
How to get URL link on X (Twitter) App

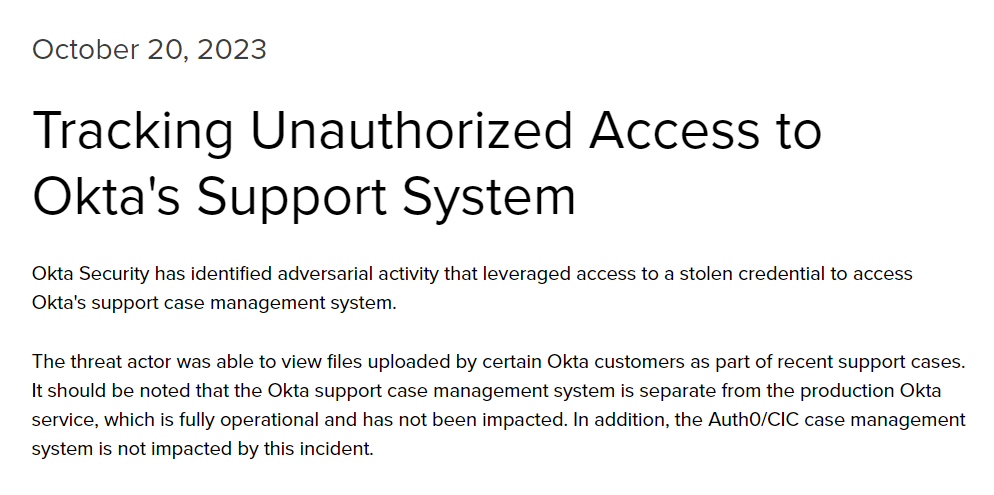
 𝗕𝗮𝗰𝗸𝗴𝗿𝗼𝘂𝗻𝗱: In March 2022, Okta experienced a breach of a third-party "customer support engineer", granting attacker's privileged access to customer environments. See the thread below for more details. 2/n
𝗕𝗮𝗰𝗸𝗴𝗿𝗼𝘂𝗻𝗱: In March 2022, Okta experienced a breach of a third-party "customer support engineer", granting attacker's privileged access to customer environments. See the thread below for more details. 2/n https://twitter.com/BillDemirkapi/status/1506107157124722690


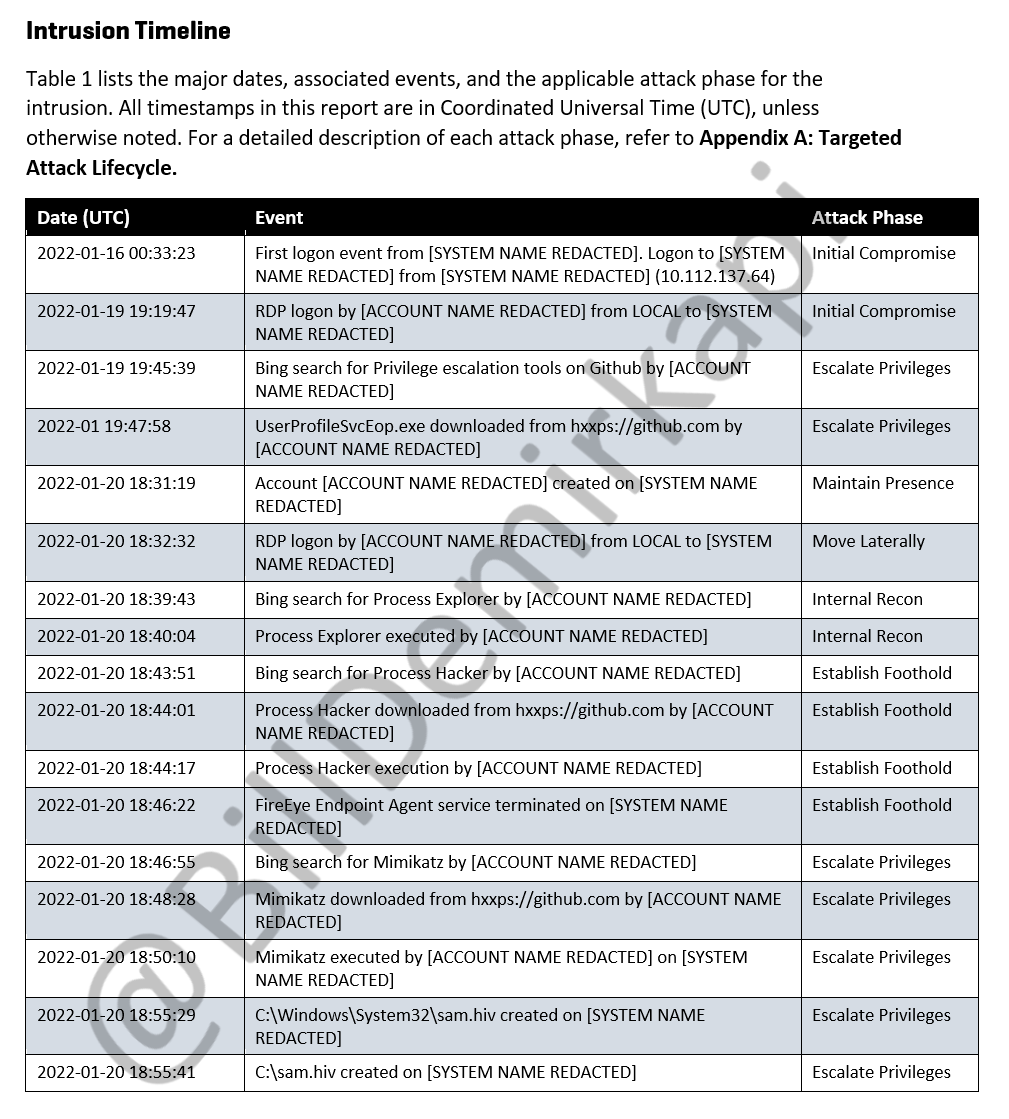
https://twitter.com/BillDemirkapi/status/1506107157124722690

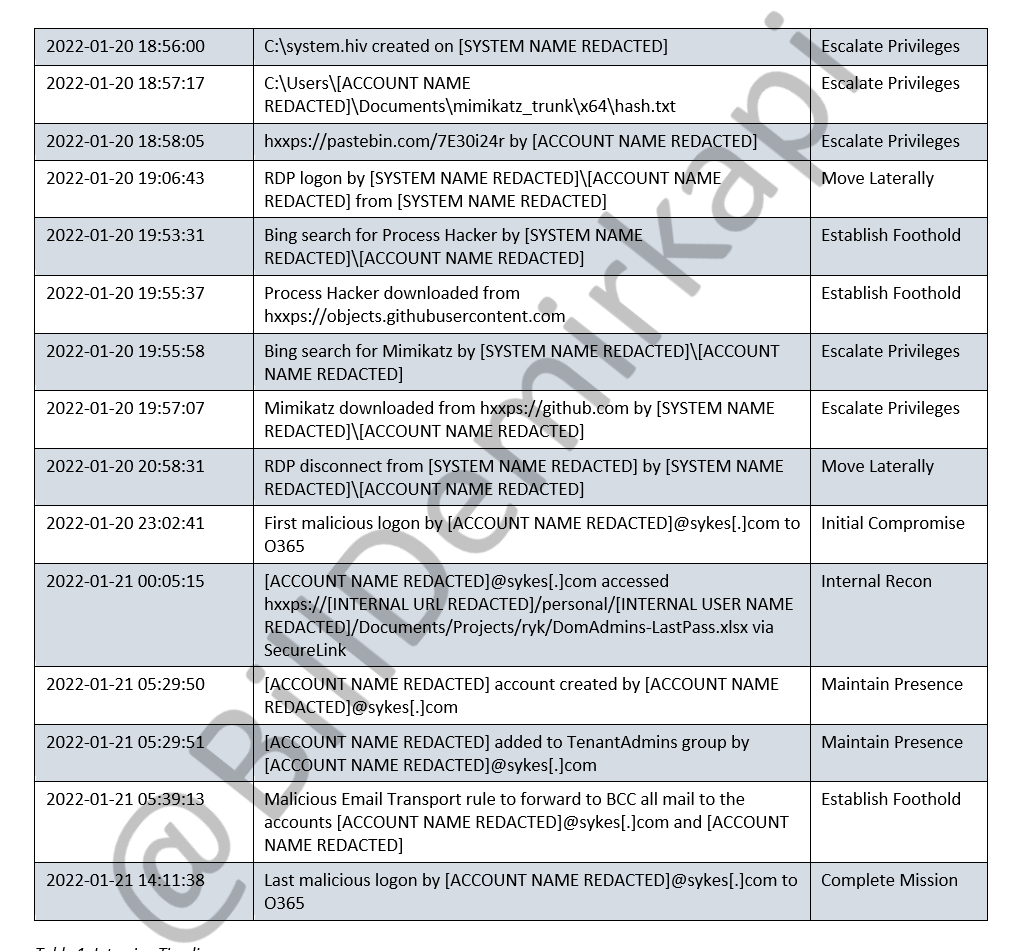 We can see how LAPSUS$ originally began investigating their compromised host on January 19th, 2022. With little regard for OPSEC, LAPSUS$ searched for a CVE-2021-34484 bypass on their compromised host and downloaded the pre-built version from GitHub. 2/N
We can see how LAPSUS$ originally began investigating their compromised host on January 19th, 2022. With little regard for OPSEC, LAPSUS$ searched for a CVE-2021-34484 bypass on their compromised host and downloaded the pre-built version from GitHub. 2/N https://twitter.com/KLINIX5/status/1451558296872173577

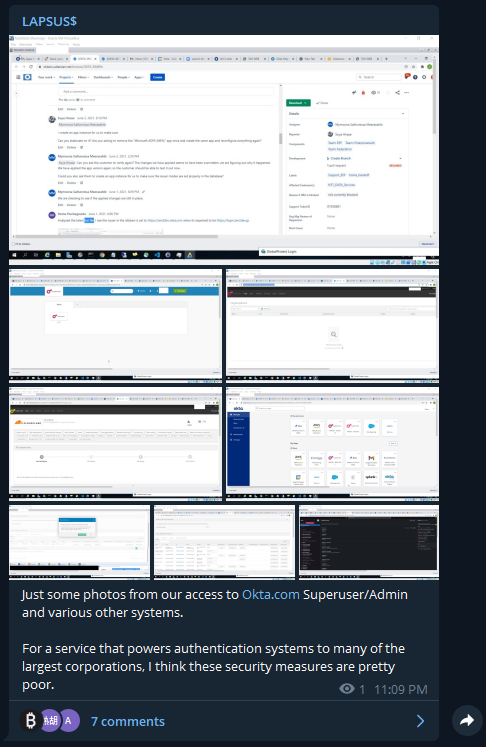


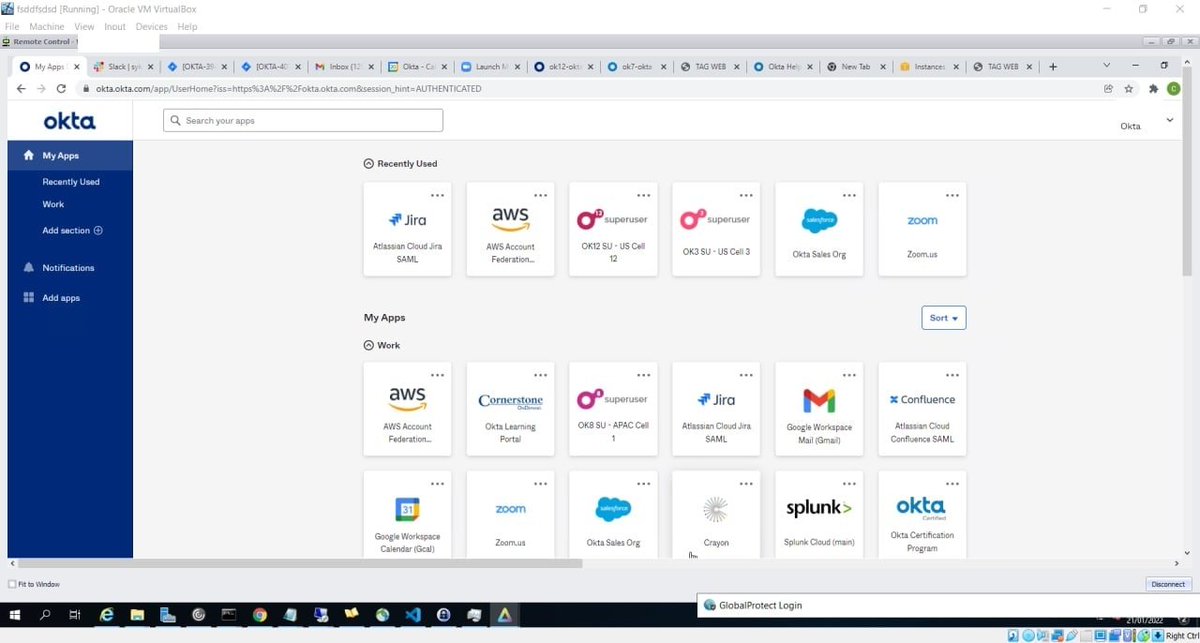
 The screenshots are very worrisome. In the pictures below, LAPSUS$ appears to have gotten access to the @Cloudflare tenant with the ability to reset employee passwords:
The screenshots are very worrisome. In the pictures below, LAPSUS$ appears to have gotten access to the @Cloudflare tenant with the ability to reset employee passwords: 


