So I've been a *mostly* happy @Ubiquiti customer, despite a few hiccups with their Cloud Key Gen 2+ model space heater.
And a security breach.
That I first found out about from @briankrebs.
Against whom Ubiquiti has apparently just filed a lawsuit.
And a security breach.
That I first found out about from @briankrebs.
Against whom Ubiquiti has apparently just filed a lawsuit.
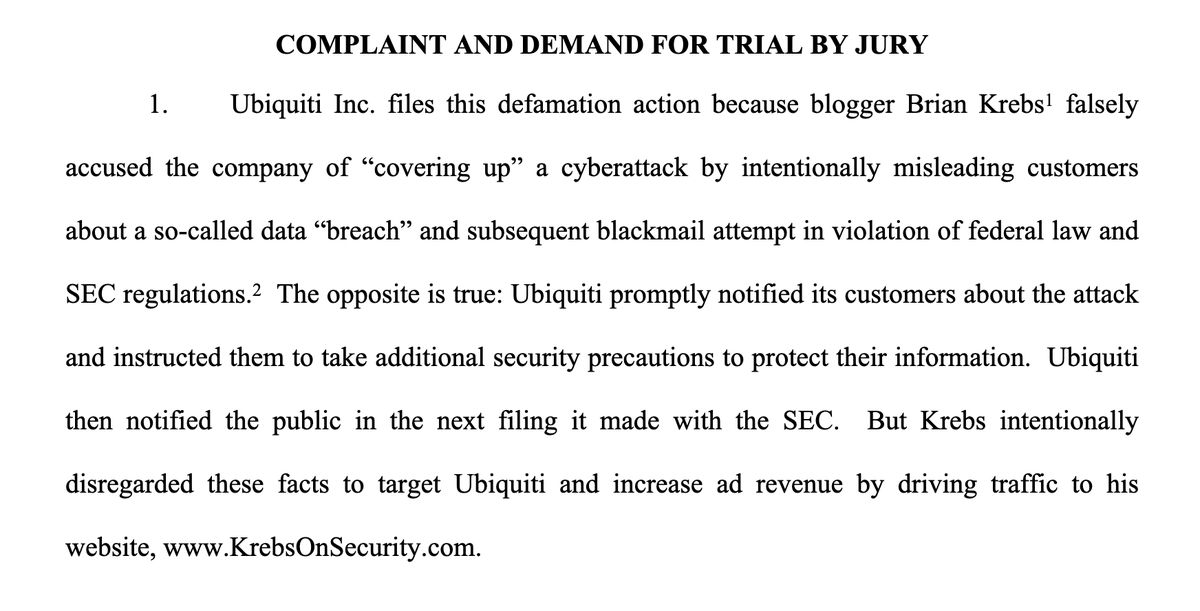
As a customer, this is the email that I got and didn't catch at the time. "Sooo, just FYI, there's been an attack against our systems with DB. Maybe consider changing your password?" Hugs and puppies, Ubiquiti. 

Yeah, the fact that credentials were not invalidated and immediately reset means that this section is complete bullshit.
It's an example of "Ubiquiti and other companies disregard(ing) their customers’ online security" because that's exactly what they did. That's not clickbait.
It's an example of "Ubiquiti and other companies disregard(ing) their customers’ online security" because that's exactly what they did. That's not clickbait.

That's funny, "we found a backdoor in our systems" in the filing is in no way the tone that your email struck, @Ubiquiti. What's the deal with that? 

Yeah, sorry. As one of those quaint things called "a paying customer," I assure you that the risk factor here is not your competition figuring out the secret to making space heaters reboot. 

Uh.... you *did* downplay the severity here. Whether it was an insider or an outsider isn't really the relevant part of the story, so much as "you failed to secure the data that I had entrusted to you." 

Oh come on @ubiquiti. Even Krebs's story and the claims therein didn't shine as much light on your failings as your own lawsuit filing is doing. My god... 

Welp @briankrebs is getting pride of place in my RSS reader for the next decade based upon this.
And at this point we've only seen the suit. Krebs hasn't filed a response yet!
And at this point we've only seen the suit. Krebs hasn't filed a response yet!

Ubiquiti seems awfully convinced that "it wasn't an outside attacker, we just suck at detecting insider threats" is a far stronger position than it is here in reality.
I don't care who pushed you or what you were carrying; everyone saw you eat shit down the stairs.
I don't care who pushed you or what you were carrying; everyone saw you eat shit down the stairs.
The meat of the accusation is that the inside attacker was @briankrebs's source. I really fail to see the problem if that's true; that guy kinda seems like one of the more competent people running the store over at @Ubiquiti right about now.
Think to all of the books you've read, the movies you've seen.
When someone sues a journalist, how often are they presented as "the good guys?"
It appears @ubiquiti is represented by @clarelockellp, who proudly boasts about... suing journalists. Genius PR move, folks.
When someone sues a journalist, how often are they presented as "the good guys?"
It appears @ubiquiti is represented by @clarelockellp, who proudly boasts about... suing journalists. Genius PR move, folks.

I eagerly await being added to the lawsuit because I have enough Twitter followers to look like media if you squint hard enough, and I too have said things about you on the internet that are likely to cause you some grief, @ubiquiti.
Be sure you get the rest of the kids saying mean things about you on the playground too, you poor delicate $18B publicly traded company.
"Do you think we can sue @quinnypig into shutting up?" wonders @Ubiquiti.
"Let me put it this way,” begins someone a bit more up to speed on my shenanigans, with the unmistakable tone of someone teeing up a long drive down the fairway of hopelessness.
"Let me put it this way,” begins someone a bit more up to speed on my shenanigans, with the unmistakable tone of someone teeing up a long drive down the fairway of hopelessness.
“He made an insulting video about the founder of the world's largest law firm (Oracle / ‘Kirkland Ellison’).
Then he got the @nytimes to print that 'nobody likes said founder.'
And *THEN* he got that company to *PAY HIM FOR ADVICE*.”
Then he got the @nytimes to print that 'nobody likes said founder.'
And *THEN* he got that company to *PAY HIM FOR ADVICE*.”
I mean, there’s a few reasons that my @LastWeekinAWS newsletter (to which you should subscribe!) has 30k subscribers, and one of them is because it’s fairly rare to find cloud-related news roundups that are entertainingly insulting to giant companies.
• • •
Missing some Tweet in this thread? You can try to
force a refresh