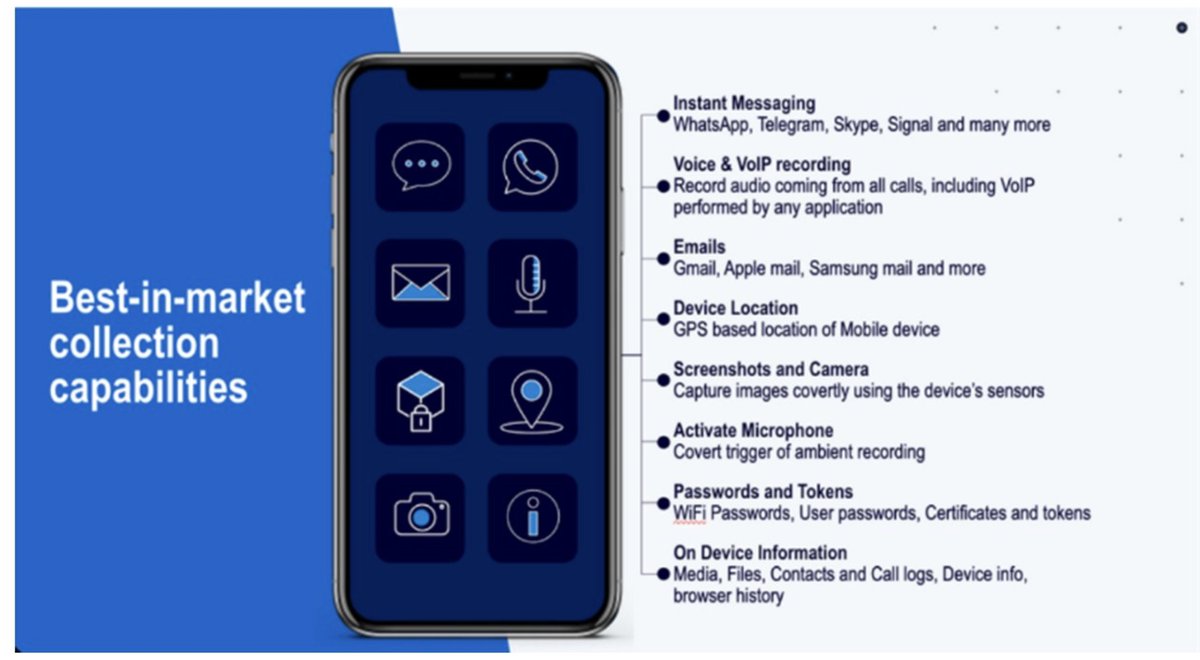
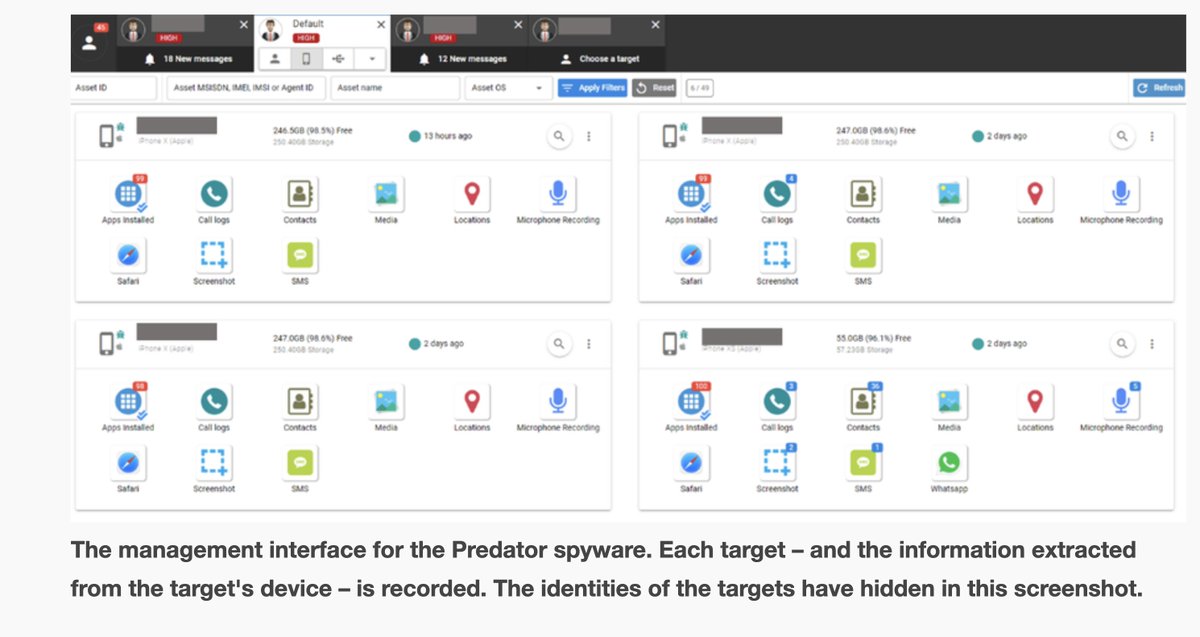
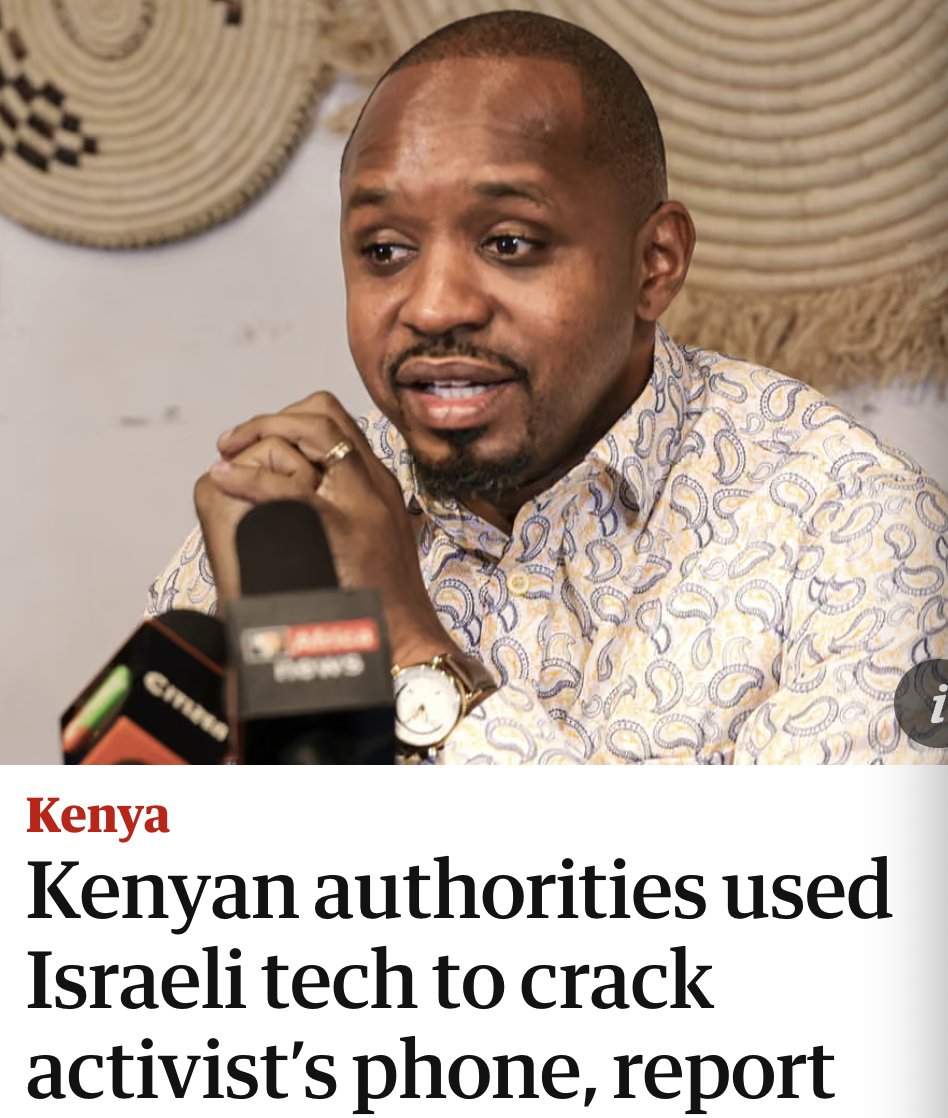
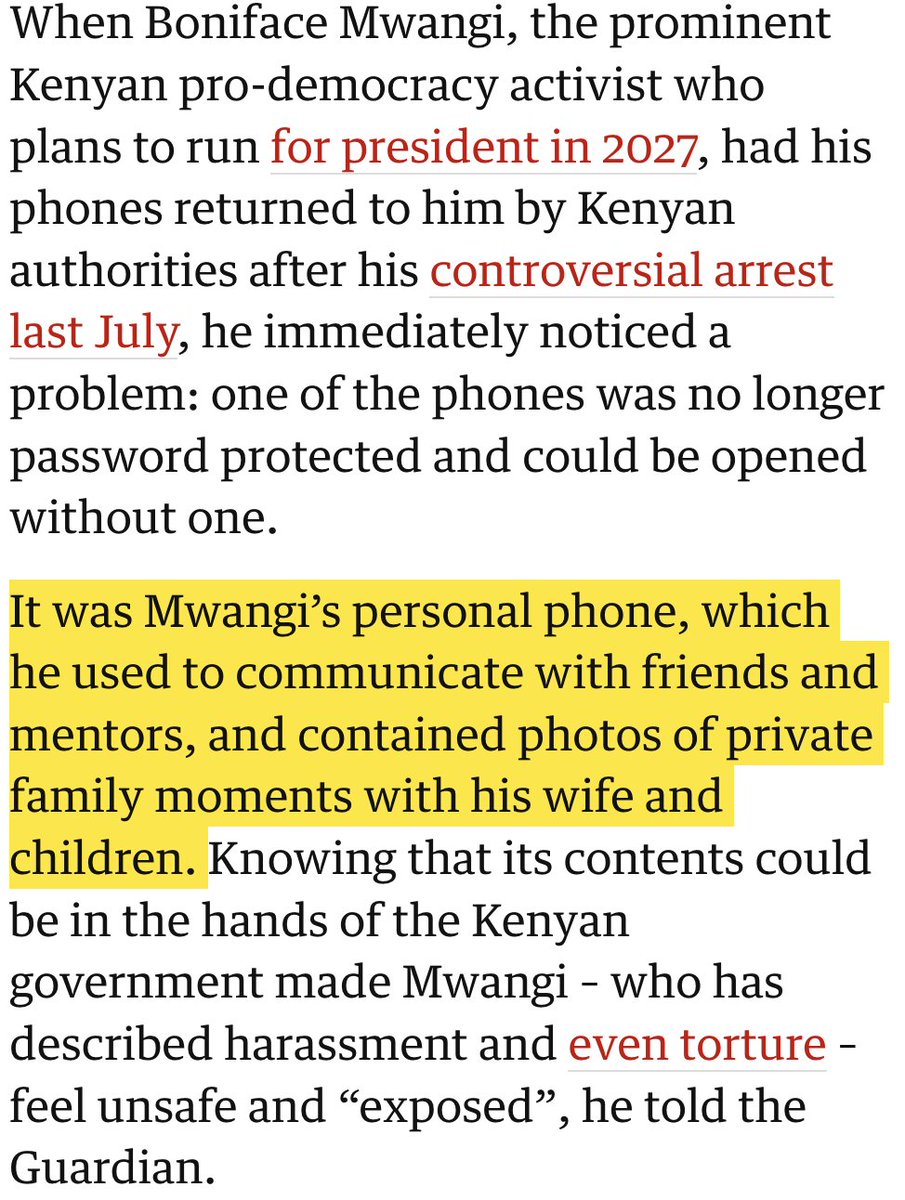
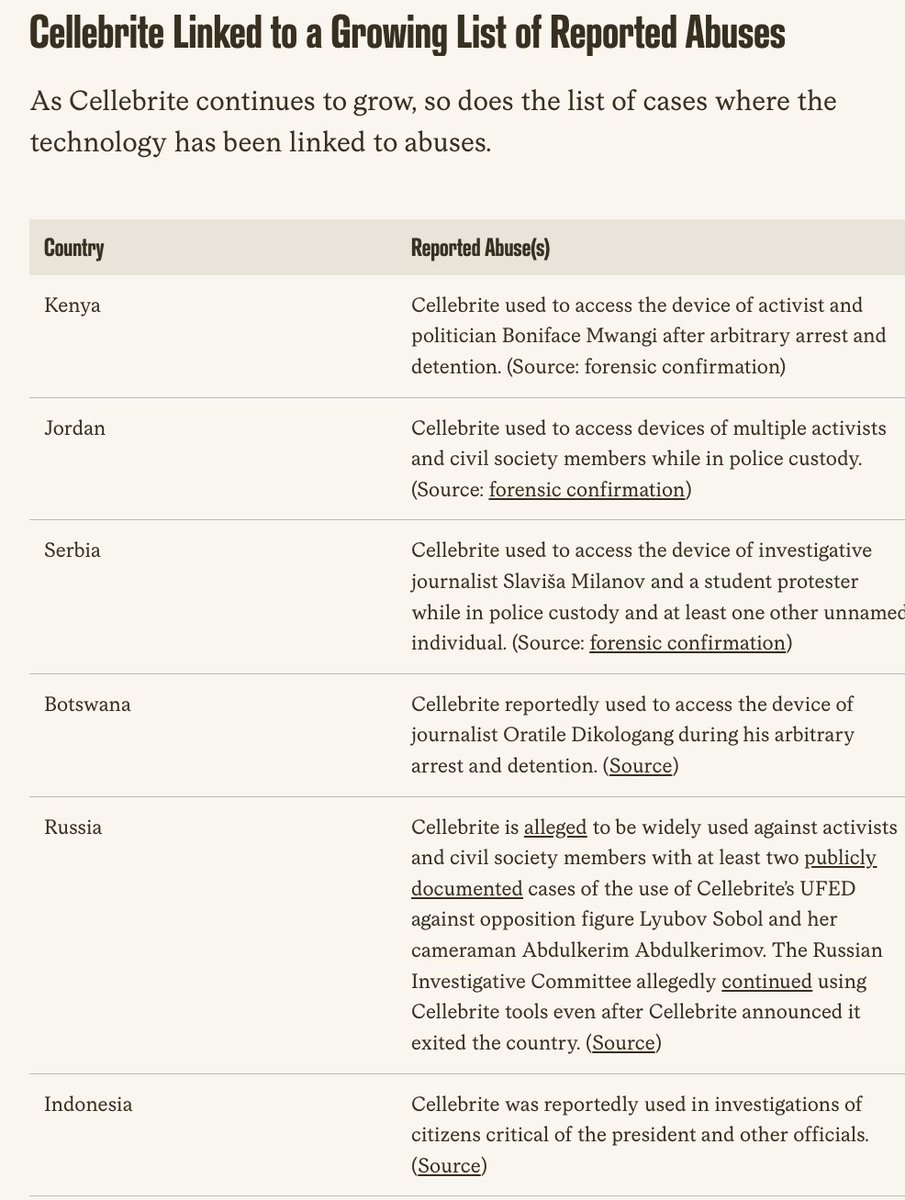
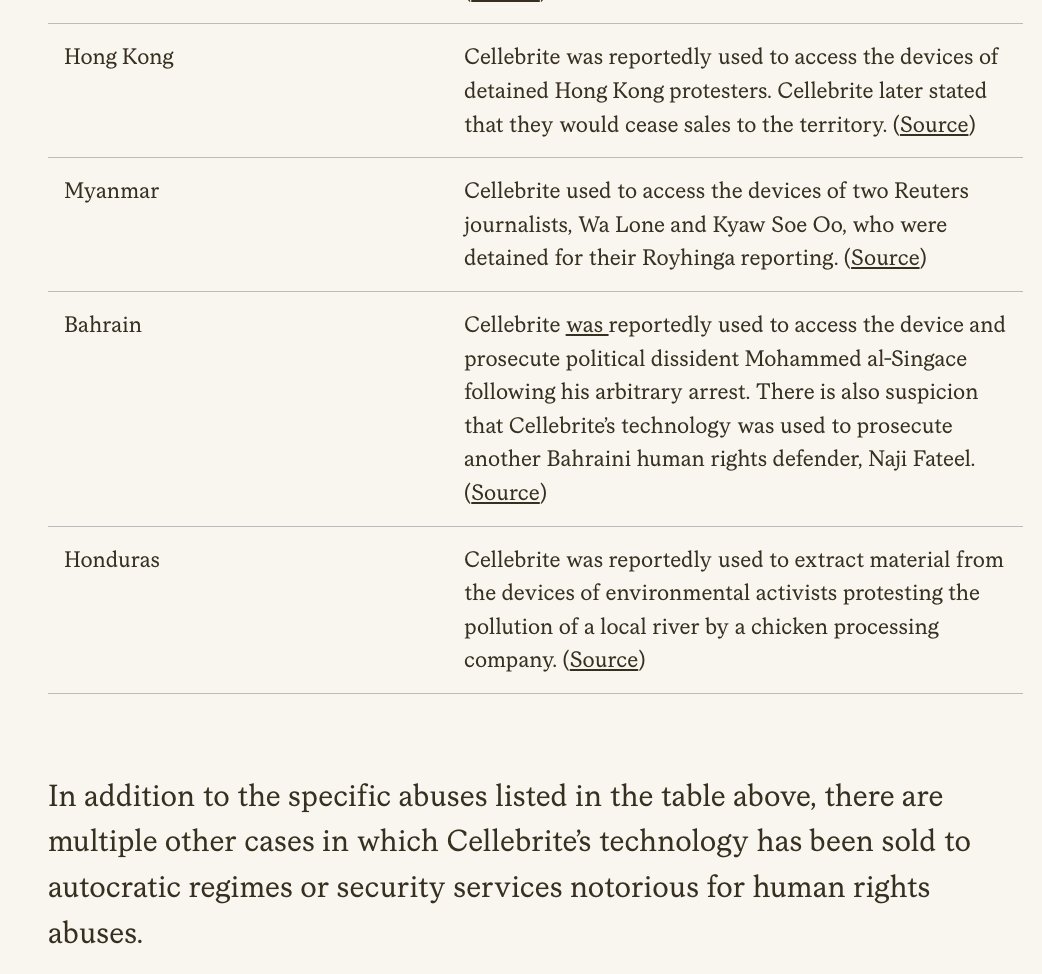
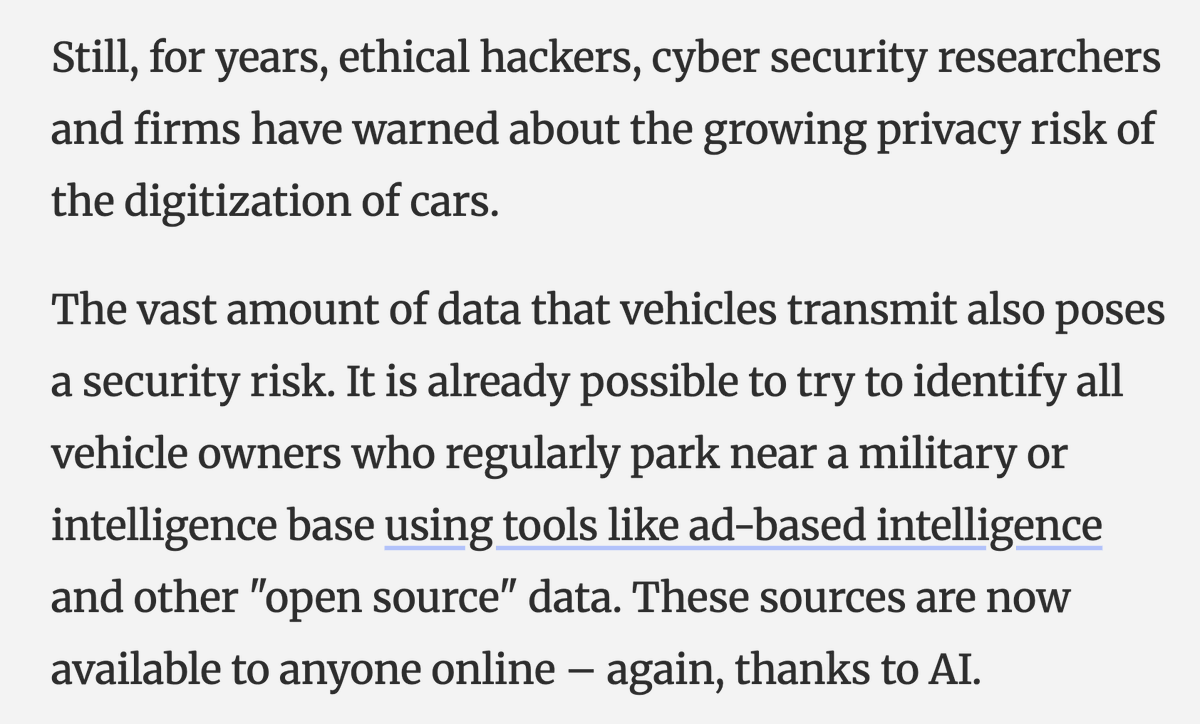
🚨MAJOR NEW INVESTIGATION: #CatalanGate state-run hacking operation.
Stunning range of #Pegasus & #Candiru infections in the EU.
Many political & civil society targets got infected. Multiple 🇪🇺 MEPs.
THREAD 1/
catalonia.citizenlab.ca
Stunning range of #Pegasus & #Candiru infections in the EU.
Many political & civil society targets got infected. Multiple 🇪🇺 MEPs.
THREAD 1/
catalonia.citizenlab.ca
2/ A jaw dropping list of people were targeted in #CatalanGate
Let's take the 🇪🇺 European Parliament.
*Every pro-independence MEP* was targeted directly or w/relational targeting:
-@toni_comin
-@DianaRibaGiner
-@jordisolef
-@ClaraPonsati
-@KRLS

Let's take the 🇪🇺 European Parliament.
*Every pro-independence MEP* was targeted directly or w/relational targeting:
-@toni_comin
-@DianaRibaGiner
-@jordisolef
-@ClaraPonsati
-@KRLS


3/ Catalan civil society was extensively targeted.
From the leadership of major civic organizations like @omnium & @assemblea_int...to open source developers working on digital voting.
Mostly #Pegasus, but #Candiru spyware, too.
Link: citizenlab.ca/2022/04/catala…



From the leadership of major civic organizations like @omnium & @assemblea_int...to open source developers working on digital voting.
Mostly #Pegasus, but #Candiru spyware, too.
Link: citizenlab.ca/2022/04/catala…


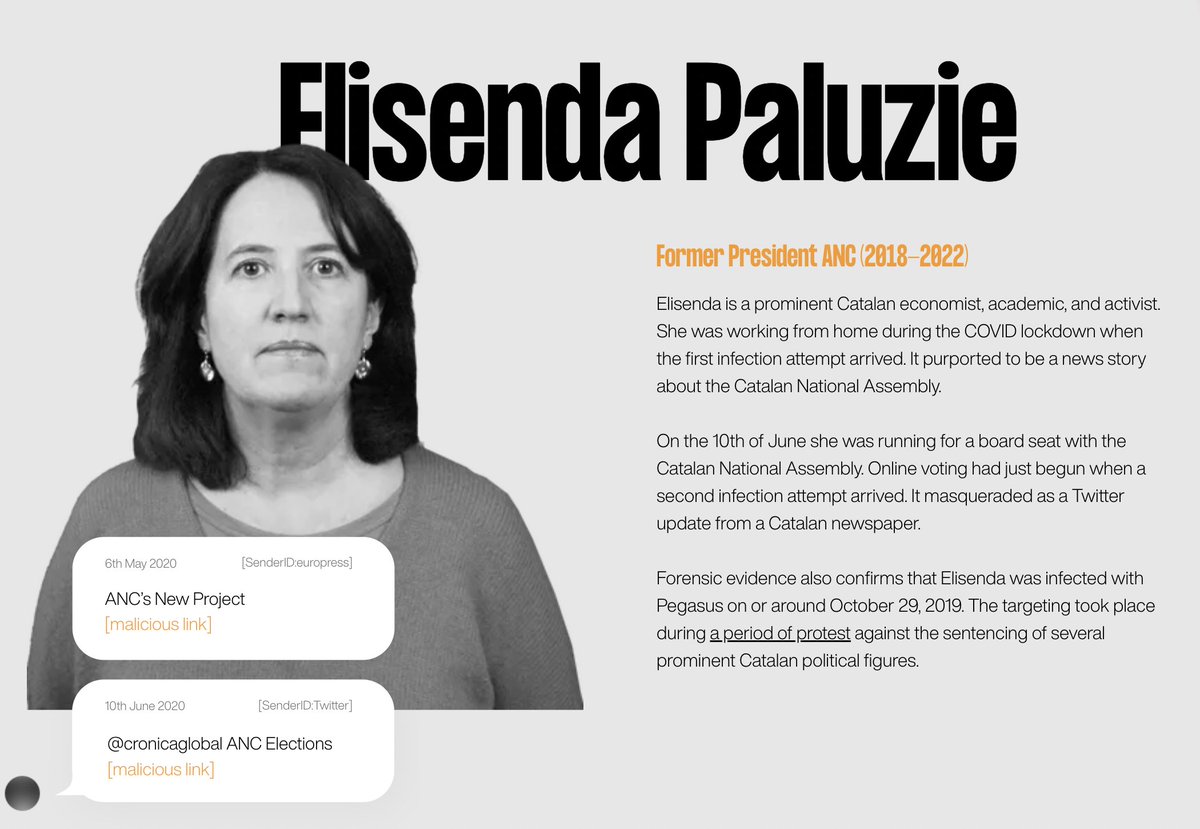
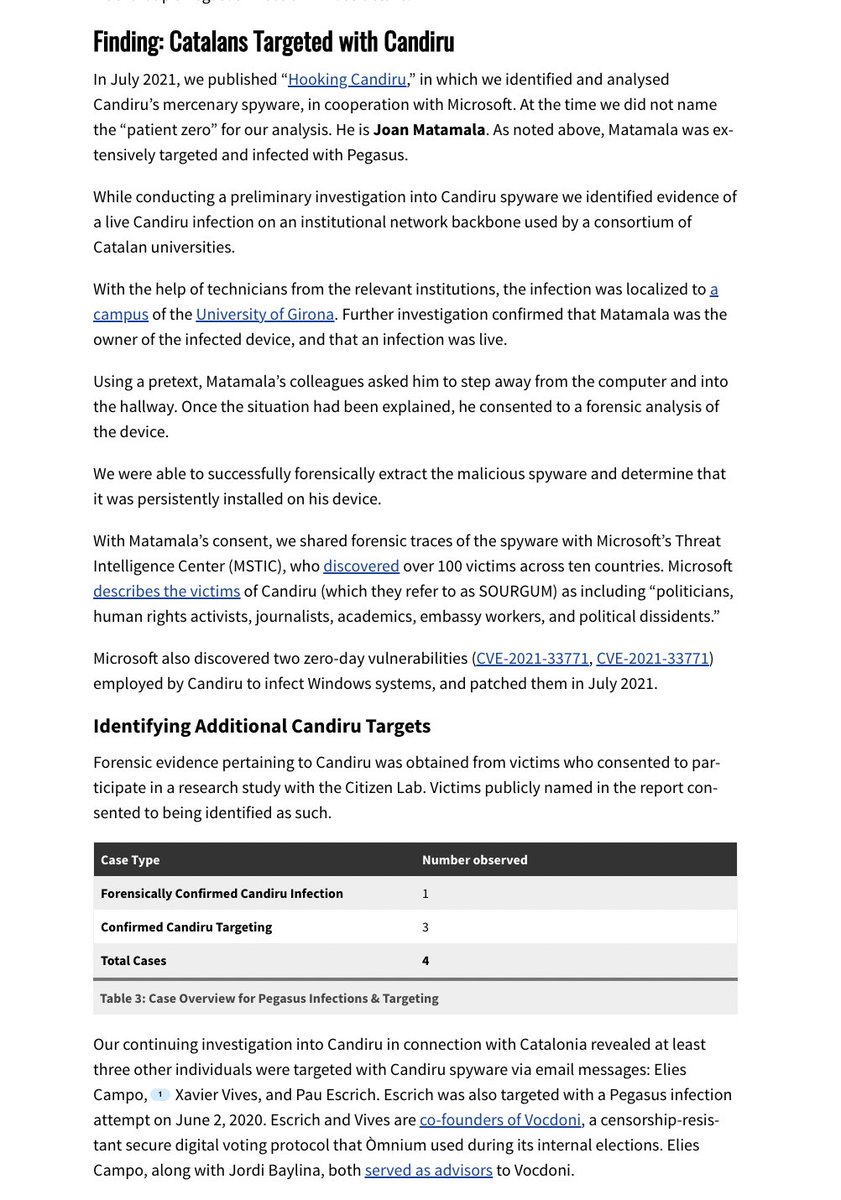
4/ So many Catalan politicians were targeted with #Pegasus between 2017-2020.
Like every current/former President of Catalonia since 2010.
Catalan's Parliamentary leadership, legislators, etc. etc. #CatalanGate



Like every current/former President of Catalonia since 2010.
Catalan's Parliamentary leadership, legislators, etc. etc. #CatalanGate




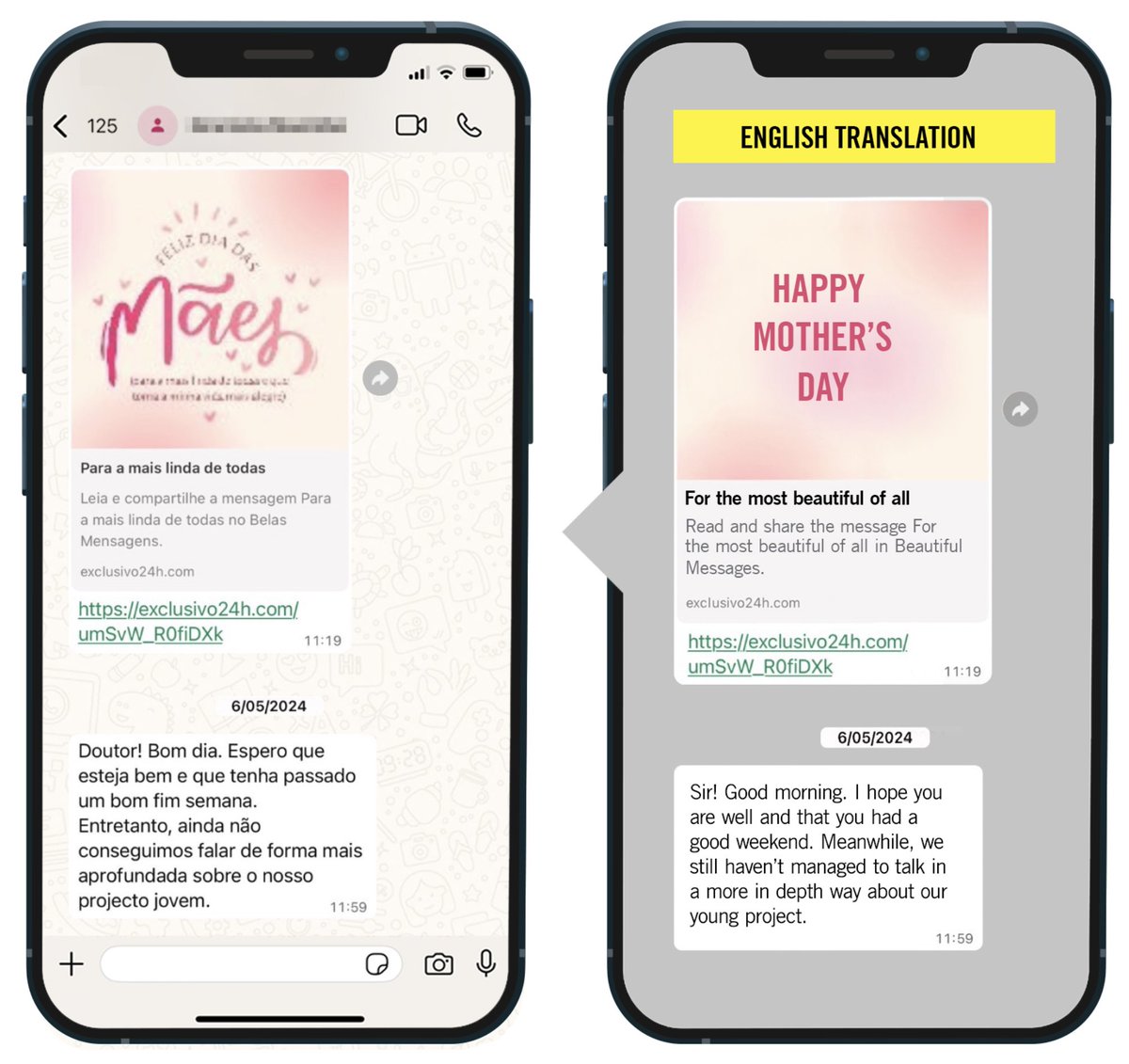
5/The #Pegasus hacking was via a mix of zero-click vulnerabilities & SMS infection attempts.
Texts were *very* well informed.
Like this one: @jbaylina was sent a mobile boarding pass link...for a @FlySWISS flight he'd booked.
Texts were *very* well informed.
Like this one: @jbaylina was sent a mobile boarding pass link...for a @FlySWISS flight he'd booked.

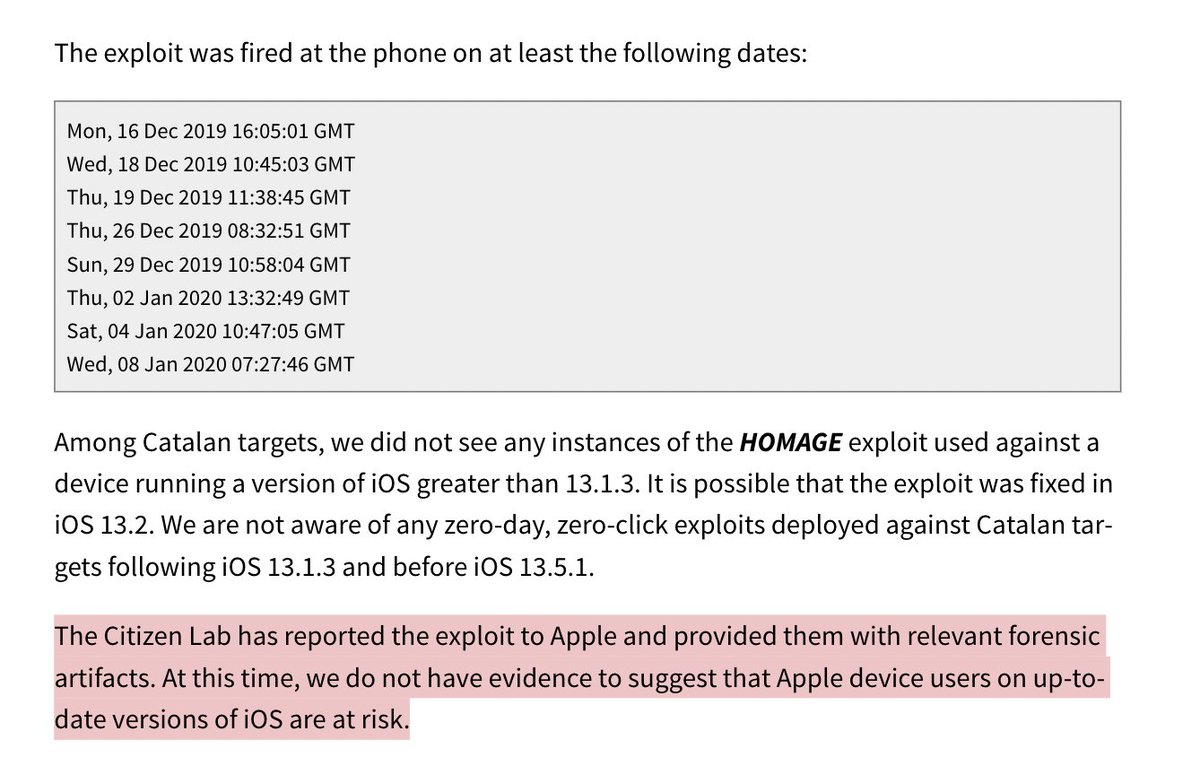
6/ WILD: while doing #Pegasus forensics, at the 11th hour on this project, @billmarczak actually discovered another NSO iOS Zero-Click 0day!
We call it #Homage
We think it stopped working by 13.2 so if you are updated, you're likely OK.
We notified @apple.

We call it #Homage
We think it stopped working by 13.2 so if you are updated, you're likely OK.
We notified @apple.

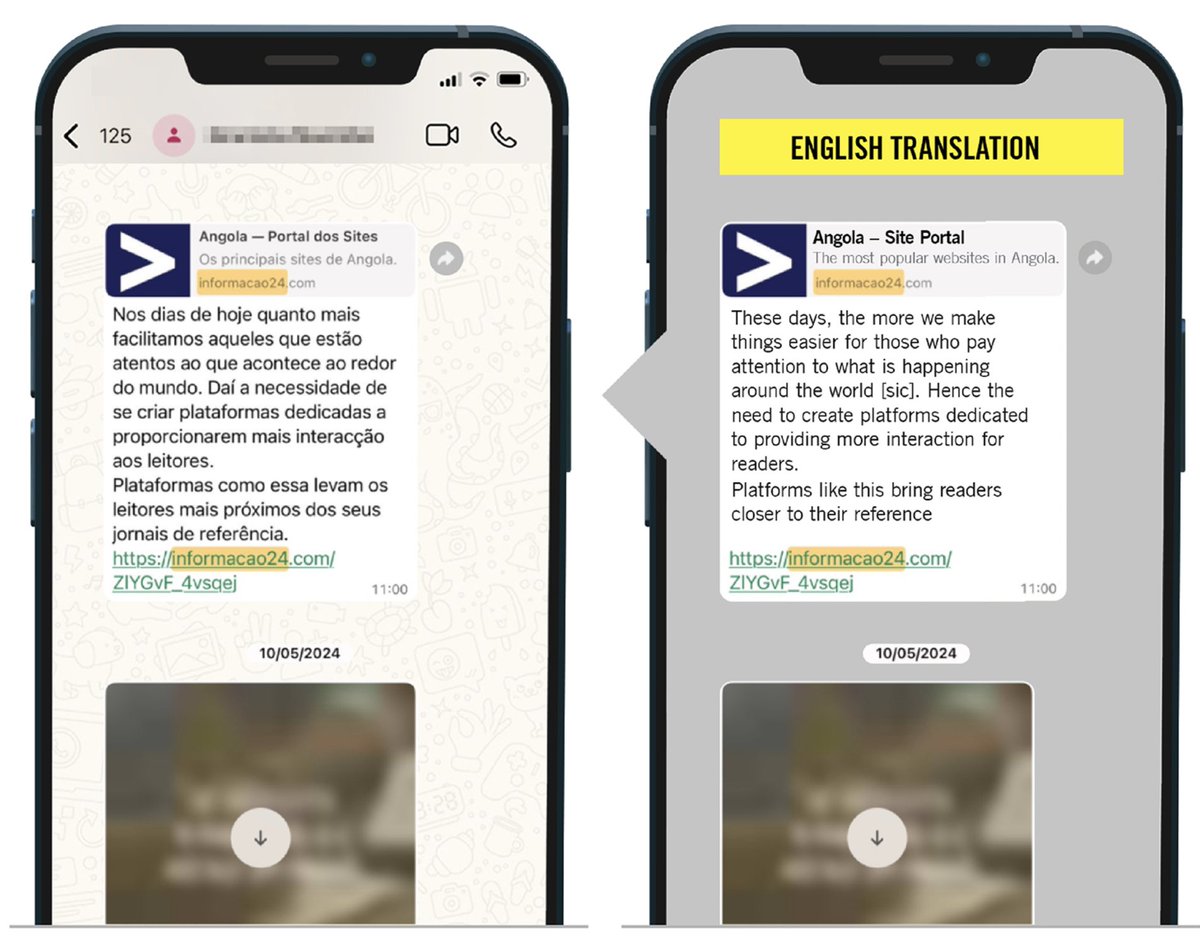
7/ The #Candiru targeting that we saw was via email. Again, often super personalized.
They impersonated official COVID communications from Spanish gov, notifications from biz registries, etc.
Sometimes Candiru & #Pegasus targeting themes overlapped.

They impersonated official COVID communications from Spanish gov, notifications from biz registries, etc.
Sometimes Candiru & #Pegasus targeting themes overlapped.


8/ Craziest story? Victim working on a live #Candiru infected computer had to be persuaded to step into the hallway using a ruse so we could explain the situation away from it's microphones...
Material was shared w/@MsftSecIntel which led to 1.4 billion devices getting patched.
Material was shared w/@MsftSecIntel which led to 1.4 billion devices getting patched.

9/ The folks at @AmnestyTech conducted an independent validation of our forensic methods on a selection of cases. 

10/ Which government is behind #CatalanGate? Well, we aren't conclusively attributing to a specific government...
But substantial circumstantial evidence suggests a nexus with the Government of Spain.
But substantial circumstantial evidence suggests a nexus with the Government of Spain.

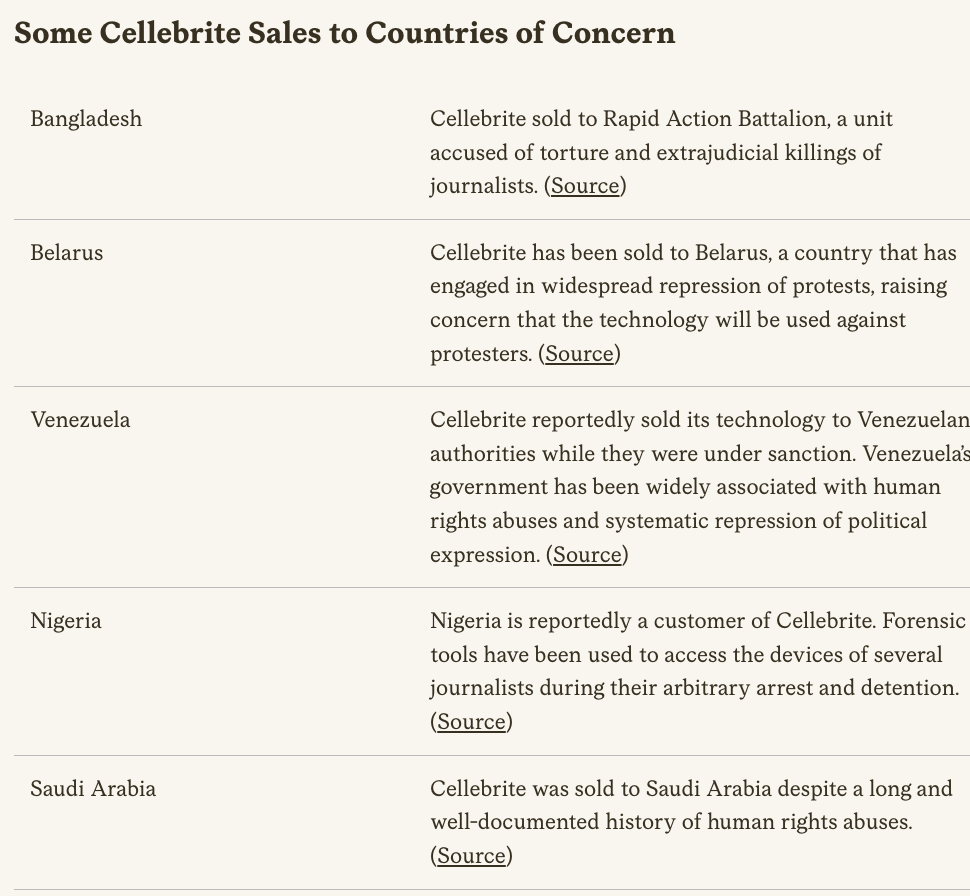
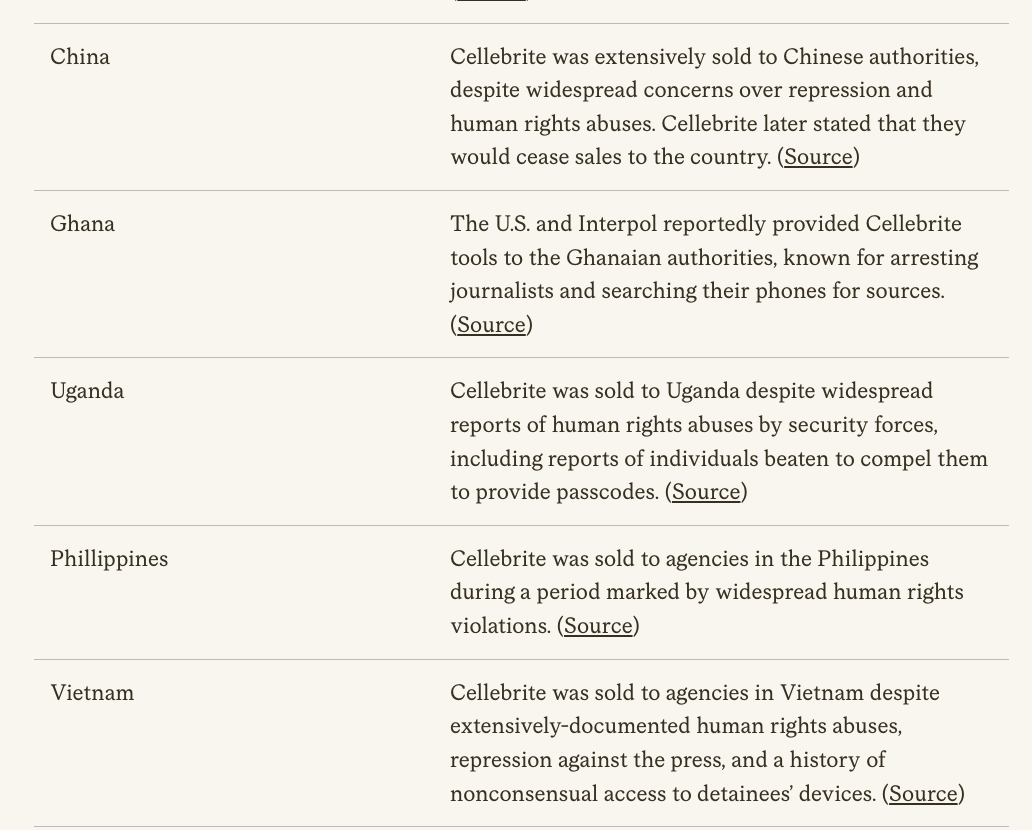
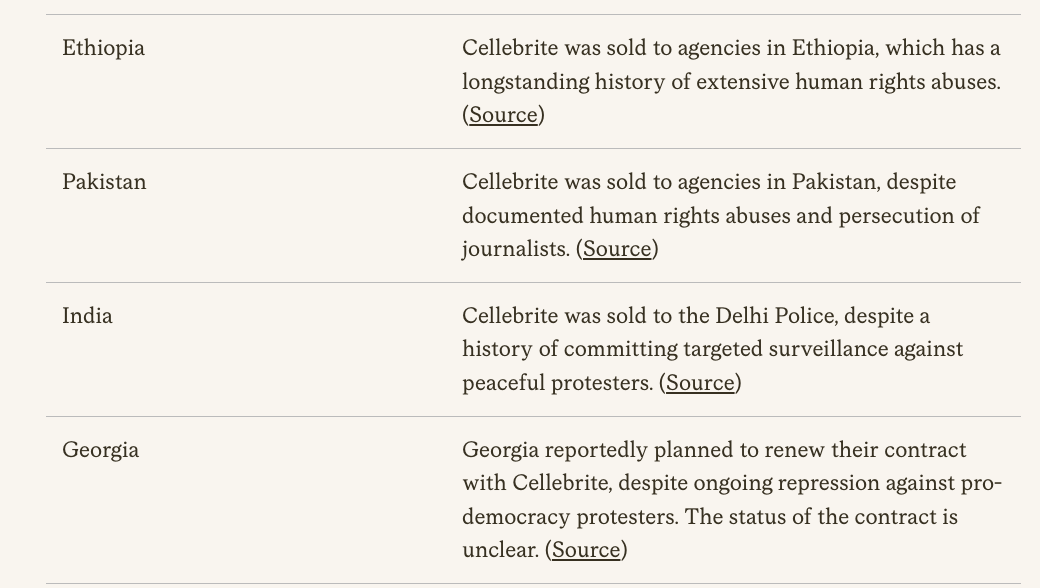
11/ Big picture: people think the problem with mercenary spyware is that it gets sold to dictators. Who abuse it. True.
Turns out that when democracies acquire it, risk of abuse is dangerously high.
It's abundantly clear that this is now a major problem in the #EU.
Turns out that when democracies acquire it, risk of abuse is dangerously high.
It's abundantly clear that this is now a major problem in the #EU.

12/ EU MEPs have begun weighing in👇
🇪🇺 EU Parliament's new committee on Pegasus spyware has first meeting tomorrow.
Sure to be interesting.
🇪🇺 EU Parliament's new committee on Pegasus spyware has first meeting tomorrow.
Sure to be interesting.
https://twitter.com/hneumannmep/status/1516038543759577089
13/ Investigations like this are group effort, huge credit to my coauthors @elies @billmarczak @insyria @sienaanstis @gozdebocu @SalSolimano & @RonDeibert
With help from Miles Kenyon @rizhouto @adamsenft
& so many others.
citizenlab.ca/2022/04/catala…
With help from Miles Kenyon @rizhouto @adamsenft
& so many others.
citizenlab.ca/2022/04/catala…
14/ Cases like this cannot come to light without the many victims & organizations that graciously consent to participating in our research, and chose to come forward & be named.
Without them, this report would not have been possible.
Without them, this report would not have been possible.
15/ Special acknowledgement to the team @domesticstream who helped us do the amazing graphical companion to our report.
They do great work, give them a follow!
catalonia.citizenlab.ca
They do great work, give them a follow!
catalonia.citizenlab.ca
16/ 16/ Nice thread by David Kaye, former UN Special Rapporteur, talking about *solutions* to the mercenary spyware problem.
https://twitter.com/davidakaye/status/1516096339599233025
• • •
Missing some Tweet in this thread? You can try to
force a refresh