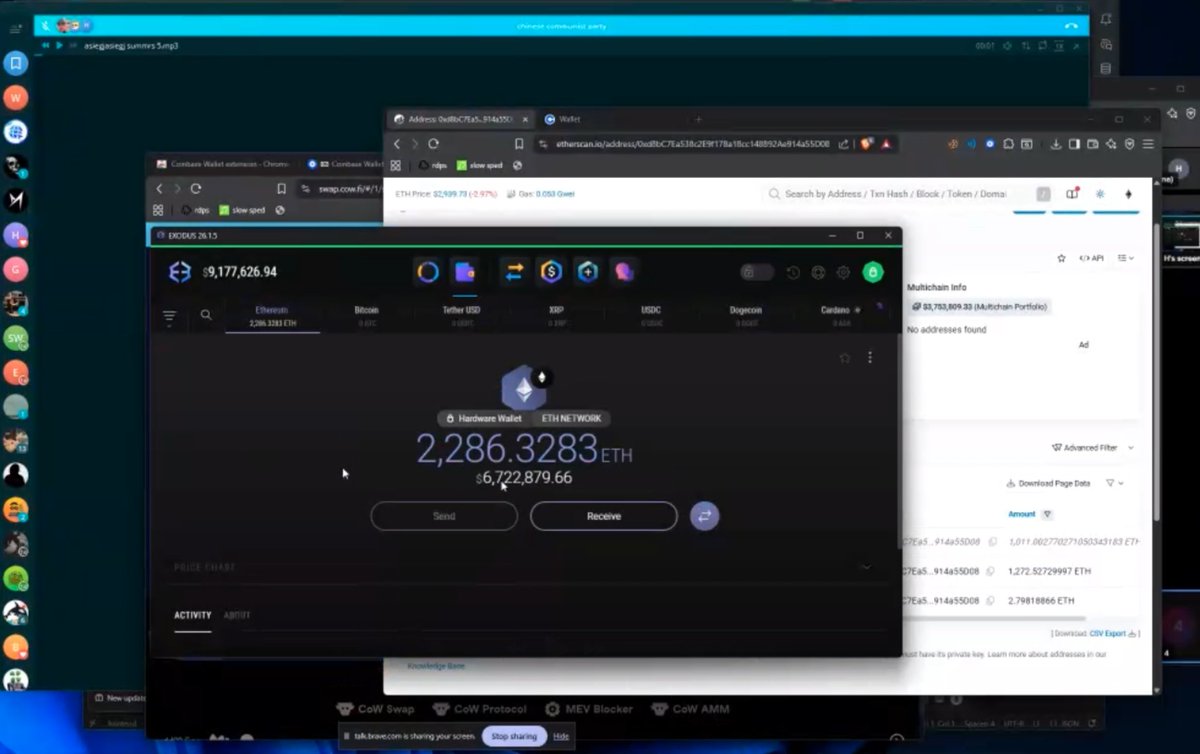
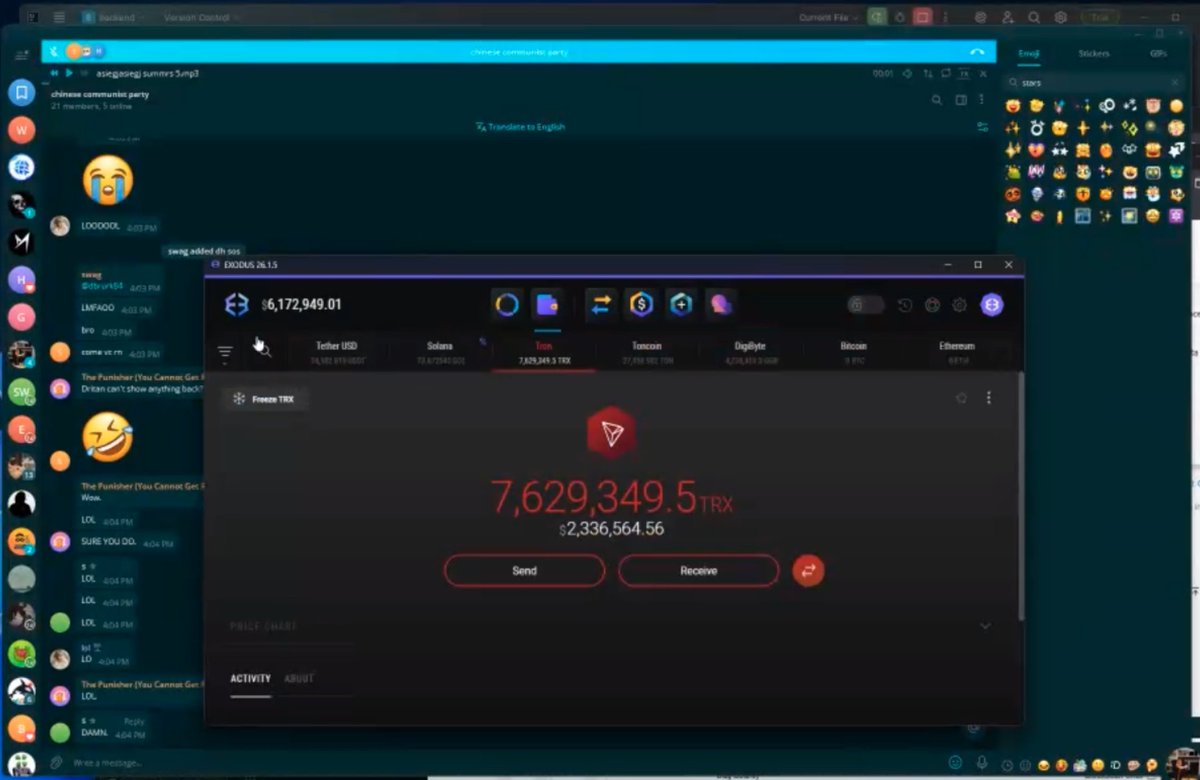
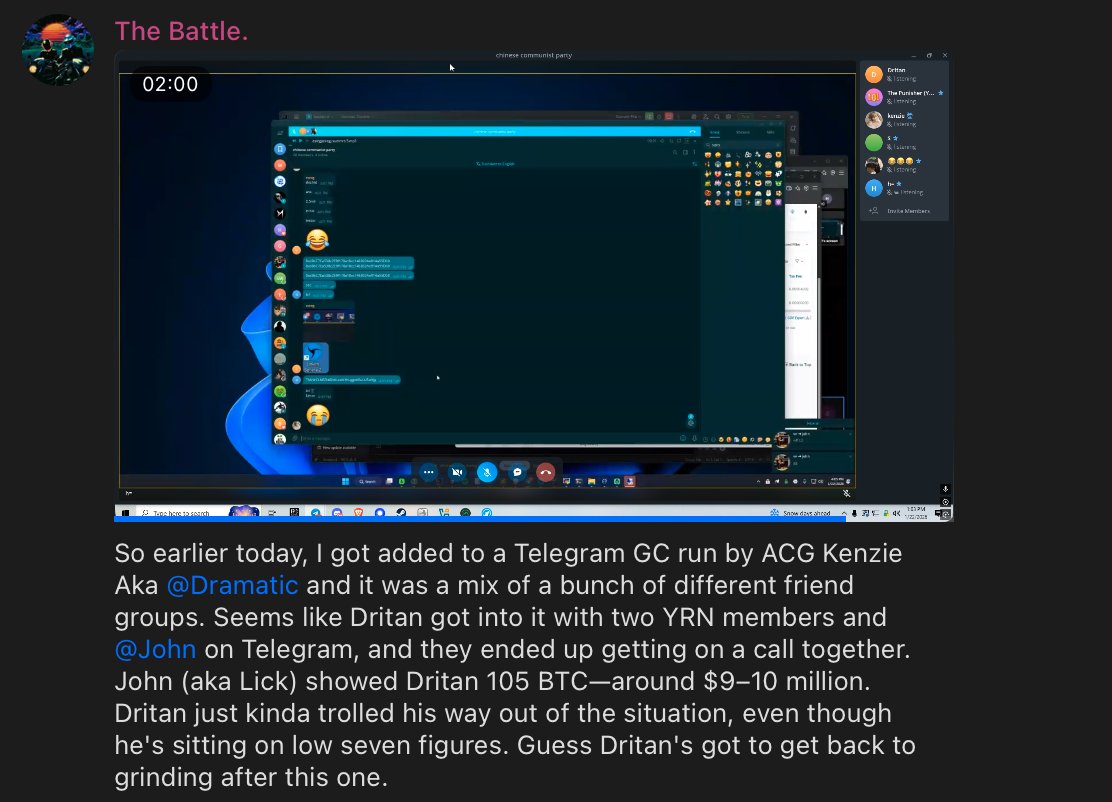
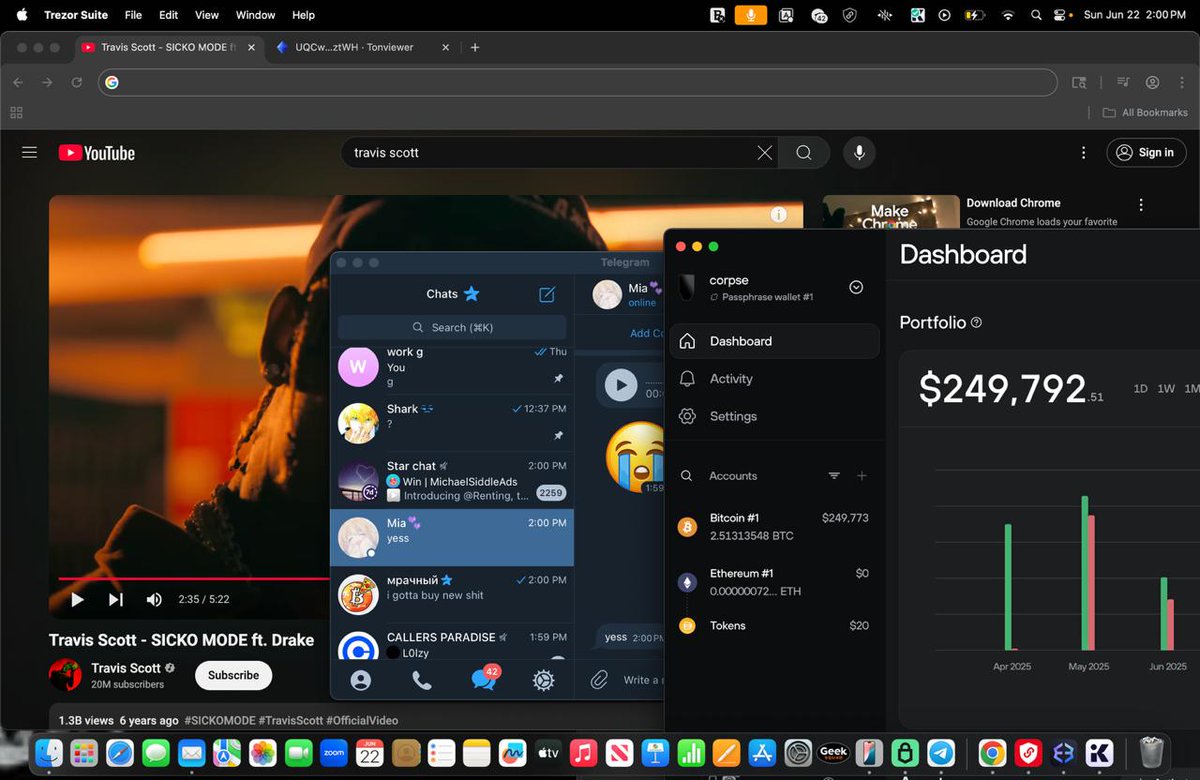
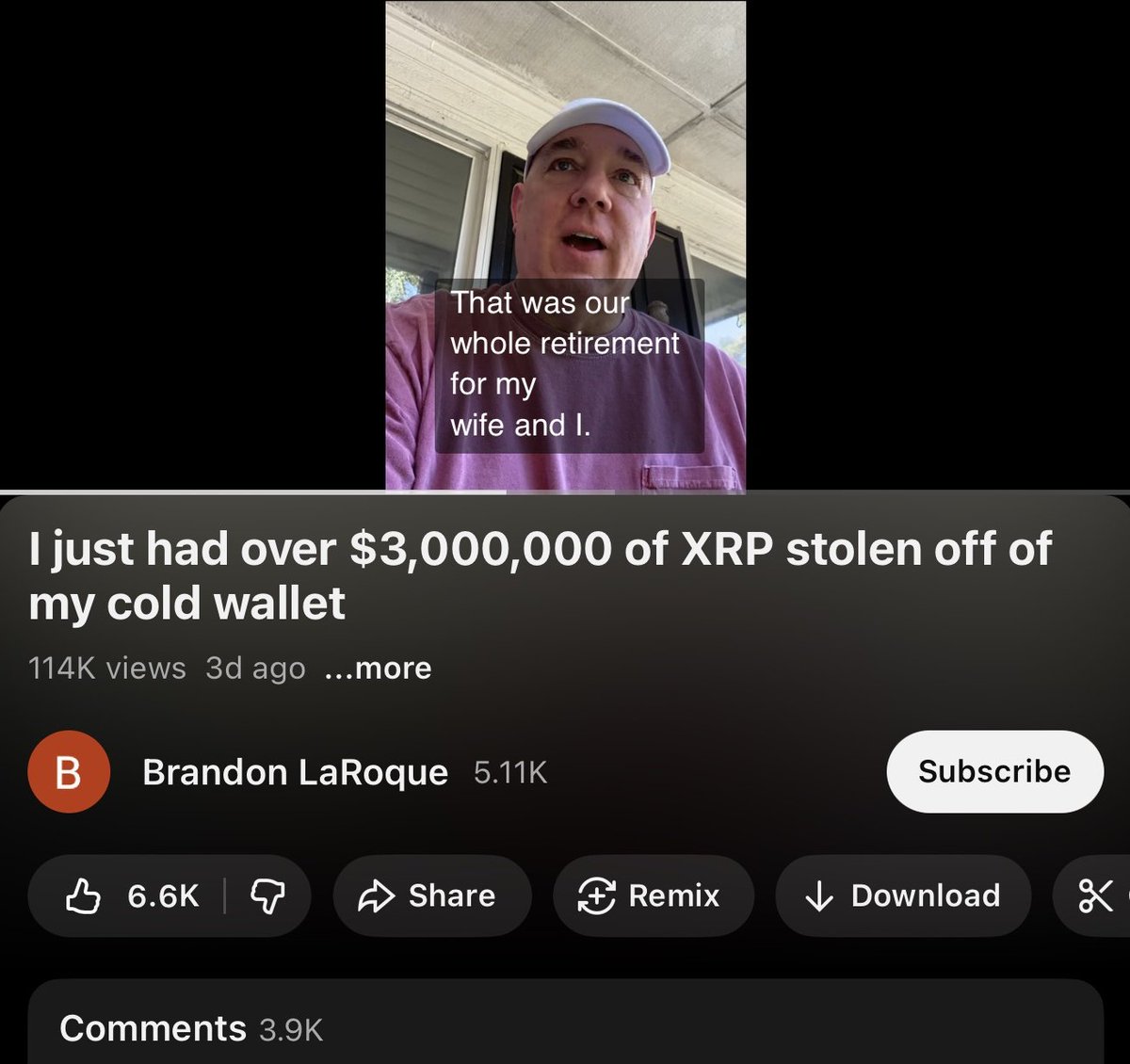
1/ It’s $TIME we talk about the launch of Wonderland and take a deep dive into what went on.
This involves some of the most prominent names in DeFi so I expect it to come off as surprising to many.
However it needs to be addressed.
👇
This involves some of the most prominent names in DeFi so I expect it to come off as surprising to many.
However it needs to be addressed.
👇

2/ If you aren’t familiar $TIME is a fork of OHM’s contracts launched in the Avalanche Ecosystem founded by Daniele Siesta.
As per the Discord server here is how is launcher.
I however received a few anonymous tips recently that a stealth launch was not what happened.
As per the Discord server here is how is launcher.
I however received a few anonymous tips recently that a stealth launch was not what happened.

3/ So what was I informed of?
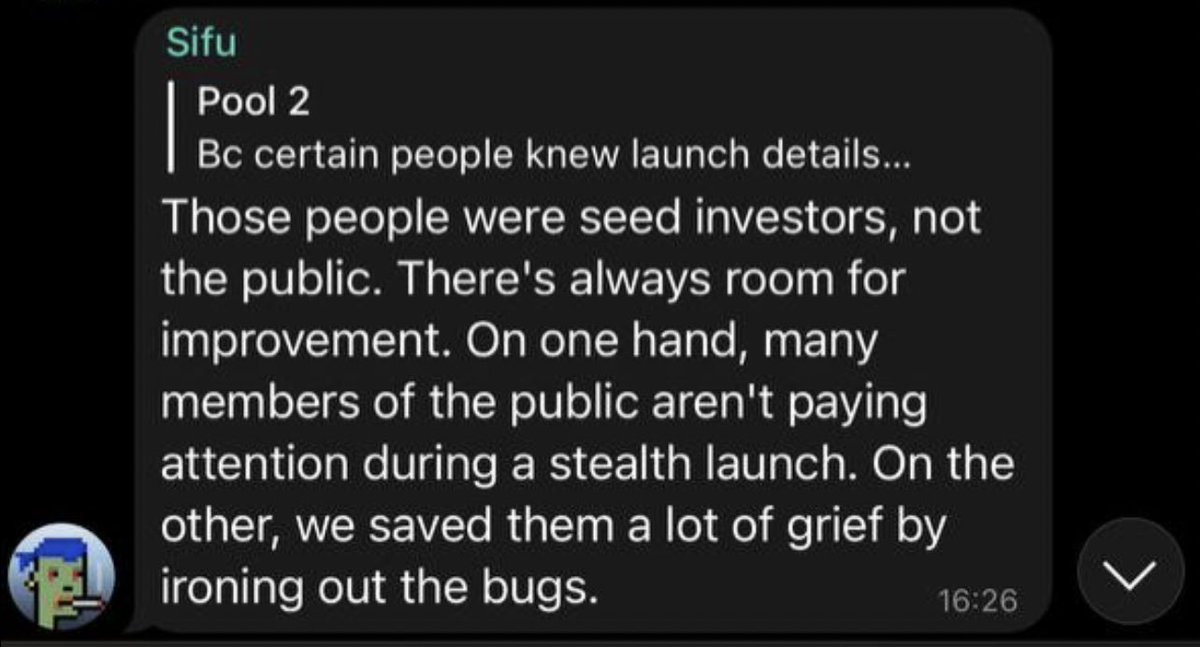
a) Although there wasn’t a presale there WAS a Seed LP made up of influencers & VC founders (Friends of Daniele)
b) Some of the people privileged to be insiders took it a step further to snipe the contract at launch
a) Although there wasn’t a presale there WAS a Seed LP made up of influencers & VC founders (Friends of Daniele)
b) Some of the people privileged to be insiders took it a step further to snipe the contract at launch
4/ This brings the questions of if they did anything inherently wrong.
I’d argue with a) there was nothing wrong with the Seed LP bc it was needed to begin the (3,3) behavioral pattern so the project isn’t dead at launch.
Not making this transparent however is the issue.
I’d argue with a) there was nothing wrong with the Seed LP bc it was needed to begin the (3,3) behavioral pattern so the project isn’t dead at launch.
Not making this transparent however is the issue.
5/ With b) I don’t think there’s much discussion needed. Sniping the contract after being a part of the core group isn’t a good look.
This is how the largest holders of $TIME & $MIM (Staked TIME) came to be.
This is how the largest holders of $TIME & $MIM (Staked TIME) came to be.
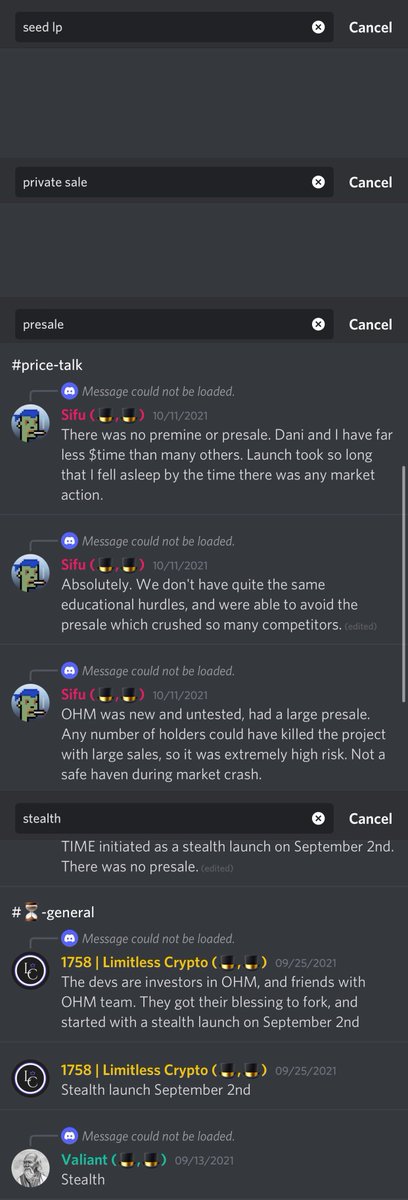
6/ You might be asking was used of insiders for the Seed LP known?
Well to verify this I went to the Discord & Telegram searching key phrases like (Seed LP, presale, private sale, stealth)
Nothing was disclosed about insiders/ DeFi friends funding the launch.

Well to verify this I went to the Discord & Telegram searching key phrases like (Seed LP, presale, private sale, stealth)
Nothing was disclosed about insiders/ DeFi friends funding the launch.

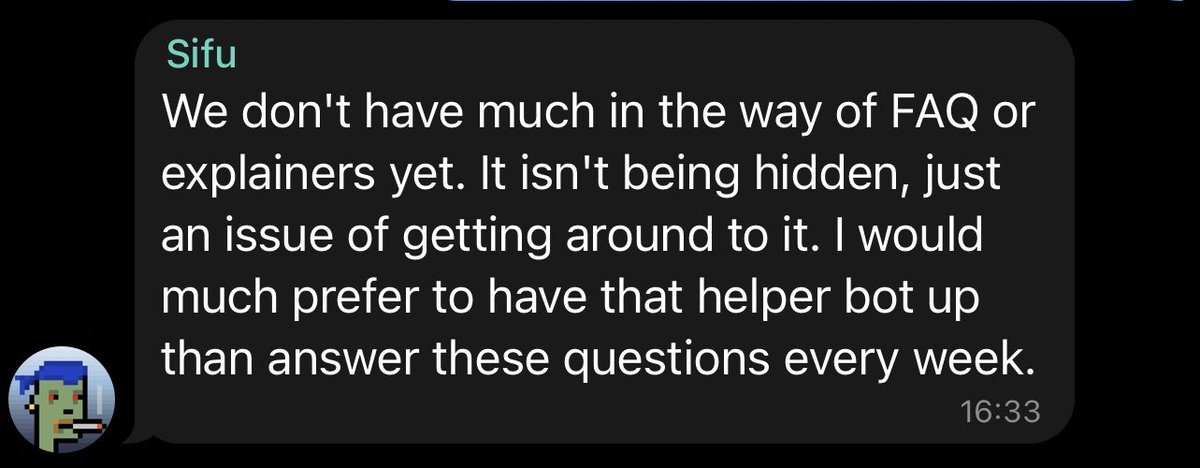
7/ You might also ask how I verified all of this?
Well after the tip I reached out a few alleged members of the core group who verified it
A core group member (CryptoMessiah) invited me to a chat with the Time Dev Sifu. They denied any wrongdoing.
See our chat below.
Well after the tip I reached out a few alleged members of the core group who verified it
A core group member (CryptoMessiah) invited me to a chat with the Time Dev Sifu. They denied any wrongdoing.
See our chat below.
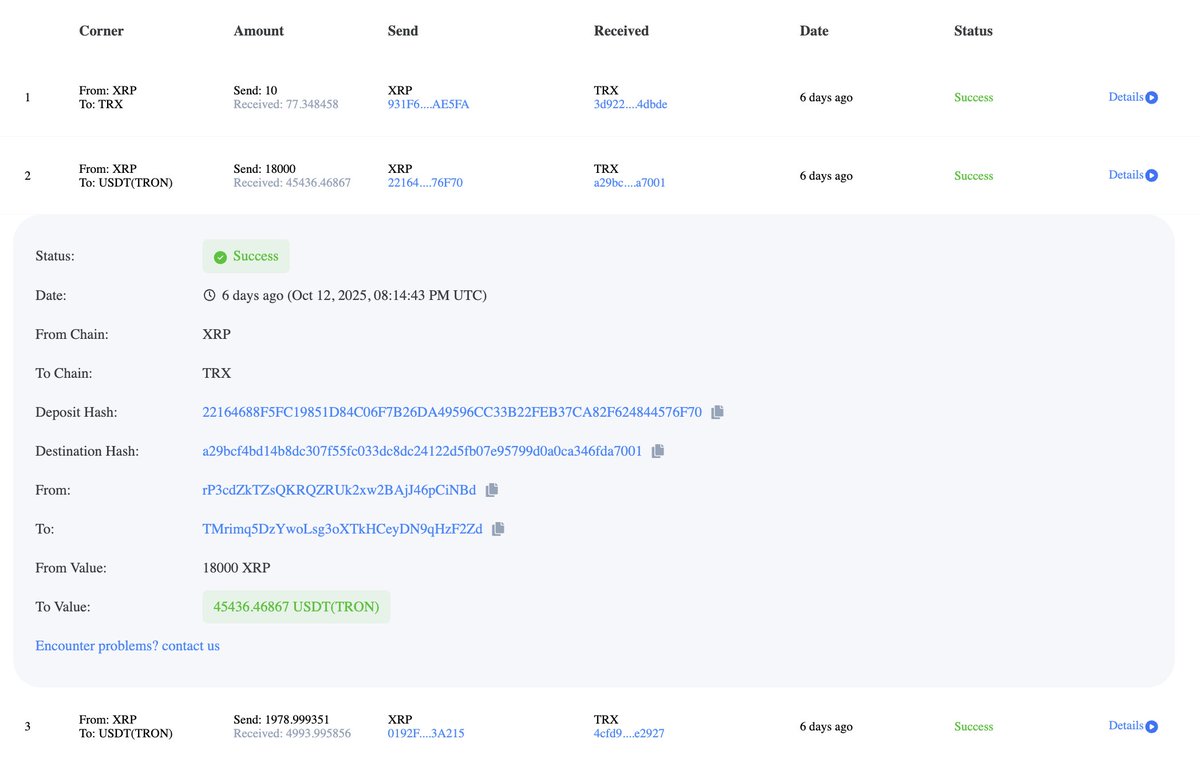
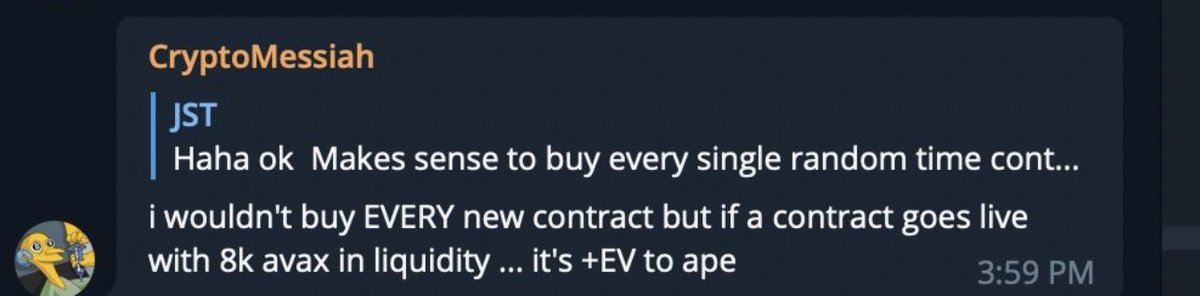
8/ As you can see from the video above they did know the exact time of the $time launch.
Here is Messi sniping at launch (one of the first buys) + in the screenshots below admitting to it.
This is worth roughly $14.7m at current prices.
avascan.info/blockchain/c/t…


Here is Messi sniping at launch (one of the first buys) + in the screenshots below admitting to it.
This is worth roughly $14.7m at current prices.
avascan.info/blockchain/c/t…



9/ It’s interesting how Sifu said it was best for the community and how they saved them “a lot of grief” to have a secret group of seed investors while at the same time trashing ones on Twitter.
At least a presale would have benefited a wider range of community members.

At least a presale would have benefited a wider range of community members.

10/ And in this portion of our convo they talk about how it was known but yet it was a straight up lie.
As you can see from a few tweets above there was nothing in the Discord or Telegram detailing it.
It’s not hard to add a few words…
As you can see from a few tweets above there was nothing in the Discord or Telegram detailing it.
It’s not hard to add a few words…
11/ This also brings the question of which other members of the core group besides Messi sniped the launch and abused their inside knowledge.
While I praise Daniele for everything he has built (one of the top shippers) transparency was not the case here.
While I praise Daniele for everything he has built (one of the top shippers) transparency was not the case here.
12/ It’s tweets like this that really annoy anyone who knows what actually happened at launch.
A few of the core members who were a part of the seed LP are even VCs…



A few of the core members who were a part of the seed LP are even VCs…




13/ Messi has became quite insufferable from $TIME when in fact he benefited from sniping & being a part of the core group
They themselves said they knew the exact launch time.



They themselves said they knew the exact launch time.



14/ It’s time you wake up and realize these people are not your friends no matter what they say.
Solution:
No you should not go about dumping your $TIME. I trust Dani to keep building exciting things. Just going forward he should be more transparent about the launch.
Solution:
No you should not go about dumping your $TIME. I trust Dani to keep building exciting things. Just going forward he should be more transparent about the launch.
15/ TLDR: I do not blame people who were a part of the core group of the $TIME but this should have been stated.
Anyone who sniped a significant portion of the supply as a result of the insider knowledge is at fault.
Hopefully more information comes w/ others who sniped
Anyone who sniped a significant portion of the supply as a result of the insider knowledge is at fault.
Hopefully more information comes w/ others who sniped
$MEMO is staked time small typo .
• • •
Missing some Tweet in this thread? You can try to
force a refresh