
Spotted an awesome data terminal made by @SirH4shalot 👀
👉github.com/sirhashalot/SC…
This list highlights the accomplishments and disclosed vulnerabilities of the top white-hat security experts in #DeFi 🤯
👉github.com/sirhashalot/SC…
This list highlights the accomplishments and disclosed vulnerabilities of the top white-hat security experts in #DeFi 🤯
This list only includes actual vulnerabilities. There are CWE-like lists that exist to capture common weaknesses in code, including these lists:
👉swcregistry.io
👉securing.github.io/SCSVS
👉github.com/sigp/solidity-…
👉github.com/blockthreat
👉secureum.xyz
👉swcregistry.io
👉securing.github.io/SCSVS
👉github.com/sigp/solidity-…
👉github.com/blockthreat
👉secureum.xyz
This list does not include black hat hacks which involved user loss of funds, even if the funds are returned. There are other lists for that, including these lists:
👉rekt.news
👉hacked.slowmist.io
👉cryptosec.info/defi-hacks
👉github.com/jwparktom/Gutt…
👉rekt.news
👉hacked.slowmist.io
👉cryptosec.info/defi-hacks
👉github.com/jwparktom/Gutt…
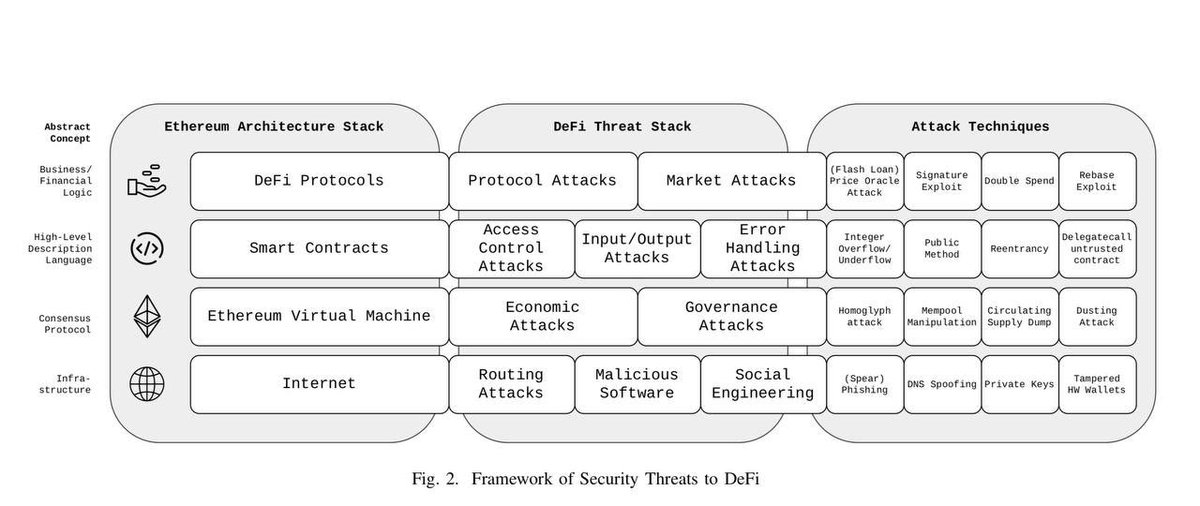
To my knowledge there were several researches on topic as well - arxiv.org/pdf/2106.10740… & arxiv.org/pdf/2109.06836… 
• • •
Missing some Tweet in this thread? You can try to
force a refresh







