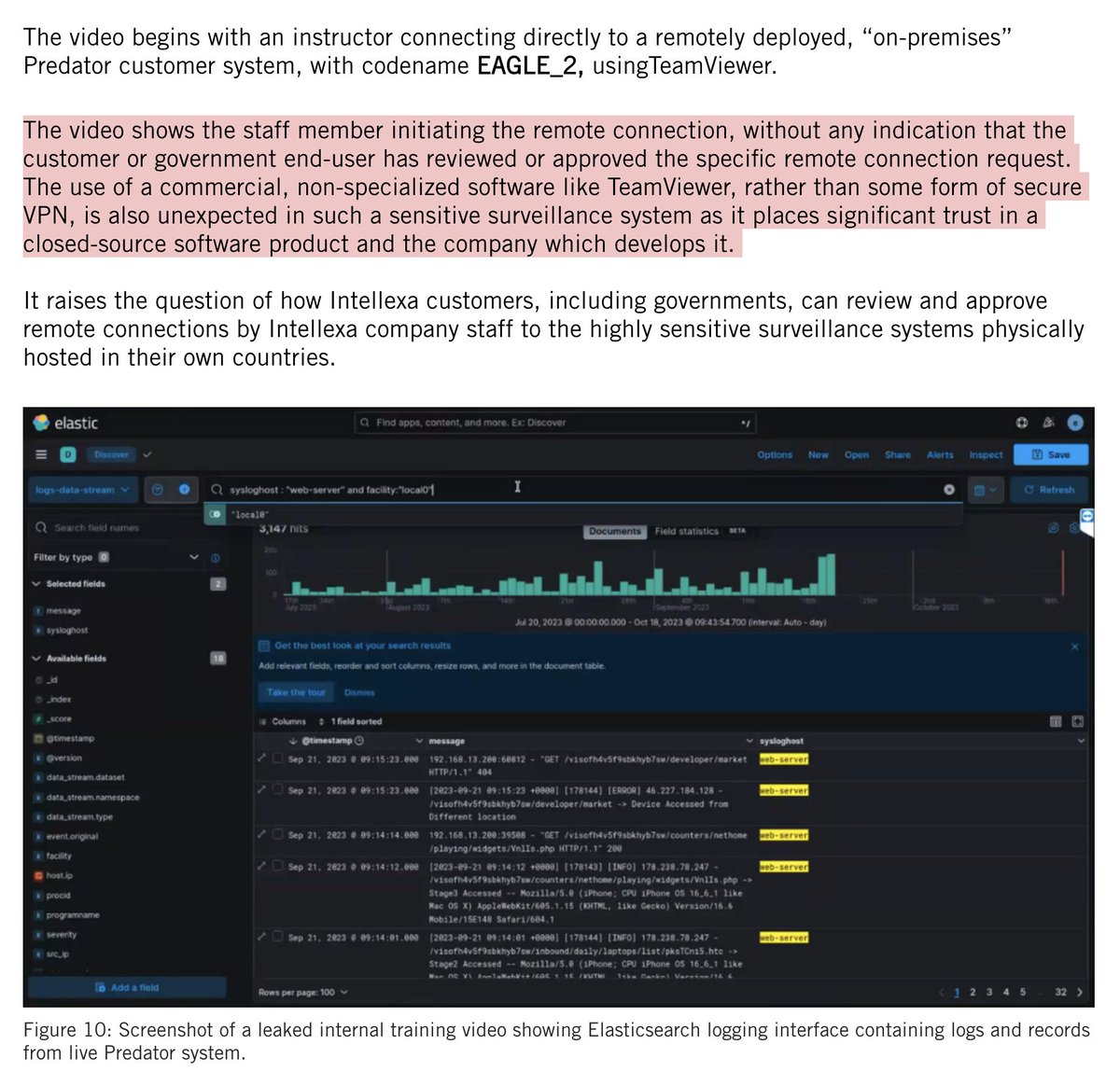
Massive container ship #EVERFORWARD has run aground in the Chesapeake Bay.
Yes, same operator as #EVERGIVEN.
Yes, almost exactly a year later. 1/



Yes, same operator as #EVERGIVEN.
Yes, almost exactly a year later. 1/




2/ Looking at charts, #EVERFORWARD may have slightly deviated from dredged navigation channel into shallower waters after departing Baltimore.
And got stuck.
She's apparently not blocking the navigation channel, but is quite close to it.



And got stuck.
She's apparently not blocking the navigation channel, but is quite close to it.



3/ The #EverForward's AIS track is... interesting.
People may read it as: she missed a waypoint (didn't make a turn) heading from Craighill Angle into Craighill Channel.
Caveat: accidents = complicated & AIS tracks can be *imprecise* so take all guesses w/big grain of salt!

People may read it as: she missed a waypoint (didn't make a turn) heading from Craighill Angle into Craighill Channel.
Caveat: accidents = complicated & AIS tracks can be *imprecise* so take all guesses w/big grain of salt!


4/ UPDATE: was going through wind records (not substantial), speed (she kept speed), draught (lot of empty containers), load condition.. when... @mercoglianos with a video!
Takeaway: he also thinks #EverForward missed the turn!
Now, here's the thing...
Takeaway: he also thinks #EverForward missed the turn!
Now, here's the thing...
5/ The #EverForward is aground in a shoal area of ~24 feet of water.
She lists as 42.6 feet of draught (depth below waterline).
Takeaway: VERY stuck. Getting her un-stuck & back into the 51 foot deep Craighill Channel is likely to be a *big production.*
She lists as 42.6 feet of draught (depth below waterline).
Takeaway: VERY stuck. Getting her un-stuck & back into the 51 foot deep Craighill Channel is likely to be a *big production.*

6/ When you talk about ships aground, tides come up.
Could a high tide free the #EverForward?
As @mercoglianos pointed out, max tide is basically a foot there.
They'll surely work with it, but it's unlikely to re-float anything.
tideschart.com/United-States/…
Could a high tide free the #EverForward?
As @mercoglianos pointed out, max tide is basically a foot there.
They'll surely work with it, but it's unlikely to re-float anything.
tideschart.com/United-States/…

7/ Investigating what led #EverForward to plow into the shoal's mucky bottom may take a while.
Pilot error? Rudder malfunction?
Key info will live in the Voyage Data Recorder.
Fun fact: the VDR capsule is often mounted on the "monkey island" (deck directly above bridge)

Pilot error? Rudder malfunction?
Key info will live in the Voyage Data Recorder.
Fun fact: the VDR capsule is often mounted on the "monkey island" (deck directly above bridge)


8/ Meanwhile, just to make the storyline more interesting, the #EverGiven will soon arrive at the #SuezCanal.
Battling very strong headwinds at the moment.
We hope she has calmer winds during her transit.
No ghusts!


Battling very strong headwinds at the moment.
We hope she has calmer winds during her transit.
No ghusts!



9/ UPDATE: #EVERFORWARD still stuck in Chesapeake muck.
So I made an explainer video.
My first video... ever. Thanks to @mercoglianos for the inspiration.
So I made an explainer video.
My first video... ever. Thanks to @mercoglianos for the inspiration.
10/ The #EVERFORWARD is very high out of the water from bow (front) to stern (rear).
Means: she's grounded along her whole length.
A lot more boat to free from the muck than the #EverGiven.
Expect to see dredges.
Video: @JulioCesrChavez
Means: she's grounded along her whole length.
A lot more boat to free from the muck than the #EverGiven.
Expect to see dredges.
Video: @JulioCesrChavez
11/ NOON UPDATE: #EverForward still #everstuck.
Folks asking: is she a "sister" to the #EverGiven? a "cousin"?
She's a different class. Not sister. Maybe cousin.
Naming convention:
"Ever G___" = G Class (400m long: massive)
"Ever F___" = F Class (333.96 m: still v. large)


Folks asking: is she a "sister" to the #EverGiven? a "cousin"?
She's a different class. Not sister. Maybe cousin.
Naming convention:
"Ever G___" = G Class (400m long: massive)
"Ever F___" = F Class (333.96 m: still v. large)



12/ Speaking of #EverGreen's "Ever ___" naming convention.
At this point, it feels like naming a vessel Ever Lucky is just tempting fate.


At this point, it feels like naming a vessel Ever Lucky is just tempting fate.



• • •
Missing some Tweet in this thread? You can try to
force a refresh