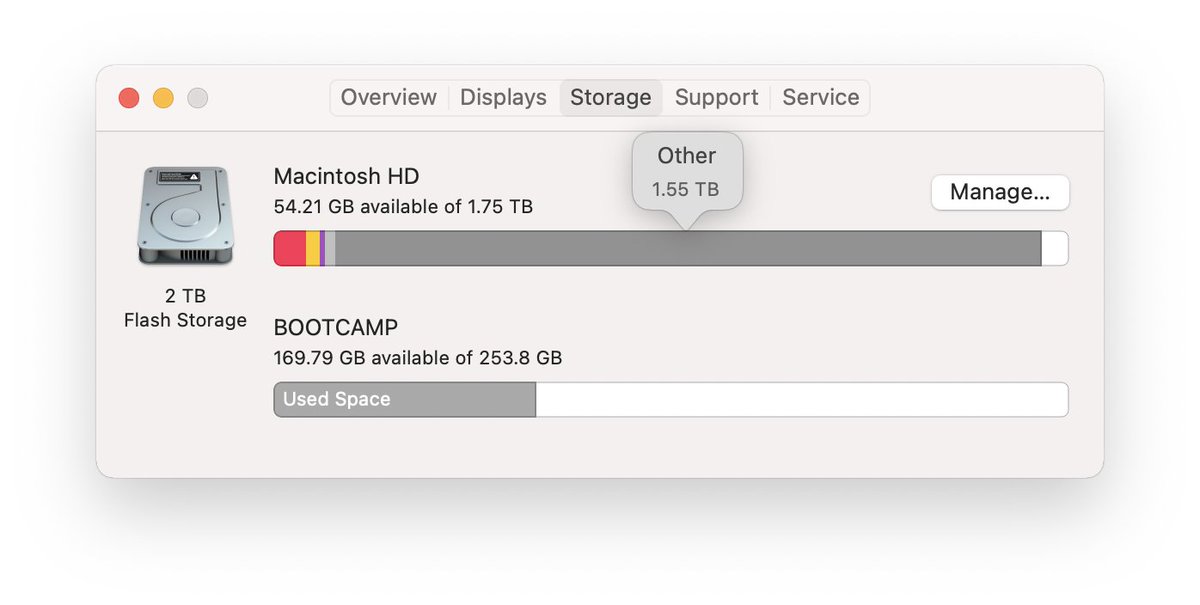
It's under-appreciated how simple and elegant the OS X UI experience is. In just a single glance here I can learn absolutely nothing about where all my disk space went 
It calls to mind the classic design principles of ed(1): "generous enough to flag errors, yet prudent enough not to overwhelm the novice with verbosity" 

Another elegant touch is the way the UI gently keeps users on the path of righteousness. Open source weirdos may complain about their "freedoms", but I sleep more soundly knowing that Big Mac is watching out for me–there will be no rogue disk inventorying in this house! 

And let me call out this detail: "macOS cannot verify that this app is free from malware". It's pretty cool to know that for signed apps, Apple is able to solve the halting problem—honestly astonishing that they only charge developers $99/year for that.
• • •
Missing some Tweet in this thread? You can try to
force a refresh