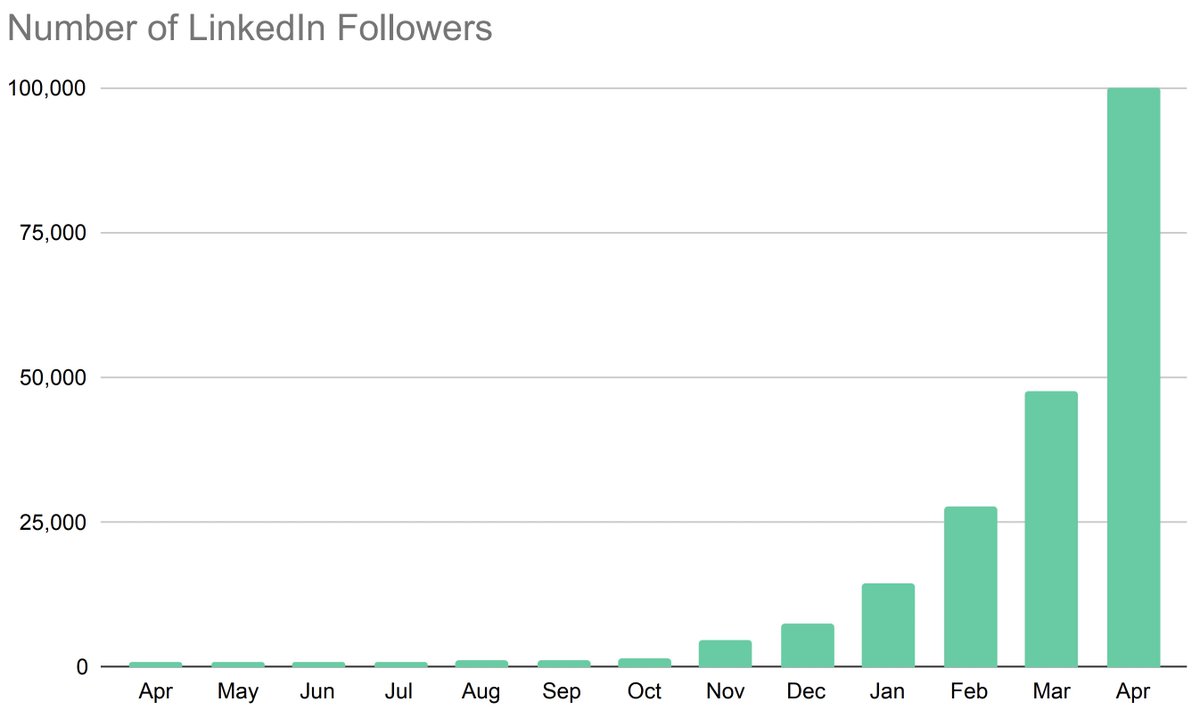
How does Twitter work? Let’s take a look at it from the architectural point of view before Elon takes it.
𝐓𝐡𝐞 𝐋𝐢𝐟𝐞 𝐨𝐟 𝐚 𝐓𝐰𝐞𝐞𝐭:
1️⃣ A tweet comes in through the Write API.
2️⃣ The Write API routes the request to the Fanout service.
#twitter #systemdesign
𝐓𝐡𝐞 𝐋𝐢𝐟𝐞 𝐨𝐟 𝐚 𝐓𝐰𝐞𝐞𝐭:
1️⃣ A tweet comes in through the Write API.
2️⃣ The Write API routes the request to the Fanout service.
#twitter #systemdesign

3️⃣ The Fanout service does a lot of processing and stores them in the Redis cache.
4️⃣ The Timeline service is used to find the Redis server that has the home timeline on it.
5️⃣ A user pulls their home timeline through the Timeline service.
4️⃣ The Timeline service is used to find the Redis server that has the home timeline on it.
5️⃣ A user pulls their home timeline through the Timeline service.

𝐒𝐞𝐚𝐫𝐜𝐡 & 𝐃𝐢𝐬𝐜𝐨𝐯𝐞𝐫𝐲
🔹 Ingester: annotates and tokenizes Tweets so the data can be indexed.
🔹 Earlybird: stores search index.
🔹 Blender: creates the search and discovery timelines.
𝐏𝐮𝐬𝐡 𝐂𝐨𝐦𝐩𝐮𝐭𝐞
🔹HTTP push
🔹Mobile push
🔹 Ingester: annotates and tokenizes Tweets so the data can be indexed.
🔹 Earlybird: stores search index.
🔹 Blender: creates the search and discovery timelines.
𝐏𝐮𝐬𝐡 𝐂𝐨𝐦𝐩𝐮𝐭𝐞
🔹HTTP push
🔹Mobile push

Disclaimer: This article is based on the tech talk given by Twitter in 2013 (bit.ly/3vNfjRp). Even though many years have passed, it’s still quite relevant. I redraw the diagram as the original diagram is difficult to read.
Over to you:
What are some of the biggest differences between Twitter and Facebook that might shape their system architectures?
What are some of the biggest differences between Twitter and Facebook that might shape their system architectures?
If you found this thread helpful, follow me
@alexxubyte for more.
Retweet the first tweet to help more people to learn system design.
@alexxubyte for more.
Retweet the first tweet to help more people to learn system design.
• • •
Missing some Tweet in this thread? You can try to
force a refresh