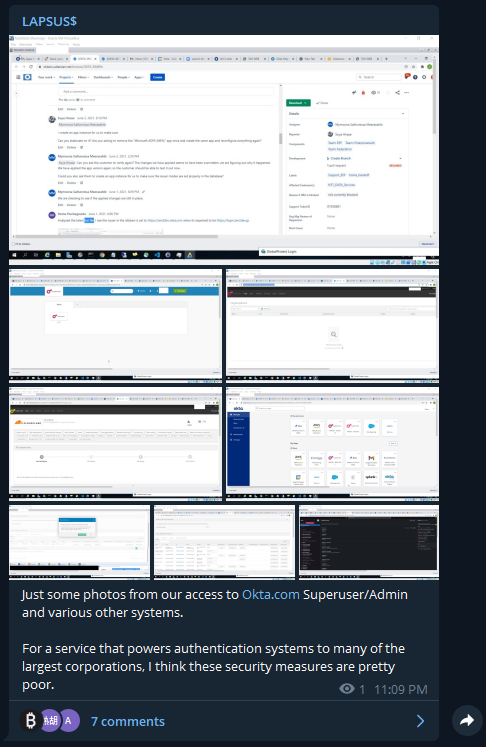
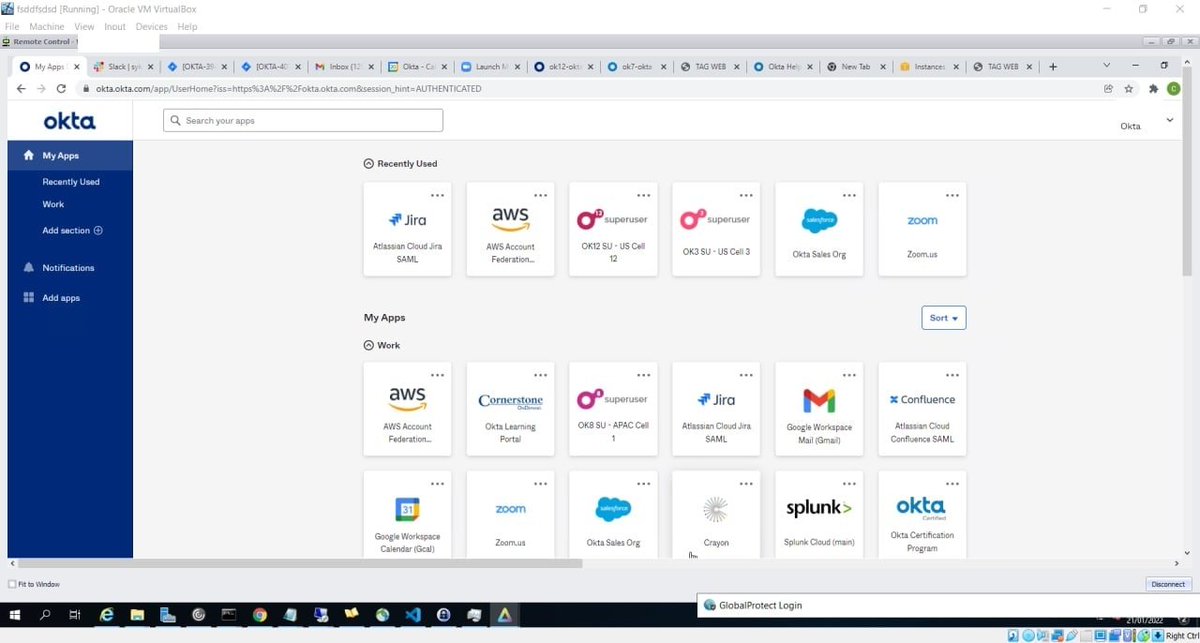
New documents for the Okta breach: I have obtained copies of the Mandiant report detailing the embarrassing Sitel/SYKES breach timeline and the methodology of the LAPSUS$ group. 1/N 

https://twitter.com/BillDemirkapi/status/1506107157124722690
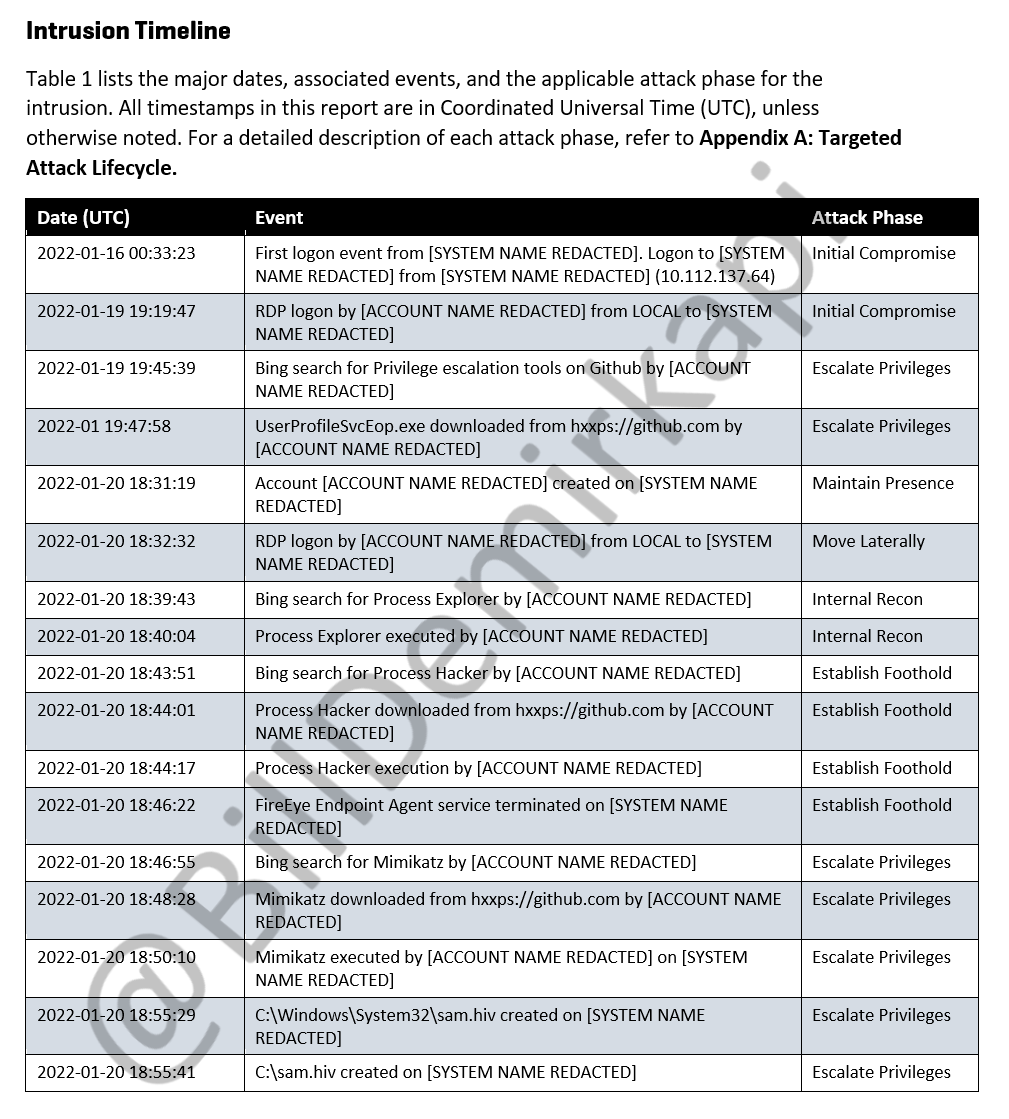
We can see how LAPSUS$ originally began investigating their compromised host on January 19th, 2022. With little regard for OPSEC, LAPSUS$ searched for a CVE-2021-34484 bypass on their compromised host and downloaded the pre-built version from GitHub. 2/N 
https://twitter.com/KLINIX5/status/1451558296872173577

LAPSUS$ used off-the-shelf tooling from GitHub for the majority of their attacks. After downloading Process Explorer and Process Hacker, LAPSUS$ bypassed the FireEye endpoint agent by simply terminating it! 3/N 

With the endpoint agent disabled, LAPSUS$ simply downloaded the official version of Mimikatz (a popular credential dumping utility) directly from its repository. 4/N 



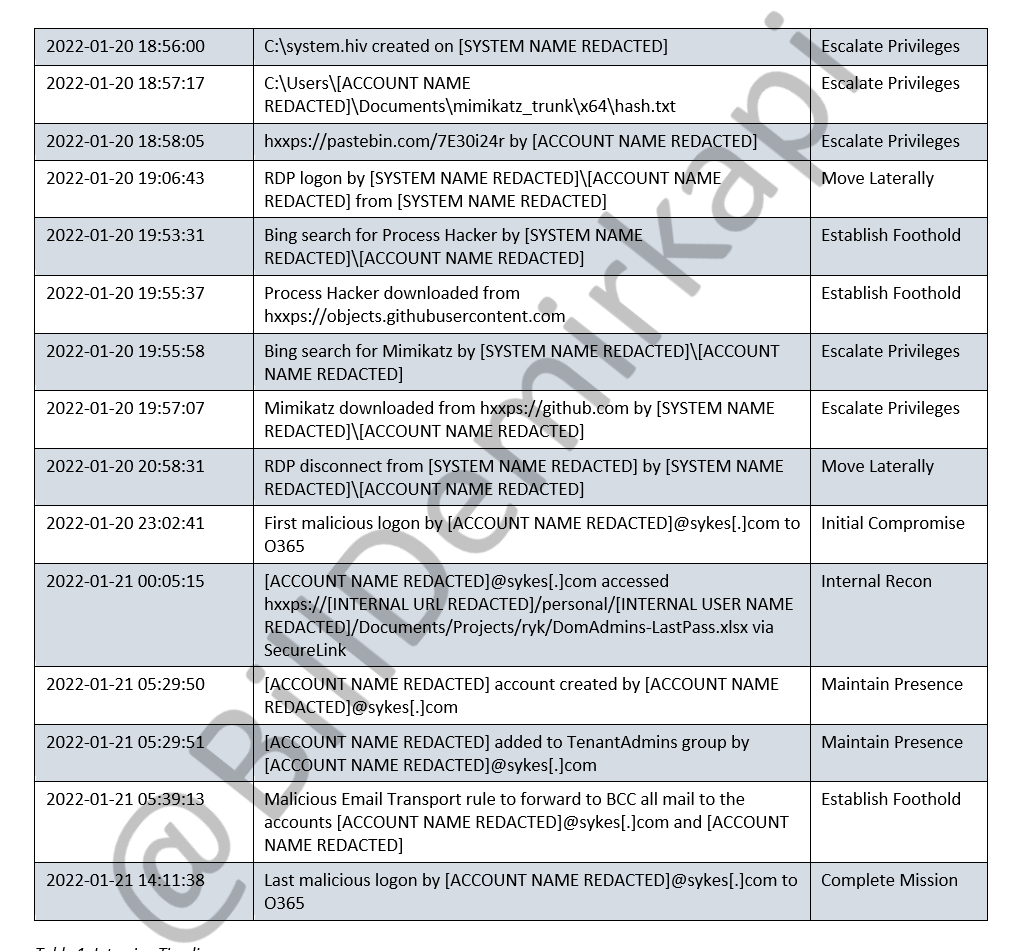
LAPSUS$ was able to create backdoor users in Sitel's environment after retrieving an Excel document conspicuously titled "DomAdmins-LastPass.xlsx" 🤦♂️. 5/N 

LAPSUS$ finished off their attack by creating a malicious "email transport rule" to forward all mail within Sitel's environment to their own accounts. 6/N docs.microsoft.com/en-us/exchange… 

My questions for Okta: You knew that the machine of one of your customer support members was compromised back in January. Why didn't you investigate it? Having the capability to detect an attack is useless if you aren't willing to respond. 7/N
Even when Okta received the Mandiant report in March explicitly detailing the attack, they continued to ignore the obvious signs that their environment was breached until LAPSUS$ shined a spotlight on their inaction. 8/N
For the Sitel Group: Why weren't your customers immediately informed upon the first sign of compromise? Why did your customers have to wait two months to even hear that you were breached? 9/N
Sitel Group serves many more customers than Okta. Often times, for support staff to perform their jobs, they need Administrative privileges into their customer's environment. The attack highlights the increased risk of outsourcing access to your org.'s internal environment. 10/N
Good questions to ask include: Who knows how your sub-processors handle their own security? As we saw in this case, Sitel didn't take the security of their environment very seriously. What can an attacker do if one of your sub-processors becomes compromised? 11/N
Anyone hiring? 😂 12/N
https://twitter.com/BillDemirkapi/status/1508820739968880640
Would like to clarify some misconceptions I've seen. No, this data is not attorney-client privileged. None of what I shared is from my organization and it was obtained entirely independently. I did not break any NDA/contract. 13/N
• • •
Missing some Tweet in this thread? You can try to
force a refresh