
New @citizenlab report, #ProjectTorogoz, documenting the use of NSO's Pegasus spyware in El Salvador, in collab w/ @AccessNow, w/ assistance from @FrontLineHRD @MohdMaskati, @socialtic, and @fundacionacceso, and w/ peer review from @AmnestyTech citizenlab.ca/2022/01/projec…
We confirmed, through forensic analysis, 35 cases of journalists and civil society members whose phones were successfully hacked with NSO Group's Pegasus spyware from July 2020 through November 2021. 

The targets included journalists at @_elfaro_, @GatoEncerradoSV, @prensagrafica, @Disruptiva2, @ElMundoSV, @EDHNoticias, and 2 independent journalists. Also NGOs @fundaciondtj, @cristosal, and another (anonymous) NGO.
Since early 2020, we've been tracking a Pegasus operator, TOROGOZ (whose first infrastructure was apparently registered in late 2019) that appeared to be spying primarily in El Salvador, but we hadn't documented any targets.
We documented the first confirmed targets in El Salvador when some independent journalists in El Salvador became suspicious of their phones, ran @AmnestyTech's mvt tool (github.com/mvt-project/mvt), and contacted @AccessNow for assistance.
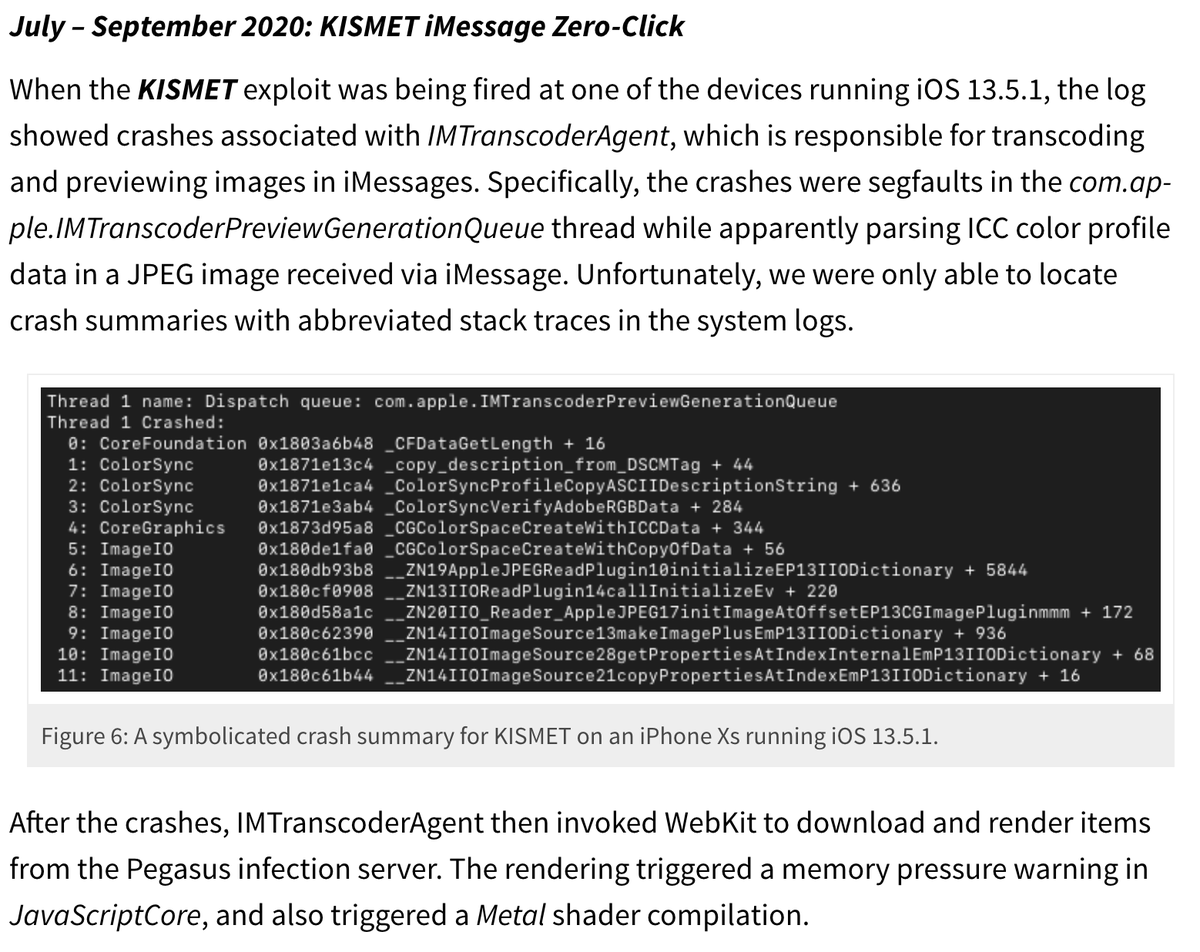
The phones were hacked using at least two different zero-click iMessage exploits: the KISMET iOS13 zero-click (deployed starting in early-to-mid July 2020), and the FORCEDENTRY iOS14 zero-click (deployed starting in ~Feb 2021).
All iOS devices running iOS14 versions up to and including 14.7.1 are believed to be vulnerable to FORCEDENTRY, and the exploit was deployed from ~Feb 2021 thru at least Nov 23, 2021, when Apple sued NSO Group and notified some FORCEDENTRY targets. apple.com/newsroom/2021/…
One journalist was additionally targeted with one-click Pegasus SMSes, in early July 2020 and again in early September 2020. The domain names in the SMSes matched one of our fingerprints for Pegasus URL shortener websites (image via @_elfaro_). 

The Pegasus SMSes contained El Salvador-themed bait content, including "District attorney’s office against journalists from El Faro" and "Nuevas Ideas [the political party of El Salvador Pres. Nayib Bukele] eclipses their opponents".
We conclude that the KISMET zero-click was also used because thirteen of the phones contained the KISMET FACTOR, which we believe is a forensic artifact left behind when the KISMET exploit runs on a phone.
(Note that the KISMET zero-click has not yet been captured and publicly disclosed, but appeared to involve JPEG attachments, as well as iMessage launching a WebKit instance for further exploitation). 
We conclude that the FORCEDENTRY zero-click was also used, because many of the targets were notified by Apple, and we also recovered a copy of NSO Group's FORCEDENTRY exploit that had been fired at one of the phones.
Interesting tidbit: the exploit we recovered had been fired at a *non-vulnerable* version of iOS (14.8.1), and thus did nothing to the phone... Perhaps it's hard for threat actors to accurately fingerprint a target's iMessage version (esp. minor version) before firing a 0-click?
One thing that is striking about the targets in El Salvador: quite a few appear to have been selected for long-term "persistent" surveillance, meaning that zero-clicks were fired again and again after targets rebooted their devices. 

Also interesting: based on dates we observed, it looks like the Pegasus campaign in El Salvador was put on pause amidst the #PegasusProject revelations in mid-Jul 2021, but the hacking quietly resumed around late Aug 2021.
In response to #ProjectTorogoz, a "person familiar with [NSO] operations" said that El Salvador does not have an "active [Pegasus] system". 

However, NSO does not appear to have (yet) incremented their "number of clients we've kicked off of Pegasus" counter beyond 5, so it's unclear if El Salvador has been kicked off Pegasus, voluntarily left Pegasus, or is on a temporary Pegasus pause, or something else...
Also, this is our first report where we have a "featured animated GIF" for the report!!! (designed by @rizhouto) Our GIF doesn't contain FORCEDENTRY, we swear 😀. You can check out our GIF here on our homepage (citizenlab.ca).
• • •
Missing some Tweet in this thread? You can try to
force a refresh







