
Thread:
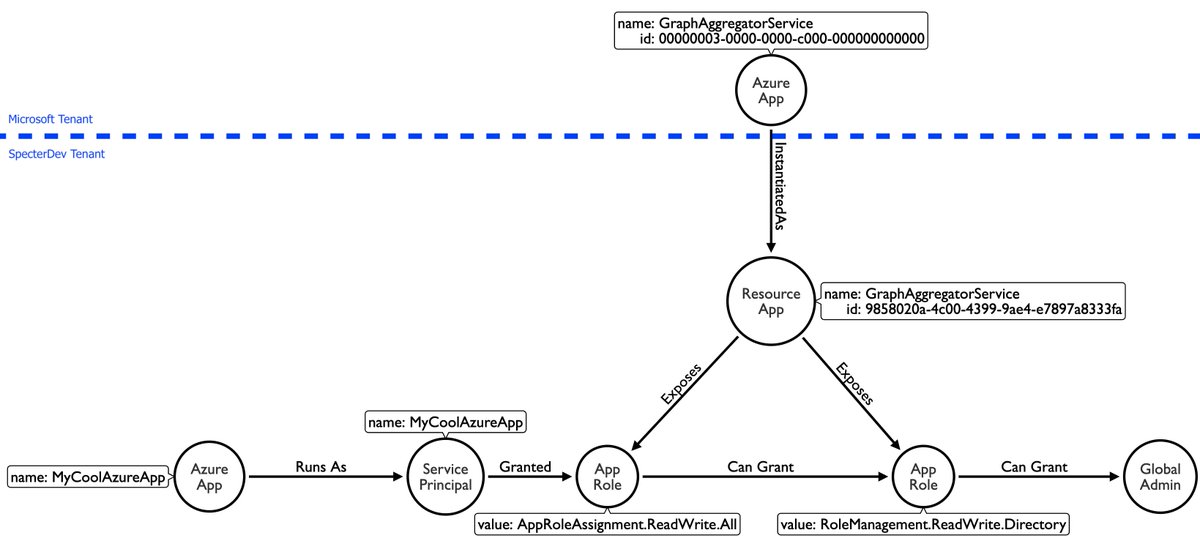
API permissions in #Azure can be configured such that attack paths leading to Global Admin emerge. Prior work and links to our work below:
API permissions in #Azure can be configured such that attack paths leading to Global Admin emerge. Prior work and links to our work below:

Blog: Azure Privilege Escalation via Azure API Permissions Abuse posts.specterops.io/azure-privileg… 
Recording of the talk: specterops.zoom.us/webinar/regist…
Deck: bit.ly/3El0nNO 

Prior work:
This topic was covered by @sahilmalik in two great blog posts:
winsmarts.com/how-to-grant-a…
winsmarts.com/automating-app…
This topic was covered by @sahilmalik in two great blog posts:
winsmarts.com/how-to-grant-a…
winsmarts.com/automating-app…
@_dirkjan discussed abusing API permissions in this blog post: dirkjanm.io/azure-ad-privi…
@inversecos discussed abusing app registrations and service principals for backdoor persistence in Azure here: inversecos.com/2021/10/how-to…
• • •
Missing some Tweet in this thread? You can try to
force a refresh



