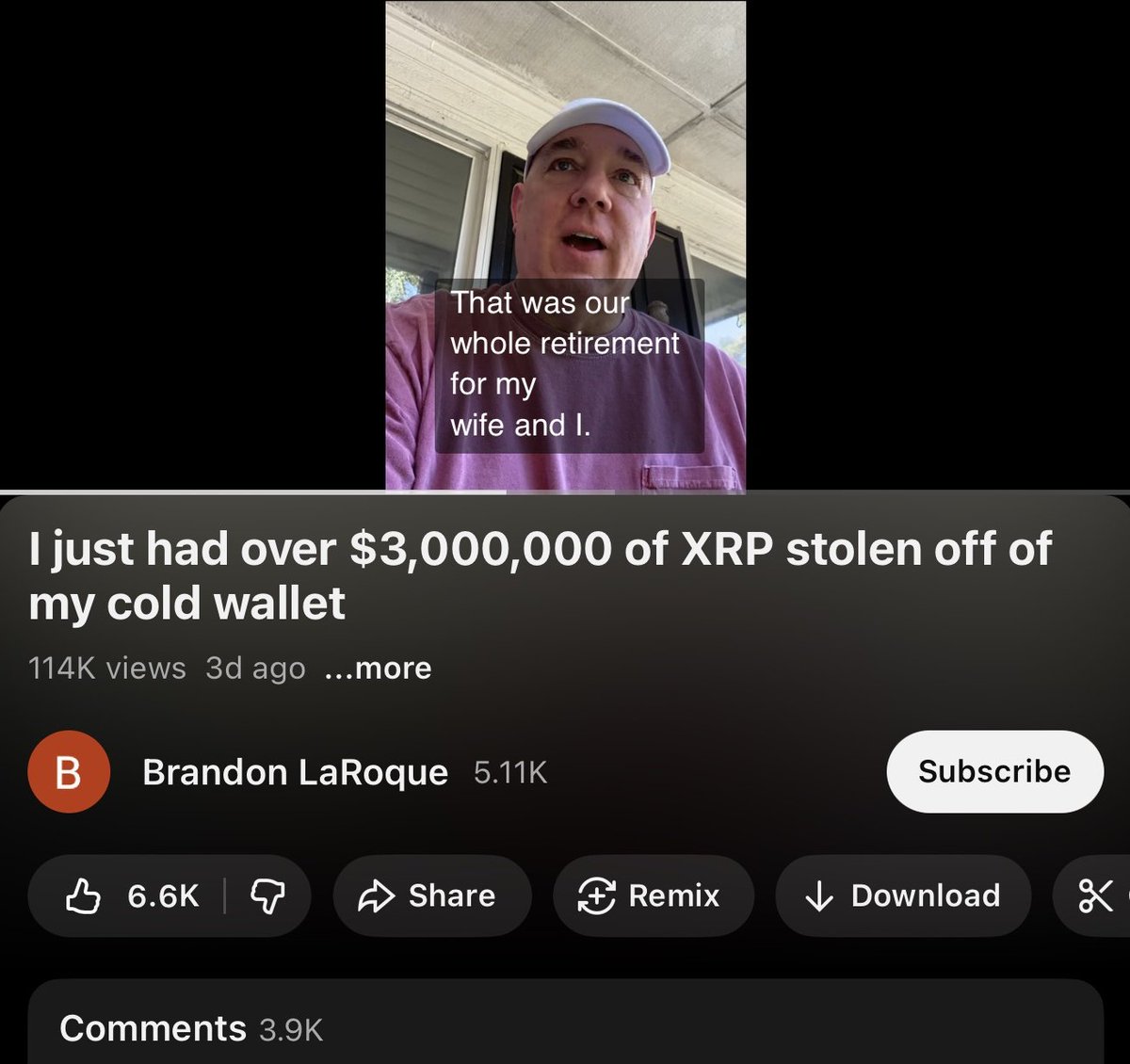
1/ Let’s discuss @moon_guurl and how she rugged $islainu (a meme coin).
You may be asking why her? Well this tweet last night peaked interest amongst people on CT. I figured why not reach out to the team to see what happened.
Time for a deep dive
👇
You may be asking why her? Well this tweet last night peaked interest amongst people on CT. I figured why not reach out to the team to see what happened.
Time for a deep dive
👇

2/ Luckily the team responded quickly providing the entire chat history.
Why way this necessary? Rea allegedly dumped 6 figures of a lowcap right after striking a deal. This destroyed the coin
Why way this necessary? Rea allegedly dumped 6 figures of a lowcap right after striking a deal. This destroyed the coin

3/ Here is the deal that REA & the team agreed to.
1% of the supply (Ik lol) for a promo Tweet about the project.
Initially the team pushed for vesting w/ presale access but she repeatedly declined and said she wouldn’t sell large amounts

1% of the supply (Ik lol) for a promo Tweet about the project.
Initially the team pushed for vesting w/ presale access but she repeatedly declined and said she wouldn’t sell large amounts


4/ Here was the promo tweet she did. Notice there was ZERO disclosure and instead pretended to have genuine interest 



5/ Everything seemed to be going well with the deal other than the undisclosed shill…
After agreeing to the 1% of the supply she was told to not sell a bunch at once since it wasn’t vested
Also clearly trying to hide her address in the second screenshot. Why so scared?

After agreeing to the 1% of the supply she was told to not sell a bunch at once since it wasn’t vested
Also clearly trying to hide her address in the second screenshot. Why so scared?


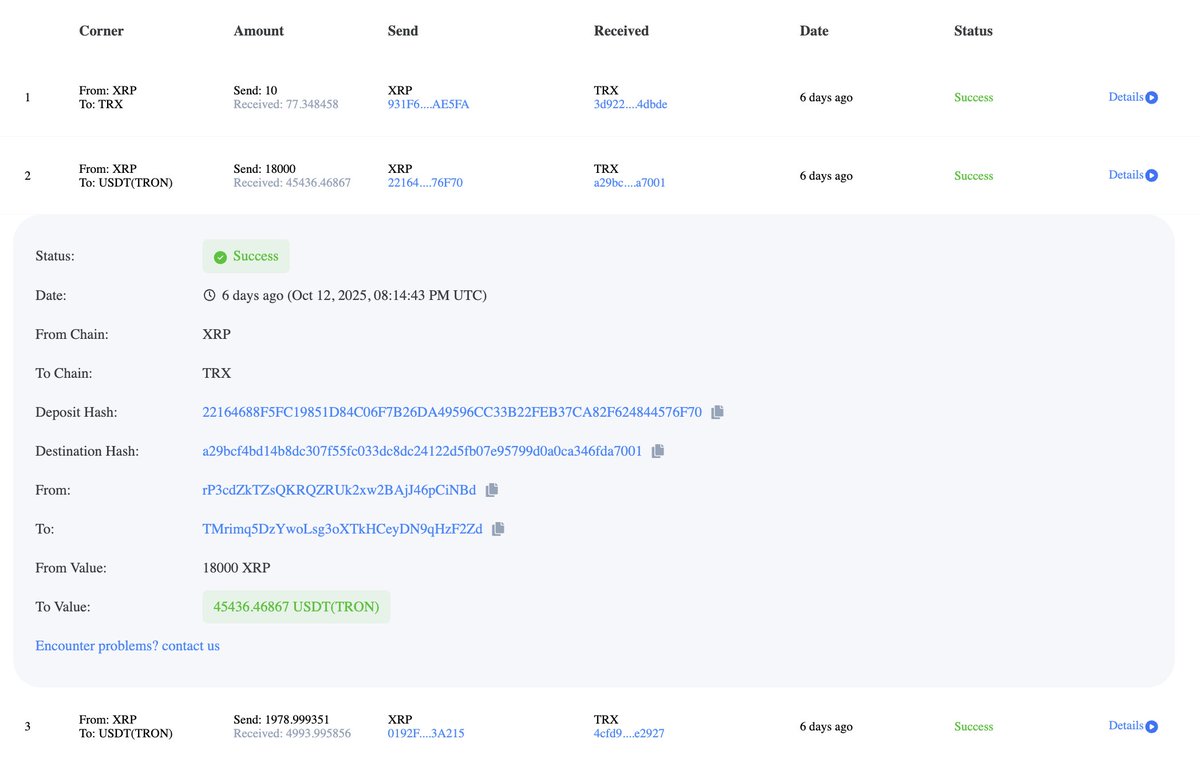
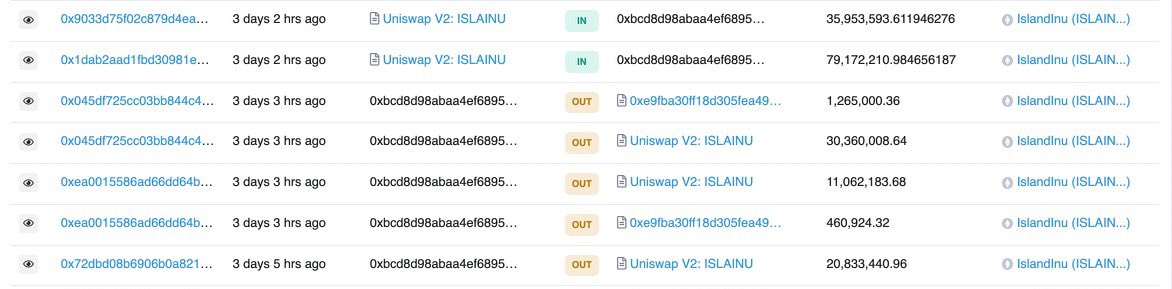
6/ Rea started selling small bits at a time immediately after launch. See the address below.
Attached are additional screenshots that proves it her.
etherscan.io/token/0xe9fba3…

Attached are additional screenshots that proves it her.
etherscan.io/token/0xe9fba3…


7/ Soon after a large sell happens and a team member preemptively messages Rea since she holds a 1% of the supply. They immediately apologize however.
They ask her to buy back the ones she’s sold but eventually does.
This is where things start to go downhill…


They ask her to buy back the ones she’s sold but eventually does.
This is where things start to go downhill…


8/ Now the project is up a bunch and the team offers to buy her out for $28k since 1% is now worth a small house (still a lowcap)
The rationale is bc her bag is causing FUD that a team member is selling
Soon after Rea acts distant citing mental health + gender discrimination



The rationale is bc her bag is causing FUD that a team member is selling
Soon after Rea acts distant citing mental health + gender discrimination
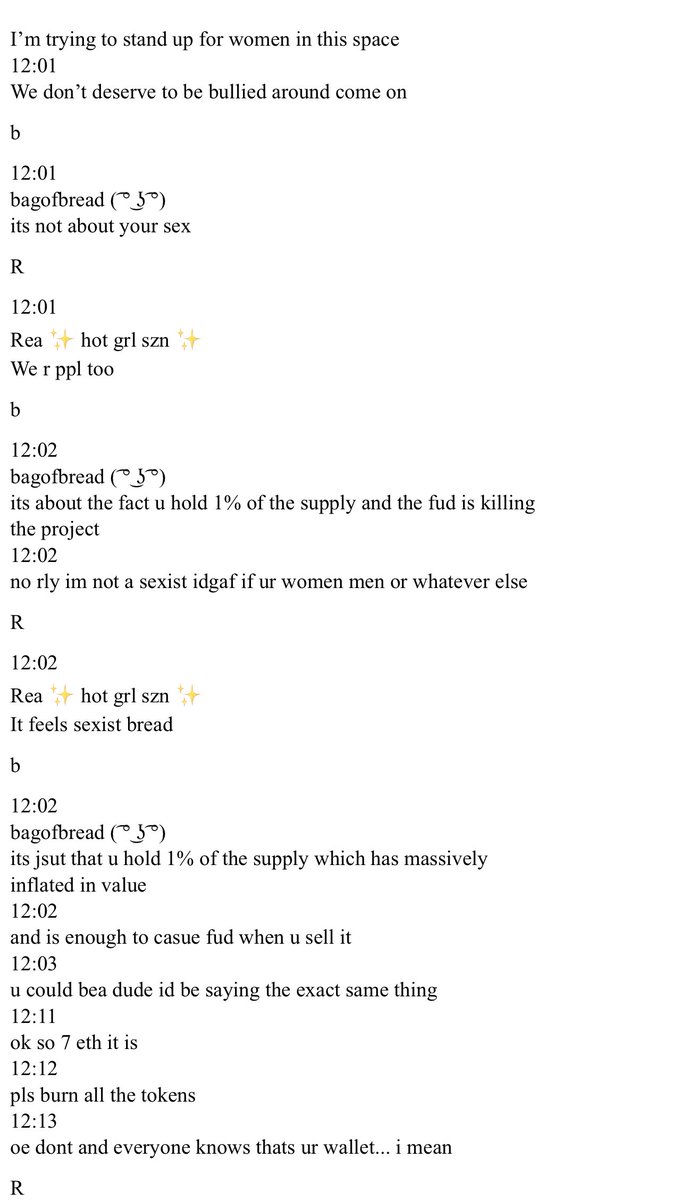
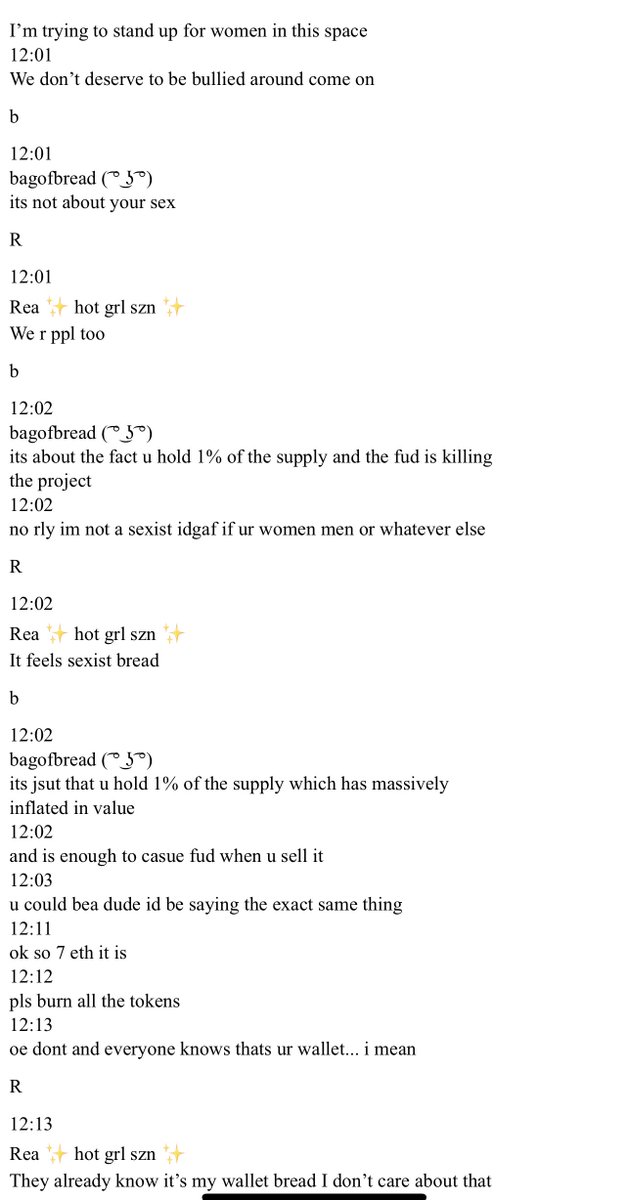


9/ The excuses continue and she then sends the tokens to her “friend” who immediately dumps the token (22.8 eth worth) rugging the project.
etherscan.io/tx/0x8e1fa8e2c…


etherscan.io/tx/0x8e1fa8e2c…



10/ Anyone who spends a few seconds in the space knows you can’t execute large sells like that on a lowcap. Rea avoided vesting for a reason
This plus the hidden shill just is sketchy behavior
Apparently she’s in a deal w/ 3AC but still knowingly shilled a lowcap meme coin?
This plus the hidden shill just is sketchy behavior
Apparently she’s in a deal w/ 3AC but still knowingly shilled a lowcap meme coin?

11/ I would be very careful going forward dealing with someone who has acted like this.
It is not someone you want to work with…
Do you really need an “InFlUeNcEr” that bad?
It is not someone you want to work with…
Do you really need an “InFlUeNcEr” that bad?
• • •
Missing some Tweet in this thread? You can try to
force a refresh