
How to get URL link on X (Twitter) App




 ** CVE-2021-42278 - Name impersonation
** CVE-2021-42278 - Name impersonation
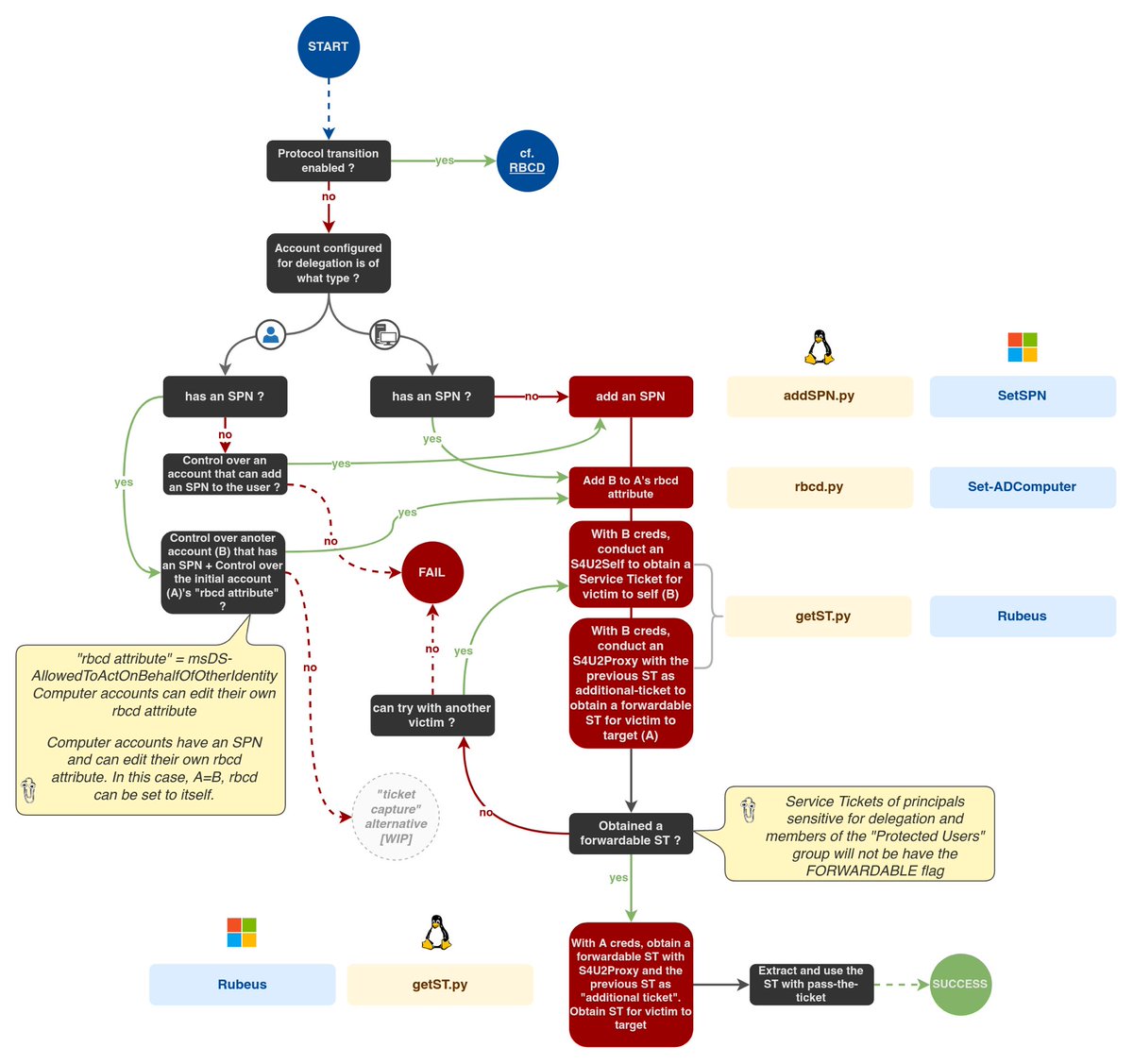
 Similarly to Unconstrained Delegations, service account configured for KCD can act on behalf of other principals on other services. The difference is that with KUD, it’s possible to delegate to any service whereas with KCD it’s possible to delegate to a specific set of services
Similarly to Unconstrained Delegations, service account configured for KCD can act on behalf of other principals on other services. The difference is that with KUD, it’s possible to delegate to any service whereas with KCD it’s possible to delegate to a specific set of services
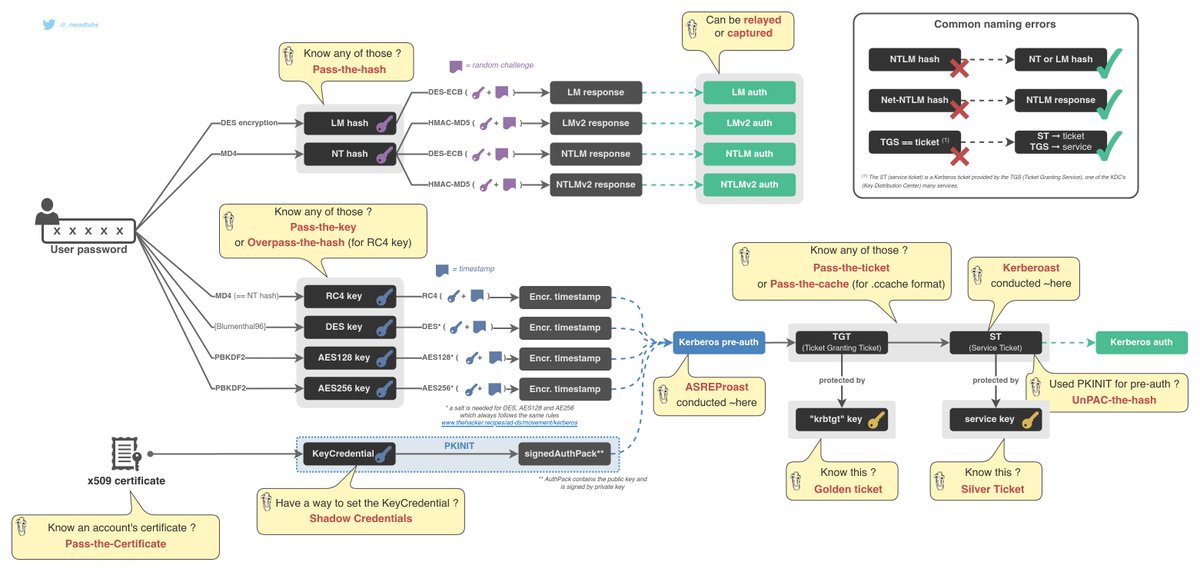
 [Kerberos 101 ⬇️]
[Kerberos 101 ⬇️]

https://twitter.com/topotam77/status/1416833996923809793PetitPotam’s MS-EFSR abuse is the equivalent (even better) of the PrinterBug’s MS-RPRN abuse that’s been here for a while now
