Good summary discussion of Russian battlefield communications and how Ukraine is intercepting calls.
1/
npr.org/2022/04/26/109…
1/
npr.org/2022/04/26/109…
Ukraine cut smartphone roaming to Russian/Belorussian numbers. Russians started using Ukrainian phones. The Ukraine Govt asked civilians to report in the phones that had been stolen.
Hey presto, Ukraine has a backdoor to Russian phone use.
2/
Hey presto, Ukraine has a backdoor to Russian phone use.
2/
Maybe more significantly, UA is defo making use of US SIGINT planes flying over Poland/Romania.
"I'm sure that they're collecting radio communications & other forms of intelligence that they then pass on to the Ukrainians that is invaluable in their prosecution of this fight"
3/
"I'm sure that they're collecting radio communications & other forms of intelligence that they then pass on to the Ukrainians that is invaluable in their prosecution of this fight"
3/
The question remains:
Why haven't the Russians directly attacked the Ukrainian telecoms networks.
@gregmyre1 suggests it is because the Russians wanted to make use of these networks post-invasion.
4/
Why haven't the Russians directly attacked the Ukrainian telecoms networks.
@gregmyre1 suggests it is because the Russians wanted to make use of these networks post-invasion.
4/
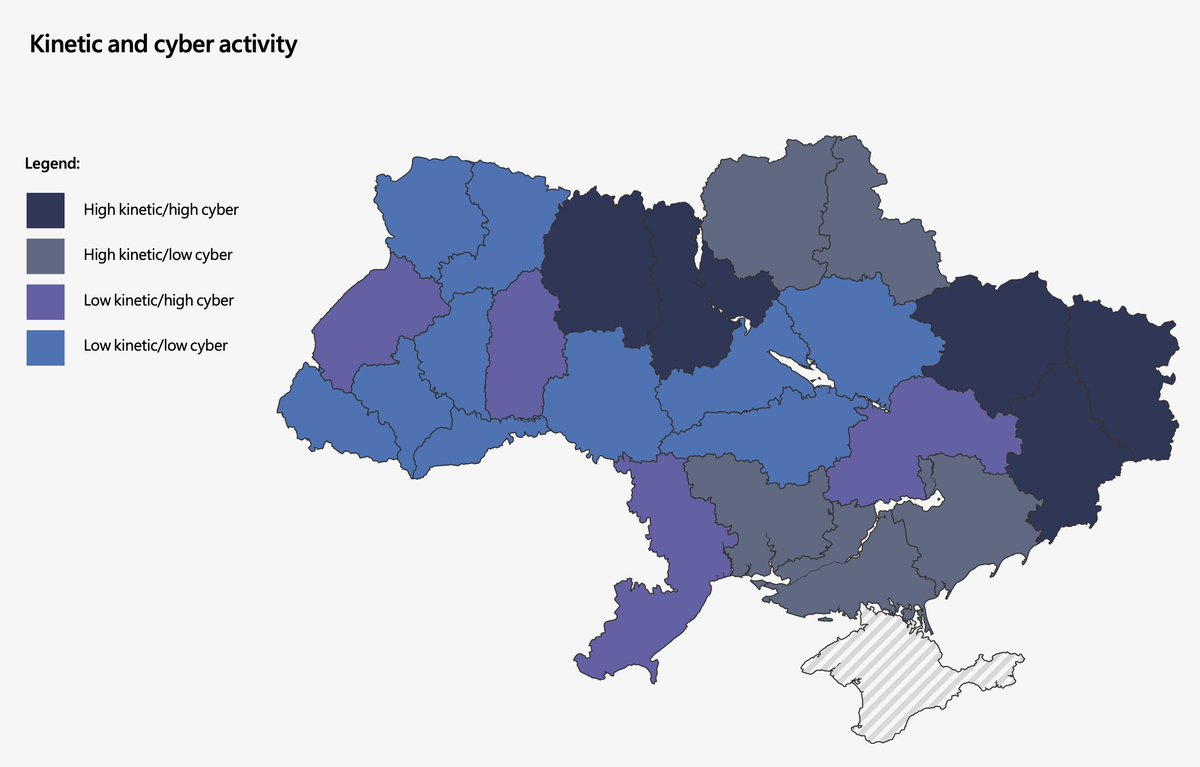
But also note the Russians HAVE been attacking Ukraine's comms network.
As Microsoft make clear, attacks have been coordinated with military activity. This implies that hybridity (see #miltwitter eyeroll) is a feature of Russian activity.
5/
blogs.microsoft.com/on-the-issues/…
As Microsoft make clear, attacks have been coordinated with military activity. This implies that hybridity (see #miltwitter eyeroll) is a feature of Russian activity.
5/
blogs.microsoft.com/on-the-issues/…
Microsoft note:
"Starting just before the invasion, we have seen at least six separate Russia-aligned nation-state actors launch more than 237 operations against Ukraine – including destructive attacks that are ongoing and threaten civilian welfare"
6/
"Starting just before the invasion, we have seen at least six separate Russia-aligned nation-state actors launch more than 237 operations against Ukraine – including destructive attacks that are ongoing and threaten civilian welfare"
6/
"The attacks have not only degraded the systems of institutions in Ukraine but have also sought to disrupt people’s access to reliable information and critical life services on which civilians depend, and have attempted to shake confidence in the country’s leadership"
7/
7/
"The destructive attacks we’ve observed – numbering close to 40, targeting hundreds of systems – have been especially concerning: 32% of destructive attacks directly targeted Ukrainian government organizations at the national, regional and city levels"
8/
8/
"More than 40% of destructive attacks were aimed at organizations in critical infrastructure sectors that could have negative second-order effects on the Ukrainian government, military, economy and civilians"
9/
9/
My own analysis of the information space is (FREE to download) and framed against my book #radicalwar.
The Microsoft report is a fascinating read. Will update this free paper as I take it towards publication.
10/
academia.edu/75845985/The_S…
The Microsoft report is a fascinating read. Will update this free paper as I take it towards publication.
10/
academia.edu/75845985/The_S…
We might focus on the armoured columns & artillery but the timely collection and fusion of this intelligence may be one of the most important features of the war in Ukraine.
11/
11/
• • •
Missing some Tweet in this thread? You can try to
force a refresh