[thread 🧵] Kerberos delegations. This meta-thread gathers three sub-threads, one for each delegation type. I’ll talk about Unconstrained, Constrained, Resource-Based Constrained (RBCD), S4U2self, S4U2proxy and abuse scenarios.
Kerberos delegations is a set of features included in the Kerberos authentication protocol. It allows services to access other services on behalf of domain users.
3 types of delegations exist
- Unconstrained: service can access any other service on behalf of any user
- Constrained: service can access a set of services on bhalf of any user
- Resource-Based Constrained (RBCD): service grants that « impersonating access » to a set of services
- Unconstrained: service can access any other service on behalf of any user
- Constrained: service can access a set of services on bhalf of any user
- Resource-Based Constrained (RBCD): service grants that « impersonating access » to a set of services

Nota bene: « any user » is not 100% true. There are limitations that I will cover later on. But TL;DR: some users are secured and cannot be delegated. Services cannot act on their behalf.
What purpose do delegations serve? They allow services to access remote resources and limit what the service account has access to. This is nice! Users have specific access that some service accounts configured for delegation can temporarily profit from by acting on their behalf 
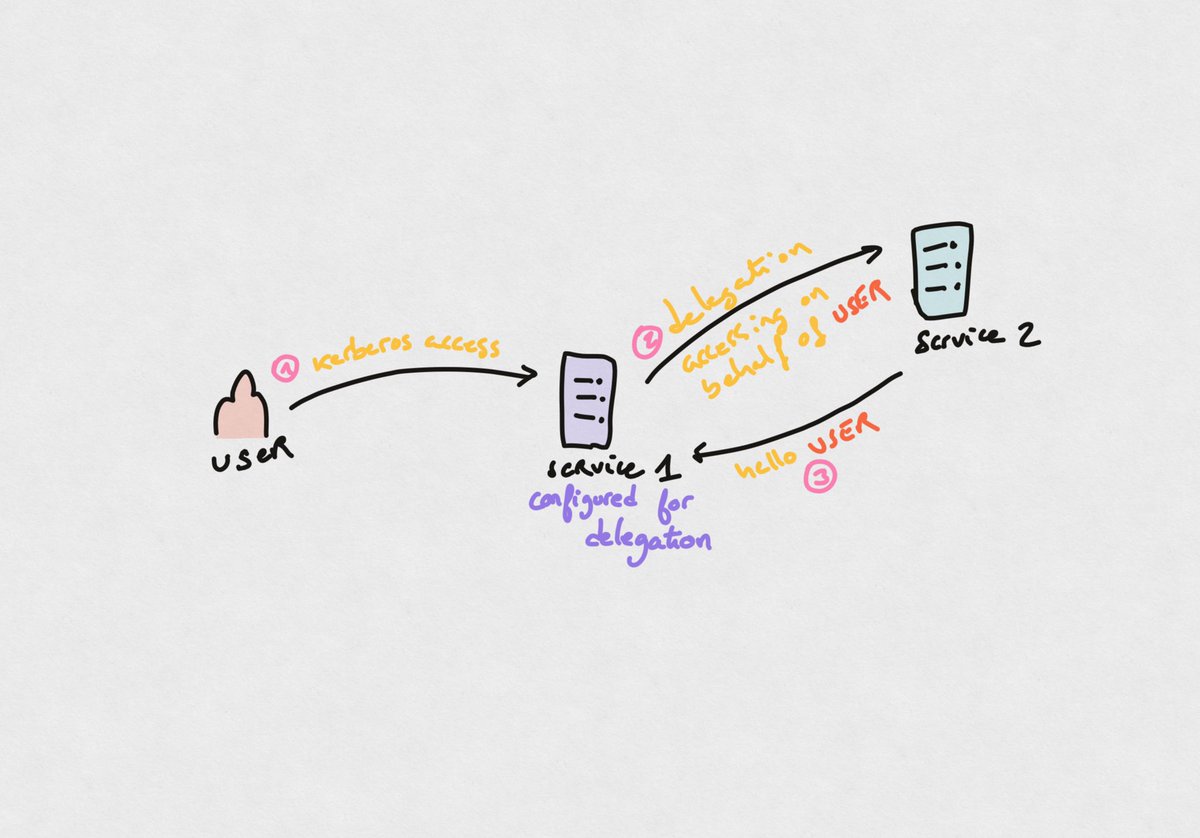
Now, let’s dive in the different types of delegations and how to abuse those shall we?
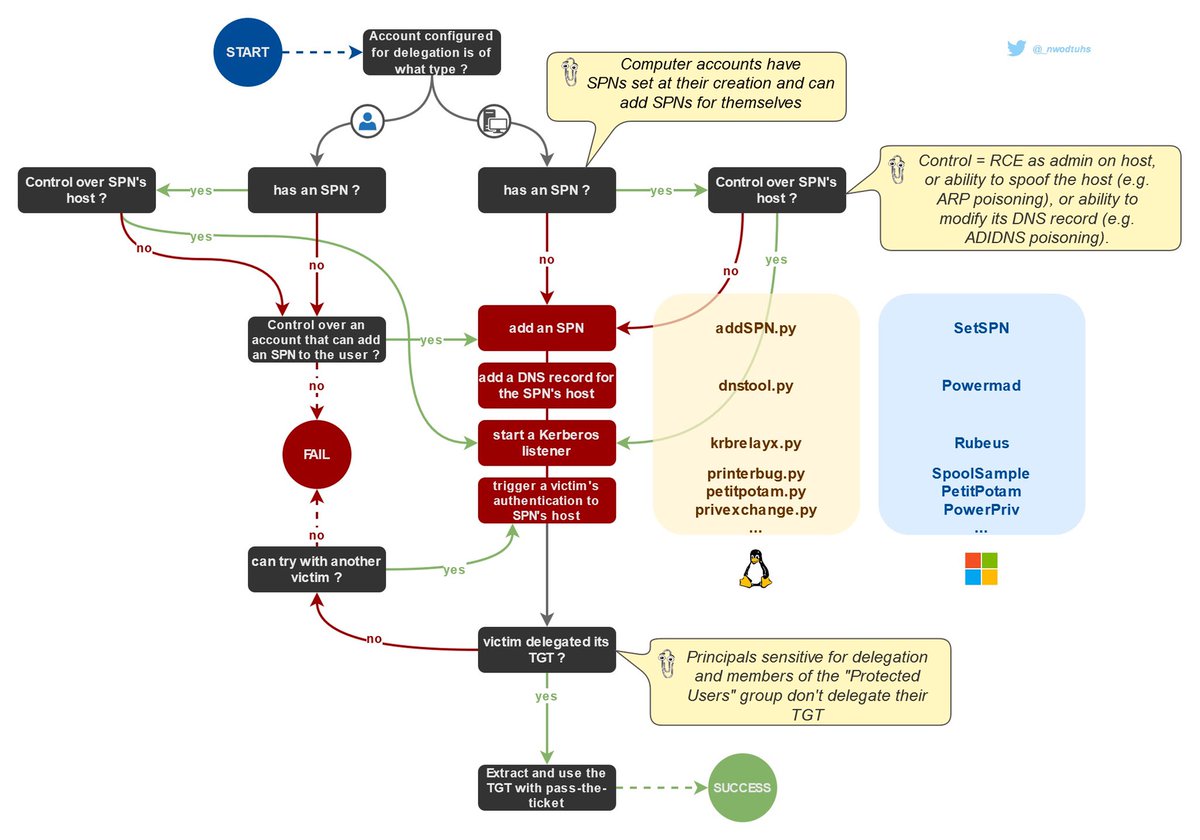
Kerberos Unconstrained Delegations 
https://twitter.com/_nwodtuhs/status/1454049485080907776?s=21
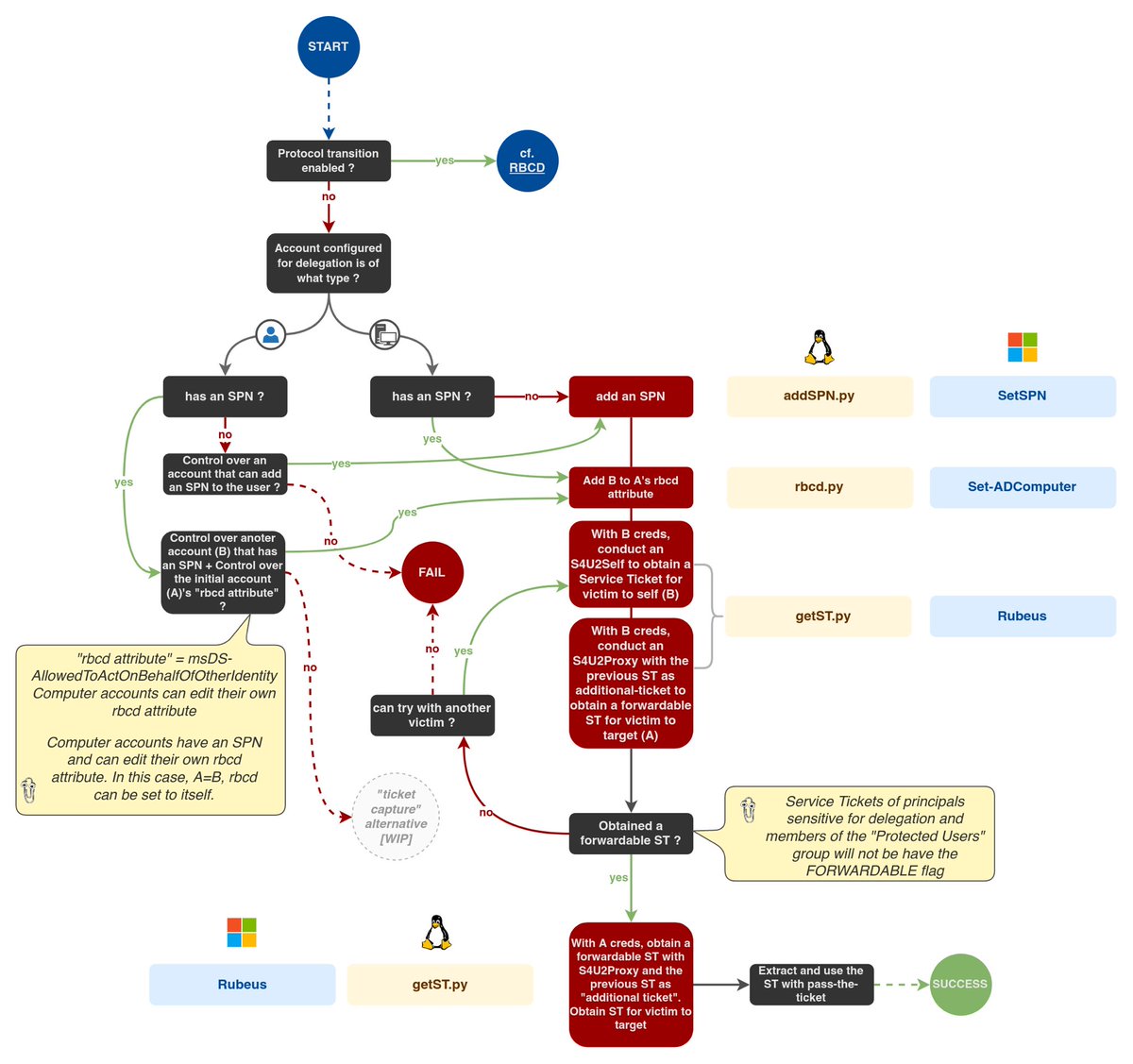
Kerberos Constrained Delegations 
https://twitter.com/_nwodtuhs/status/1454049170243952640?s=21
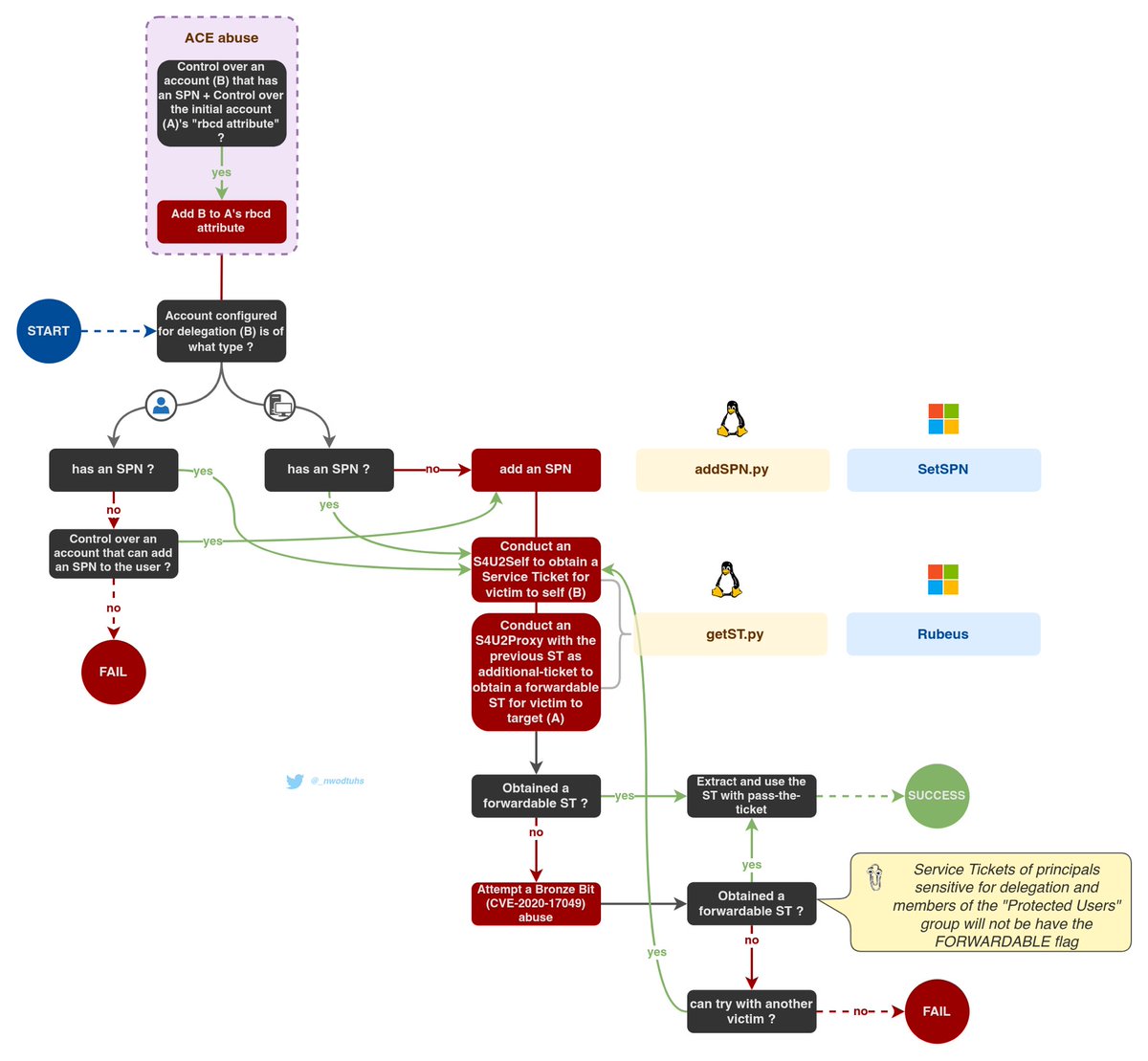
Kerberos Resource-Based Constrained Delegations 
https://twitter.com/_nwodtuhs/status/1454048919579676676?s=21
• • •
Missing some Tweet in this thread? You can try to
force a refresh






