
It's time for a 🧵on Boot devices. No we are not talking about SD cards, instead we are going to talk about encryption and security of boot devices!
One trend lately has been to use PCI-E attached RAID controllers for a pair of M.2 SATA/NVMe devices that boot the server. Example Dell BOSS (Great option!). One challenge is these controllers often lack encryption support.
So first off. Do you even need to worry about this? What is the attack surface of an ESXi device.
1. If you didn't use TPMs for caching vSAN encryption keys, in theory those would be there. (Spend $50 and buy a TPM, and this problem is solved).
2. Make sure someone didn't meddle with the binaries. Secure boot and host attestation require a TPM and cover this. There's noting proprietary unique here (Anyone running their own custom VIBs?) so this doesn't need to be encrypted just verified not tampered with. 
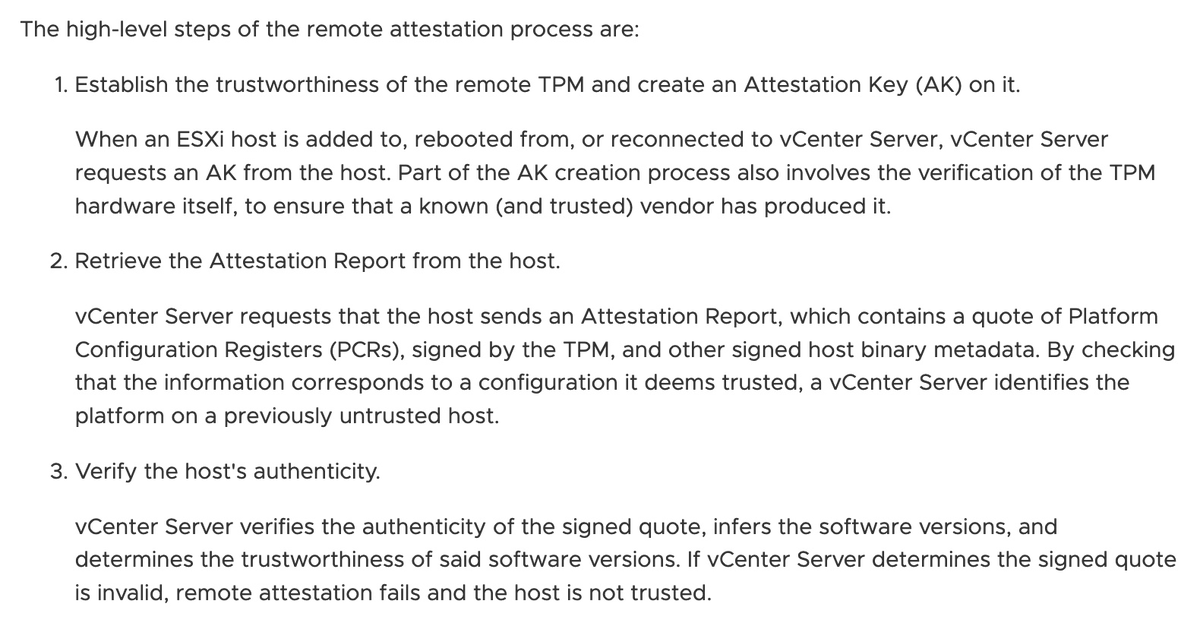
3. There also is the host configuration files and the "archive" of the configuration that is used at boot. This is encrypted by default in 7U2. Using a TPM (Again buy a TPM!) this information is sealed in the TPM.
What if I want full drive encryption? Well there are some options. 1. You can use a dedicated full RAID controller that supports this.
2. Some platforms are supporting SEDs with intel VMD. In this case the CPU acts as the controller.
core.vmware.com/blog/using-int…
2. Some platforms are supporting SEDs with intel VMD. In this case the CPU acts as the controller.
core.vmware.com/blog/using-int…
I've been dubious long term about attaching NVMe drives to a PCI-E attached raid controller (botteneck/complexity) and this from @IntelStorage is looking interesting. Note Intel is not providing encryption here, just key management with their VROC system. 
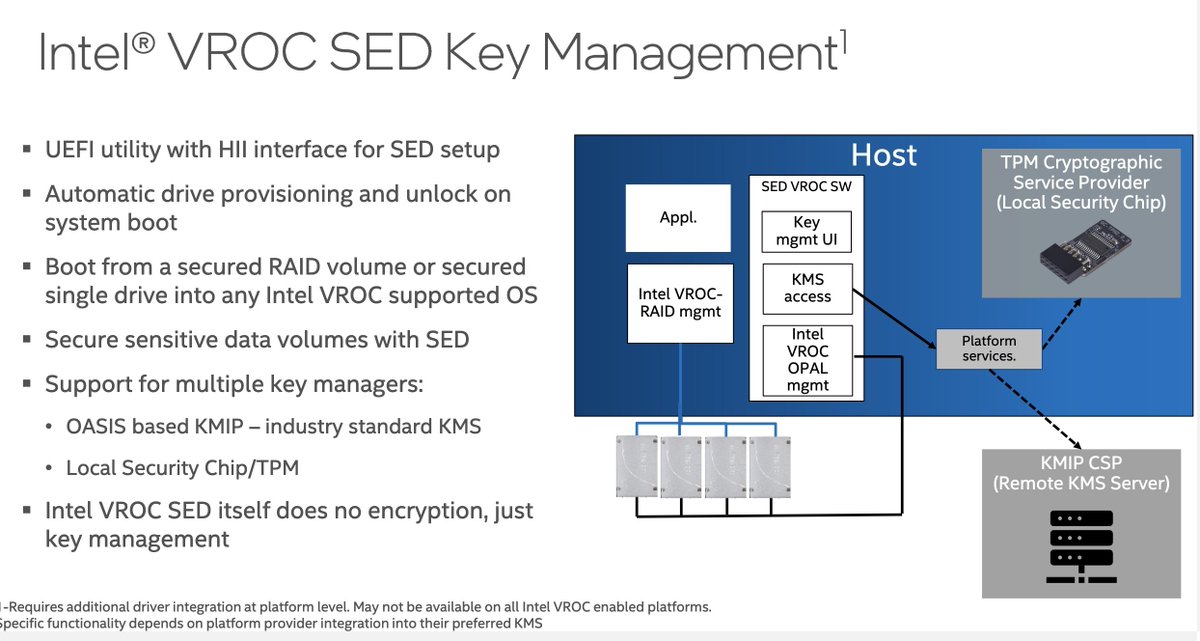
So In summery:
1. you can secure/encrypt everything on the boot device without using full drive encryption.
2. Intel is making a RAID 1 controller native to the CPU and SED key management is becoming table steaks.
3. BUY a TPM. If you don't see a TPM on the quote slap the SE.
1. you can secure/encrypt everything on the boot device without using full drive encryption.
2. Intel is making a RAID 1 controller native to the CPU and SED key management is becoming table steaks.
3. BUY a TPM. If you don't see a TPM on the quote slap the SE.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



