
I play with vulnerabilities and exploits. I used to be here on Twitter but now I'm here:
@wdormann@infosec.exchange
https://t.co/hXggdAVkSQ
3 subscribers
How to get URL link on X (Twitter) App

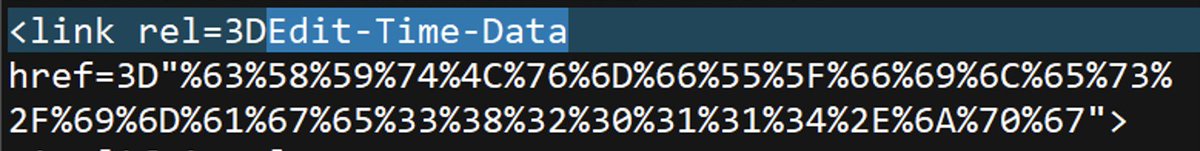
https://twitter.com/jpcert_en/status/1696056414148645326Note that the normal MotW-enabled Macro protections remain in place. (Macros on files from the internet aren't allowed these days)






 Similarly, the malicious ffmpeg.dll will have the wide string "d3dcompiler_47.dll" in it, whereas the legit ffmpeg.dll does not.
Similarly, the malicious ffmpeg.dll will have the wide string "d3dcompiler_47.dll" in it, whereas the legit ffmpeg.dll does not.

 This may be Thunderbird-specific, as Apple Mail seems to work fine.
This may be Thunderbird-specific, as Apple Mail seems to work fine. 

 And just to clarify, even just taking the simplest sort of calendar invite MSG from MsgKit and attempting to save it as anything else (.ics, .vcs) w/ Outlook results in the same sort of error message. No SMTP / Exchange transport involved.
And just to clarify, even just taking the simplest sort of calendar invite MSG from MsgKit and attempting to save it as anything else (.ics, .vcs) w/ Outlook results in the same sort of error message. No SMTP / Exchange transport involved.


 Ok, yeah, thx to @jduck TNEF does indeed include compressed RTF data in it.
Ok, yeah, thx to @jduck TNEF does indeed include compressed RTF data in it.

https://twitter.com/NFT_GOD/status/1614442010773004288

 This is probably crazy, but hear me out...
This is probably crazy, but hear me out...
https://twitter.com/sadreck/status/1585977258367483904



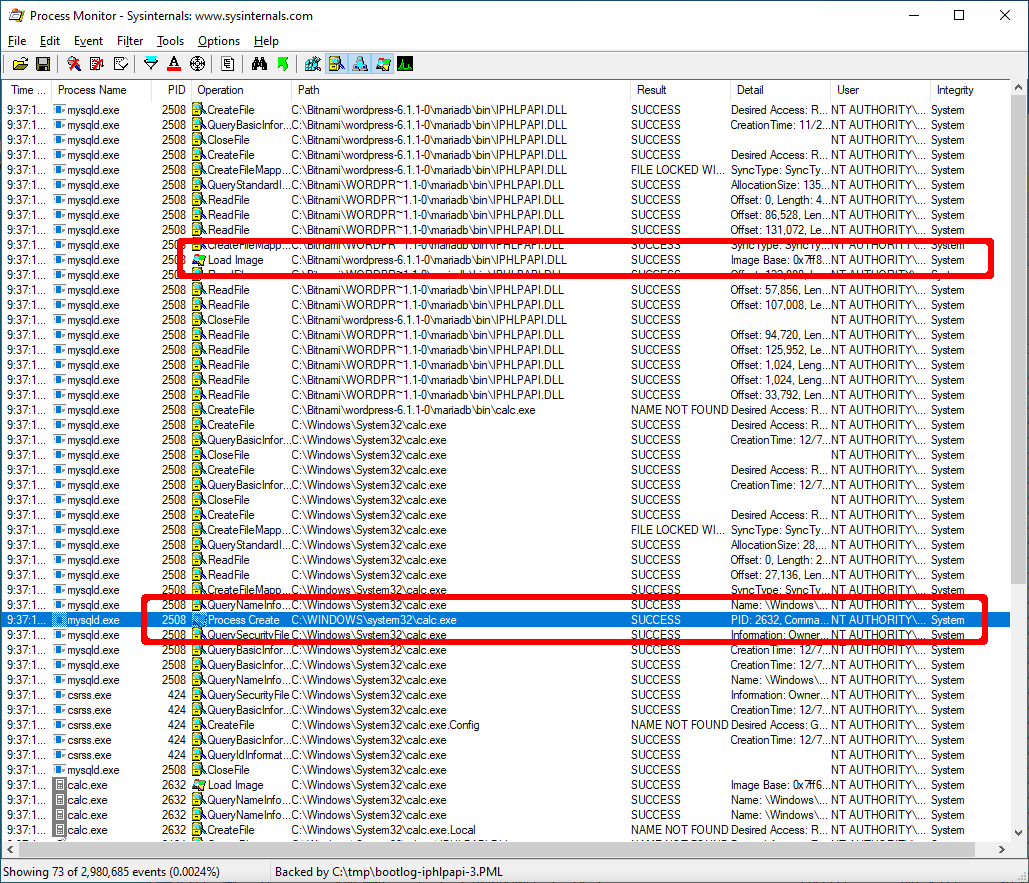 And now that I think about it, programmatic parsing of PML files and checking of filesystem ACLs can make the whole process of finding privilege escalation vulnerabilities on Windows require fewer brain cells.
And now that I think about it, programmatic parsing of PML files and checking of filesystem ACLs can make the whole process of finding privilege escalation vulnerabilities on Windows require fewer brain cells.

https://twitter.com/wdormann/status/1582458287915573249Can we do the same trick with a signed EXE file?

https://twitter.com/wdormann/status/1570520940811030528
 The GUI for "Microsoft Vulnerable Driver Blocklist" isn't present unless you're running the "Dev Channel" Insider Preview for Windows 11.
The GUI for "Microsoft Vulnerable Driver Blocklist" isn't present unless you're running the "Dev Channel" Insider Preview for Windows 11.https://twitter.com/wdormann/status/1570123694554374144


 Let's take Microsoft 365, which I'm confident that several people use.
Let's take Microsoft 365, which I'm confident that several people use.

https://twitter.com/wdormann/status/1544416883419619333For what it's worth, I downloaded ~100 recent ZIP samples from VirusTotal that had a positive detection and a LNK in them.

https://twitter.com/campuscodi/status/1544344477048770560

 The ISO in question here takes advantage of several default behaviors:
The ISO in question here takes advantage of several default behaviors:

https://twitter.com/GossiTheDog/status/1531011653235523586

 The important difference is that this variant still works.
The important difference is that this variant still works. 
https://twitter.com/dec0ne/status/1518516602458759168
 If "Domain Controller: LDAP server signing requirements" is set to "Require signing", this appears to block the exploit at the stage of relaying kerberos authentication to LDAP.
If "Domain Controller: LDAP server signing requirements" is set to "Require signing", this appears to block the exploit at the stage of relaying kerberos authentication to LDAP. 


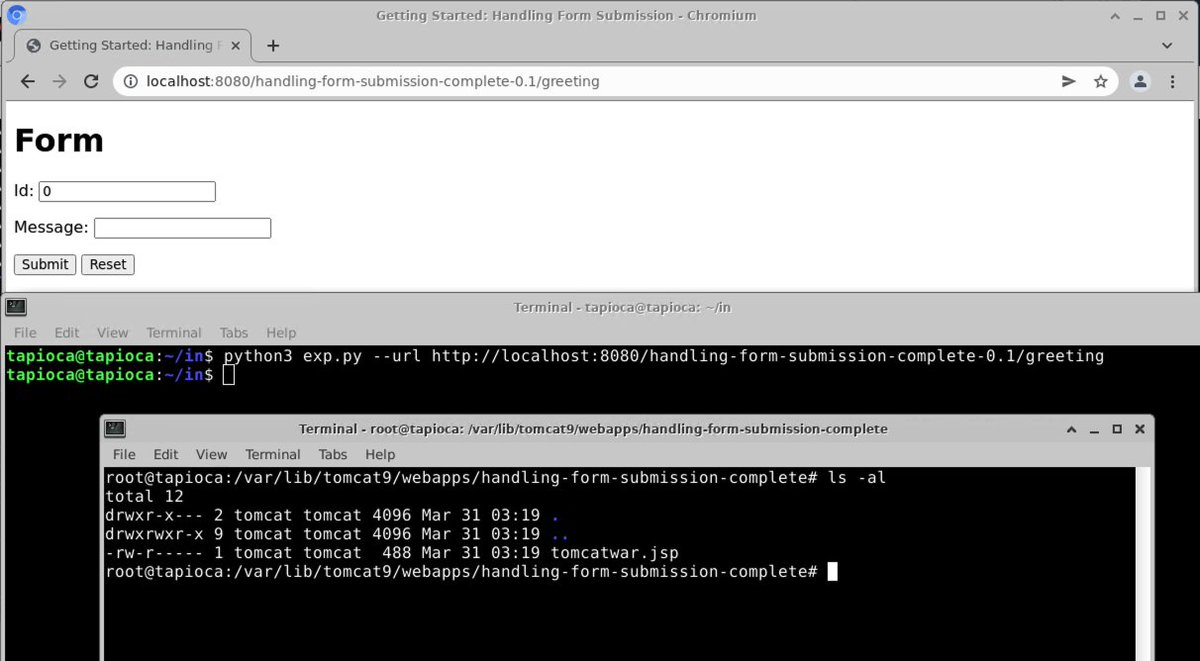
https://twitter.com/th3_protoCOL/status/1509345839134609408


 Ways that Cyber Kendra made this worse for everyone:
Ways that Cyber Kendra made this worse for everyone:




 And just for the Twitter record, @VMwareTanzu assigned CVE-2022-22963 a CVSS score of 5.4
And just for the Twitter record, @VMwareTanzu assigned CVE-2022-22963 a CVSS score of 5.4
https://twitter.com/mrd0x/status/1503801717414105089But wait!

https://twitter.com/_dirkjan/status/1496201867117928453

 Nothing more than a system on the same (V)LAN as a domain-joined host is required. No password knowledge necessary.
Nothing more than a system on the same (V)LAN as a domain-joined host is required. No password knowledge necessary.


 How did the CVE entry get to be wrong?
How did the CVE entry get to be wrong?