Let's talk about tiered administration in AzureAD:
- What it starts with
- How it can be violated
- What you can do about that
In 10 tweets or less. Go:
- What it starts with
- How it can be violated
- What you can do about that
In 10 tweets or less. Go:
1/ There are three default admin roles that belong to Tier Zero in AzureAD:
Global Admin
Priv. Role Admin
Priv. Auth Admin
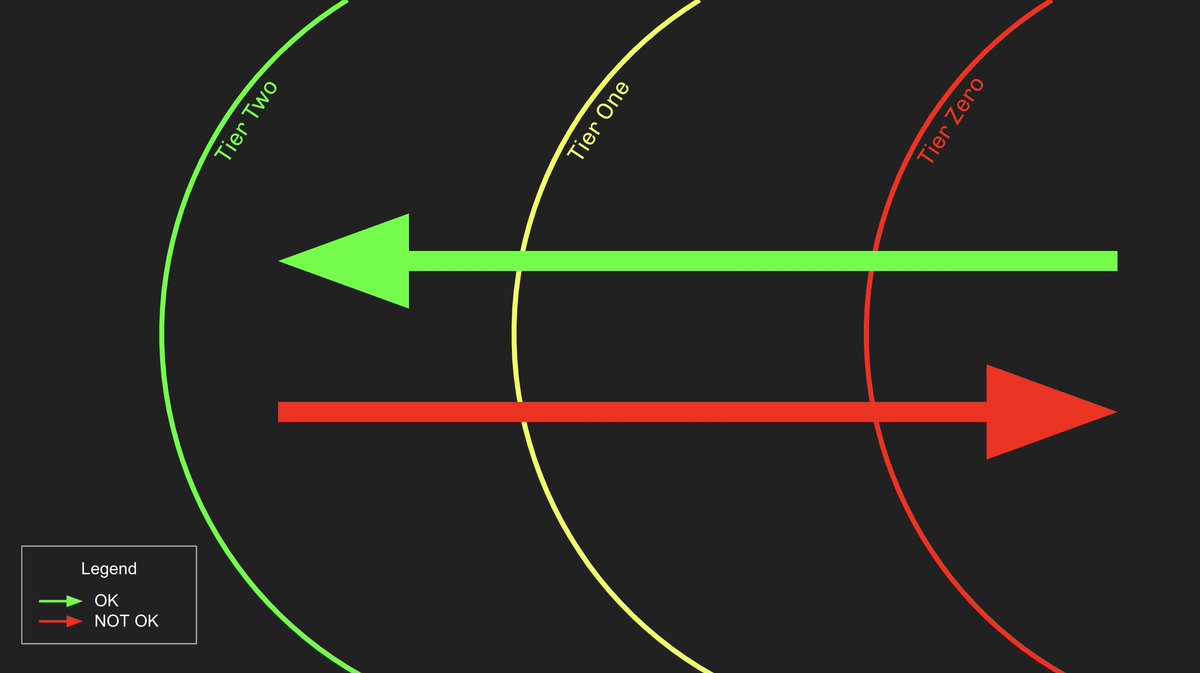
Everything IN tier zero is tier zero. Everything ELSE is not tier zero has has no business controlling anything IN tier zero.
Global Admin
Priv. Role Admin
Priv. Auth Admin
Everything IN tier zero is tier zero. Everything ELSE is not tier zero has has no business controlling anything IN tier zero.

2/ These admin roles aren't of much use if you don't grant them to anyone. Let's grant a service principal the Global Admin role: 

3/ If we agree that this service principal needs this role assignment, then this isn't a *violation* of tiered administration -- it is an *expansion* of the definition of tier zero in our environment: 

4/ You've expanded the definition of what tier zero is to now include this service principal. Cool.
But what has control of this service principal? For starters, the Cloud App Admin role:
But what has control of this service principal? For starters, the Cloud App Admin role:

5/ Other things control this SP, too, but let's stay focused on this admin role to illustrate the point.
We've agreed that the SP needs GA and will be part of Tier Zero. We must now also agree that the Cloud App Admin role is a tier zero role, as well:
We've agreed that the SP needs GA and will be part of Tier Zero. We must now also agree that the Cloud App Admin role is a tier zero role, as well:

6/ Why must Cloud App Admin be tier zero? Because the actions allowed by this role are immutable: you cannot change them. ANYONE granted this role can control your tier zero SP now, so this role must now be considered tier zero.
7/ Now let's say we grant the Cloud App Admin role to two users: a tier zero user and a tier one user: 

8/ Now we have a tiered administration violation: a tier one user has control of a tier zero object.
See this post for how an attacker can abuse this: posts.specterops.io/azure-privileg…
See this post for how an attacker can abuse this: posts.specterops.io/azure-privileg…

9/ The "all or nothing" nature of Azure AD admin roles means that the most straight-forward way to deal with this is to revoke the tier one user's Cloud App Admin role assignment
10/ You can start to find these tiered administration violations yourself today with FOSS #BloodHound: github.com/BloodHoundAD/B…
• • •
Missing some Tweet in this thread? You can try to
force a refresh