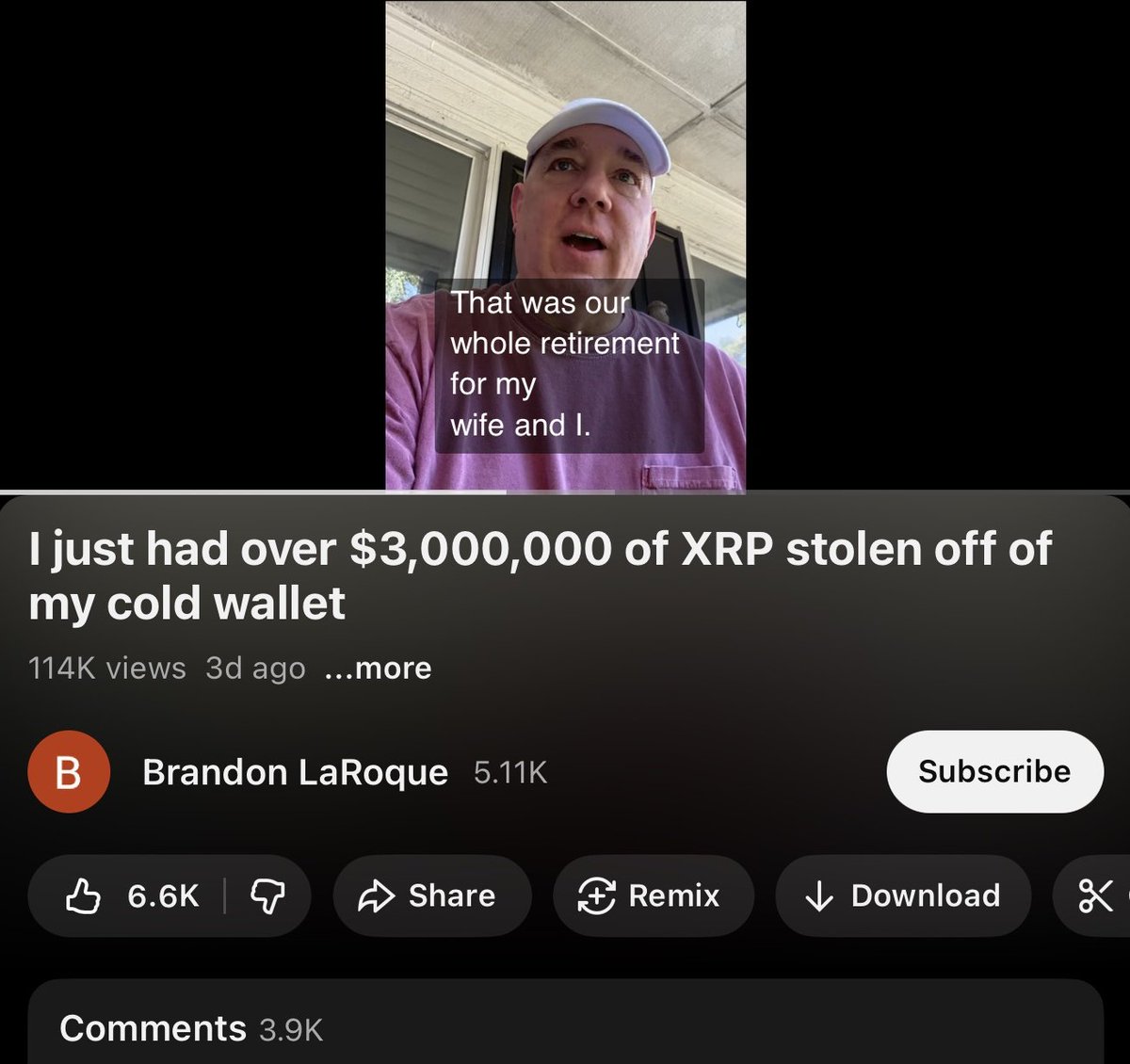
1/ Examining how @ashwsbreal has mislead thousands of people to build up an 8 figure crypto portfolio. 

2/ Our story begins with Ash’s Telegram group.
Well what’s wrong with the TG group?
a) pumping & dumping lowcaps on CEXs.
b) Insider paid group to receive picks before main TG channel.
c) Undisclosed IDO promotions
d) Links to a sketchy VC

Well what’s wrong with the TG group?
a) pumping & dumping lowcaps on CEXs.
b) Insider paid group to receive picks before main TG channel.
c) Undisclosed IDO promotions
d) Links to a sketchy VC


3/ All messages of pumping & dumping lowcaps have been deleted but I’ve recovered a few instances from people on Twitter complaining. 







5/ Ash claimed it wasn’t intentional and they would refund people.
Yet there’s people complaining on Twitter they never were reimbursed for the P&D.
There’s also zero mention of the VIDT P&D either.

Yet there’s people complaining on Twitter they never were reimbursed for the P&D.
There’s also zero mention of the VIDT P&D either.


6/ Here’s a breakdown of the paid group:
In the public TG group Ash would market a paid private group to its members.
-Blatantly saying they get buy signals & insider info before the main public channel
-I’ve attached the payment address courtesy of a former member



In the public TG group Ash would market a paid private group to its members.
-Blatantly saying they get buy signals & insider info before the main public channel
-I’ve attached the payment address courtesy of a former member




7/ On 03/06/21 a buy signal was made in the paid group to buy $ROYA
Guess what? The address in the photo above (0X43) was making large buys a few days prior.
The paid group is told it will be shilled shortly in the public group.


Guess what? The address in the photo above (0X43) was making large buys a few days prior.
The paid group is told it will be shilled shortly in the public group.



8/ As of now all is going well and it gets posted in the public group.
Immediately after Ash says in the paid group “who the f is selling”
*hint it’s the address from above sending to a different wallet to sell*
Ash acts mad saying everyone messed up the pump (the irony).



Immediately after Ash says in the paid group “who the f is selling”
*hint it’s the address from above sending to a different wallet to sell*
Ash acts mad saying everyone messed up the pump (the irony).




9/ Here are all the undisclosed shills that tie between the public Telegram & Twitter account:
AIOZ is down 93%
GS is down 97%



AIOZ is down 93%
GS is down 97%




10/ Most shills in the Public Telegram get deleted. Here are a couple more Twitter ones.
BLES down 99%
EQZ down 97%
KPAD down 99%
MNY down 94%
Just a quick scroll through Ash’s feed shows all the undisclosed shills. It’s clear they will promote any IDO.



BLES down 99%
EQZ down 97%
KPAD down 99%
MNY down 94%
Just a quick scroll through Ash’s feed shows all the undisclosed shills. It’s clear they will promote any IDO.




11/ Here’s where things get even more interesting I messaged the same account to try and join the “paid TG group” and now instead of Ash the account says Jazz @EverseHQ 


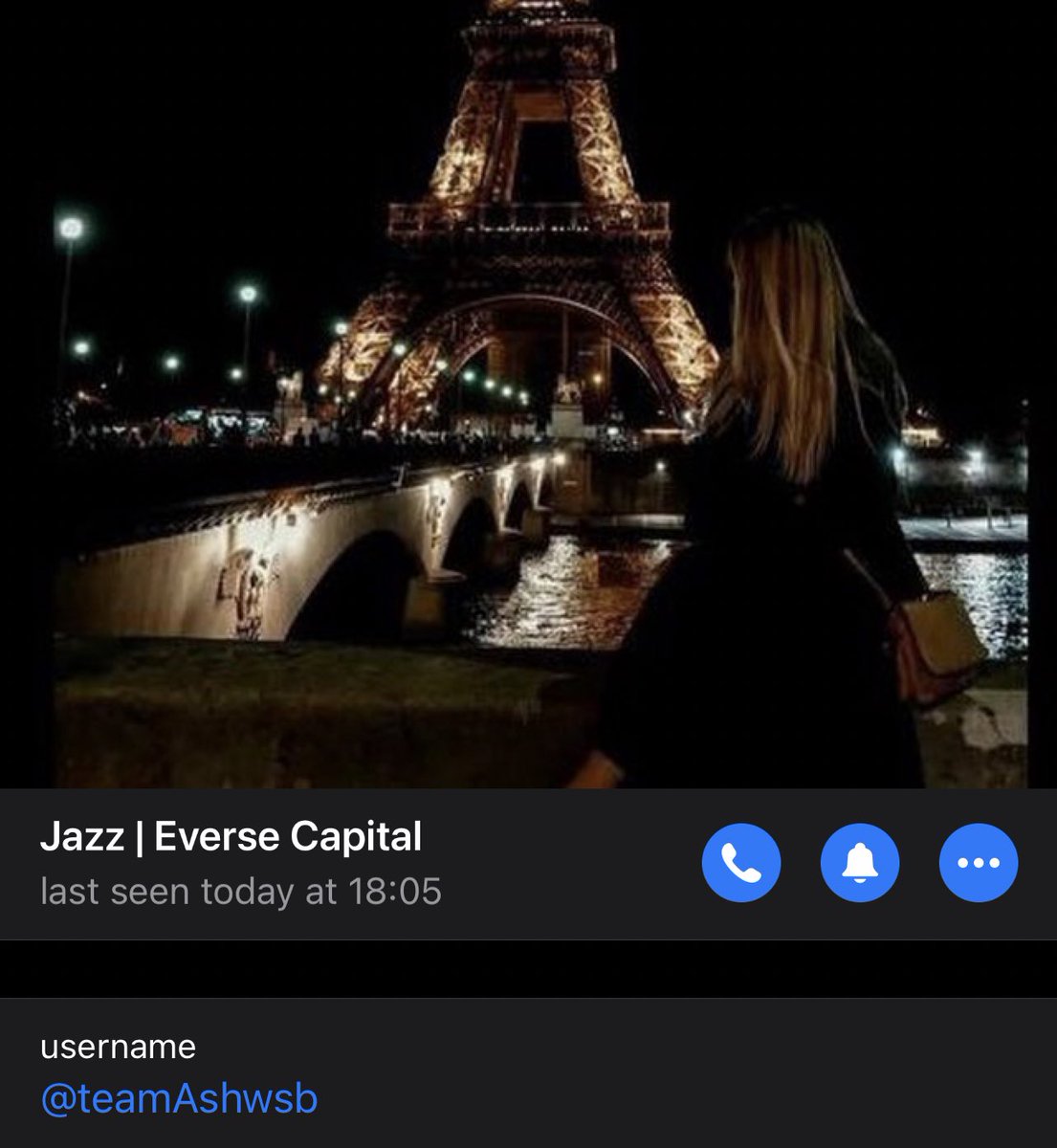
12/ What remains unclear is if the Ash account is ran by that VC or they are just working together.
The fact the TG account matches the Public TG leads me to believe Ash is owned by Everse.
You can see all the cash grabs they work with & on their Twitter
cypherhunter.com/en/p/everse-ca…
The fact the TG account matches the Public TG leads me to believe Ash is owned by Everse.
You can see all the cash grabs they work with & on their Twitter
cypherhunter.com/en/p/everse-ca…
13/ I glanced over all the related addresses (giveaways, dumping, paid group).
Both show a transaction history filled with IDO allocations with outflows to the main wallets (don’t appear to be CEXs)
Also further leads me to believe Ash is Everse.


Both show a transaction history filled with IDO allocations with outflows to the main wallets (don’t appear to be CEXs)
Also further leads me to believe Ash is Everse.

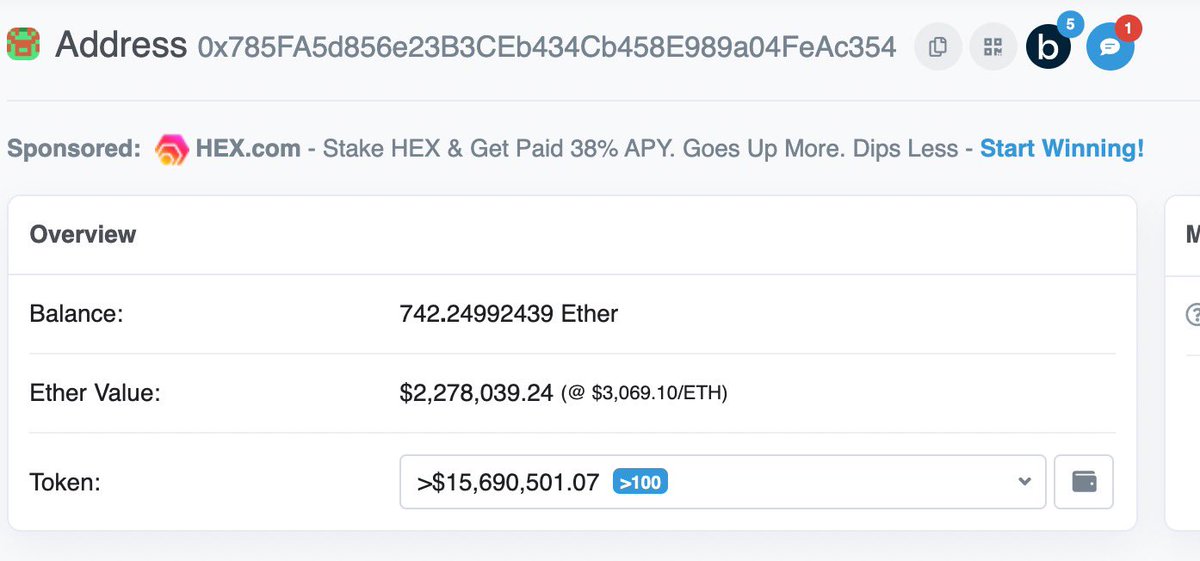

14/ It’s interesting to see how large this operation is and how they have no morals to disclose to followers.
Hopefully some more information about this relationship can come to light. It’s clear whatever is happening is making these people millions at the expense of others.
Hopefully some more information about this relationship can come to light. It’s clear whatever is happening is making these people millions at the expense of others.

Update: I’ve received multiple DMs from people that in fact confirm Ash & Everse Capital are ran by the same person
• • •
Missing some Tweet in this thread? You can try to
force a refresh