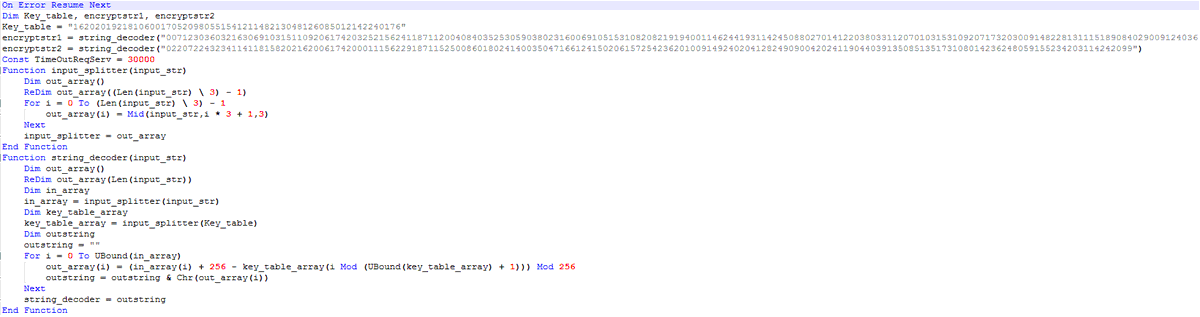
Interesting #maldoc
#TrickBot is distributed using a maldoc that uses #Emotet Template:
Process:
- It drops a small dll (1.xml) and executes its by creating an Outlook instance that calls rundll to execute 1.xml
- Drops a PS file and executes it
- Downloads and executes TrickBot


#TrickBot is distributed using a maldoc that uses #Emotet Template:
Process:
- It drops a small dll (1.xml) and executes its by creating an Outlook instance that calls rundll to execute 1.xml
- Drops a PS file and executes it
- Downloads and executes TrickBot



Maldoc:
b2859b4165a3047632174c1cd26b6756
1.xml:
8de70541621842ae7e3e6e21b41ee155
TrickBot download urls:
http://91.92.109.142/wolf.png
http://192.99.255.33/images/wolf.png
http://83.138.53.103/images/wolf.png
http://172.96.189.216/images/wolf.png
b2859b4165a3047632174c1cd26b6756
1.xml:
8de70541621842ae7e3e6e21b41ee155
TrickBot download urls:
http://91.92.109.142/wolf.png
http://192.99.255.33/images/wolf.png
http://83.138.53.103/images/wolf.png
http://172.96.189.216/images/wolf.png
TrickBot:
ad5ad0ce03a4de9de5829cdf2ec78d59
b4dcf8f35e2ba2fa4af1ec6c95d4c179
efaf7ddf9bc9398f18c76bf16e23755e
ff1f685e2a3381d277e71580e1166b06
a051cc64e345d440606d3c28463b8f95
ad5ad0ce03a4de9de5829cdf2ec78d59
b4dcf8f35e2ba2fa4af1ec6c95d4c179
efaf7ddf9bc9398f18c76bf16e23755e
ff1f685e2a3381d277e71580e1166b06
a051cc64e345d440606d3c28463b8f95
• • •
Missing some Tweet in this thread? You can try to
force a refresh