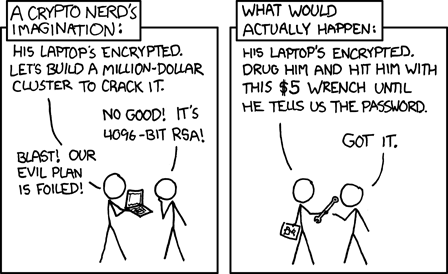
1/ On How To Secure Your NFTs
Where are your NFTs out in the metaverse?
How do you store them?
How do you keep people from stealing them?!
How do you pass down your Grails to your grandkids?
Let’s find out!
Where are your NFTs out in the metaverse?
How do you store them?
How do you keep people from stealing them?!
How do you pass down your Grails to your grandkids?
Let’s find out!
2/ There is a lot of confusion about wallets and NFT storage.
This thread is going to try to cover everything from basics for our new NFTs frens to some advanced topics for 🐳s
Make sure you click “read more” after tweet #30 because we are going to #30 and beyond!
This thread is going to try to cover everything from basics for our new NFTs frens to some advanced topics for 🐳s
Make sure you click “read more” after tweet #30 because we are going to #30 and beyond!
3/ Disclaimers:
Security is hard, you may make mistakes, I may make mistakes, new attack vectors might emerge
I discuss specific solutions. They might have bugs, there might be other better solutions
So this is my best view, but I can’t take responsibility for your NFTs
Security is hard, you may make mistakes, I may make mistakes, new attack vectors might emerge
I discuss specific solutions. They might have bugs, there might be other better solutions
So this is my best view, but I can’t take responsibility for your NFTs
4/ The first part of this thread is not going to discuss any particular wallet, but the general concepts on how ETH stores and secures tokens.
For some, these will be trivial and obvious.
For others, confusing and you will have to re-read.
For some, these will be trivial and obvious.
For others, confusing and you will have to re-read.
5/ You need to understand these concepts first.
Otherwise, you won’t ever really understand what you are doing with your wallet.
I reference ETH in this thread for simplicity, but the same general concepts apply to many other chains
Otherwise, you won’t ever really understand what you are doing with your wallet.
I reference ETH in this thread for simplicity, but the same general concepts apply to many other chains
6/ OK, LFG
Let’s start with “where are your NFTs?”
No, actually let’s start with “where your NFTs are not”:
❎ Metamask
❎ Your computer
❎ Your Trezor
❎ Your Ledger
Let’s start with “where are your NFTs?”
No, actually let’s start with “where your NFTs are not”:
❎ Metamask
❎ Your computer
❎ Your Trezor
❎ Your Ledger
7/ Your NFT is a token.
That token is on the Ethereum blockchain, a copy of which is being held by the 3,000 or so Ethereum nodes that are running globally.
etherscan.io/nodetracker
That token is on the Ethereum blockchain, a copy of which is being held by the 3,000 or so Ethereum nodes that are running globally.
etherscan.io/nodetracker
8/ What is great about this is the level of backup and redundancy you have
It is nice to have a backup of your files. Right now, for your ETH tokens, you have about 3,000 backups distributed around the world
And anyone, including you, could add another backup to the system
It is nice to have a backup of your files. Right now, for your ETH tokens, you have about 3,000 backups distributed around the world
And anyone, including you, could add another backup to the system
9/ So, to say it another way
When you sell an NFT to someone else, nothing is moving from your computer/trezor to their computer/trezor.
All that is happening is that the database that is the ETH blockchain is changing the entry for which address the NFT is owned by.
When you sell an NFT to someone else, nothing is moving from your computer/trezor to their computer/trezor.
All that is happening is that the database that is the ETH blockchain is changing the entry for which address the NFT is owned by.
10/ What about the JPG? Where is that?
Your NFT has a URI field (like a URL) that points to where the JPG is.
The best practice is that it is on IPFS or Arweave which is “decentralized storage”.
Alternatively, it might be on someone’s server (“centralized”).
Your NFT has a URI field (like a URL) that points to where the JPG is.
The best practice is that it is on IPFS or Arweave which is “decentralized storage”.
Alternatively, it might be on someone’s server (“centralized”).
11/ But the cloud (centralized or decentralized) is still just a server somewhere.
The main difference between IPFS and AWS is that anyone (including you) can join your computer to IPFS and decide to also store any particular IPFS object (including your JPG)
The main difference between IPFS and AWS is that anyone (including you) can join your computer to IPFS and decide to also store any particular IPFS object (including your JPG)
12/ Some art (usually generative art) is completely on-chain
This means that the instructions to draw the art is contained in the token itself.
This means the art is stored on the ETH blockchain, right with the token.
This means that the instructions to draw the art is contained in the token itself.
This means the art is stored on the ETH blockchain, right with the token.
13/ So let's go to the next step and discuss public keys and private keys
A public key is an ETH “address”
0x98b7AAeb419394b13D46C9508d79b335FF6D98A0
(This is an address used for small 6529 acquisitions. Mostly spam there now)
A public key is an ETH “address”
0x98b7AAeb419394b13D46C9508d79b335FF6D98A0
(This is an address used for small 6529 acquisitions. Mostly spam there now)
14/ The best analogy for a public key is an email address.
You can safely share it publicly and people can send things to it.
Those things are most typically:
- ETH
- ERC20 Tokens (fungible tokens, like UNI or SUSHI)
- ERC721 or ERC1155 tokens (non-fungible tokens aka NFTs)
You can safely share it publicly and people can send things to it.
Those things are most typically:
- ETH
- ERC20 Tokens (fungible tokens, like UNI or SUSHI)
- ERC721 or ERC1155 tokens (non-fungible tokens aka NFTs)
15/ Like email, you have no control over what people send to your public address so you receive spam.
My addresses receive a lot of spam NFTs from people who want to get my attention or want to trick others into thinking that I bought from those collections.
My addresses receive a lot of spam NFTs from people who want to get my attention or want to trick others into thinking that I bought from those collections.
16/ Unlike email, your ‘inbox’ is also public
Everyone can see every transaction in every ETH address and what assets are currently stored there
You can go here & see what is at this address: etherscan.io/address/0x98b7…
Mostly some small NFT transactions & some spam right now
Everyone can see every transaction in every ETH address and what assets are currently stored there
You can go here & see what is at this address: etherscan.io/address/0x98b7…
Mostly some small NFT transactions & some spam right now
17/ So your public key is also NOT what you are storing and trying to keep safe.
What you are trying to keep safe is your PRIVATE KEY.
Your Private Key is your “password” for your public key/address.
What you are trying to keep safe is your PRIVATE KEY.
Your Private Key is your “password” for your public key/address.
18/ What the private key primarily allows is for you:
a) to move tokens out of your address
b) sign messages proving you have the private key for that address
a) to move tokens out of your address
b) sign messages proving you have the private key for that address
19/ Unlike your public key, you must never ever show your private key to anyone.
If someone has your private key, it is GAME OVER.
They can very quickly take every single asset – ETH, fungible tokens, NFTs – from your address.
It is the keys to the kingdom
If someone has your private key, it is GAME OVER.
They can very quickly take every single asset – ETH, fungible tokens, NFTs – from your address.
It is the keys to the kingdom
20/ Now we are starting to get closer to the main event.
A “wallet” is a piece of software that contains a set of private keys.
A private key controls a public key.
A “wallet” is a piece of software that contains a set of private keys.
A private key controls a public key.
21/ Every wallet, whether software or hardware, is just this.
A piece of software that holds a set of private keys that allow you to execute transactions on specific ETH addresses.
A piece of software that holds a set of private keys that allow you to execute transactions on specific ETH addresses.
22/ There are a couple of more concepts we need to introduce. The first is the seed phrase.
A seed phrase is a set of 12, 18, 24 (or more) words.
If your private key is your password, your seed phrase is your password recovery method.
A seed phrase is a set of 12, 18, 24 (or more) words.
If your private key is your password, your seed phrase is your password recovery method.
23/ If you lose your private keys, you can recreate them from your seed phrase.
As with your private key, never ever share your seed phrase.
Once someone has it, your wallet will be emptied
As with your private key, never ever share your seed phrase.
Once someone has it, your wallet will be emptied
24/ The last concept is the ‘passphrase’. The passphrase is an unusual concept with no good IRL analogy.
It is a series of characters/words that, when combined with your seed phrase, creates a wallet with a set of private keys
It is a series of characters/words that, when combined with your seed phrase, creates a wallet with a set of private keys
25/ In other words, if I created my wallet/private keys with:
seed phrase + “apple”
seed phrase + “nft”
seed phrase + “6529”
seed phrase + “seize the memes of production”
Each one would create a wallet with different private keys for different public keys (addresses)
seed phrase + “apple”
seed phrase + “nft”
seed phrase + “6529”
seed phrase + “seize the memes of production”
Each one would create a wallet with different private keys for different public keys (addresses)
26/ What is strange about passphrases is that there are no ‘wrong’ answers.
If you put the wrong passphrase, you don’t get some type of error message, you just get a different set of private keys that work fine, but don’t have your tokens in them
If you put the wrong passphrase, you don’t get some type of error message, you just get a different set of private keys that work fine, but don’t have your tokens in them
27/ Even stranger, if you don’t use a passphrase, you are still using a passphrase.
By default, the empty set passphrase of “” (no characters) is used
There is NO recovery system if you lose your passphrase
By default, the empty set passphrase of “” (no characters) is used
There is NO recovery system if you lose your passphrase
28/Summary:
Address/Public Key: Your email address (can be shared)
Private key: The password to your inbox (never share)
Wallet: Holds private keys
Seed phrase: Recovery system for private keys (never share)
Passphrase: Optional: extra password to create new wallets (never lose)
Address/Public Key: Your email address (can be shared)
Private key: The password to your inbox (never share)
Wallet: Holds private keys
Seed phrase: Recovery system for private keys (never share)
Passphrase: Optional: extra password to create new wallets (never lose)
29/ The whole discussion about wallets (software or hardware) and NFT security is a discussion about two topics:
a) security: how do you keep someone else from getting a hold of your private keys
b) resiliency: how do you ensure you do not lose control of your private keys
a) security: how do you keep someone else from getting a hold of your private keys
b) resiliency: how do you ensure you do not lose control of your private keys
30/ Security/resiliency are opposite goals.
Printing flyers with your private keys is very resilient but your NFTs will be gone.
You can easily solve security by destroying your private keys. But then you can’t access your NFTs either.
The art is balancing these two goals
Printing flyers with your private keys is very resilient but your NFTs will be gone.
You can easily solve security by destroying your private keys. But then you can’t access your NFTs either.
The art is balancing these two goals
31/ To summarize the security failure cases:
If someone gets a hold of:
your private keys
OR
seed phrase AND passphrase (if you used a passphrase)
If someone gets a hold of:
your private keys
OR
seed phrase AND passphrase (if you used a passphrase)
32/ To summarize the resiliency failure cases:
If you lose your private keys AND seed phrase AND passphrase (if you used one)
If you lose your private keys AND seed phrase AND passphrase (if you used one)
33/ With the basics out of the way, let’s go to the main event, “wallets”
“software wallet” = a software wallet on a general purpose device (computer or mobile phone)
“hardware wallet” = a software wallet on a dedicated hardware device (Trezor or Ledger)
“software wallet” = a software wallet on a general purpose device (computer or mobile phone)
“hardware wallet” = a software wallet on a dedicated hardware device (Trezor or Ledger)
34/ I am now going to say the word: metamask
This will summon the phishing bots below these tweets. These are all fake, their goal is your seed phrase and they should be always blocked and reported
General rule: “enter your private key or seed phrase at this link” is a SCAM
This will summon the phishing bots below these tweets. These are all fake, their goal is your seed phrase and they should be always blocked and reported
General rule: “enter your private key or seed phrase at this link” is a SCAM
35/ In order to interact with web 3.0 dapps like Uniswap or Opensea, you need a browser extension that interacts with them.
The most popular is @MetaMask, but there are others.
Metamask has a mobile app that is a pure software wallet
The most popular is @MetaMask, but there are others.
Metamask has a mobile app that is a pure software wallet
36/ Metamask also has a browser extension that can either:
a) operate as a pure software wallet
or
b) provide the browser interface for hardware wallets to interact with dapps
a) operate as a pure software wallet
or
b) provide the browser interface for hardware wallets to interact with dapps
37/ The two most popular hardware wallets are @Trezor and @Ledger. They are both good for security but have different strengths and weaknesses.
@Trezor for ETH NFT has the best browser integration. @Ledger tends to crash quite a bit, drive people crazy
@Trezor for ETH NFT has the best browser integration. @Ledger tends to crash quite a bit, drive people crazy
38/ However @Trezor does not yet support polygon or Tezos. For those you need @Ledger
They came from BTC era so their documentation on how to use with NFTs still sucks and they should invest a person-month each into doing an A+ job on tis
They came from BTC era so their documentation on how to use with NFTs still sucks and they should invest a person-month each into doing an A+ job on tis
39/ My summary recommendations are the following:
Phase I: You have less than $500 to $1,000 to invest in NFTs *in the foreseeable* future. This is the only case to use a software wallet. Metamask is fine on both computers and mobile.
Phase I: You have less than $500 to $1,000 to invest in NFTs *in the foreseeable* future. This is the only case to use a software wallet. Metamask is fine on both computers and mobile.
40/ Phase II: You are going to invest more than $1,000 in NFTs, set up a proper hardware wallet from Day 1.
Trezor and Ledger are both fine, but my detailed setup recommendation is below.
Trezor and Ledger are both fine, but my detailed setup recommendation is below.
41/ Phase III: You have more than $1M to $3M of NFTs or you are working in an institutional context or you have irreplaceable NFTs.
You should set up a @gnosisSafe multi-signature wallet.
You should set up a @gnosisSafe multi-signature wallet.
42/ Software Wallet: Only if you are investing small amounts in NFTs (<$1,000).
Software wallets are not long-term safe. They simply store your private key on your phone or computer.
If your computer is compromised by a virus, your private keys will be stolen.
Software wallets are not long-term safe. They simply store your private key on your phone or computer.
If your computer is compromised by a virus, your private keys will be stolen.
43/ When you are setting up the wallet, you will be given your seed phrase.
You need to write this down carefully on a piece of paper. This allows you to recreate your wallet
You should never ever ever type your seed phrase into a computer or photocopy it.
You need to write this down carefully on a piece of paper. This allows you to recreate your wallet
You should never ever ever type your seed phrase into a computer or photocopy it.
44/ Metamask will have you create a password.
That password is the password that Metamask uses to give you access to Metamask.
This is NOT your passphrase.
It is specific only to Metamask on the specific computer you have installed Metamask.
That password is the password that Metamask uses to give you access to Metamask.
This is NOT your passphrase.
It is specific only to Metamask on the specific computer you have installed Metamask.
45/ You will need your seed phrase if your computer dies, if Metamask gets corrupted, if you lose your computer, if you forget your Metamask password.
The seed phase is your backup! Ideally, your seed phrase is not in your house, but somewhere else.
The seed phase is your backup! Ideally, your seed phrase is not in your house, but somewhere else.
46/ Some people use a steel object to store their seed phrase to be more fire resistant.
This is fine, but overkill if you are on Metamask.
A hardware wallet is more important.
This is fine, but overkill if you are on Metamask.
A hardware wallet is more important.
47/ Phase II: Hardware Wallet
The most expensive hardware wallets are ~0.06ETH (~$200).
If you are investing ANY significant amount in NFTs or expect any significant price appreciation in your NFTs, you must use a hardware wallet.
The most expensive hardware wallets are ~0.06ETH (~$200).
If you are investing ANY significant amount in NFTs or expect any significant price appreciation in your NFTs, you must use a hardware wallet.
48/ You: Which one?
6529: Well, any is fine
You: Yes, but which one?
6529: Fine, if you are working primarily in ETH NFTs, buy the Trezor Model T.
Why? It works better on ETH NFTs than the Ledgers and unlike the Model One, it currently supports 1559 and SSSS (see below).
6529: Well, any is fine
You: Yes, but which one?
6529: Fine, if you are working primarily in ETH NFTs, buy the Trezor Model T.
Why? It works better on ETH NFTs than the Ledgers and unlike the Model One, it currently supports 1559 and SSSS (see below).
49/ OK, how are we going to set this up? 6529 is going to push you do it correctly from Day 1 and use the full panoply of tools available to you. Why? Because if you do, your setup for $5K in NFTs is also a good setup even for $1M in NFTs and you don’t have to change later
50/ Changing default wallets is a huge pain in the ass and 6529 has not enjoyed it at all. I have done both transitions, from software wallet to hardware wallet and from hardware wallet to Gnosis.
It sucks.
It sucks.
51/ You have pay gas to move each individual NFTs.
The second move I did cost me $40K-$50K in gas in total across almost 1,000 NFTs and I have other NFTs where it is not worth it move them.
The second move I did cost me $40K-$50K in gas in total across almost 1,000 NFTs and I have other NFTs where it is not worth it move them.
52/ Also, it is terrifying.
When I moved the Tulip and Sunshine, all I was thinking was “do not fumble this cultural grail and send it to the wrong address”
When I moved the Tulip and Sunshine, all I was thinking was “do not fumble this cultural grail and send it to the wrong address”
53/ This is why I am going push all of you to invest a couple of hours to do the most correct setup possible at the beginning.
For most of you, this type of setup will cover you for a very long time.
The 🐳 are a different story.
For most of you, this type of setup will cover you for a very long time.
The 🐳 are a different story.
54/ My recommended setup for setting up a Trezor for a civilian is the following:
a) Install Trezor Suite
b) Set up the Trezor
c) Apply a PIN to the device
d) Use the Shamir’s Secret Sharing Scheme to split your seed phrase 2 of 3
e) add an easy-for-you-to-remember passphrase
a) Install Trezor Suite
b) Set up the Trezor
c) Apply a PIN to the device
d) Use the Shamir’s Secret Sharing Scheme to split your seed phrase 2 of 3
e) add an easy-for-you-to-remember passphrase
55/ I know that:
a) using Shamir's Secret Sharing Scheme (SSSS)
b) using a passphrase
Are considered advanced and I am OK if you do not do it.
Also, only the Model T supports SSSS
a) using Shamir's Secret Sharing Scheme (SSSS)
b) using a passphrase
Are considered advanced and I am OK if you do not do it.
Also, only the Model T supports SSSS
56/ Let’s take it one step at a time.
Step 1: Buy a Trezor directly from the Trezor web site
Step 2: Follow the software’s instructions for installing the Trezor Suite Software and getting the device set up
Step 1: Buy a Trezor directly from the Trezor web site
Step 2: Follow the software’s instructions for installing the Trezor Suite Software and getting the device set up
57/ Step 3: Select a PIN.
This PIN is the equivalent of the password on Metamask. It unlocks the Trezor device so you can use it. You must do it.
Go for at least 8 digits.
This PIN is the equivalent of the password on Metamask. It unlocks the Trezor device so you can use it. You must do it.
Go for at least 8 digits.
58/ Step 4: Split your seed phrase through Shamir’s Secret Sharing Scheme (it is a built in option in Trezor Suite).
What is this?
One naïve security measure is to divide your seed phrase in half or in thirds so “nobody can find it all in one place”
What is this?
One naïve security measure is to divide your seed phrase in half or in thirds so “nobody can find it all in one place”
59/ This weakens its security however.
If you divide a 12 word seed phrase into two and someone finds 1 part, it is computationally feasible to crack 6 words. (It is not computationally feasible to crack 12 or 18 or 24 words).
If you divide a 12 word seed phrase into two and someone finds 1 part, it is computationally feasible to crack 6 words. (It is not computationally feasible to crack 12 or 18 or 24 words).
60/ When you select SSSS as an option, and you select 2 out of 3, the software will create 3 lists of 20 words. You will need any 2 of out 3 to recreate your wallet.
You can then put these 3 lists in three different places (safety deposit box, your in-laws house, whatever).
You can then put these 3 lists in three different places (safety deposit box, your in-laws house, whatever).
61/ This means your system is robust to your house + 1 other place burning down.
It is also robust to any one of the seed phrases being exposed.
You need at least two to replicate a wallet.
It is also robust to any one of the seed phrases being exposed.
You need at least two to replicate a wallet.
62/ A sophisticated argument against SSSS is that multi-sig is better for multiple people recovering a key.
I agree with this. SSSS is better for protecting one key for one person and you can use it in combination with multi-sig
I agree with this. SSSS is better for protecting one key for one person and you can use it in combination with multi-sig
63/ You apply a passphrase. The passphrase should be something you and/or your family can easily remember.
The hardcore recommendation is “do not write down the passphrase” but if solo you should consider writing it down somewhere else bc you might forget it
The hardcore recommendation is “do not write down the passphrase” but if solo you should consider writing it down somewhere else bc you might forget it
64/ I would have a minor amount of ETH in your wallet without a passphrase aka passphrase “”
This is the decoy wallet, something to be discussed later.
Then your main assets go in the wallet with the passphrase
This is the decoy wallet, something to be discussed later.
Then your main assets go in the wallet with the passphrase
65/ VERY IMPORTANT
You need to test that you recorded your seed phrase correctly before you store it.
In other words, your order of operations is:
a) set up the trezor, with SSSS 2 out of 3 and a passphrase and non passphrase wallet
You need to test that you recorded your seed phrase correctly before you store it.
In other words, your order of operations is:
a) set up the trezor, with SSSS 2 out of 3 and a passphrase and non passphrase wallet
66/
b) send some small amount to ETH to both wallets
c) wipe your Trezor
d) set up again using first 2 out of 3 seed phrases. See that your ETH is there in both wallets
e) wipe your Trezor again
f) repeat the recovery with the last 2 seed phrases
b) send some small amount to ETH to both wallets
c) wipe your Trezor
d) set up again using first 2 out of 3 seed phrases. See that your ETH is there in both wallets
e) wipe your Trezor again
f) repeat the recovery with the last 2 seed phrases
67/ If you have recovered the wallet with both ways, you are cleared for take-off.
Go stash away your seed phrases in different secure locations and, probably your passphrase, in a 4th location (or stash the passphrase in the brain of various other people)
Go stash away your seed phrases in different secure locations and, probably your passphrase, in a 4th location (or stash the passphrase in the brain of various other people)
68/ You now go back to Metamask and Import Hardware wallet to connect your hardware wallet to Metamask.
Now you can use Metamask, using your hardware wallet.
Now you can use Metamask, using your hardware wallet.
69/ If you have NFTs, you have to transfer them to this new wallet. The easiest way is the ‘transfer’ function on OpenSea.
You should transfer 1 to the new wallet and then transfer it back to make sure you do control your address. Only then should you transfer the rest.
You should transfer 1 to the new wallet and then transfer it back to make sure you do control your address. Only then should you transfer the rest.
70/ You should NOT just migrate your existing wallet to your Trezor. Your keys might have already been compromised in Metamask.
You must make a new wallet and transfer the NFTs
You must make a new wallet and transfer the NFTs
71/ Your wallet has multiple ETH addresses.
You should use one as the vault for important NFTs & do not transact out of that wallet. You can use another address on ur same hardware wallet for doing things like minting the new unaudited contract for the Slimy Snail collection
You should use one as the vault for important NFTs & do not transact out of that wallet. You can use another address on ur same hardware wallet for doing things like minting the new unaudited contract for the Slimy Snail collection
72/ That way, if the contract is malicious, you don’t risk your important NFTs.
You can use a mobile wallet for fun/small purchases like this too, at the cost of the extra gas to send them to the vault wallet
You can use a mobile wallet for fun/small purchases like this too, at the cost of the extra gas to send them to the vault wallet
73/ All of the following are reasonable:
a) 1 hardware wallet with 2 ETH addresses, one vault, one for interactions
b) 2 hw, the vault one in a safe place, the other one with you for interactions
c) Either of the above, plus a mobile software wallet for “emergency” purchases
a) 1 hardware wallet with 2 ETH addresses, one vault, one for interactions
b) 2 hw, the vault one in a safe place, the other one with you for interactions
c) Either of the above, plus a mobile software wallet for “emergency” purchases
74/ Now, what is not protected by the above?
a) you give someone your seed phrase
b) you click on a malicious link on your address with your valuable NFTs
So, don’t do that.
a) you give someone your seed phrase
b) you click on a malicious link on your address with your valuable NFTs
So, don’t do that.
75/ Now time to go to the more complex stage for the 🐳and their collections.
This is the highest level of security you can have today but it comes with real costs in inconvenience
The major additional concern of a 🐳 is a wrench attack
This is the highest level of security you can have today but it comes with real costs in inconvenience
The major additional concern of a 🐳 is a wrench attack
77/ The theoretical defense against the wrench attack was the decoy wallet.
Open your wallet without a passphrase, show 10ETH, send it to the attacker, wish them a nice day.
They don’t realize that with a passphrase, you have 1000ETH.
This does not work with well-known NFTs
Open your wallet without a passphrase, show 10ETH, send it to the attacker, wish them a nice day.
They don’t realize that with a passphrase, you have 1000ETH.
This does not work with well-known NFTs
78/ So if someone wants to attack me for summer.jpg, they aren’t going to get fooled by decoy wallet.
For this level of sophistication, you need to move to @gnosisSafe.
For this level of sophistication, you need to move to @gnosisSafe.
79/ Gnosis is a smart contract masquerading as a wallet. In other words, it has an address that can be treated as a public address, but it is really its own smart contract on the ETH blockchain and it is visibly so
80/ Gnosis has been used as a vault/treasury by many defi protocols and increasingly for NFT vaults. The important feature for these purposes is that you can create whatever signing protocols you want to authorize a transaction.
For example 2 out of 3 or 2 of 4 or 3 of 5 etc
For example 2 out of 3 or 2 of 4 or 3 of 5 etc
81/ In the high-end setup, each of the signers can be anything – a software wallet or a hardware wallet.
The most hardened approach would be that each signer is a distributed offline SSSS hardware wallet setup
The most hardened approach would be that each signer is a distributed offline SSSS hardware wallet setup
82/ So opensea.io/6529Museum is now a Gnosis multi-signature wallet. You can check online and see that it is a smart contract, not an address.
83/ It has multiple signing keys, each of which is broken into its component parts and distributed across dozens of people and institutions in multiple continents.
None of the keys are hot, none of the keys are on us. Even I don’t even know where all the components are.
None of the keys are hot, none of the keys are on us. Even I don’t even know where all the components are.
84/ Without getting into further detail, I think trying to wrench attack anyone in the 6529 team would likely result in:
a) not getting the keys because it would take days and institutions and
b) you getting arrested
Also, who is going to believe I sold you the Tulip? 😉
a) not getting the keys because it would take days and institutions and
b) you getting arrested
Also, who is going to believe I sold you the Tulip? 😉
85/ So how does 6529 operate now? My day-to-day actions are a hardware wallet setup.
Then NFTs are sent to the Gnosis 6529 Museum Vault.
It costs 2 x gas but that is the price to pay to operate at this scale.
Then NFTs are sent to the Gnosis 6529 Museum Vault.
It costs 2 x gas but that is the price to pay to operate at this scale.
86/ This has a cost of course which is the Museum is no longer flexible. The process of moving something out of the Museum to use it to mint or stake is now a multi-day, multi-person process which is really only worth it if there is something important to do.
87/ So this really only makes sense for very valuable and publicly visible collections to both:
a) use a multi-sig wallet and
b) keep everything distributed and not accessible
a) use a multi-sig wallet and
b) keep everything distributed and not accessible
88/ There is another potential use of a multi-sig which is “being an idiot insurance”.
Here you can make a 2 out of 3 setup, give a trusted friend 1 key and don’t do anything unless they sign also.
Here you can make a 2 out of 3 setup, give a trusted friend 1 key and don’t do anything unless they sign also.
89/ That way if you have a momentary FOMO moment and start trying to connect to some site someone pitched you on Discord, you might have a 2nd voice of reason that prevents disaster.
@argentHQ, in a different way, tries to provide something like this
@argentHQ, in a different way, tries to provide something like this
90/ There is one more great use of Gnosis and it is for collective holdings.
A group of friends or an institution (e.g. company, fund, etc) or a DAO hold some NFTs.
A group of friends or an institution (e.g. company, fund, etc) or a DAO hold some NFTs.
91/ Nobody should have sole responsibility or authority to hold those NFTs, regardless of value.
A Gnosis multi-sig, possibly with the keys more accessible for convenience, is a great solution for this situation.
A Gnosis multi-sig, possibly with the keys more accessible for convenience, is a great solution for this situation.
92/ So let me summarize the key steps so far:
a) <$1,000 – software wallet
b) everyone else – hardware wallet
c) [🐳only in most cases] – gnosis multi-sig, with offline key distribution
d) friends/groups/institutions – gnosis multi-sig, offline or online keys
a) <$1,000 – software wallet
b) everyone else – hardware wallet
c) [🐳only in most cases] – gnosis multi-sig, with offline key distribution
d) friends/groups/institutions – gnosis multi-sig, offline or online keys
93/ If you are distributing SSSS seed phrase shards, pins, hw wallets, passphrases and so on, you need to think carefully who could get quorum on your wallet or multi-sig and who you trust.
This is very individual, I can't help, just think about it very very carefully
This is very individual, I can't help, just think about it very very carefully
94/ One of the nice thing about distributing SSSS off-site versus seed phrases is that the shards are individually useless.
Whereas a seed phrase without a passphrase is the keys to the kingdom
Whereas a seed phrase without a passphrase is the keys to the kingdom
95/ One more thing to consider. I regret to inform you that one day we are all going to ngmi and we will go 6 feet under.
If you have NFTs of financial and emotional value, you should think through how the beneficiaries of your will, will receive those NFTs.
If you have NFTs of financial and emotional value, you should think through how the beneficiaries of your will, will receive those NFTs.
96/ There have been many horror stories from BTC era on of huge fortunes dying with the key holder
Every situation varies, but if you think through the possibilities with seed phrases (SSSS) and/or multi-sig wallets, you can construct I believe logical estate planning approaches
Every situation varies, but if you think through the possibilities with seed phrases (SSSS) and/or multi-sig wallets, you can construct I believe logical estate planning approaches
97/ What is great about all the above? They are all non-custodial. There will be custodial solutions soon from the major players and those are fine too.
98/ But I doubt they are much more secure in practice (the risk of social engineering or a wrench attack just moves to the authorization stage between you and the custodian) and you are no longer digitally self-sovereign.
Or, at least, you are less so.
Or, at least, you are less so.
99/ This might seem like a lot to absorb, or maybe even difficult. But the investment in time to get up to speed is really not that high.
It is a 1-time cost and once you have done it and you on the other side, it is quite straightforward.
It is a 1-time cost and once you have done it and you on the other side, it is quite straightforward.
100/ I consider crypto competency a core life skill like 'driving a car' or 'understanding how budgets work'. Each of those things takes hundreds of hours to learn. This will be a few hours for most people. But even if it is 10 or 20 or 40, why not?
101/ Learning these skills puts you a step ahead for the Web 3.0 economy and lets you reduce dramatically the risk of some type of disaster with your NFTS and crypto.
So get over here with the cool crypto kids and learn this stuff
So get over here with the cool crypto kids and learn this stuff
102/ That is all for this thread. I hope it is helpful. 🙏
If you came here for the first time for this thread and want to learn more about NFTs and the Open Metaverse, go here and here:
If you came here for the first time for this thread and want to learn more about NFTs and the Open Metaverse, go here and here:
https://twitter.com/punk6529/status/1429399888786333697
https://twitter.com/punk6529/status/1448399827054833668
103/ Update: The feed says that Model T works on Polygon and it was the uncorrected 1559 issue on Model One that was the problem.
I have not checked, but you can check this out.
I have not checked, but you can check this out.
104/ @gnosisSafe display of NFTs is immature. I do not think it properly handles punks or 1155 yet. But you can use OpenSea for now
https://twitter.com/XCOPYART/status/1461762048031965199?s=20
105/ Key Swapping
Another advantage of the multi-sig wallets is that you can swap out the keys.
So if later a key gets compromised or you decide to use a different hardware wallet or different setup, you can swap keys in and out
Another advantage of the multi-sig wallets is that you can swap out the keys.
So if later a key gets compromised or you decide to use a different hardware wallet or different setup, you can swap keys in and out
106/ Dedicated Laptop
You may consider a dedicated laptop (Mac or Linux) for interacting with vault and/or high value NFTs.
It is <0.5 ETH
I don't think it is necessarily needed for day to day transactions.
You may consider a dedicated laptop (Mac or Linux) for interacting with vault and/or high value NFTs.
It is <0.5 ETH
I don't think it is necessarily needed for day to day transactions.
107/ Risk v Convenience
Vault: Losses that would be devastating to you (economically or emotionally)
Day to Day (not in vault): Amounts that might be annoying but you will get over it in a week
The absolute value will vary by person
Vault: Losses that would be devastating to you (economically or emotionally)
Day to Day (not in vault): Amounts that might be annoying but you will get over it in a week
The absolute value will vary by person
• • •
Missing some Tweet in this thread? You can try to
force a refresh