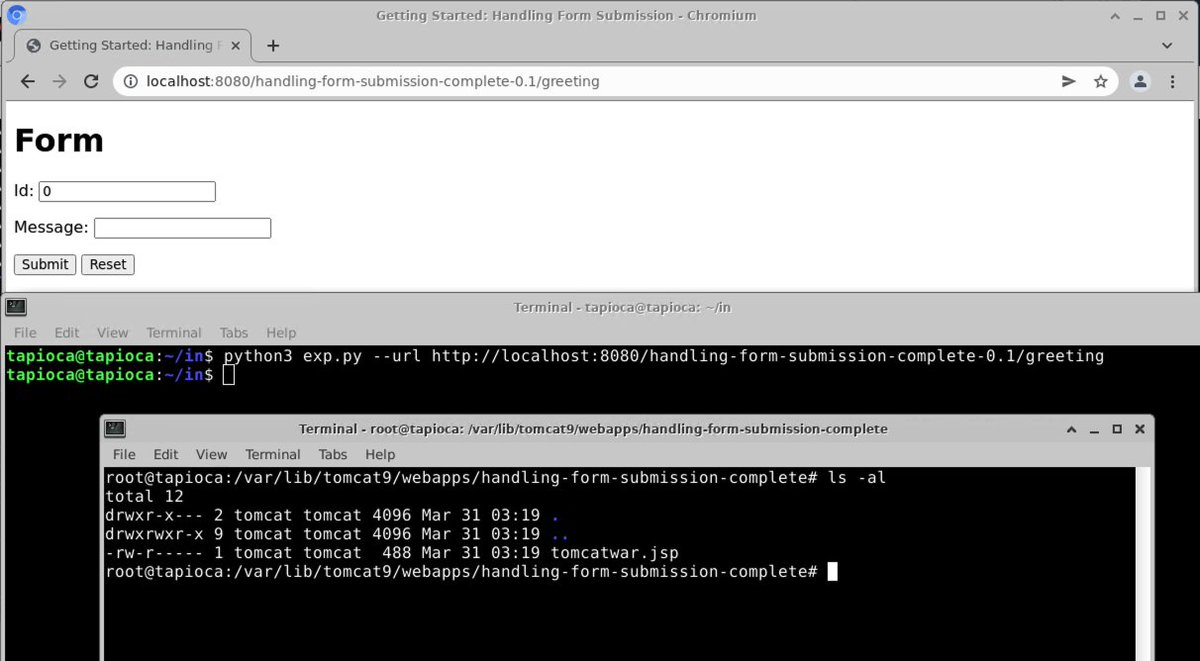
OK, where are we with Spring stuff?
1) CVE-2022-22963 is a thing, and it affects Spring Cloud Connector. It's RCE, so the CVSS score of 5.4 seems way off.
2) Spring4Shell / SpringShell, invented by Cyber Kendra, isn't a Spring vulnerability at all.
Does that sound about right?


1) CVE-2022-22963 is a thing, and it affects Spring Cloud Connector. It's RCE, so the CVSS score of 5.4 seems way off.
2) Spring4Shell / SpringShell, invented by Cyber Kendra, isn't a Spring vulnerability at all.
Does that sound about right?



And just for the Twitter record, @VMwareTanzu assigned CVE-2022-22963 a CVSS score of 5.4
Yet it's an unauthenticated RCE vulnerability.
Which in my mind puts it closer to a 9.8.
Yet it's an unauthenticated RCE vulnerability.
Which in my mind puts it closer to a 9.8.

And to tie up this thread, I've confirmed that #SpringShell / #Spring4Shell *IS* indeed a thing.
This wasn't immediately obvious because of Cyber Kendra linking SpringShell to a commit for a COMPLETELY UNRELATED issue that is NOT A VULNERABILITY.
<sigh>
This wasn't immediately obvious because of Cyber Kendra linking SpringShell to a commit for a COMPLETELY UNRELATED issue that is NOT A VULNERABILITY.
<sigh>
https://twitter.com/wdormann/status/1509372145394200579
• • •
Missing some Tweet in this thread? You can try to
force a refresh