
This question's wording belies immense technical difference in what they want for security education, and what they are literally asking.
They are asking for the highest-level privately owned domain. Determining this is actually really complicated to authoritatively answer. 🧵👇
They are asking for the highest-level privately owned domain. Determining this is actually really complicated to authoritatively answer. 🧵👇
https://twitter.com/tedgarb/status/1461461358826999810
The domain name system is read right-to left.
three.two.one(.<start here>)
To make security decisions, you want to determine when a potentially untrustworthy individual entity starts to control the string.
google.example.com starts at example. Easy.
BUT...🚨
three.two.one(.<start here>)
To make security decisions, you want to determine when a potentially untrustworthy individual entity starts to control the string.
google.example.com starts at example. Easy.
BUT...🚨
Just saying look at the second-level domain doesn't work because
1.) The top-level-domain could be privately owned
2.) The second-level domain may still be owned by countries, infrastructure services firms, private registrars.
For example, here's the -EFFECTIVE- TLDs for India.
1.) The top-level-domain could be privately owned
2.) The second-level domain may still be owned by countries, infrastructure services firms, private registrars.
For example, here's the -EFFECTIVE- TLDs for India.
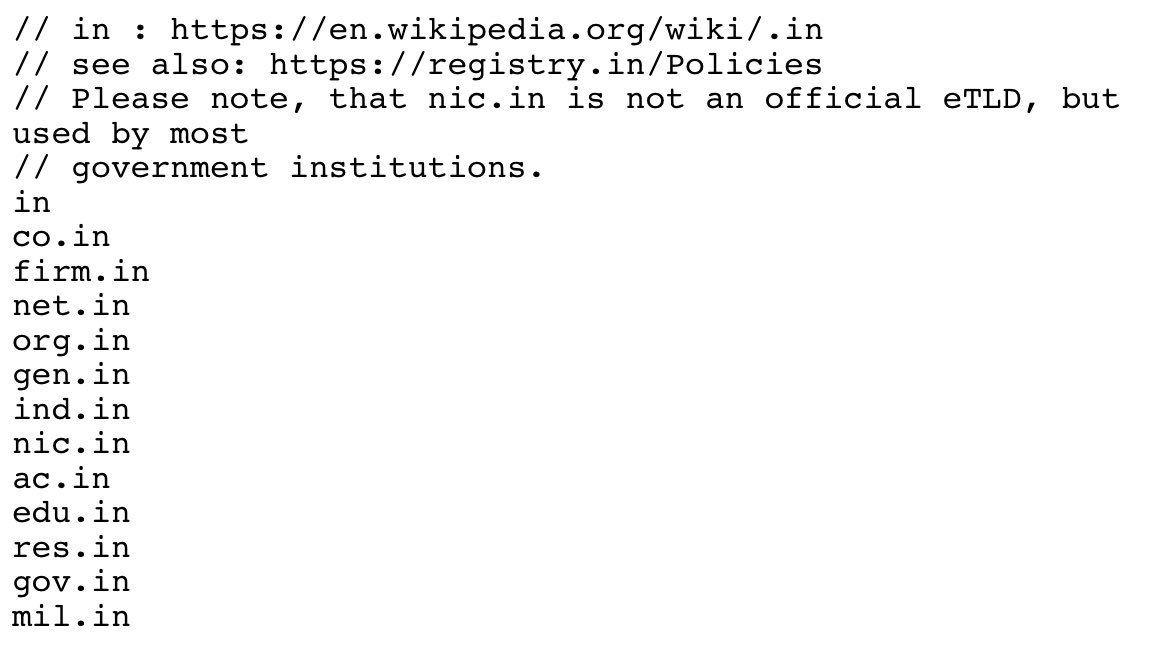
There's also infrastructure. Here's an incomplete list of domains that any Microsoft customer can register privately and put anything they want on. It's Microsoft, but NOT Microsoft.
Stuff like "…lDownloadServer.blob.core.windows.net" could be anybody despite saying Windows. Just terrible.
Stuff like "…lDownloadServer.blob.core.windows.net" could be anybody despite saying Windows. Just terrible.

For this reason, the concept of the Public Suffix List was developed, to inventory WHERE PRIVATE CONTROL OF DOMAIN CONTENT ACTUALLY STARTS in a multi-part domain name.
wiki.mozilla.org/Public_Suffix_…
Actual list: IT'S REAL FRIGGEN LONG.
publicsuffix.org/list/public_su…
Unfortunately...
wiki.mozilla.org/Public_Suffix_…
Actual list: IT'S REAL FRIGGEN LONG.
publicsuffix.org/list/public_su…
Unfortunately...
Even domain names completely controlled by trustworthy companies can still host malicious content.
A download from storage.googleapis.com is often just malware.
These design decisions were some of the most disastrous abdications of internet ecosystem stewardship in modern times
A download from storage.googleapis.com is often just malware.
These design decisions were some of the most disastrous abdications of internet ecosystem stewardship in modern times
I could keep talking for quite a bit longer about all the extensive technical knowledge you need to determine what to trust before you even click something. The correct answer is turn your router off and go outside.
Anti-toxicity notice: You'll notice I never upbraid the writer of the question, and instead comment on the technical distance between what users are taught as simple enough to be vaguely effective, and the true complexity.
Frankly, I have no idea how'd I approach teaching this.
Frankly, I have no idea how'd I approach teaching this.
Just what I tweeted takes multiple lectures to fully convey, to a beginning SOC analyst, trying to competently address web-based threats. We didn't even get into what comes AFTER the domain in common patterns on compromised websites used for malware delivery. It expounds forever.
https://twitter.com/mrd0x/status/1459210707321380874
• • •
Missing some Tweet in this thread? You can try to
force a refresh







