Our #BloodHoundEnterprise customers really value measuring the exposure of any given #AttackPath so I figured I'd do a quick 🧵 to explain how this works
We'll start with an example, Riley (a regular user) has rights over a Domain Controller (Tier Zero / Critical Asset): 

This is certainly an issue we'd want to address but how do we really assess the risk?
Let's look at who can control Riley's account.
Let's look at who can control Riley's account.
The Help Desk Group (5 members) can reset her password and the sysadmin team (3 members) who have local administrative rights on her machine: 

This is starting to look serious.
But look at what happens when Riley runs a script across some servers to install some software:
But look at what happens when Riley runs a script across some servers to install some software:

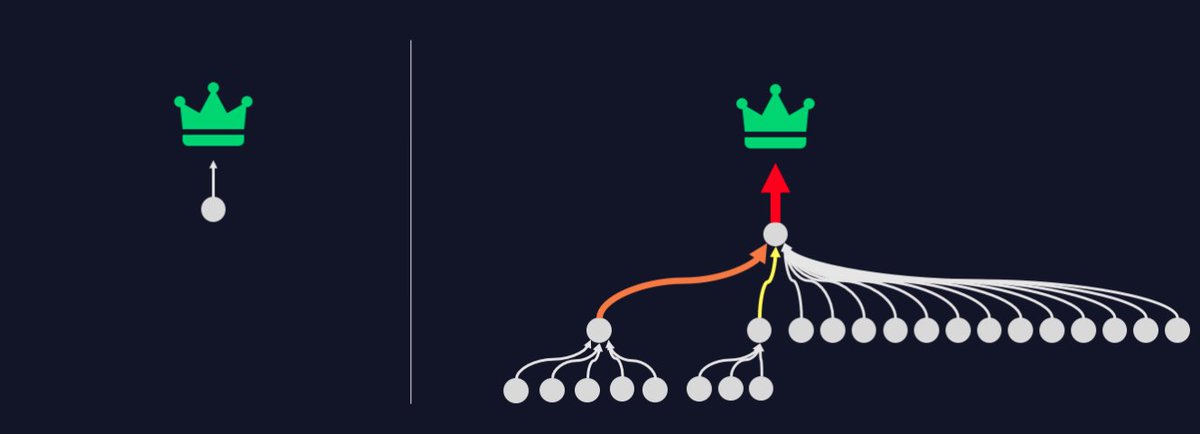
This exposure measurement continues even further:
- Who can target the Help Desk team?
- Who has privileges on those servers?
And further still:
- For each of those answers, who has an Attack Path to those?
And so on, and so on
- Who can target the Help Desk team?
- Who has privileges on those servers?
And further still:
- For each of those answers, who has an Attack Path to those?
And so on, and so on
A seemingly innocuous privilege can quickly cascade through the relationships in AD and make it trivial for an adversary to find a path to their objective.
BloodHound Enterprise continuously monitors and measures this Attack Path risk by first mapping all paths from critical assets: 

And quantifies their exposure based on how much of the environment can abuse each path.
I.e. "92% of all users have an Attack Path to fully control our domain through this GenericWrite privilege on the CONTOSODC01 Domain Controller":
I.e. "92% of all users have an Attack Path to fully control our domain through this GenericWrite privilege on the CONTOSODC01 Domain Controller":

This is objective, empirical measurement of risk.
Your environment and your specific AD architecture.
Your specific risk.
Your environment and your specific AD architecture.
Your specific risk.
Empirical measurements of risk allow BloodHound Enterprise customers to better prioritize remediation: 

For more detail, check out this post:
posts.specterops.io/3-foundational…
Want to see it in your environment? Sign up here for a demo: bloodhoundenterprise.io
posts.specterops.io/3-foundational…
Want to see it in your environment? Sign up here for a demo: bloodhoundenterprise.io
• • •
Missing some Tweet in this thread? You can try to
force a refresh